How to prevent a data breach
Five quick tips and one easy solution to help you secure your data

Data breaches cost, on average, $9,440,000 per year, just in the U.S. alone according to a report by IBM. It explains that the use of ransomware in connection with a data breach has grown by 41%, and in 2022, it took an average of nine 9 months to identify and contain a breach.
While major data breaches are often found with large companies, for example, AT&T, Twitter, Meta, and T-Mobile have all reported data breaches within the last year, the biggest breaches of personal identity information come from phishing schemes. This is malware that poses as a legitimate email or instant message from someone you know or a company you do business with. It asks for personal information, like login credentials or bank accounts, to steal your identity.
You can't always control a data breach, but there are things you can do to help minimize the damage. With all that said, an ounce of prevention is worth a pound of cure. So here are our recommendations:
1. Install reliable antivirus software
Since the biggest malware threat that contributes to data breaches is ransomware, it makes sense to use antivirus to detect and stop it. There isn't a huge threat of ransomware infecting a personal device, but there is a risk if you work in a high-profile industry, such as in government offices, infrastructure design, and construction, or even the military. Cybercriminals look for these types of workers and target their home computers and personal devices just in case they do any work from home or on the run.
Even if you’re not in a risky data-handling industry, using antivirus software is still a good way to protect your computer from any online or network threat out there.

2. Learn to recognize phishing
Phishing schemes are very specific scams that come through email messages, instant messages, and texts. They are becoming more and more difficult to recognize because cybercriminals are getting smarter. But there are still ways to detect a phishing scheme and steps you can take just to make sure you don’t fall prey to one.
To begin with, know that financial institutions, including banks and credit card companies, won’t ever send you a message asking for personal information to be sent to them. If you get any message asking for this kind of information, call your financial institution directly and ask them.
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.
In fact, any message that asks for personal identifying information, including your full name, birthday, address, or social security number, shouldn't be answered through return messages. Instead, call the company to see why they need that information. As an extra precaution, find the number from the company’s website, and don’t trust any contact information in the message you receive.

