Your bank account is a tradable commodity on the black market. Over the past decade, the emphasis has shifted from destroying the contents of victims' computers to plundering them, and bank accounts are now harvested on a truly industrial scale.
Every small time crook wants a slice of the action, but becoming a customer of the hardened gangs controlling the world's largest botnets can be difficult. A much easier approach is simply to grab a phone book and pretend.
Sometimes, the fear induced by this new breed of fraudster can make people panic, and they can end up doing silly things that jeopardise their data, as the following true story shows.
A familiar story
A few weeks ago, a friend of mine received a phone call, apparently from Microsoft. Her computer, the caller said, was spamming the world. Worried, she did exactly as the caller asked.
She opened a command prompt window, entered something and read out what appeared on the screen. Could she open a browser and surf to a site that would confirm her infection? When she did so, a big red warning flashed on the screen. After entering a couple more commands, surfing to the site again showed that the stream of spam had abated.
Unsurprisingly, the caller told her that Microsoft would have to invoice her for the call, but could offer a discount if she paid now with a credit card. She didn't have one. The caller was insistent and asked for her husband's card details. She refused and asked for the invoice to be sent for her husband to deal with. The caller became aggressive. She hung up.
When the victim's husband arrived home, he half-remembered something on TV about the 'Microsoft calling' scam and malware. Not realising what it would do, he immediately ran the initialisation DVD that came with the laptop and then called me, wanting to know why the computer now looked like it did when they bought it at Christmas. Where were their holiday photos, emails and other stuff? Having no backups, the sad truth is that their data was gone for good.
Get the best Black Friday deals direct to your inbox, plus news, reviews, and more.
Sign up to be the first to know about unmissable Black Friday deals on top tech, plus get all your favorite TechRadar content.
Don't panic
Though it's possible that the caller in a 'Microsoft calling' scam might try to make you install malware, it would be a very inefficient route to obtaining your credit card details. The caller already has you in a compliant state and can just ask for them.
These people are con artists, but this story shows that it pays to know what to do in situations where you feel you have good reason to believe that you've been hacked or infected. It may just be a hunch, or your computer might have begun acting differently.
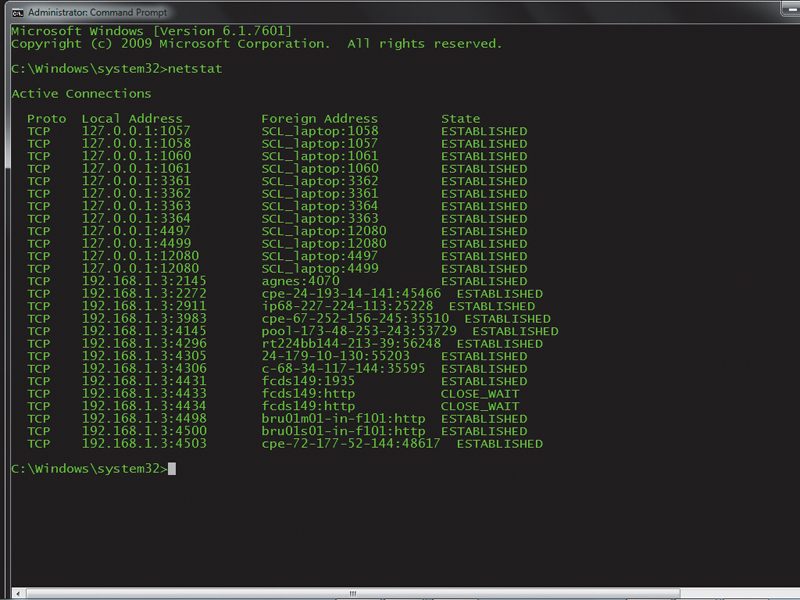
The first thing to do is to collect evidence, and the first port of call is the little-used netstat command. This will tell us if the computer is connected to the world beyond our network, and will help find where those connections go.
Reboot the computer to ensure that you have no spurious connections open, then right-click the command prompt (it's in the 'Accessories' program group) and run it as Administrator.
Before running a browser, mail client or any other network-aware program, type netstat. The result is a short list of connections. Most, if not all, should be between the computer and itself. These will have either 127.0.0.1 or the computer's IP address as the local address, and the computer's name as the foreign (remote) address.
After the IP address you'll see a colon and the port number in use. Any unexpected connections to foreign IP addresses must be investigated. Most will turn out to be links to legitimate services, but it pays to be sure.
Many legitimate online companies use obscure domain names for connections that are never usually seen by end users. We need to turn those foreign IP addresses into readable names using the netstat -f command. This time, the screen fills with a longer list of information.
In the Foreign column, you'll see remote server names, some of which you won't recognise, along with other IP addresses that can't be resolved into DNS names. We can trace all these DNS names and addresses.
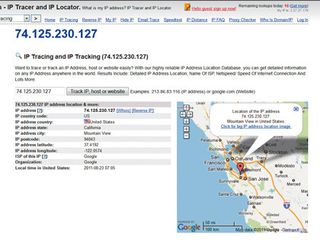
First, open a browser and go to www.ip-adress.com/ip_tracer (that's 'adress' with one D). Enter the domain name or IP address of an unknown foreign server and press [Enter]. The results can be very enlightening.
If your freshly booted computer shows connections to IP addresses that link to Google without you having used one of its sites or services yet, the connection could be from Google Update checking for new versions of installed products. Similar connections will be seen as other products call home to check for updates. Even the act of surfing to www.ip-adress.com will open new connections.
Using this site, distinctly odd looking domains like 'dy-inf100.1e100. net' resolve into harmless data domains – in this case owned by Google. The complexity of even seemingly simple web apps means that they can pull data and code in from a number of sources.
Other addresses will take a little more digging to determine their identities. If you're unable to identify the connection from the initial results at www.ip-adress.com, click one of the 'Whois' links. This produces a page containing much more detailed domain information, and should help you connect addresses to companies.
When trying to decide whether a connection is malicious, it also helps to be able to see the individual programs that connect to remote servers. If one of these is nothing you remember installing, it may be malware or a botnet client. Here again netstat can help with the initial investigation.
Type netstat -b and a slightly more complex list emerges. This time, a second line containing the name of a program in square brackets accompanies each connection. The program is the executable managing the connection. Though these should all be recognisable, sometimes even legitimate executables can have obscure names.
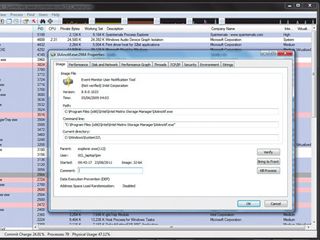
We can verify that programs are what they say they are using our old friend Process Explorer. It requires no installation, but remember to right-click the executable and run it as Administrator. Locate the suspect program in the list of processes double click it. This results in a sub-window with several tabs.
On the 'Image' tab, click 'Verify' to check that the signature of the public executable is correct. If an image cannot be verified, it may be old code that hasn't been updated explicitly for Windows 7, or it could be an unwelcome addition.
To decide which, Process Explorer uses a crude form of crowd sourcing. Close the sub-window, right-click the process and select 'Search online' to see what others have to say about it. If it isn't welcome, it may be time to take action, but not until your data is safe.
- 1
- 2
Current page: Recover from an attack: are you infected?
Next Page Recover from an attack: rolling backMost Popular
