8 reasons why smartphones are privacy nightmare
Beware the spy in your pocket
Our phones have truly become the new personal computer for many of us – in addition to being our primary means of communication we can watch movies, play games and now even enjoy virtual reality experiences on our handsets.
But while smartphones are the epitome of modern convenience, the dirty little secret is that these omnipresent devices, which we have with us 24/7, and keep switched on for most of that time, are also a serious threat to our privacy.
In this guide you’ll find some of the ways that your smart phone can spy on you, as well as some ways you can try to make it safe, short of switching it off altogether.
1. Geotracking

A key feature of a smartphone is being able to locate itself, via multilateration to cell towers, or via the integrated GPS chip. This enables features such as tracking distances during running, and map navigation.
This geolocation information can be quite useful, and law enforcement can track a suspect via their phone. Apps also track users, and can use that information to see which retailers the owner of the phone visits, and the time spent there.
Think disabling the GPS on the phone means you can’t be tracked? Guess again, as there are even reports of locating phones via the other sensors, including the accelerometer, barometer and magnetometer.
Even if you disable these services altogether, law enforcement can also gain a rough idea of your location through tracking the cell towers to which your mobile device has connected. Even the time zone in which your phone’s registered could be useful data to people looking to track you down, as they can examine it at regular intervals to calculate your movements.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
While disclosing location data may seem innocuous, it is still an invasion of privacy. Furthermore, according to Michael Cobb of Computer Weekly, this data can easily be used to build a profile on a user, which can subsequently be used for a phishing attack.
The most common ways to track your movements illegally involve apps containing malicious code. This means your best defense is to install mobile apps only from legitimate sources like the Google Play or Apple App stores.
2. Malicious apps

A great feature about a smartphone is that its functionality can be massively expanded by installing apps, allowing you to build a device with a personalized feature set over time. However, those apps are often not from the most reputable sources – and they may help themselves to more information than is required.
The scary thing is that we willingly provide this when we agree to the app permissions, and we should at least be a little more suspicious why that new game needs access to our contacts, GPS and camera.
It's recommended that you only download apps from more reputable sources, such as the Google Play Store, and steer clear of unfamiliar websites. However, digital security experts RiskIQ found 333 known blacklisted malicious apps at the Google Play Store in a 2017 analysis for the single category of ‘back to school’ apps, so mobile malware is totally everywhere.
Apple users can’t afford to feel smug either. In 2022, cybersecurity researchers from ZecOps discovered a type of malware that fakes an iPhone shutdown, fooling users into thinking it’s been removed.
Apple has also approved apps for inclusion in the official store in the past that contain malware. This said, most often when an iPhone is infected with a virus, it’s been jailbroken. This removes many of the built-in protections in iOS, including being able to install apps from the official Apple store.
The best solution is, where possible, use open source apps. These are programs where the source code has been made available freely online, so security experts and the wider community can check it for bugs or hidden backdoors.
3. Wi-Fi tracking

As cellular connections often falter indoors, retailers have offered free Wi-Fi to their shoppers. Eager to stay connected, these shoppers click to accept the terms of service, and are thankful for the connection, with plenty of modern handsets able to use it for everything including phone calls.
This free Wi-Fi connection, while convenient, is too often in reality an invasion of privacy. US department store Nordstrom hit the headlines when it emerged that it was using a service known as Euclid Analytics to track shoppers . Via the free Wi-Fi, Euclid can determine which departments the shoppers have visited and how long they spent there. While Nordstrom reportedly no longer uses Euclid after a shopper backlash when the tracking came to light, Forbes reports that more than 100 other retailers use their service.
Even at the best of times, public WiFi is dangerous given that other devices connected to the wireless network can try to access yours. This is why you need the best VPN (or a dedicated mobile VPN app) whenever you’re out and about.
Alternatively, simply disable the WiFI feature altogether on your mobile device unless you’re in your home and workplace. You can still access the internet via 4G or 5G.
4. Limited antivirus software
In this day and age, just about everyone accepts that the OS on their Windows or Mac PC needs some additional security, and so they download and install the best anti-virus software.
The necessity of antivirus software is not as clear to most smartphone users, and this is borne out by lower adoption rates of antivirus software on a smartphone compared to full-fledged PCs, despite the amount of personal info many of our phones contain and have access to – 61% of us use mobile banking on our smartphone.
The Google Play Store isn't consistently helpful either, as there are even fake antivirus apps, that are really disguised malware.
Apple has taken a stronger stance against fake antivirus or “antivirus scanning” apps in recent years and has pulled many from the store. Still, if you type “antivirus” into the search bar on your iPhone or other Apple device, you’ll see that not all the apps on offer actually scan for and remove viruses: for instance there are many “cleaner” devices, which might remove old files but won’t necessarily protect you from malware.
To stay protected on the go, be sure to install the best Android antivirus software or the best iPhone antivirus apps on your device.
When it comes to viruses, also remember that prevention is better than cure: the best adblockers can prevent most malicious links from loading in the first place. The good people of AdBlock Plus offer their own browser for Android. iPhone users can also benefit from the built in AdBlock Plus extension for the Safari browser.
5. Your camera could be watching you

