How to completely uninstall a VPN
Fully remove a VPN and clean up afterwards on your Windows PC
Event logs
The Windows event logs typically record a vast amount of detail on your PC activities, and these can include basic details of a VPN session: connect and disconnect times, and the VPN server you accessed.
This only applies to native Windows VPN protocols – IKEv2, L2TP, PPTP, SSTP – and the OpenVPN connections used by most VPN clients won't be covered. Anything that is logged will be overwritten after a few days, too, as new Windows events overwrite the old ones. Still, if you're looking to maintain maximum privacy it might be worth checking what's being recorded on your system.
Launch Event Viewer (press Win+R, type eventvwr.msc and press Enter) to begin.
In Windows 10, click Action > Create Custom View. Expand the Event Logs list, then Windows Logs, and check the Application and System boxes.
Expand the Event Sources list and check the RasClient, Rasman and RasSstp boxes.
Click OK, give the filter a name of Connection Events and click OK.
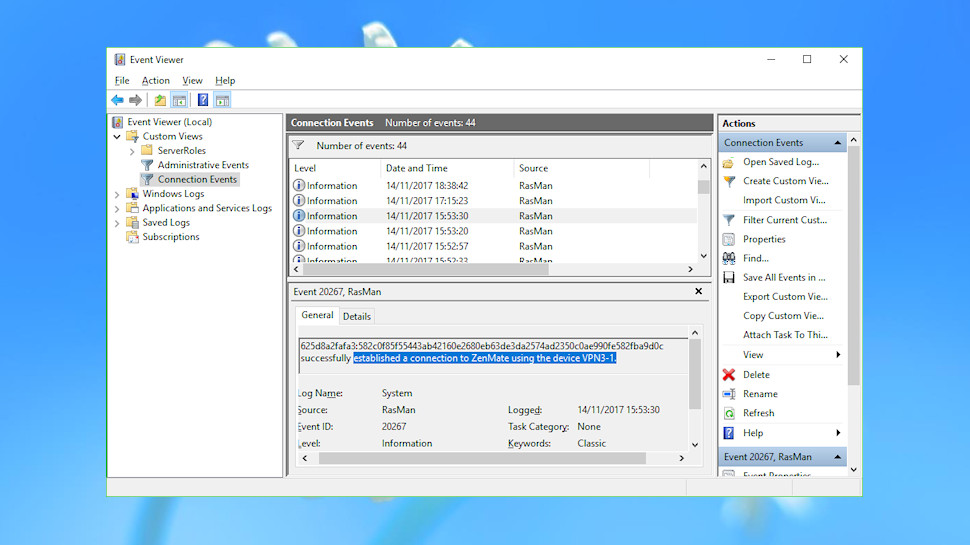
Event Viewer should now add your Connection Events view to the Custom Views section in the left-hand pane, and display all events from the RasMan, RasClient and RasSstp sources.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Now scroll down the list and look at the details of each event.
There aren't any details? Click View and make sure the Preview Pane option is selected.
In some cases you will see RasMan events recording connect and disconnect times for named VPNs over the past few days. RasClient events may go further, including the name of the VPN server you're accessing.
Does this matter? If you're using your own computer, and no-one else has access to it, probably not. But if you're looking for maximum privacy, you can delete this history by right-clicking the Application and System logs and selecting Clear Log.
Firewall rules
Some VPNs add custom rules to the Windows firewall. Typically this is just to ensure they always get access to the outside world, but occasionally they'll also use the firewall to control particular types of traffic.
Usually this scheme works well, but the problem is these rules aren't always removed, cluttering the list and maybe leading to unpredictable network issues later.
Launch the 'Windows Firewall with Advanced Security' applet to find out more (press Win+R, type wf.msc and press Enter.)
