Windows 8 security: everything you need to know
The security enhancements that Windows 8 brings
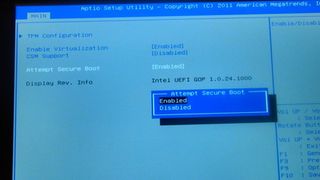
New Windows 8 PCs have UEFI Secure Boot firmware, which enables your PC to check security certificates for the boot loader, kernel, system files and drivers against a database as Windows loads. Think of it as a mini operating system that checks that your usual OS hasn't been tampered with.
Mind you, Windows RT is one way of avoiding a lot of security problems; if you can't install your own desktop software, Windows malware is going to have a hard time running as well.
Windows RT will certainly come under attack, but it has the same protections as Windows 8, starting as soon as you turn it on.
Your anti-virus software starts running while Windows is still booting (as long as it supports Early Load Anti Malware or ELAM), so it is running before any malware that's managed to get onto your PC.
If there's a rootkit on your PC waiting to change Windows components when you boot, Windows will find the code it changes and replace it with the original, legitimate code from the Windows 'side by side' store. You don't see a warning for that during boot, but the details will show up in your anti-virus warnings in the Action Centre.
Guard pages
Once Windows is running, it's harder to use the way it handles memory that's in use (called the heap) to attack the OS or the programs you're running.
In previous versions of Windows it's not hard to allocate too much memory, have it overflow the buffer it's supposed to fit in and use that to run an attack. The Windows 8 kernel has much stricter limits on how much memory can be allocated, so an overflow attack would have to be exactly the right size.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
The kernel can put 'guard pages' of memory around important code, like a moat, so that if malware tries to attack by corrupting the next chunk of memory and overflowing, it's more likely to end up in the memory moat, and Windows will shut down the process for accessing invalid memory.
Randomising memory
The tools for keeping track of the memory allocated to applications are smarter - they now make sure that the memory allocated starts in a random place, rather than picking it based on a value that malware could interfere with to make it point to malicious code, or using a predictable location such as the next free chunk of memory.
To make the random number really random, Windows collects a mix of data when it boots, from the clock, performance logs, power management systems and other sources, which it combines into a new random number seed every time.
Memory that's no longer needed is less vulnerable as well. Malware used to be able to force the kernel to allocate memory to a program and then release it so that a virus could use memory that Windows thought wasn't in use; that's now blocked.
Memory allocation
In Windows 7, Data Execution Prevention (DEP) can already mark memory allocated to applications for storing data so it can't be used for running code. And Address Space Layout Randomisation (ASLR) 7 means program code isn't always loaded into the same place, which makes it harder for malware to find where to attack.
They protect Windows, but you have to rely on developers turning them on when they write their own programs. Windows 8 won't run on CPUs that don't have the hardware to mark memory as only for data (NX - Non executable) and the improvements to the memory heap are on by default, so they protect everything.
Windows 8 also uses the Supervisor Mode Execution Protection (SMEP, or OS Guard, as Intel calls it) in Ivy Bridge CPUs to stop the CPU running any memory pages that are marked as 'user' rather than 'kernel' (user pages are only for data).
So using NX to protect kernel memory is important, because otherwise malware would just target kernel memory to bypass SMEP.
Safer Wi-Fi
When you connect to a secure Wi-Fi hotspot, you need to type in a password - and for very secure networks you might need to have a certificate installed on your PC.
Windows 8 adds support for several wireless and mobile Extensible Authentication Protocol standards that enable you to connect to secure networks without having to get a certificate or roam between different wireless and mobile broadband networks.
There's a new standard on the way called Hotspot 2.0 that will make it easier to automatically connect to Wi-Fi hotspots as you travel around; these new protocols are what you'll need to use it.
So when your mobile operator supports Hotspot 2.0, your Windows 8 tablet will be ready to get you online with it.
Mary (Twitter, Google+, website) started her career at Future Publishing, saw the AOL meltdown first hand the first time around when she ran the AOL UK computing channel, and she's been a freelance tech writer for over a decade. She's used every version of Windows and Office released, and every smartphone too, but she's still looking for the perfect tablet. Yes, she really does have USB earrings.
Most Popular



