CoSoSys data loss prevention
Centralized data protection for individual endpoints
CoSoSys Endpoint Protector is one of the best data loss prevention services for businesses with computers and servers running on multiple operating systems. This software works on Windows, Mac, and Linux, offering tools to control data transfer to external devices and to keep sensitive data inside your organization. CoSoSys also offers flexible deployment and granular permission controls, which makes it versatile enough for a wide variety of enterprise-scale networks.
Is this data protection company the best choice for your business? In our CoSoSys evaluation, we’ll take a closer look at everything the company has to offer.
CoSoSys: Plans and pricing
CoSoSys doesn’t offer standardized pricing plans for its Endpoint Protector software. You’ll have to contact the company for a quote, which will be tailored based on the number of devices in your network, your deployment needs, and the specific software modules you need access to. Keep in mind that this is an enterprise-scale data loss prevention service, so it’s likely to run upwards of $10,000 per year.
CoSoSys: How it works
CoSoSys offers three ways to deploy Endpoint Protector across your network. The simplest option is to use an Endpoint Protector Hardware Appliance, which is a dedicated server stack that can be used to push the software to devices across your network. Alternatively, you can install Endpoint Protector on an internal server using a virtual appliance. Virtual appliances are available for most common virtualization software platforms, including VMWare, VirtualBox, and Hyper-V Manager environments.

Endpoint Protector is also available as a cloud application. The software can be installed within an existing cloud space through Amazon, Microsoft, or Google. CoSoSys can also host Endpoint Protector on its own cloud if you prefer a SaaS arrangement, although this can be more expensive in the long run.
CoSoSys: Features and services
CoSoSys Endpoint Protector is split up into several modules, which you can mix and match depending on your company’s data security needs.
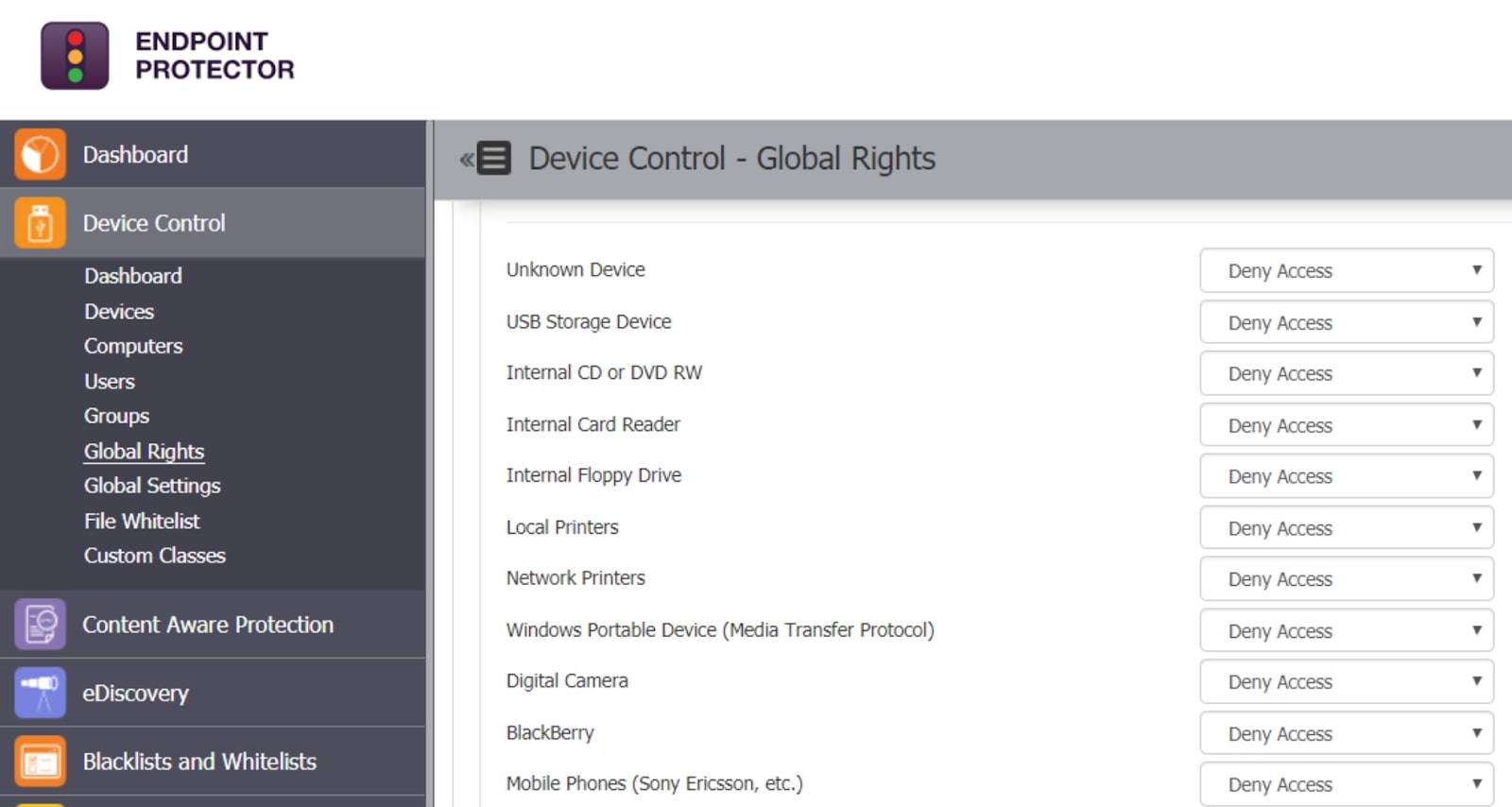
External device control is at the heart of Endpoint Protector. With this core module, IT administrators can remotely scan USB-connected drives in real-time as soon as they are connected to a protected machine. Device data is displayed in the CoSoSys administrative portal and the software records an activity log of all external device connections and data transfers.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
In addition, Endpoint Protector allows administrators to set granular permissions to restrict data transfers to and from external devices. Permissions can be role-based or set for specific types of devices.
Unfortunately, setting these permissions can be time-consuming, since they cannot be seamlessly copied across operating systems. It’s also noteworthy that while the permission settings are extremely advanced, they don’t allow for whitelisting or blacklisting specific file types rather than entire devices.