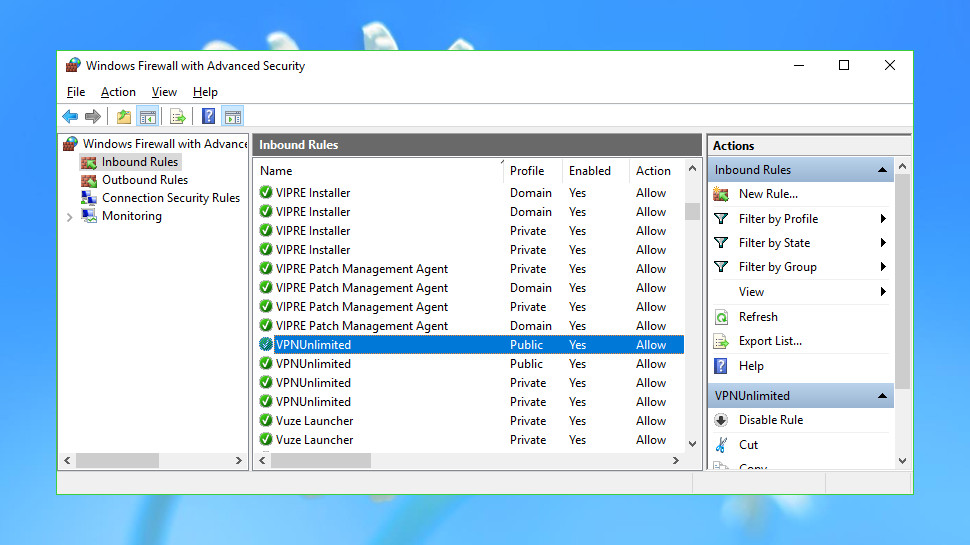
Click 'Inbound Rules' in the left-hand sidebar and browse down the list. If you find a rule relating to a VPN (or any other application) you've uninstalled, and its program file no longer exists, then you can safely remove it by right-clicking and selecting Delete.
Click 'Outbound Rules' and repeat the process.
We found leftover rules for Norton Secure VPN, PureVPN, SlickVPN, Trust.Zone and VPN Unlimited. They were very simple – merely having been set up to allow the client executables to get through the firewall – and they weren't causing any problems. But as the clients had been removed, they weren't necessary anymore, so we deleted them in just a few clicks.
Be careful. Making a mistake here could weaken your security or cause all kinds of odd problems. Don't delete anything that references 'System' or 'SystemRoot' in the Program column, and don't touch anything else unless you're entirely sure it's safe to do so.
Windows network profiles
Windows maintains profiles of some of the networks you access, optionally including your logon details, making it easier to reconnect later.
The privacy impact of this is small, but it could allow snoopers to see which VPNs you've used and when, months or even years after any client was uninstalled.
On Windows 10, press Win+I to open the Settings dialog and click 'Network & Internet'. (If you're on an earlier version of Windows, you can also view your network profiles from the Control Panel 'Internet Options' applet.)
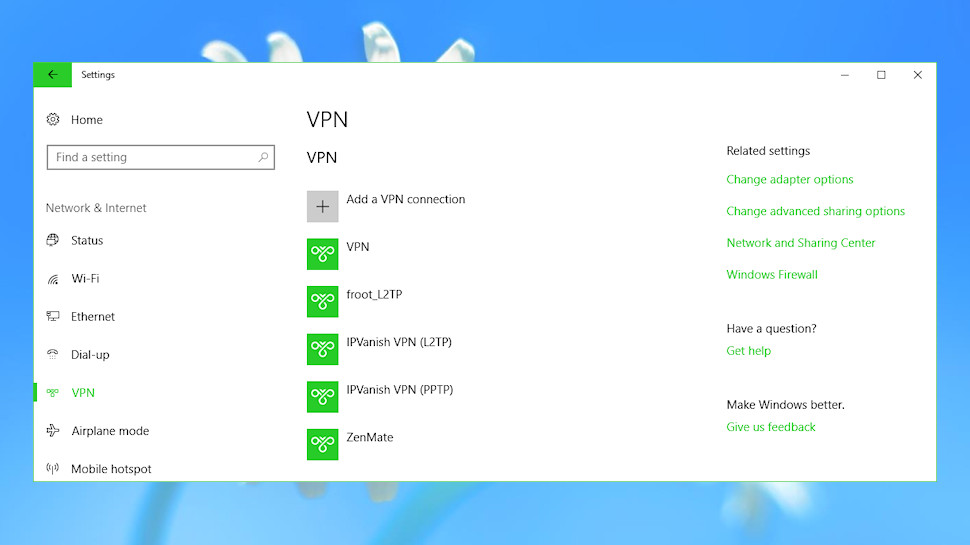
Click VPN in the left-hand pane to view any VPN profiles. These only list basic L2TP and PPTP connections, and as most VPNs use OpenVPN there's a chance you'll see nothing at all.
