How to secure your Linux system
Linux security tips and tricks and you need to know
Are you running Linux just because you think it's safer than Windows? Think again. Sure, security is a built-in (and not a bolt-on) feature and extends right from the Linux kernel to the desktop, but it still leaves enough room to let someone muck about with your /home folder.
Linux might be impervious to viruses and worms written for Windows, but that's just a small subset of the larger issue. Attackers have various tricks up their sleeves to get to those precious bits and bytes that make up everything from your mugshot to your credit card details.
Computers that connect to the internet are the ones most exposed to attackers, although computers that never get to see online action are just as vulnerable. Think of that ageing laptop or that old hard disk you just chucked away without a second thought. Bad move.
With the kind of data recovery tools available today (many as a free download) it doesn't matter what OS was installed on the disk. If it holds data – corrupted or otherwise – it can be retrieved, bank accounts recreated, chat transcripts reconstructed, images restitched. But don't be scared. Don't stop using the computer.
While it's virtually impossible to make a machine connected to the internet impenetrable to attacks, you can make an attacker's task difficult and also ensure they have nothing to learn from a compromised system. Best of all, with Linux, and some pieces of open source software, it doesn't take much effort to secure your Linux installation.
There is no golden rule for security that applies in every single case, and even if there were it would have been cracked already. Security is something that needs to be worked upon, and personalised. Follow the tips and tools in this tutorial as we show you how to adapt them to your very own Linux installation.
Follow these six tips to get a safer computer the easy way
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.
1. Keep up with security updates
All mainstream Linux desktop distros (such as Debian, Ubuntu, Fedora, etc) have security teams that work with the package teams to make sure you stay on top of any security vulnerabilities. Generally these teams work with each other to make sure that security patches are available as soon as a vulnerability is discovered.
Your distro will have a repository solely dedicated to security updates. All you have to do is make sure the security specific repository is enabled (chances are it will be, by default), and choose whether you'd like to install the updates automatically or manually at the press of a button.
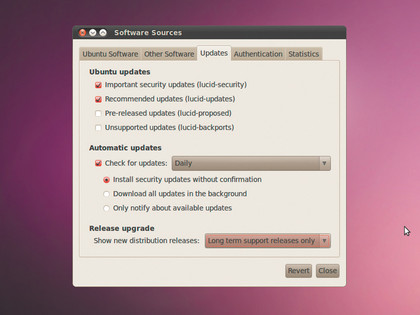
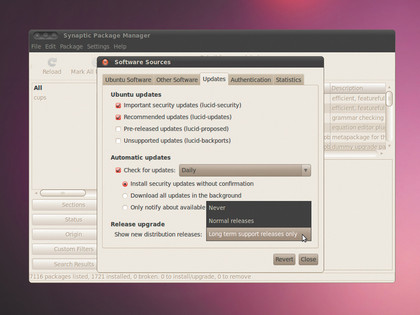
For example, under Ubuntu, head over to System > Administration > Software Sources. Here, under the Updates tab, specify how frequently the distro should ping the security repository for updates, and whether you'd like to install them without confirmation, or just be notified about the updates.
The latter is a better option, because it lets you review the updates before installing them. But chances are they'll be fine, and you can save yourself some time by having your distro install them automatically.
In addition to the updates, distros also have a security mailing list to announce vulnerabilities, and also share packages to fix them. It's generally a good idea to keep an eye on the security list for your distro, and look out for any security updates to packages that are critical to you.
There's a small lag between the announcement and the package being pushed to the repository; the security mailing lists guide the impatient on how to grab and install the updates manually.
2. Disable unnecessary services
A Linux desktop distro starts a number of services to be of use to as many people as possible. But one really doesn't need all these services.
For example, do you really need Samba for sharing files over the network on your secure server, or the Bluetooth service to connect to Bluetooth devices on a computer that doesn't have a Bluetooth adapter?
All distros let you control the services that run on your Linux installation, and you should make full use of this customisation feature.
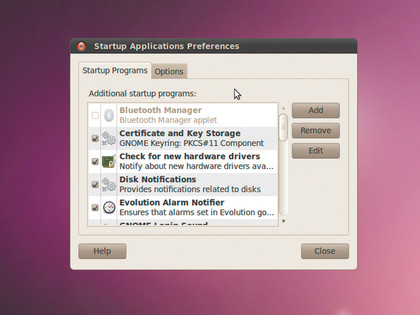
Under Ubuntu, head to System > Preferences > Startup Applications. Here you can remove check marks next to the services you wish to disable. But be careful when turning off services. Some applications might stop functioning because you decided to disable a service on which they rely.
