A brief history of hacking and how to protect yourself today
Hacking’s fascinating history has important lessons for protecting yourself in 2025

Hacking has been used as a tool for good and evil since machines existed. At its simplest, it refers to using something in a way that wasn’t intended, but it’s generally (and unfairly) regarded by the mainstream public as something perpetually nefarious. So, let’s take a look at the modern history of hacking and see how it’s led to the protections we need today.
The hacks, the myths, the legends
The movies illustrate good-guy ‘white hat’ hackers, bad-guy ‘black hat’ hackers and in-between, ‘grey hat’ hackers, as well. There’s Matthew Broderick in War Games cheekily hacking into his school’s computer system to change his girlfriend’s grades, and Mark Zuckerberg’s pre-Facebook ‘Face Mash’ exploits in The Social Network, as memorable examples. But, it’s another real-life character that bridges cheeky shenanigans and a criminal mindset.
In the 1970s, Apple co-founder Steve Wozniak joined the ‘phreaker’ community which figured-out how to get free, long-distance phone calls by playing the right tones to a payphone. His Blue Box made this simple and Steve Jobs says that without it, there’d be no Apple.

Other notable hacking communities grew from video games: speedrunners use tweaks and exploits to complete games in record times, and early PC gamers overclocked CPUs and graphics cards for upgraded performance. In 2009, a University of Toronto research team hacked graphics cards, using its processors to train a neural network for the first time.

Things are getting serious
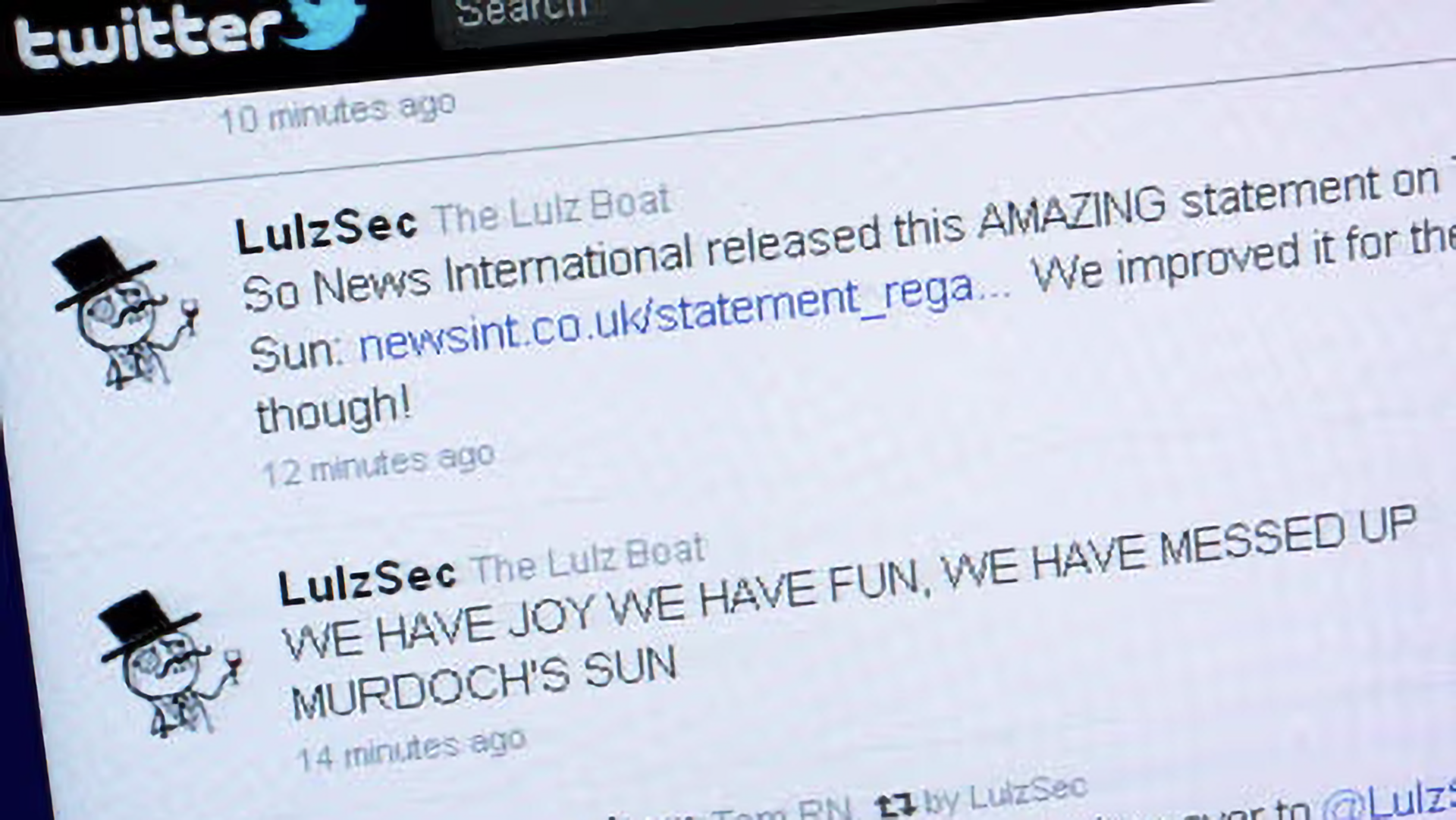
Other hackers make a nuisance of themselves for laughs and Wozniak is, worth mentioning. At a time where it was common to manipulate ‘bunny ears’ TV antennae to achieve a clear picture, he’d use a secret TV broadcaster box to produce static that would only vanish when someone held the antennae in increasingly absurd positions. Fast-forward to 2011 and LulzSec hacked into notable Fortune 500 companies and governments. They didn’t steal money but left taunting messages that made global headlines. It was their actions that motivated many big businesses to finally take cybersecurity seriously.
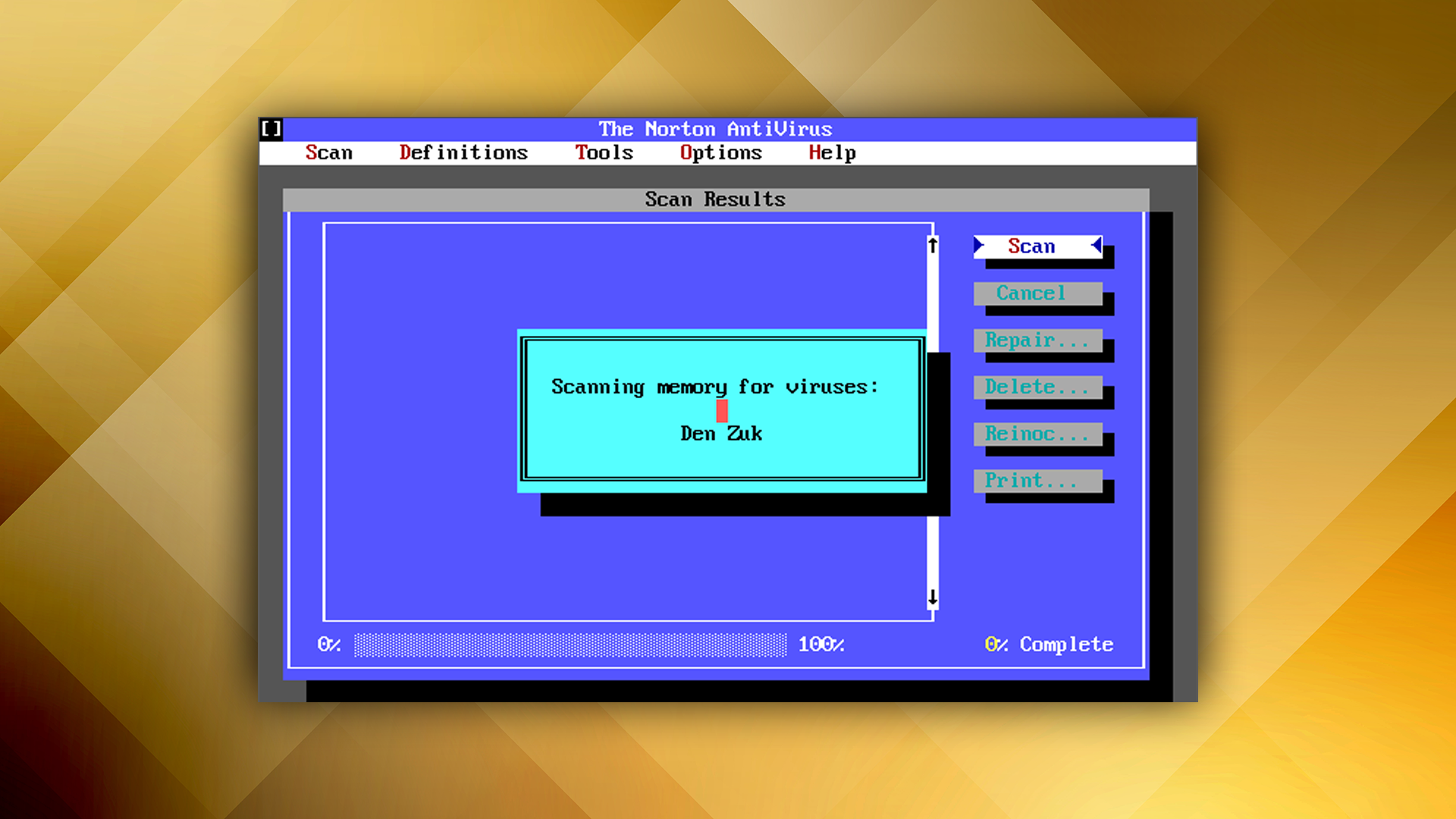
Before that, nuisance virus outbreaks like 2001’s Nimda would quickly infect computers and networks. It didn’t steal anything, just stopped them functioning. This led to an increased adoption of antivirus software such as Norton AntiVirus, which had seen its popularity grow rapidly ever since it was first launched way back in the early 1990s, as concerned users took steps to help block threats.
