How to use One Time Pad cryptography with a Raspberry Pi
Secure messaging
It has never been harder to be entirely certain that any message you send can be transmitted or received in absolute secrecy.
This holy grail of cryptography has long frustrated security experts, and most people are willing to settle for using encryption programs like gpg, which while theoretically breakable will resist all cracking attempts long after you’re pushing up the daisies.
What if, however, there were a way to be certain that your personal emails, pictures of your pet kitten, backups of your tax returns for the past decade and so on were safe even if intercepted? Enter the One Time Pad.
The Notorious OTP
In simplest terms, a One Time Pad is a series of random numbers which you agree upon with someone with whom you wish to communicate, usually by meeting in person and exchanging pads.
When sending a message, you first need to convert it to numbers, then add each of these numbers to the numbers in the pad. Once the recipient receives the message, they can work backwards using their copy of the pad, deducting the numbers to retrieve your original message.
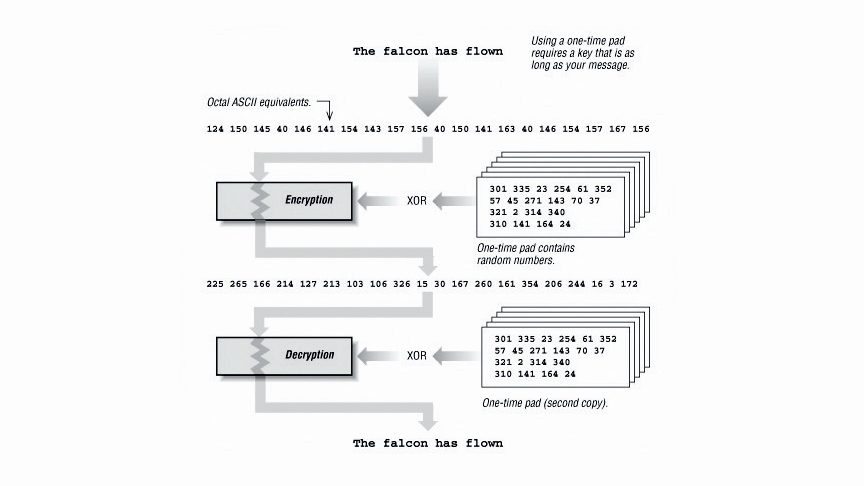
Provided that the numbers are truly random, no one else sees the pad, and the same text isn’t encoded twice with the same pad, then even the world’s fastest supercomputer couldn’t decode the message.
The strength of the encryption lies in the randomness of the pad numbers. Without knowing these, anyone who intercepted a message might see the word ‘LINUX’ encrypted as ‘OSYAJ’ but would have no way of knowing it isn’t another five letter word, like ‘CHILE’.
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.
The One Time Pad has been kicking around in some shape or form since the 1880s but it wasn’t until 1917 that Gilbert Vernam et al formally patented a machine for automating the process.
In this case two reels of punched tape were used, one with the original message and one with the pad of random numbers.
KGB agents in the US were quick to exploit this during the Cold War, placing small pads inside hollowed-out nickels, fake walnuts and any number of dastardly hiding places.
In the 21st century, computers like Raspberry Pi lend themselves well to being carried around easily and are perfect for generating and processing One Time Pads. But in order to understand why, it’s necessary to understand the pitfalls of the One Time Pad.

In order to proceed, you’ll need to have your Adafruit Printer set up and working. Fortunately the website has an excellent guide to this.
First install rng-tools as indicated in Step 1 of the walkthrough on ther next page. You’ll also need to edit /etc/default/rng-tools in your favourite text editor. Remove the # at the beginning of the line HRNGDEVICE=/dev/hwrng. Save and exit.
Use sudo /etc/init.d/rng-tools restart to be certain the Raspberry Pi is using only the hardware RNG now.
Next, download the otp-gen software:
$ git clone https://github.com/iworkinpixels/otp-gen.git
At this stage if you wish you can go into the opt-gen/ folder and run off a sample pad to see what it looks like:
$ cd otp-gen
$ sudo ./otp.py
$ nano otp.txt
Next we need to make sure the software starts automatically when the machine starts:
$ sudo nano /etc/rc.local
Scroll to the bottom of this file and insert the following three lines above the words ‘exit 0’:
$ cd /home/pi/otp-gen
$ ./otp.sh
$ python ./otp.py
If you have downloaded the otp-gen folder to anywhere else besides /home/pi/ then change the first line accordingly.
Use Ctrl+X to come out of the text editor, and press Y to save the changes.
Next use sudo reboot to restart your Raspberry Pi. The printer should print out a message saying it’s connected to the network along with your IP address, then pause.
Simply press the button to generate your own one time pad. Repeat as many times as you like.
Entropy isn’t what it used to be...
Bruce Schneier once described the One Time Pad as “theoretically secure, but... not secure in a practical sense.”
This reflects the fact there have been times that OTPs have been broken in practice despite their theoretical security. In the 1940s, for instance, US SIGINT’s counterintelligence program Venona was able to decrypt a number of Soviet OTP messages simply because some pads had been reused.
