How to completely uninstall a VPN
Fully remove a VPN and clean up afterwards on your Windows PC

Most VPN providers make big claims about their ‘no logging’ policy, and how they don't maintain the slightest trace of anything you do online.
What these companies don't always explain is that VPNs (including free VPNs) can keep detailed logs on your PC, often including account details, session connect and disconnect times, and the names of any servers you've accessed.
Often there's no automated way to remove this information. Even uninstalling the VPN will usually leave at least some traces behind, and there are plenty more clues to your activities in Windows' various network histories. Most could remain on your system for years.
Whether this is any kind of privacy risk depends on your situation. If others have access to your PC, or maybe you're running a VPN on a work computer, maybe; if it's your own system, probably not.
- We’ve also debunked 6 common myths concerning VPNs
Whatever your circumstances, it's interesting to see what a PC might hold regarding your VPN history. Deleting ancient network remnants brings benefits of its own, too, freeing up resources, simplifying your network settings and maybe reducing the chance of problems occurring with other networking software.
Bear in mind that there are risks involved with this kind of low-level clean-up. Accidentally deleting something important could cripple your PC. Be very careful, and don't wipe anything unless your system is fully backed up, and you've got the tools and experience to recover the computer if anything goes wrong.
So, let’s look in detail at how to go about uninstalling your VPN software and subsequently cleaning up after that process. Note that you don’t have to follow all these steps, at least beyond the first and primary uninstallation process. You can be as thorough – or not – as you like.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
And if you’re not confident with some of the more involved elements – like editing the Registry – then it’s probably best to skip these steps. Furthermore, some of the latter steps will only really apply to those who are extremely privacy-conscious, as you’ll see when you read through.
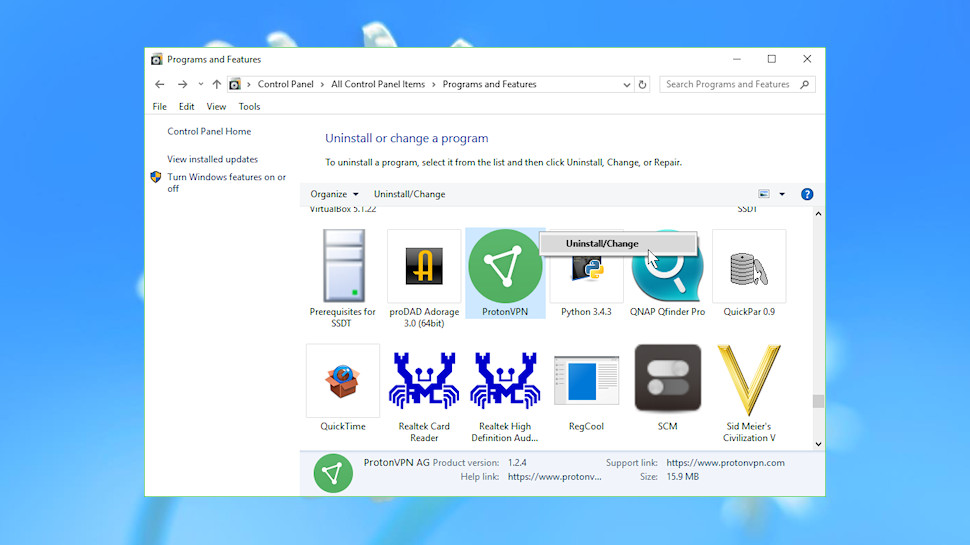
Uninstall VPN clients
The first step in removing a VPN is to clear away its client.
Start by finding where the program files are stored on your hard drive. Open a client window, press Ctrl+Shift+Esc to launch Task Manager, right-click the app name and select Open File Location. Make a note of the folder name – you'll need it later.
Close the client completely (don't just minimize it), then try to uninstall it from the regular Control Panel applet (Control Panel > Programs and Features > Uninstall a Program).
The installed programs list might also include a TAP driver (a virtual network adapter) for your VPN provider. If the list is sorted alphabetically, scroll to the T's and look for items beginning 'TAP-' (our test system included TAP-NordVPN and TAP-ProtonVPN). Remove these by right-clicking and selecting Uninstall.
If you don't find anything, search your system for the VPN name and look for an Uninstall shortcut.
Once you've run the regular uninstaller and removed any associated TAP files, reboot your PC to make sure Windows is able to delete locked program files.
Remove local logs
Uninstalling a VPN won't necessarily remove all of its files. There are often plenty of leftovers, ranging from stray DLLs to detailed logs of all your recent VPN connections.
Open the client folder you noted in the previous step, if it still exists, and search your system for folders with similar names. Investigate these to see what's left, and whether the folders can safely be deleted.
You could also manually browse for files in the most likely locations: \Program Files, \Program Files (x86), \ProgramData, \Users\<username>\AppData\Local, \Users\<username>\AppData\Roaming.
If you don't see the ProgramData or AppData folders, launch Control Panel, go to File Explorer Options and make sure 'Show hidden files, folders and drives' is selected.
It's amazing what you can discover. Even after uninstalling VPNs, we've found folders left behind in ProgramData, with connection information, including BullGuard VPN\logs, Encrypt.me\Logs, Hotspot Shield, NordVPN, PrivateVPN, SafeVPN\logs, SurfEasyService, Surfshark, UltraVPN\logs and VPNArea\Logs.
Depending on your setup, you might have a separate installation of OpenVPN, the open source client used by many pieces of VPN software to manage their connections. Look for a \Users\[Username]\OpenVPN\Log folder and delete any log files you don't need. Which can be all of them, if you like – the files are just for troubleshooting, and it's safe to remove them.

