Computing Security
Explore Computing Security
Latest about Computing Security

Quishing is the new QR code scam you need to watch out for – here's how to stay safe
By Chris Rowlands published
QR code phishing is getting increasingly sophisticated

What a new Trump mandate could mean for American data privacy rights
By Chiara Castro published
While it's still early to know for certain, many fear that online surveillance could increase, making VPNs and other encrypted services a even more crucial tools for people in the US.
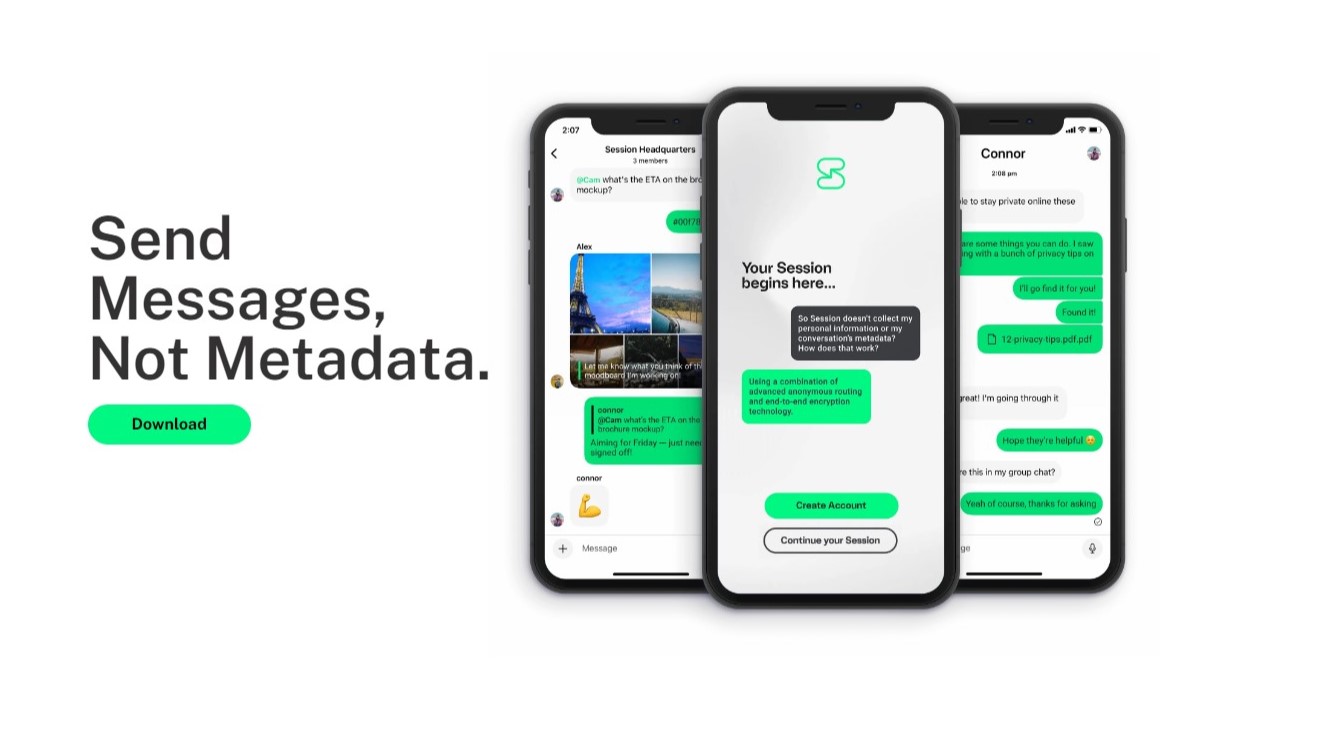
Undermining your privacy? Session says no and leaves Australia
By Chiara Castro published
The message is clear – the team at Session isn't willing to compromise users' privacy and landed in Switzerland. Here's what happened.
Are online dating and data privacy an incompatible match?
By Chiara Castro published
Mozilla is challenging Bumble, a popular dating app, to do better when it comes to users' privacy. Something is slowly changing, but you still need to do your part to protect your data.

Give Meta my face recognition data? I'd rather lose my Instagram account
By Chiara Castro published
Despite the security benefits, Facebook's parent company's bad track record when it comes to protecting our data rather scares me.

How to choose a secure password?
By Bryan M Wolfe last updated
Tutorial Passwords are vital, but how should we select them?

Before moving from "analogue to digital," the NHS has to fix its privacy flaws
By Chiara Castro published
"Patient passports" promise to fix UK's flawed health system. Yet, they could eventually lead to a security and privacy nightmare for our most sensitive data.

I attended the 2024 Encryption Summit - here are my 5 takeaways
By Chiara Castro published
I attended the second edition of the virtual event to shed light on the need for encryption and the challenges this tech faces. Here's what I learned.
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.