Smartphone cameras are a great convenience, and embody the statement that the best camera is the one that you have with you.
Smartphone cameras are also a security risk, however, as they can be activated and used to spy on the owner. Notorious hacker and author Kevin Mitnick explains that this can be done by either installing software on the phone via physical access, or by using the preferred method of security services via remote exploitation.
Google tried to fix this issue by making it impossible for Android devices to start camera recording without displaying a preview on screen first so users would see that it’s been activated. Unfortunately some malware is capable of shrinking this preview to just one pixel across, making it almost invisible.
The same security researcher who uncovered the vulnerability recommended only installing apps from the Google Play store in order to be safe. Android apps also have to specifically ask permission to use features like the camera, so only allow this if you really need it.
The same advice holds true for iPhone users: do not jailbreak your phone to install unofficial apps and make sure to remove those you don’t need. As for Android devices, you can fine tune the permissions each app is allowed, so make sure only to allow camera access to apps that need them.
6. Microphone eavesdropping

Every smartphone has a microphone, and it's another security risk. While the main concern for many of us may be someone eavesdropping on private conversations, microphones also can be used for data collection.
For example, the company Alphonso uses smartphone mics to record the ambient noise of the owners' environments, and then creates a database of TV shows that a phone’s owner has watched, which it then sells this data to advertisers hungry to target ads to those users.
The problem has been made even worse by voice-activated services like Google Assistant and Siri, as the relevant apps need to be listening to you at all times in case you need to ask for anything. In theory, this gives bad actors access to your private conversations, despite Google and Apple’s best intentions.
The only safe way to avoid eavesdropping by voice assistant is to deactivate them altogether in your device settings. When it comes to individual apps, you need to do the same as for the camera. Check individual permissions for each app within your device settings and only enable microphone support if it's absolutely necessary. You can always change these permissions again later.
7. Lack of security patches
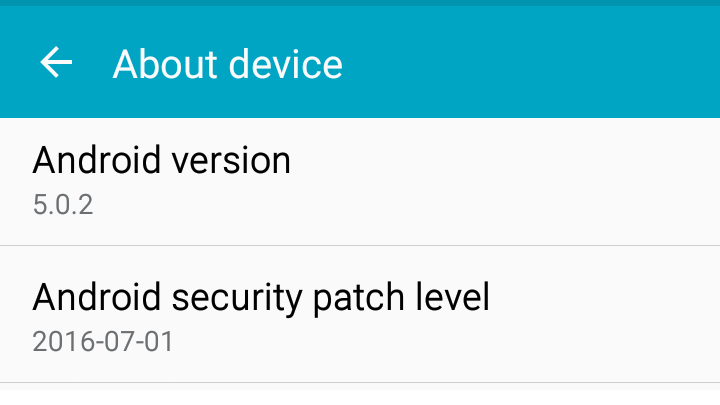
Weekly security patches are a fact of life for Windows users, but when it comes to phones, while things are better for iOS and the Apple camp in general, there's a lack of updates for Android, and not everyone will be running the latest version of Android at a given time.
This has to do with a lack of support in the Android camp, both from the phone manufacturers, as well as the wireless carriers, neither of whom have any incentive to do anything other than sell users something new and shiny.
Not only does an OS go out of date, security updates are also lacking. According to Adrian Ludwig and Mel Miller of Google’s Android Security Team “About half of devices in use at the end of 2016 had not received a platform security update in the previous year,” and therefore should be considered insecure devices.
The situation isn’t helped by the fact that many users in both the Google and iPhone camp fail to update their software or upgrade to a new device when theirs have reached end of life. This may be why Apple released some new security updates for older devices like the iPhone 5S, which will protect against more modern forms of malware.
If you’re running an Android device, make sure to check with your device manufacturer regularly that you’re running the latest version of Android for your particular device. The good news is that the Android 13 should automatically download updates in the background, saving you having to check yourself.
Apple users have a slightly easier time of it, as the company doesn’t have as many devices to maintain. You can upgrade to the latest iOS with just a few taps.
Whatever device you have, make sure to fully charge your device battery and back up all your data before applying any updates or security patches.
8. Beware the backdoor

Most of us would worry about what the government could do if had a ‘backdoor’ into our smartphone, and could access all of our data whenever it wanted to, and this issue became a battle royale when the FBI demanded that Apple help it circumvent an iPhone's security in the wake of a terrorist attack in 2016.
This issue was never really resolved in court as the FBI found another way to get into the phone, so dropped their demand from Apple.
In 2018, the concern is that the Chinese have engineered a backdoor into smartphones from two manufacturers: Huawei and ZTE. This growing uncertainty has led the directors of six US intelligence agencies, including the FBI, CIA and the NSA, to recommend that Americans do not purchase smartphones from these manufacturers during official testimony before the US Senate Intelligence Committee.
In November 2022 the US went even further and banned Huawei and ZTE altogether from the USA. Google also blocked Huawei from accessing Android updates, forcing the firm to create their own version of the operating system.
This is the second time this ban has happened, the first being during President Trump’s presidency. The American Government was apparently concerned that the Chinese government would force these companies to build backdoors into 5G technology.
Whether this is true or not, the manufacturing process behind smartphones is very different to computers and is concentrated in the hands of fewer companies. If a large cellphone manufacturer like Huawei or Apple did agree to include a hardware or software backdoor in their products, it would be devastating for the privacy of millions of people around the world.
Unfortunately the only solution to this is to use a mobile device built on entirely “open source” principles. This is extremely difficult to achieve as most hardware components require proprietary firmware. The only phone on the market to do this successfully currently is the Librem 5 but it’s also expensive and has performance issues.
The Linux-based PinePhone can also be upgraded only to use open source firmware but this is only for experienced programmers.
Jonas P. DeMuro is a freelance reviewer covering wireless networking hardware.