How to protect yourself online
Anticipate and respond to threats before they happen

Stay safe

2017 was the year of ransomware according to the Kapersky Security Bulletin, with 26.2% of those targeted being business users, and one in six of businesses that paid the ransom not recovering their data. There were multiple ransomware outbreaks, including WannaCry, ExPetr and Bad Rabbit.
In other cyber threat news the KRACK vulnerability was discovered, leaving wireless network encryption exposed, and users waiting for patches. Finally, early this year, our CPUs were discovered to have security holes via the Spectre and Meltdown vulnerabilities.
As well as reviewing last year's cyber attacks, and discussing the lessons that can be learned, the Kaspersky Security Bulletin also predicts some likely threats for the coming year.
The bottom line is that it's a cybersecurity jungle out there, but by following a few simple tips you can maximize your business's chances of making it unscathed.
1. Update Update Update

For 2017, the Sans Institute documented a number of online security threats, including phishing, ransomware, and DDoS attacks. The most common mechanism of entry of the malware was through users clicking on a link or opening an email attachment.
Updates are issued to try and minimize the vulnerability of systems, but many users don’t bother to install the latest version of their operating system and so aren't getting the benefits of the latest security updates. Turn on Automatic Updates in Windows and on your Mac to stay safe.
2. Maintain your Airgap

Sophisticated malware like that used in the ProjectSauron cyber-espionage platform will often make use of network-driven backdoors. These can sit benignly in a computer system until activated remotely.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
In December 2015, tech giant Juniper Networks made the shocking announcement that it had found unauthorized code embedded into its firewalls which could potentially allow attackers to take control of their systems.
Rather than scan your OS’s code line by line, employ an airgap. Any truly sensitive data will then be stored on a device that is not connected to the internet, protecting it from network backdoors.
However, more recently, techniques including Magneto and Odini have been able to extract data from an air-gapped computer via the magnetic field frequencies of the machine, with the appropriate malware installed.
3. Backup

According to Kaspersky, 2017 was the year of ransomware, with three ransomware epidemics garnering attention: WannaCry, Bad Rabbit and ExPetr.
While traditionally there has been a certain honor among thieves when it came to unlocking machines, at least in some cases victims' data was not decrypted even following the payment of the ransom. In fact, ExPetr does not even have any integrated mechanism to identify victims, so there's no way for them to be provided with a decryption key.
Use the backup and restore features available in both Windows and OS X to avoid being extorted. When backing up be sure to use a separate, external drive to store your files, and keep it off-site when it's not in use.
Our TechRadar guides show you how to back up your device:
- How to back up your Android device
- How to back up your iPhone or iPad
- The ultimate guide to backing up your Mac
- The best free PC backup software
4. Lock down your IoT devices

In October 2016, more than 80 major websites were forced offline in a DOS (Denial of Service Attack) using hundreds of enslaved 'internet of things' (IoT) devices. A Chinese Electronic component manufacturer later sheepishly admitted that its devices, from CCTV Cameras to digital recorders, had been hijacked to form a huge slave network.
More recently, in December 2017, 360 Netlab described a new family of malware, which has been named Satori, and covers three variants. This Satori malware has been used to exploit a zero-day vulnerability on home routers.
Contact the manufacturer of your devices for help with changing the default password. Make sure to use a secure wireless network for your IoT appliances, ideally one secured with WPA2-PSK (AES), and keep your router’s firmware updated, and only with firmware directly obtained from the manufacturer.
5. Stoke your firewall

In January of this year a vulnerability was discovered in Cisco's Adaptive Security Appliance (ASA), one of the most widely deployed SSL VPNs on the market. It was discovered that hackers could penetrate the Secure Socket Layer (SSL), and remotely reconfigure the box to run code, which Cisco has designated a critical issue. Firewall manufacturers will most likely continue to discover backdoors in their products.
Consider installing the free and open source firewall distribution IPFire onto a dedicated computer such as an inexpensive Raspberry Pi to be certain there are no hidden surprises. IPFire is designed specifically for people with little networking experience, and allows you to separate your home network and internet traffic into separate 'safe zones'.
6. Advanced Intrusion Detection
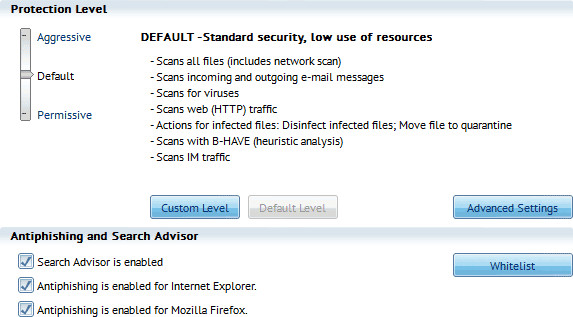
Antivirus databases require continuous updates to remain current. First the viruses need to be identified, then inserted into the database, and the user needs to keep their software up to date. It becomes a continuous game of leapfrog, with users attempting to keep up with the latest malware, but it too often becomes a hopeless effort as databases in some examples go out of date faster than the process can be updated.
One example of this dates back to August 2015, when the hacking group Sofacy launched a cyberattack using its own tool AZZY. Kaspersky countered by updating its virus recognition database. Sofacy responded to this by releasing a modified version of AZZY within 90 minutes which wasn't recognized by the virus scanner.
The bottom line is that in 2018, simple antivirus programs relying on signature based-verification won't be able to detect malware fast enough.
Choose security software which also employs anomaly-based detection, which will block any programs that behave unusually. ClamAV, for instance, is an excellent free, cross-platform antivirus program which uses both types of detection.
7. Turn off tracking

Kaspersky predicts that in 2018 advertisers and malicious actors will step up their efforts to undermine your anonymity through the use of tracking cookies.
This has worrying implications for your privacy if, for example, you visit a life insurance website for a quote and they're able to detect that you recently bought a book about heart disease on Amazon.
Microsoft Edge, Firefox and Chrome users can adjust their preferences to state that they would prefer not to be tracked. Consider also installing a browser extension such as Ghostery to block all trackers.
8. Be more Antisocial

Kaspersky has predicted that in 2018, in addition to advertising networks, vigilante hackers are increasingly likely to target social networks – the best known example has been the use of bots to influence politics and elections.
While you can't control the servers used by your favorite social networking websites, consider carefully what you post online, and make sure to familiarize yourself with the privacy settings of the social networks you use.
Facebook users can benefit from TechRadar’s recently updated article on Advanced Facebook privacy and security tips.
9. Use 2FA
Recent reports have shown that even with 2FA, accounts can be hacked. For example, T-Mobile accounts in the US were recently compromised due to inadequate security precautions that relied on text messaging, which were compromised via the cloning of SIM cards. The hackers' ultimate goal was to steal cryptocurrency.
While it would be wonderful if everyone used a different, complex password for each site, it's not very practical. Major websites like Facebook, LinkedIn and Twitter do however offer two-step verification, which requires you to input a code sent to your phone in addition to entering your password when logging in from a new location.
Although text messages are one option, the state of the art in terms of 2FA is an authenticator app, which is considered more secure as it's not vulnerable to a SIM card cloning. These apps are available from the likes of Microsoft and Google.
- Security Week by TechRadar Pro is brought to you in association with CyberGhost.
Jonas P. DeMuro is a freelance reviewer covering wireless networking hardware.