Most profiles will be easy to recognize. Our test system listed 'IPVanish VPN (L2TP)' and 'IPVanish VPN (PPTP)', for instance, clearly left over from a previous IPVanish installation.
If you're unsure how a profile is used, select it and click Advanced Options. This displays properties including the server name, and optionally the username and password, which may give you some clues.
If you've found a profile which you'd like to delete, click it and select Remove.
This article is about cleaning up VPN records, but you can apply the same principle to remove stored wireless network profiles. If you're interested, click Wi-Fi in the left-hand pane (on Windows 10) and click Manage Known Networks to view and delete stored profiles.
System drivers
Set up a VPN on a PC and it will often install one or more system drivers. Uninstalling the VPN won't necessarily remove the drivers, though, so it could be worth checking out your computer for any leftovers.
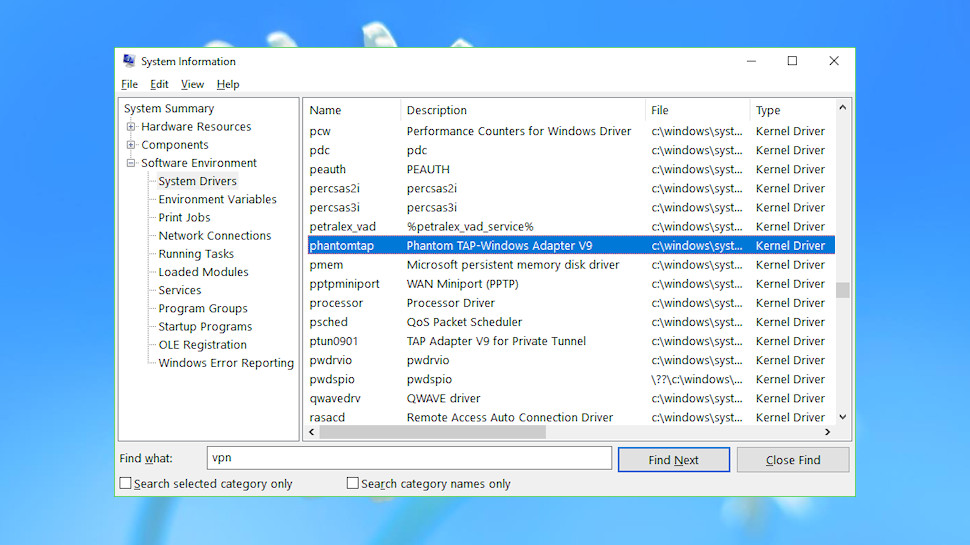
Launch the System Information applet (press Win+R, type msinfo32.exe, press Enter), expand Software Environment and click System Drivers to see the installed drivers on your system. Scroll down the driver descriptions, looking for anything that relates to a VPN you've tried before but subsequently uninstalled.
Examples of leftovers on our test system included 'Astrill SSL VPN Adapter' and 'Phantom TAP-Windows Adapter V9'.
If you find anything, check its values in the Started and State columns. If these show the driver has started and is in the running state, that suggests the VPN has an installed device and perhaps other software. Check our earlier instructions to make sure you have removed any clients and virtual network adapters.
If the table tells you the driver is in the 'Stopped' state, and hasn't started, then that indicates it's not being used right now. The safest option is still to leave it alone, but you can try to remove a driver if you're sure it won't be needed again.
First, open an elevated command line (search for Command, right-click Command Prompt, select Run as Administrator).