CoSoSys also supports content scanning for data transferred through common enterprise applications, such as Skype, Dropbox, Google Drive, and Slack. This allows administrators to identify and flag unauthorized data transfers outside an organization. Content scans can be defined using a set of text filters, but CoSoSys lacks automation or machine learning features that could make scanning more efficient.
It’s also noteworthy that the software doesn’t actively prevent flagged transfers; it only notifies data administrators of the problem.
Endpoint Protector can be used to require users to encrypt data when transferring it to an external drive. This is a very helpful feature for working with sensitive data, since it largely eliminates data security concerns in the event that external drives are lost or stolen. Encryption requirements can be modified by IT administrators along with other device-control-related user permissions.
One thing to note is that enforced encryption is only available for Windows and Mac machines, and not for Linux machines.
CoSoSys’s eDiscovery feature scans the files at rest on employees’ computers in order to identify sensitive data. IT administrators can then encrypt or delete that data remotely. This is a critical feature for HIPAA, PCI, and GDPR compliance, since it ensures that critical data cannot be stolen if an individual machine is lost or stolen.
CoSoSys: Support and customer care
CoSoSys offers support seven days a week by phone, email, and live chat. The company’s country-specific offices aren’t open 24 hours a day, but there are offices around the world, so a support team is always available. CoSoSys does have an online knowledgebase for Endpoint Protector, but it is difficult to navigate since it’s not organized by module or topic area.
The competition
Several other data protection companies, including McAfee and Acronis, offer endpoint protection software similar to CoSoSys. Notably, software offerings from both of these companies are available for Windows and Mac endpoints, but not for Linux devices. In addition, they lack Endpoint Protection’s granular level of user access control.
The main reason to opt for either McAfee or Acronis over CoSoSys is that they are significantly cheaper. Acronis, for example, offers multi-device plans starting at $99 per year.
Final verdict
Endpoint Protector from CoSoSys is an extremely powerful software for businesses that need to control the flow of data outside their organizations. The platform can easily be deployed with a pre-configured server or fully customized to fit a cloud environment depending on your organization’s needs. Plus, this data protection company offers granular, role-based user permissions that can help your IT team manage your network.
The biggest downside to CoSoSys is the service’s cost, which can be prohibitive for smaller enterprises.
Further reading
Michael Graw is a freelance journalist and photographer based in Bellingham, Washington. His interests span a wide range from business technology to finance to creative media, with a focus on new technology and emerging trends. Michael's work has been published in TechRadar, Tom's Guide, Business Insider, Fast Company, Salon, and Harvard Business Review.