This crypto-cardinal sin was committed because the Soviets simply couldn’t generate pads fast enough for the thousands of daily messages sent during wartime.
A similar chink is found by German codebreakers in Neal Stephenson’s Cryptonomicon. The British employ a raft of old ladies with small bingo machines to draw numbered balls to generate pads.
Unfortunately the old dears don’t always obey best practices – they fail to look away each time they draw a ball as instructed, meaning that they subconsciously select predictable numbers.
Fast forward to the 21st century and the issue hasn’t improved much. Entire books have been devoted to this subject but suffice it to say that computers generally aren’t very good at generating true randomness.
Usually when it’s required a website or program will ask you to wiggle your mouse to provide a so-called “noise source” to work from.
Mostly however when a computer requires larger amounts of randomness it will form a string of pseudo-random data from your entropy pool, which, while ideal for determining where the next block will fall when you play Tetris, is less than perfect when it comes to security.
Thankfully one of the lesser known features of the Raspberry Pi is that it has its own built-in hardware random number generator, which in combination with the rng-tools suite can generate exactly the kind of high-quality randomness needed for an OTP.
The second obstacle faced by those using OTP has to do with key generation and distribution. The Soviets were unable to keep up with the demands of war, and in real life the bingo machines of Britain’s little old ladies would probably end up smoking with the number of times they’d need to be churned.

Fortunately the hardware RNG built into the Raspberry Pi can generate large amounts of data in a short amount of time. For instance a pad with 10,000 sets of five-digit random numbers can be generated in seconds by activating the hardware RNG (see step 1 of our guide on the next page) and then entering:
$ sudo base64 /dev/hwrng | tr -dc '0-9' | fold -sw 5 | head -c 10000 > bobtoaliceotp.txtIt’s best before sending any private information with an OTP to send a Challenge-Response message first. Technically you could agree on two code words to use with your recipient: one could indicate that it’s you and you’re able to talk freely – for example, “Everest” – and another could disclose that you’re talking under duress – for instance, “Sparrow”.
This means however that the same text is being encrypted each time, making messages easier to crack.
A better system is to choose from a list of prearranged words or phrases. One way to do this would be to agree on a book – directories and almanacs are perfect types of book for this – and in your “challenge” message you could send an arbitrary page and line.
For example you could agree to use the 1992 edition of Wisden Cricketer’s Almanack. Bob can message Alice saying, “613-1.” Alice can reply with the first line of page 613, which is: “Worcestershire were the only county to win two trophies in 1991.”
She can then add a challenge of her own to the message, for example asking for page 582, line 4.
If of course Alice replies with anything other than the correct words, Bob will know that it’s not her or she’s under duress, and the same applies with his reply to her.
You can further increase the security of this system by agreeing beforehand that the response to the challenge should not be the line requested in the message but the one (say) three lines after, or perhaps the same line on the following page.
The resulting text file can then be printed out, for instance by Adafruit’s thermal printer. This printer has the advantage that unlike most laser printers it doesn’t record the serial number, make or model on each sheet it prints out (on this, see this website).
It also holds up to 15m of paper, which will be plenty for generating long messages. Using this in combination with the excellent program otp-gen, you can print off your own pads automatically at the touch of a button too (see the ‘OTP goes Thermal’ box on this page).
Once the reams of paper are safely printed and tucked away, next comes the issue of physically distributing pads.
This is no doubt the main reason why the OTP hasn’t seen much widespread use. It’s rumoured that the red phone running between Washington and Moscow for instance is secured by an OTP, mainly because both Superpowers are wealthy and melodramatic enough to have men with dark glasses to handcuff themselves to briefcases and swap pads at regular intervals.
Of course if you have printed paper pads, it is possible to mail them to your recipient, but then your OTP would be no safer than a regular letter because it may have been intercepted and copied along the way. The same applies for using regular encryption programs like GnuPG.
The only way to be sure that your pad cannot be intercepted is to deliver it in person. Again the humble Raspberry Pi comes to the fore here because it’s extremely small and easy to carry. Upon meeting the person with whom you want to exchange messages, you can give them a copy of your Raspberry Pi’s MicroSD card or the Raspberry Pi itself.
To ensure perfect security of your messages, it’s necessary to delete pads that have previously been used.
If you have printed yours out, a little tearing off and a Zippo lighter is likely to be helpful here. (Other lighters are available.)
Otherwise running the shred command on the pad you just used should be enough to prevent recovery. Both SD cards and Raspberry Pis are inexpensive also, so if you really feel you have to destroy them once the pads have changed hands, you can do this too.
The low cost of a Raspberry PI is also a great answer to another common criticism, which is that an OTP is usually very difficult to scale beyond two people exchanging messages.
If you do decide to form a secret society, it may be best to designate one person to meet each member and exchange pads regularly. That person can then sit at the centre of the web and act as a clearing house for messages, forwarding them between members as need be.
Even using a Raspberry Pi, however, it is still possible for pads to be intercepted, and communicating can be cumbersome. This is why it’s good to employ some best practices for your OTP.
Nate Drake is a tech journalist specializing in cybersecurity and retro tech. He broke out from his cubicle at Apple 6 years ago and now spends his days sipping Earl Grey tea & writing elegant copy.