How to add extra security to your Apple ID
Secure your Apple ID

Boost your Apple ID protection
Last year Apple received criticism when a number of celebrities claimed their iCloud accounts had been hacked, leading to personal photographs being published online. Apple's response was to remind people to keep their passwords safe.
However, security experts argued that this couldn't have happened if Apple had adopted a security technique known as two-factor authentication to Apple ID. This adds a second layer of security to your Apple ID, sending an extra security code to your iPhone or iPad that must be entered in addition to your normal Apple ID or iCloud password before anyone can gain access to your account.
That was back in 2014, and thankfully Apple has now included two-factor authentication for its products, building the technical underpinnings for it into OS X El Capitan and iOS 9, which is no small task.
For more information check out our guide on how to enable two-factor authentication on your iPhone or iPad.
Apple's two-factor authentication has a limitation, however. It's only available if all the devices linked to your Apple ID are running Apple's latest software – the web page just mentions details of the system requirements for Apple devices and Windows PCs.
So, if you use your iCloud account on one device that isn't running, or is unable to run, the latest software, you won't be able to benefit from the stronger protection afforded by two-factor authentication on any of your other devices.
However, in the wake of the celebrity hacking scandal, Apple introduced a security measure it calls two-step verification. Though it bears a similar name and works in a similar fashion to two-factor authentication, it merely sends a four-digit verification code to you; two-factor authentication's codes are six digits long, and are pre-empted by details of an access attempt's location, so you can reject it immediately rather than receive a code.
In the long run, two-factor authentication will be the stronger option. However, until everyone can use it, two-step verification is worthwhile because it adds extra security to your Apple ID to help keep your data safe.
Also, you don't need to be running iOS 9 or El Capitan to benefit from it, so having one bit of hardware running an older operating system won't hold you back.
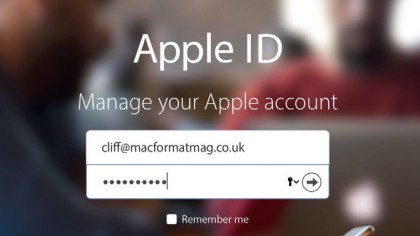
1. Manage your Apple ID
To set up two-step verification, go to the Apple ID website using a web browser on any device. Right now only the email address and password associated with your Apple ID are needed to sign in, but that will change in a moment.
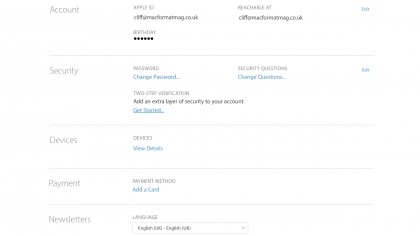
2. Request to turn on
Under Security, click Get Started next to Two-Step Verification. Apple will send a confirmation email.
If you've made significant account changes recently, this email can take three days to arrive; your account works as normal in the interim.
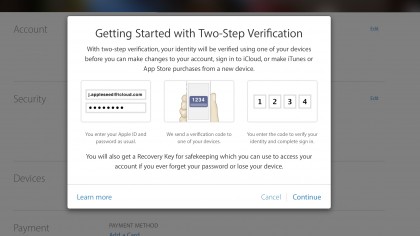
3. Confirm it's you
When you receive the email, return to your Apple ID account page and click Get Started again. A message will explain two-step verification sends an extra verification code to one of your devices.
This code can only be used once.
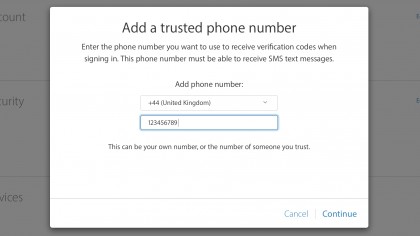
4. A trustworthy phone
Now you have to provide a 'trusted phone number'. This doesn't have to be an iPhone, or even your own phone – but it should obviously belong to someone that you trust, and the phone must also be able to receive text messages.
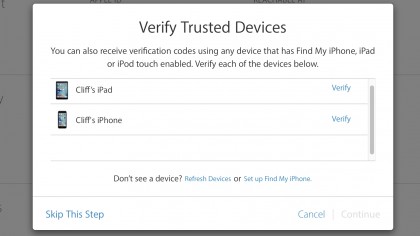
5. Other trusted devices
You can add other trusted devices to your account, and send the verification code to any of those devices.
During this step you should make sure that all your devices are awake, signed in to your Apple ID, and connected to the internet.