Registry references
Windows VPN clients often store at least some of their settings in the Windows Registry. At least some of these may survive the uninstaller, and they can sometimes give away details of your account or connection history.
Another quick warning here: always be very careful when editing the Registry.
To begin, launch REGEDIT and browse to HKEY_LOCAL_MACHINE\SOFTWARE and HKEY_CURRENT_USER\SOFTWARE. Scroll through each set of keys, looking for anything relating to VPNs that you have uninstalled.
Typically you won't find very much. Our test system had leftover keys relating to ExpressVPN, IPVanish, IVPN, ProtonVPN, SecureVPN and VyprVPN (Golden Frog), but these were all either empty or contained nothing of interest.
Others may be more significant. NordVPN had some IP addresses, Windscribe left all our settings and the last external IP address, and FrootVPN and Anonine left data including our usernames and encrypted password.
Whatever you find, if you're sure it's no longer necessary then you can remove it by right-clicking the key in the left-hand pane and selecting Delete. As we already mentioned, when editing the Registry, be cautious – accidentally deleting the wrong item could cause all kinds of problems. If you're at all unsure about anything, leave it alone.

Network adapters
Windows VPN clients work by setting up virtual network adapters for your other applications to use. These are often left behind when you uninstall a VPN, unfortunately, cluttering your network settings and occasionally conflicting with other software.
Launch Device Manager (press Win+R, type devmgmt.msc and press Enter) and click the arrow to the left of 'Network adapters' to display everything installed on your system.
VPN-related adapters usually include TAP in the name (a virtual network adapter standard) and the service name, which makes them easy to spot. Our test system had 'ibVPN Tap Adapter', 'SwitchVPN Tap Adapter' and 'TAP-NordVPN Windows Adapter V9', for instance.
Our system also had the more vaguely named 'VPN Client Adapter - VPN'. If you're not sure where a network adapter has come from, double-click it, choose the Driver tab and look at the Driver Provider and Digital Signer items. These typically show the name of the service and the company behind it.
As a cross-check, select the Events tab and scroll to the bottom of the list. If the last event was a long time ago this might indicate that the adapter is no longer used, although this isn't guaranteed.
If you're confident an adapter is no longer necessary, and you're also happy you know how to fix the problem if you're wrong (reinstall it, use a system restore point, or something else), right-click it, select Uninstall Device and check the box to 'Delete the driver software for this device.'
- Check out the best VPN
- 1
- 2
Current page: Introduction, uninstallation and registry
Next Page Event logs, system drivers and more
Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided. Mike began his career as a lead software developer in the engineering world, where his creations were used by big-name companies from Rolls Royce to British Nuclear Fuels and British Aerospace. The early PC viruses caught Mike's attention, and he developed an interest in analyzing malware, and learning the low-level technical details of how Windows and network security work under the hood.