Also, be wary of messages coming from someone you know asking you to help them out by paying money or purchasing gift cards. An experience I recently had was through an email message from the principal of a local school asking me to help him purchase gift cards to hand out to staff as an end-of-year thank you.
At first glance, it sounds like a legitimate request, but the sender’s email address did not originate from a school district email address. Furthermore, much of the message was written very poorly without proper grammar, capitalization, or punctuation.
When in doubt, call the person or company directly.
3. Invest in a VPN
A VPN, or virtual private network, is a tool that hides your online identity as you browse, shop, play, or work online. Everything that is shared, uploaded, downloaded, or sent through the web is encrypted, so it's difficult for snoops to grab your information even if it is intercepted.
The best VPNs have an effective kill switch that will protect your identity if the VPN connection is accidentally interrupted or lost. And, when you are done using the VPN, it won’t log your browser history, so there’s no way to trace your online activity back to you.
While using a VPN won’t stop a company data breach from happening, it can help you protect your data in your own home. It makes it more difficult for hackers to grab your information, keyloggers to swipe login credentials, and even cookies to remember you the next time you visit a website.
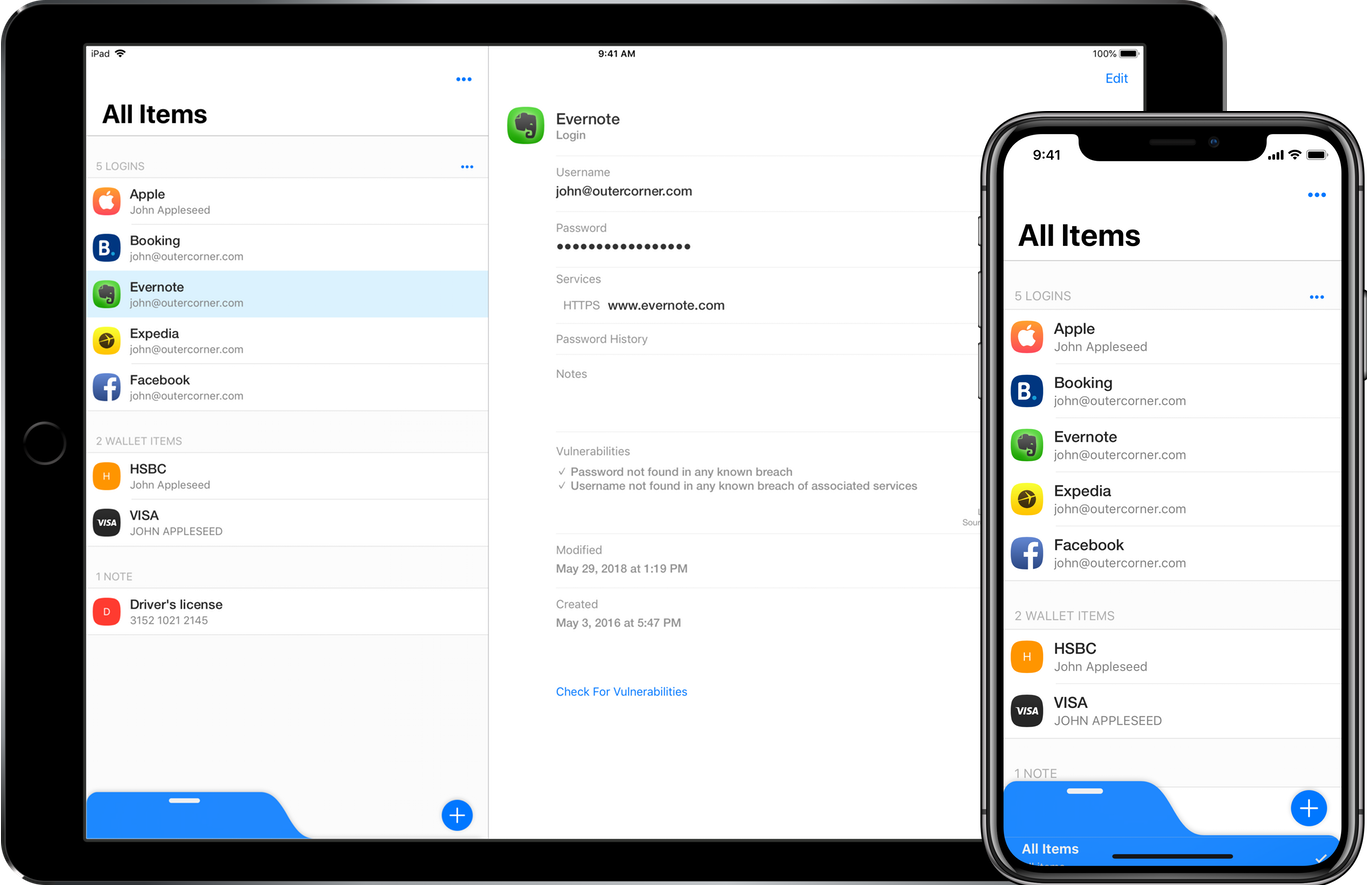
4. Use a password manager
Password managers are handy to have because they are a safe place to securely keep all your passwords to every account. When a hacker breaks into your device, one of the first things it looks for is a sticky note or Word document with your login credentials. This allows them to break into social medial accounts, online banks, and credit card sites in order to swipe personal and financial information.
With the right password, a cybercriminal could easily change your authorization information to their own, making it very difficult for you to log in and change your credentials. A password manager uses encryption to make it difficult for hackers to get your login information.
You can use a good password manager to quickly log into any online account. But it will also help you create passwords that are difficult for hackers and bots to figure out. With most people using birthdays, family members, or even pet names as passwords, it doesn’t take long for a bot to crack an easy password. But a password manager helps you create a difficult one and keeps it where you can get to and use it without having to write it down to remember.
5. Sign up for identity theft protection
Identity theft monitoring and identity theft protection are often used interchangeably, but there are differences between them. Both are helpful, though one is more comprehensive than the other.
ID theft monitoring looks out for your digital identity more than your physical. This includes the buying and selling of your email addresses, passwords, and phone numbers. Some services, such as Have I been pwned are free to use, though they are a bit limited. It won’t tell you exactly who, what, or where the breached information was found. And you have to do all the leg work in order to protect yourself going forward, including changing passwords, or adding your phone number to the National Do Not Call Registry.
Identity theft services take extra steps to help protect your identity, including tracking your physical identity, These services look at criminal records, medical records, and financial information to make sure someone other than yourself isn’t using your information.
If there has been a data breach and your information has been compromised, identity theft services will walk you through every step to help reclaim your identity, including providing the proper forms to fill out and submit to tax authorities and credit reporting agencies.
Or you can get an all-in-one solution
You can purchase each of the tools mentioned above as stand-alone programs. but it is possible to find software that combines all of them in one place making it easier to use them, and often, cheaper than buying them separately. These solutions are referred to as internet security suites.
For example, Bitdefender Total Security is a complete computer protection program that includes a VPN, password manager, and anti-phishing scheme tools. Buying Bitdefender will save you hundreds compared to buying each tool individually.
The same is true of Norton 360 with LifeLock . On top of password managers, a VPN, and email monitoring, Norton also includes access to one of the leading identity theft services, Lifelock. It monitors both your physical and online identity and helps you restore your identity if compromised.
Other all-in-one solutions to consider include McAfee+ Ultimate and Avast One Premium.

Nikki is a commissioned editor for Future Plc covering internet security including antivirus and VPN. With over 18 years of research and writing experience, and 11 years of testing and reviewing internet security solutions, Nikki knows how to dive deep to get the information consumers need to make better buying decisions. She is also a mom to 10 children, and personally uses many of the products she reviews to ensure the safety of her own family.