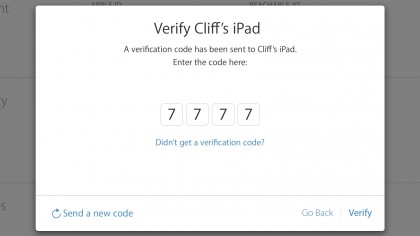
6. Verification codes
Each device or phone number that you identify as trusted receives a special one-off verification code.
You can read the code on that device and then enter it on the Apple ID management site to confirm the device is in your possession.
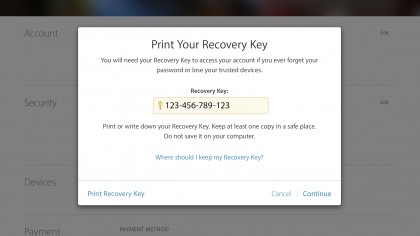
7. Your Recovery Key
Your final line of defence is a special recovery key. Should you forget your password, or if your trusted devices are lost or stolen, you can use this key to regain access to your account – so commit it to paper and keep it safe!
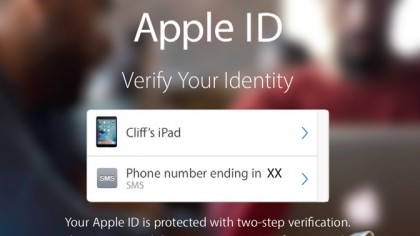
8. Who goes there?
In future, when you sign in to your account, you'll be asked to enter your password as usual. However, there's now a second verification step, so you'll be asked on which of your trusted devices you want to receive a verification code.
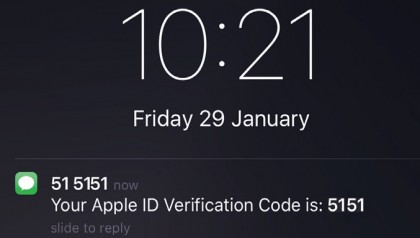
9. Device defence
We've sent the verification code to our iPhone. On whichever trusted device you choose, the code will appear after a few seconds.
Enter the code on whatever device you were using to sign in to your Apple ID and access your account.
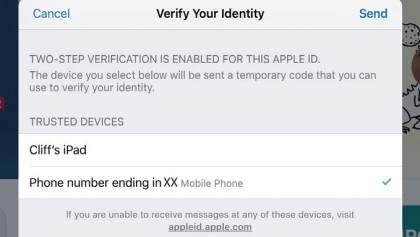
10. Purchase protection
Extra protection now applied on any Mac or iOS device linked to your Apple ID. Here it has kicked in when we tried to buy an app on our iPad.
A code is also needed to sign in to iCloud on a new device, or to use apps such as FaceTime.
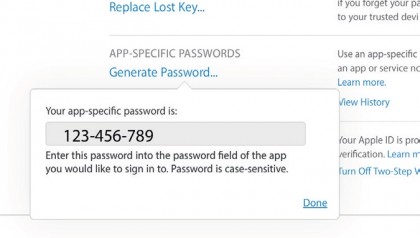
11. Third-party apps
Apps such as Fantastical connect to your iCloud account but provide no way for you to enter a verification code; an app-specific password is needed to grant them access.
Edit your account's security settings, then click Generate Password.
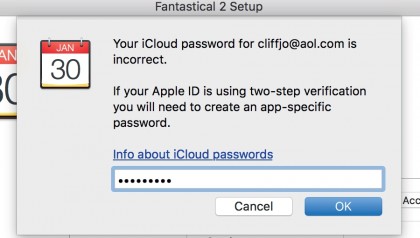
12. Manage them
In your app's password request box, immediately enter the generated password. You can create up to 25 appspecific passwords.
If you alter your main one, all of these will be revoked and you'll need to generate new ones for your apps.
- Enjoyed this article? Get more tutorials, guides, and tips on how to get the most from your Apple devices inside MacFormat. Take advantage of an exclusive offer in our sampler today.
Cliff Joseph is a former Editor of MacUser magazine, and a freelance technology writer with 30 year’s experience in the industry (and old enough to remember when Apple was close to going bust…).
His first job involved using Macs for magazine sub-editing and typesetting, which led to the realisation that these computer-thingies might actually turn out to be useful after all. After a few years specialising in the Mac side of the market, he went freelance and embraced the wide world of digital technology, including Windows PCs, digital audio and hi-fi, and networking. Somewhere along the line he also developed a bit of a gaming habit and has stubbornly waved the flag for Mac gaming for far too many years.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful