Antivirus jargon buster: online security terms explained from A-Z
Not sure what crypto-jacking is, or a botnet? Find out here

Confused by some of the most-used terms used in the antivirus world? There are certainly some odd sounding abbreviations or bits of jargon which can prompt a bout of head-scratching.
In this article, we’re going to highlight some of the most common offenders, giving you clear and concise definitions of these terms. On with the jargon busting…
- Our definitive list of today's best antivirus software
- Looking for even more protection? Grab the best VPN
- See why we rate Bitdefender so highly in our testing
Antivirus
OK, so you probably don't need this one explaining. Consider it an easy start to this jargon buster!
It's software that you install on to your computer or phone to prevent cyber attacks from stealing your data or infecting your hardware. It can vary from very basic free virus prevention software and malware detection, to all-singing all-dancing internet security suites that pack every defence you can imagine but cost a little bit more.
Botnet
An army of hacked computers (each device being known as a ‘bot’) which can be controlled to act in unison for malicious ends, such as spamming other PCs or engaging in a DDoS attack (as defined below).
Crypto-jacking
This is the name for the process of malware hijacking your PC and using its system resources to engage in mining cryptocurrencies (like Bitcoin) for the eventual profit of the author. This kind of attack can slow down your PC considerably.
DDoS
Stands for Distributed Denial of Service, and refers to the practice of bombarding a target network using multiple devices (sometimes via a large botnet), flooding the target so it’s overwhelmed. In this way, malicious actors can take down websites or services so that you won’t be able to use them while the DDoS attack persists - and where DDoS protection becomes so useful.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
False positive
When an antivirus app flags up something as malicious, and it turns out that the file (or web page, or whatever) in question is actually legitimate, and not dangerous at all, this event is referred to as a false positive, or in other words a false detection.
Heuristics
The process of detecting malware simply based on its behavior (as opposed to the antivirus engine recognizing a threat based on existing definitions). By looking for software or processes behaving suspiciously, in a similar way to already known malware, an antivirus can detect and negate a threat which it hasn’t seen before (such as a zero-day – see the separate definition below).