Fast forward to today and the black-hat hackers are incredibly well organised. Some are using AI to automatically scour the internet for compromised systems, while others are selling off-the-shelf hacking tools to wannabe cybercriminals. They even provide helpdesk support!
Hacking in the modern world
Nowadays it’s common for state actors to hack into organisations to steal IP or disrupt their national infrastructure, while criminal gangs use ransomware to permanently encrypt files unless a ransom is paid. It’s big business too: one ransomware attack recently scored a $75m payout. Major organisations counter with policies like multi-factor authentication and zero trust strategies (where passwords alone are not enough) plus, AI-based behavioural protection that automatically flags and locks-down anomalous behaviour.
Of course, the same major organisations still regularly suffer major breaches, and it’s largely down to the cybercriminals targeting the weakest link in the chain – the users – with all kinds of fake emails, text messages and scams. It escalated during Covid and it’s not slowing down.
One hacker recently showed celebrity Joe Rogan a USB drive that actually functioned as a keyboard. These devices would be left around car parks so that when a curious employee inserted one into their work computer, it instantly typed a series of commands that gave hackers full access.
Protection has evolved

So, with such concerted efforts from criminals and AI to attack you, it’s never been more important to use technology to help watch your back and defend yourself.
It was back in the 1990s that commercially available virus scanners really took off, and there are still some big names from that era protecting their customers today.
Over the years people using their computers and other devices have become acutely aware of the need to add an additional layer of protection, and today’s security suites do just that.
A good security suite should offer a wide gamut of protection and be simple to use. Hackers have been at it for decades and they’re not going away any time soon. Let history be your teacher, and always be prepared for the unexpected!
Today, Norton 360 Premium helps provide real-time antivirus and malware protection for five PCs, Mac, tablets or phones, but that’s just the tip of the iceberg. Also included is:
● A VPN to help you browse more securely and privately
● Dark Web Monitoring to see if your personal information has been found on the dark web
● Password Manager to help store and manage your passwords and other credentials online more securely
● 100GB cloud-storage backup for Windows PC to help store important files and documents in case of data loss due to a device being stolen or ransomware
This is the sort of comprehensive feature set that’s necessary to help combat cyber threats in 2025. We no longer live in the simple age where the only threat was a simple virus. Now, identity protection is also critical. For a limited time, Norton is offering Equifax Credit Protect (12-month)¹, a credit monitoring service to help you monitor your credit profile. With this, you can receive alerts for key changes on your credit report, get monthly credit report updates for 12 months, and track your credit score over time with Equifax Score Tracker.
All of this works in the background to help protect you and your family against nefarious types who seek to compromise your data and steal your money.
¹ Offer valid while supplies last from 21 Oct 2024 with new purchases of Norton 360 Premium, Norton 360 Advanced, and Norton Identity Advisor Plus on au.Norton.com. Eligible Norton customers will be invited to redeem an Equifax Credit Protect (12-month) promo code. Only 1 redeemable code per purchase. Equifax Credit Protect (12-month) promo code must be activated by 29 Mar 2025. Codes cannot be resupplied or reissued.
The TechRadar hive mind. The Megazord. The Voltron. When our powers combine, we become 'TECHRADAR STAFF'. You'll usually see this author name when the entire team has collaborated on a project or an article, whether that's a run-down ranking of our favorite Marvel films, or a round-up of all the coolest things we've collectively seen at annual tech shows like CES and MWC. We are one.