Type PNPUTIL -e and press Enter to display all the third-party drivers installed on your system.
Browse the list looking for package providers which match the drivers you noticed earlier, then look for their 'published name'. On our test system, the package provider 'Phanton TAP-Windows Provider V9' had a published name of oem103.inf.
To remove a driver, use the pnputil command with its delete-driver option and the published name. For our example, that meant typing:
pnputil /delete-driver oem103.inf /uninstall
Replace oem103.inf with the published name of your driver, then reboot and check the results.
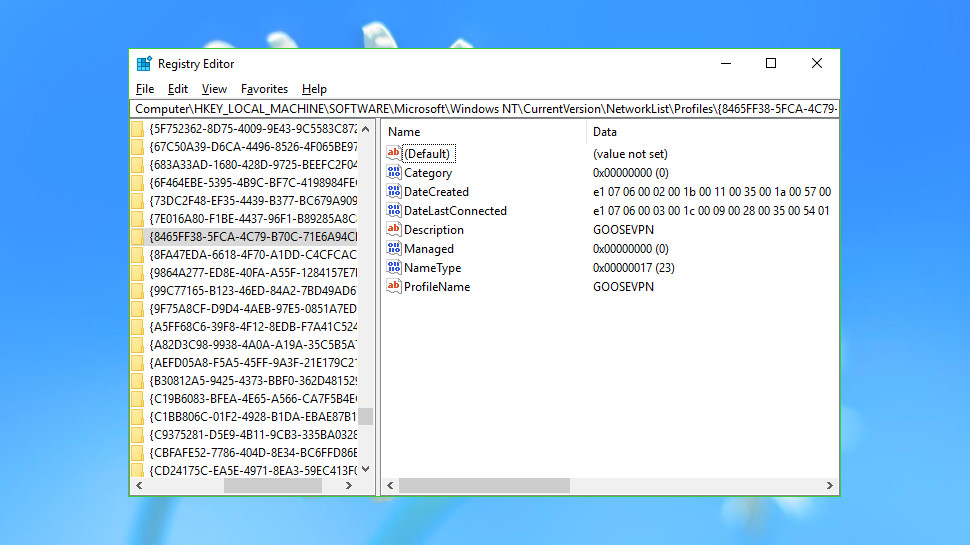
Network history
Windows records some basic details on every network you access, even if it's via a VPN. There's not much recorded – a name, the first and most recent connection dates – and having this information around won't cause you any technical issues. Still, it could tell others a lot about how the system has been used, and if you're really concerned about privacy you might want to clear it away.
Launch REGEDIT, browse to Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Profiles and scroll through the subkeys in the left-hand pane.
Look at the Description value to identify each item. On our test system, some of these represented system network adapters ('Local Area Connection'), others were hotspots we had had accessed ('Premier Inn Ultimate Wi-Fi'), but others clearly belonged to VPNs ('GooseVPN', 'PureVPN', 'IPVanish VPN').
If you see a profile representing a VPN or network you're sure you'll never use again, you can remove it by right-clicking the profile in the left-hand pane and selecting Delete.
A related list at HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Signatures\Unmanaged provides more details on the same networks. Scroll it to see everything you've accessed, check the descriptions, and delete any keys you no longer need.
A final Connections key at HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections records basic connection settings for your regular network adapters and any virtual adapters (VPNs) you might have installed.
It's safe to delete keys for VPNs you no longer use, but be sure to leave the system connections alone. On our test system, these included DefaultConnectionSettings, LAN Connection and SavedLegacySettings, but you may have others, and it's very important they remain untouched.
- Check out the best VPN services
- 1
- 2
Current page: Event logs, system drivers and more
Prev Page Introduction, uninstallation and registry
Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided. Mike began his career as a lead software developer in the engineering world, where his creations were used by big-name companies from Rolls Royce to British Nuclear Fuels and British Aerospace. The early PC viruses caught Mike's attention, and he developed an interest in analyzing malware, and learning the low-level technical details of how Windows and network security work under the hood.