Your smartphone PIN isn't as safe as you'd think
There's always someone out to get you

We all know the dangers. The smartphone is the portal to online shopping, our bank accounts and all manner of social network profiling – for many, it is our digital identity.
We know what we have to do: make sure it has a lock code, and never share it with anyone.
But…what if even that isn't enough?
Researchers at Cambridge University recently proposed a method of discovering the PIN on your Android phone by using a malicious app to capture data through your smartphone's camera and microphone. This technique made headlines as it was able to correctly identify a 4-digit PIN, from a test set, 30% of the time after two attempts, rising to 50% after five attempts.
Flanking maneuver
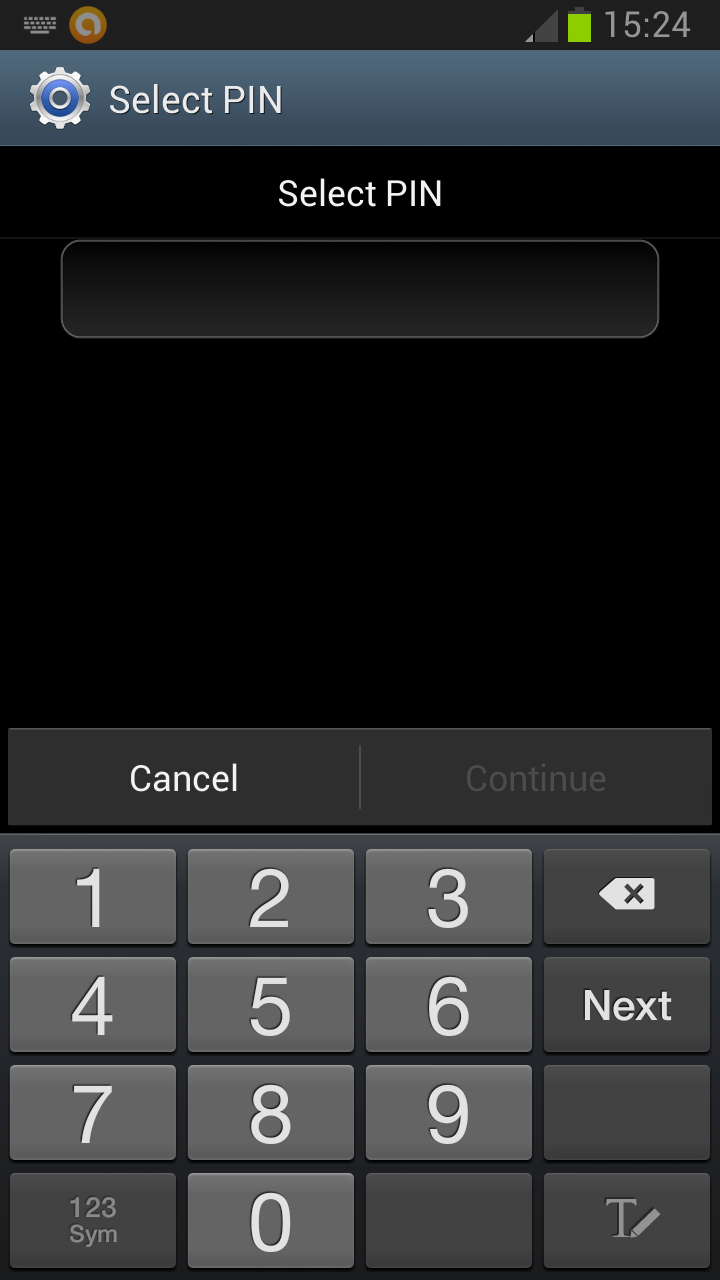
The reason this technique, known as a "side-channel" attack, is so noteworthy, is that it circumvents the supposedly secure split between the Android system and the trusted zone on your smartphone.
"Side-channel" attacks use sensors like the gyroscope and accelerometer, or hardware, like the microphone and camera, in order to capture data that's uploaded to a remote server where an algorithm is used to take an educated guess at your PIN.
The 'trusted' part of your phone is separate from the main OS and is designed to isolate sensitive applications, such as banking apps. This is all part of a move to keep sensitive data like your PIN on separate hardware, with companies like ARM inventing technologies such as TrustZone to ensure this stays secure.
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.
However Laurent Simon, one of the authors of PIN Skimmer: Inferring PINs Through The Camera and Microphone, told us, "it's not obvious that the accelerometer or the microphone could be used to leak information…the focus is on the touchscreen, on securing the screen."
How does it work?
This attack involves using the PIN Skimmer app, which is malware disguised as a game, to record users interacting with the touchscreen.
The front-facing camera can be used to capture a shot of the user and determine what they look like when pressing a specific point on screen. This data can then be used to build a model and analyze a video of them entering their PIN.
This is further bolstered by using the microphone to capture audio of the haptic vibration feedback when the user presses the screen in specific spots.
In fairness to phone developers, victims have to download the app and grant it permission to access the microphone, the camera, and the Internet in the Android system.
Once the attacker identifies a likely PIN, they still need the smartphone physically in hand before they can try it, as Simon explained, "in that sense it's limited, you can't do everything remotely; you would need to [inadvertently] collaborate with thieves."
Before you dismiss this idea as never going to happen to you, consider that malware could also be used to track your location, and smartphone theft is at an all-time high. Earlier this year the Met revealed that there are more than 300 mobile phones stolen every day in London alone.
How can you protect yourself?
Marc Rogers, Principal Security Researcher at Lookout, told us "The absolute, most common, method of compromising your smartphone is installing something from a third-party store that will send out your phone number, your contacts list, your SMS messages, and allow someone to remotely control the phone.
"We did a study on the likelihood of encountering this kind of malware and we found in the US and UK that the likelihood of encountering something nasty (a phishing link, adware, or malware) is around 2% to 3%. Your probability of actually encountering malware is about 0.5%."
Those figures are based on data captured from millions of Lookout Mobile users, with Rogers suggesting that to protect themselves users should "stick to [Google's] Play Store and don't go to third-party stores. These don't necessarily have the same level of protection and that's why the probability rises from 0.5% in the UK to around 40% in the Russian Federation and Ukraine."