Keylogger
Although these can be legitimate (albeit niche) programs, in the antivirus world, they are malware which stealthily logs your keypresses, or in other words, spies on you and records everything you type, in an effort to discover sensitive details like your passwords.
Malware
A contraction of ‘malicious’ and ‘software’, malware refers to any kind of software which is specifically designed to do bad things to your device or otherwise compromise your security or data.
Phishing
Phishing is the act of baiting a user to click on a link or attachment in a message (usually an email) to compromise them in some way, often with a malware infection. The message in question usually looks like it comes from a reputable authority or company, to try and trick the user into being more likely to believe it because the content seems genuine.
Pwned
Slang for ‘owned’ (with its alleged origins in a mis-typing), meaning that you’ve fallen victim to an exploit or been compromised in some way. In other words, you have been ‘pwned’, and it’s such a common term online these days that a famous hacking contest, Pwn2Own, is built around ‘pwning’ systems and software.
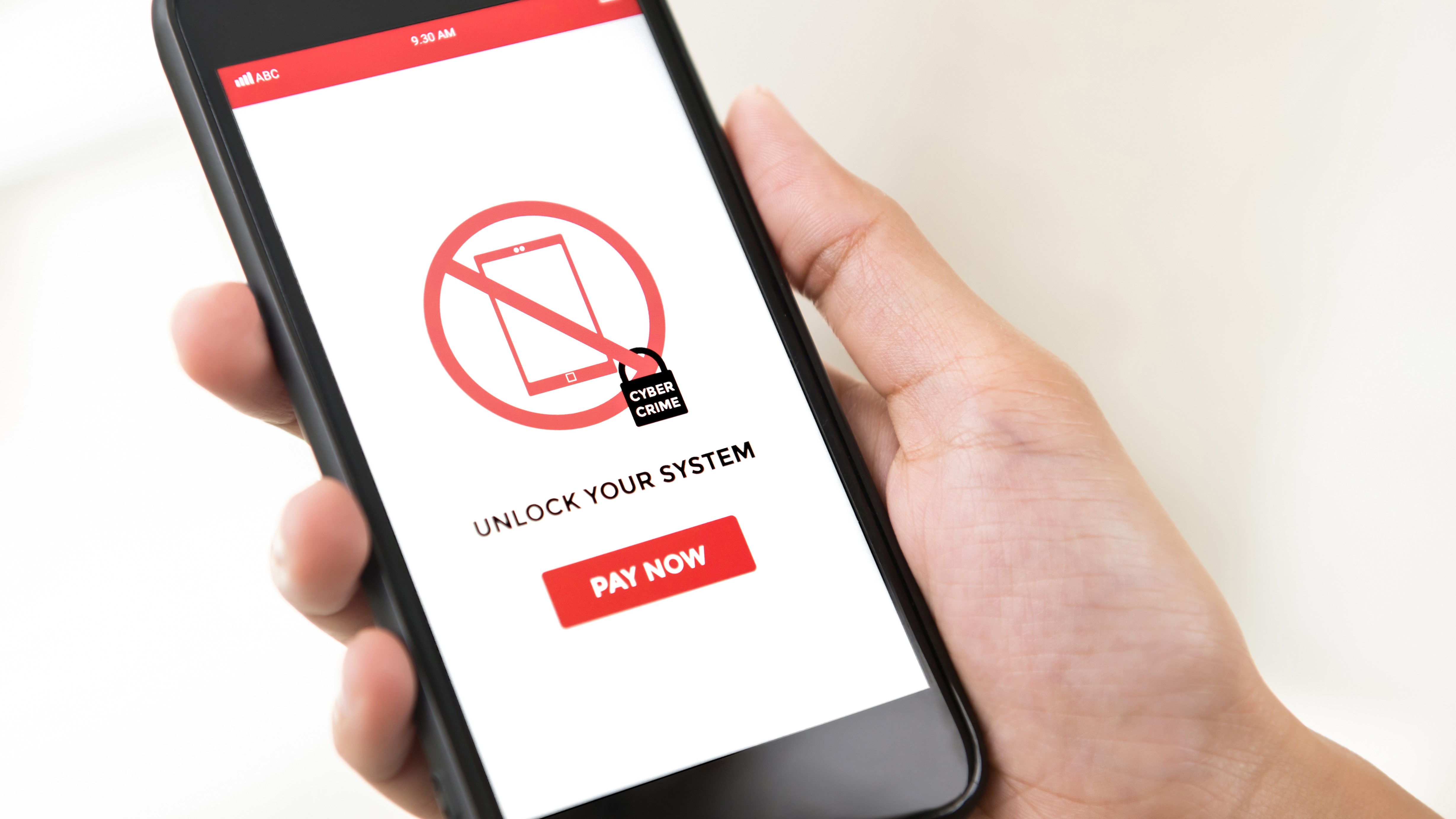
Ransomware
This is malware which stealthily encrypts your files, effectively locking them away from you, and demands a payment for the digital key to unlock them. Even if you pay the ransom – usually in Bitcoin online – there’s no guarantee that the perpetrator will actually decrypt your data, so better to play things safe with antivirus software that includes ransomware protection.
Trojan
Named after the Trojan horse, this simply refers to the practice of creating a piece of software which looks like a legitimate app, but really it’s a carrier for malware. When you run the application, you’ll be infected.
Virus
Antivirus apps themselves are named because they defend against viruses, which is one type of malware – but not the only type (and of course antivirus applications these days protect you from a broad range of malware).
A virus is placed into a file by its author, and when that file is run, it infects the system (potentially doing all manner of nasty things). It usually operates stealthily, in the background, and is designed to spread to other files on your system – the hope of the author being that if those files are subsequently transferred to another user, the virus will compromise them too. And it’ll continue to spread, just like a real-world virus.
VPN
An abbreviation for 'virtual private network', VPNs consist of secure, encrypted tunnels via which all the data you receive and send online travel. The providers use their own servers based in different countries, meaning they can also serve a second function as a way to 'geo-spoof' your IP address. They often come included in more substantial internet security suites.

White hat hacker
An ethical hacker who attempts to compromise systems and find exploits with the intention of informing developers of any security flaws, allowing them to be fixed before malicious hackers can leverage them to nefarious ends. White hat hackers can sometimes be handsomely rewarded with bounties for discovering vulnerabilities that could otherwise have wreaked havoc on a company’s reputation.
Worm
A worm spreads itself in the same way a virus does (as we explain in the definition above), but it’s even more of a worry as it automatically propagates. In other words, the user doesn’t need to click on or run a file to be infected. Wannacry is a famous example of a supremely dangerous worm in action.
Zero-day
A zero-day (or 0-day) refers to a vulnerability which has freshly arrived on the scene. It’s dangerous because its existence has only just been uncovered, and therefore it hasn’t been patched against. The rush is then on to defend against the threat as quickly as possible, before attackers concoct exploits for the zero-day (which an antivirus could struggle to detect, because the threat is new and not seen before – although a good antivirus will hopefully detect it simply based on its suspicious behavior).
- Read more: How to choose the best antivirus for you
Darren is a freelancer writing news and features for TechRadar (and occasionally T3) across a broad range of computing topics including CPUs, GPUs, various other hardware, VPNs, antivirus and more. He has written about tech for the best part of three decades, and writes books in his spare time (his debut novel - 'I Know What You Did Last Supper' - was published by Hachette UK in 2013).