How to protect your data when traveling
Don't compromise your security

How to protect your data when traveling
While officials usually need a warrant to invade your privacy and search your devices, border check points operate in a legally grey area. Warrantless searches have been found to be legal when entering the USA for instance.
In this guide we'll explore ways to keep your data safe across borders. Bear in mind that some countries have laws which require you to hand your device passwords over and refusal can lead to you being detained or denied entry altogether. Explore your options to make sure that you can both stay within the law and keep your data safe.
- Get rewards for your next trip with the best credit cards for travel (US only)

1. Unplug
Your simplest and most effective option to protect your devices from being seized is not to bring any.
Once you have cleared Customs, you can either buy or rent a device in your destination country. This may not be suitable for places where technology is expensive or difficult to get hold of.
If you have no phone or laptop, your friends and colleagues also won't be able to contact you as easily. Consider buying a basic prepay phone and SIM card at the airport so you can stay in touch or contact them via a pay phone.

2. Restore from Cloud
If you don't want to unplug altogether, consider backing up your data to the Cloud then resetting your device. Even if your device is seized it will be almost impossible to recover your personal data. Once you're safely cross the border, you can then re-download your information.
Apple devices lend themselves particularly well to this as you can back up and restore data from iCloud. (See our guide on how to back up your iPhone and iPad).
For computers, install a cloud storage client. Check out our roundup of the best cloud storage providers of 2017 if you need help with this.

3. Encrypt and authenticate mobile devices
If you don't trust your data to the cloud, you can encrypt your device so that no one can access it without the correct passcode. Apple devices such as iPhones do this by default. See our guide on how to do this for Android devices.
If you're worried you'll be forced to hand over the password, set up Two Factor Authentication on your Apple or Android device but leave your SIM card with someone you trust. Without both the 2FA code and your passcode, no one can sign in with your Apple ID/Google Account.
4. Use plausible deniability
While you can encrypt your devices to make data irretrievable, anyone inspecting them will know you have something to hide, even if they don't know what it is.
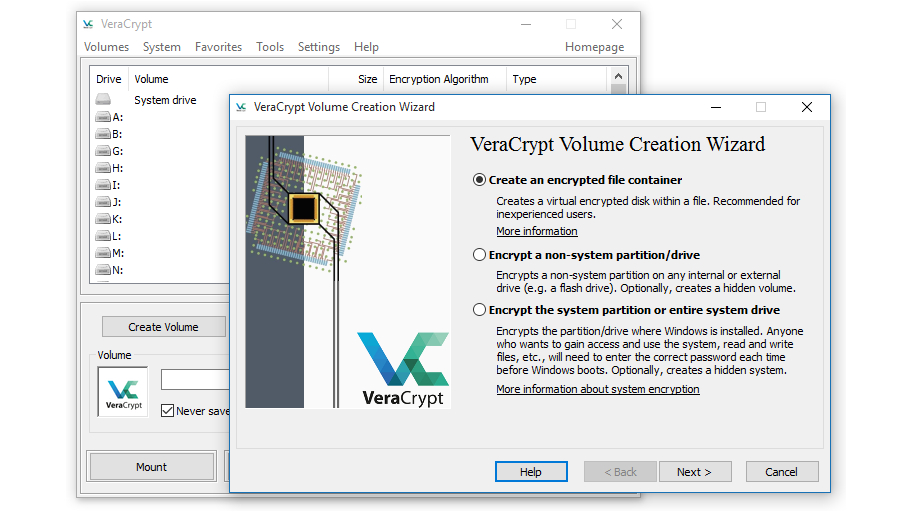
Certain computer encryption programs such as Veracrypt offer a solution through plausible deniability.
Essentially this involves creating two passwords for an encrypted drive. One will display an 'outer' volume into which you can place some plausible dummy data. The other password reveals your 'hidden' volume which you use to access your real information.
Plausible deniability can be tricky to achieve in practice, see Veracrypt's website for more information on how to set this up.

5. Snail mail
While border checkpoints may operate in a legally grey area, many countries have much stricter rules about sending items by post. In the US for instance, many categories of mail can only be searched with a valid warrant.
If can afford the courier fees and have someone you trust in your destination country, you can mail a cellphone, USB stick or even an entire laptop and retrieve it on the other side.
Consider wiping or encrypting your devices before mailing, so that if they're intercepted your data will still be safe.
Nate Drake is a tech journalist specializing in cybersecurity and retro tech. He broke out from his cubicle at Apple 6 years ago and now spends his days sipping Earl Grey tea & writing elegant copy.