For example, many server applications rely on databases, so before you turn off MySQL or PostgreSQL you should make sure you aren't running any applications that rely on them.
3. Restrict root access
Most distros these days don't allow you to login as root at boot time, which is good. When you have to execute a task that requires super user privileges you'll be prompted for a password. It might be a little irritating but it goes a long way to making sure that admin tasks are isolated from the user.
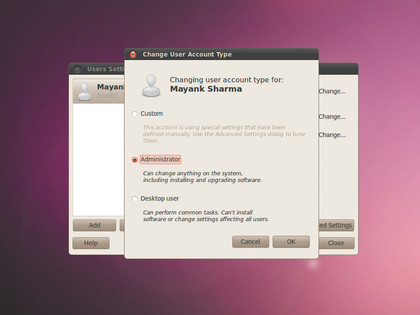
You can restrict access privileges for a user from under System > Administration > Users and Groups. Here you can broadly categorise a user as a desktop user or a system administrator or customise access privileges manually. By default, users are created as with 'Desktop user' permissions and can't install software or change settings that affect other users.
On the command line, the su command (on Fedora, and the like) lets normal users switch to the root account, while the sudo command (on Debian, Ubuntu, etc) grants more privileges to the user. The usage of these commands can be limited to a particular group, which prevents any user from administering the system. sudo is also the more secure of the two, and it keeps an access log under /var/log/auth.log.
Make a habit of regularly scanning the log for failed and successful sudo attempts.
4. Don't auto-mount devices
If you're really concerned about security, you need to lean on the customisation feature of the Users And Groups settings. One of the areas to look at is auto-mounting devices.
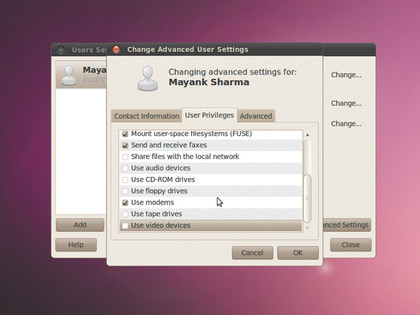
Most distros auto-mount USB drives and CDs as soon as they are inserted. It's convenient, but allows anybody to just walk up to your machine, plug in a USB disk and copy all your data. To avoid such a situation, go to to System > Administration > Users and Groups, select your user and head to the Advanced Settings > User Privileges tab.
Make sure you uncheck the boxes corresponding to the Access External Storage Devices Automatically option, the Mount Userspace Filesystems, and Use CD-ROM Drives option. When unchecked, these options will prompt the user for a password before giving them access to these devices.
You might also want to disable sharing files on the network, as well as require the user to enter a password before connecting to the Ethernet and wireless devices. By disabling access to configure printers you prevent important data from being printed.
5. Don't stay on the bleeding edge
Packages included in a desktop Linux distribution are updated regularly. Besides the official repositories, there are custom repositories for third-party software. While developers do take care to scan the packages for vulnerabilities before pushing them on to the repository, it's almost inevitable that some updates with defects do get through.
While it's good to keep the system updated, from a security point of view, not all updates are good for the system. Some updates conflict with existing installed package or may even pull in new dependencies that may make the system more prone to attack. All this is why you should only update packages if you have to.
Scan the updates and look for updates to packages that are critical to you. Most package managers also make it possible to check an update and display its changelog and a brief description of the changes. UI changes can safely be ignored or delayed until a package has been thoroughly tested. Instead, look out for and grab updates that offer a fix to existing issues with packages.
6. Don't upgrade every six months
Most major desktop Linux distributions make a new release every six months, but you don't have to install every last upgrade just because it's there. Debian, for example, offers three distributions to choose from based on the extent of the stability of the software available in it. After Debian 6.0, stable releases will be made every two years.
Other distros take a different approach to guarantee secure releases. Ubuntu marks certain releases as LTS (or Long Term Support). A desktop release of the LTS version is supported for three years, and a server release is supported for five years, which is a lot longer than the 18 months for a standard Ubuntu release.
Although not up to date, these releases are much more secure from a security point of view, with packages that are a lot more stable and more thoroughly tested than their latest versions. If running a secure system is your goal, you should think of sticking to one of these long-term stable releases and avoid the temptation to upgrade as soon as the latest version of your becomes available.
With almost two decades of writing and reporting on Linux, Mayank Sharma would like everyone to think he’s TechRadar Pro’s expert on the topic. Of course, he’s just as interested in other computing topics, particularly cybersecurity, cloud, containers, and coding.
