How to use One Time Pad cryptography with a Raspberry Pi
Secure messaging
For pen and paper OTPs, although technically it’s possible to convert each letter to numbers (A = 1, B = 2, etc) and then add them to the numbers in the pad, this can be rather cumbersome and it doesn’t allow you to send any special characters.
One very easy way around this issue is to write a message on your Raspberry Pi and then combine it with a block of random data using Karl Fogel’s excellent program OneTime, as explained in the walkthrough below.
If you prefer going old-school, Russian spies used to use a device called a straddling checkerboard to avoid long nights struggling with walnut shells.
Search online for an image of this and you’ll see that, although there’s a lot of variations, the most common letters are typically along the top row, which means they can be enciphered as a single digit.
Less common letters are represented by their row and column – for example the letter C is represented by the number 21. This also allows special characters such as 62, which switches between letters and numbers. The alphabet can be rearranged in any order you like for extra security if you wish.
Another way to save on scribble time is to borrow a trick from thrifty business owners in the 1800s by using codes for common words and expressions – to avoid having to pay for long messages, Bolton’s Telegraph Code for example uses the number 0446 to represent the classic excuse, “The cheque was sent to you in the last post.”
Sadly there is no corresponding code for “It was like that when I got here.” Books like Bolton’s aren’t meant to disguise the meaning of what you say, just to save time. However, if you are going to the trouble of meeting and exchanging keys with a friend, there’s no harm in deciding together your own code names for common people and places.
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.
For instance if the members of your secret society regularly meet by a weeping willow in Hyde Park, you might decide to refer to that location as “Sweden” and to refer to each of the members using animal names.
This would mean that if the decoded message “Meet me with Penguin in Sweden” is intercepted, shadowy government spooks will be left scratching their heads. As you meet to exchange more pads, you can decide on code names for new people and places.
Any OTP system is only as good as the security of the pads, so regardless of whether you use a computer program or paper, it’s important to destroy both the pad and your ‘plaintext’ message once you have sent a message and both the pad and the ‘ciphertext’ message once you’ve decoded any message you’ve received.
If you use the OneTime program in combination with a large file of random data, say 1GB, the program will only use as much data as is needed to encode your files – so a 128K PDF will only be around 128K in size.
Each encoded file records the offset in bytes of those used in your pad, so your contact’s version of OneTime will be able to decode it. Drawing on one very large file, however, means you cannot delete pad data no longer in use without removing the entire file.
This is why it’s best to split your large file of random data into multiple smaller chunks, which you can delete regularly. By default OneTime will prevent you from encoding files with the same random data. See the walkthrough below for more information on this.
OTP also doesn’t have any built-in way to make sure that the person you’re talking to is the person to whom you gave the pads. If you’re using your Raspberry Pi to send and exchange messages, it’s best to use gpg to digitally sign any messages you send.
If you’re using pen and paper, you can use a less secure form of Message Authentication.
Finally, there is no reason that you can’t use OTPs in combination with other forms of security. For instance you can encrypt a zip file with a ridiculously long password and send just the password via OTP instead of the whole message.
In particular the OneTime program encrypts files in text format, so you can place these files on a passwordprotected drive also to boost your security. Feel free to experiment and decide if this is right for you.
How to use digital One Time Pads
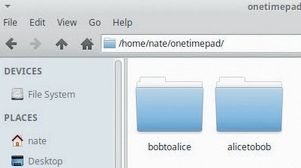
1. Install OneTime and create folders
The OneTime application is available as part of the Debian jessie repository – simply run the following:
$ sudo apt-get install onetimeIf you’re using the Adafruit printer, you’ll also need rng-tools:
$ sudo apt-get install rng-toolsAt this stage you may wish to create a folder for your pads:
$ mkdir -p onetimepad/{bobtoalice,alicetobob}Use cd to go to the first folder, for example:
$ cd home/pi/onetimepadbobtoalice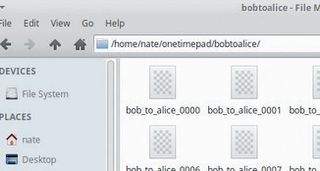
2. Generate random pads
The following commands create a 10MB block of random data, and splits it into numbered 1MB chunks, named bob_to_alice_0009 and so on. Feel free to change the numbers:
$ sudo dd if=/dev/hwrng of=bob_to_alice.pad bs=1000 count=10000
$ sudo split -b 1000000 -d -a 4 bob_to_alice.pad bob_to_alice_
$ sudo shred -uz bob_to_alice.padRepeat this for the “Alice to Bob” pad. Give your contact a copy of both pads.
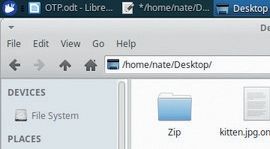
3. Encrypt your data with OTP
Onetime has a simple format for encoding files:
$ onetime -e -p ~/pathto/your.pad yourfile.extSo, for example:
$ onetime -e -p ~/onetimepad/bobtoalice/bob_to_alice_0001 ~/Desktop/kitten.jpg(The file must be smaller than the pad.) You’ll see alongside the original file a file with the same name and the .onetime extension.
Make sure to run the shred command on the pad you just used and the original file.

4. Decrypting OTP messages
Once ‘Alice’ receives your message and has installed OneTime, the command to run is simple, provided she has a copy of the same pads:
$ onetime -d -p ~/pathto/your.pad yourfile.extSo in the example case we’re using:
$ onetime -d -p ~/onetimepad/bobtoalice/bob_to_alice_0001 ~/Downloads/kitten.jpg.onetimeThe decrypted file will appear in the same folder as the .onetime file. ‘Alice’ in turn should be sure to run the shred command on the pad and the encrypted file once decoded.
- Enjoyed this article? Expand your knowledge of Linux, get more from your code, and discover the latest open source developments inside Linux Format. Read our sampler today and take advantage of the offer inside.
Nate Drake is a tech journalist specializing in cybersecurity and retro tech. He broke out from his cubicle at Apple 6 years ago and now spends his days sipping Earl Grey tea & writing elegant copy.