Hackers dangle a wide variety of phishing hooks beyond email
Phishing attacks are growing more complicated

A recent report from Barracuda Networks found that 87 per cent of respondents faced an attempted email-based phishing attack in the past year, making it clear that email-based phishing continues to be a major threat vector. But what happens when improved security defences and employee awareness training make email phishing threats less likely to succeed? Well, if nothing else, hackers are smart and resourceful. They just change to phishing tactics beyond email.
Today, most security teams are finally becoming more aware of the large and growing threat of sophisticated phishing attacks that tempt employees outside of email. These new and fast-evolving attack vector targets users with increasingly sophisticated phishing attacks delivered via ads, search results, pop-ups, browser extensions, social media, chat applications, “free” web apps, and more.
Such sneaky socially engineered attacks often appear in an “arena of trust,” like a legitimate website or social media application. They deceive employees into offering up personal credentials or visiting malicious web pages that compromise their browsers and do keylogging and other malevolent actions that are hard for traditional security solutions to detect.
Hackers are preying on human fallibility with HTML-based attacks that evade existing defences by design. Disguised as legitimate web traffic, they slip through firewalls and secure web gateways. And with these new phishing campaign typically lasting just hours, existing threat-based defences can’t keep up with fast-moving attacks. In essence, browsers and browser users are the new OS that need increased protection in order to stop phishing that leads to breaches and other damage.
New types of phishing attacks are on the rise
The growing use of the Web, SaaS applications, social media, and other Internet-based resources for daily tasks is making it an increasingly appealing attack vector for hackers. While employees are on the Web or using social media, they are vulnerable to a growing variety of complex phishing attacks outside of their inbox. And with devices such as laptops and phones increasingly being dual use devices, used for both business and personal use, compromises that take place during personal time can compromise a device and help hackers gain entry into corporate networks.
Here is a brief roundup of the most common types of phishing attacks beyond email on the rise today, and why organisations should be on the alert.

Fake logins and credential stealing
It starts out looking real enough. You search for a login page for your Facebook, Google, or Dropbox account at work and come across what appears to be a legitimate page, so you enter your credentials into the phony login. This mistake makes you fair game for attackers to steal your info and get access to your critical files and passwords, and possibly even infiltrate the larger corporate network.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
In the example below, attackers provide a custom Dropbox phishing page that allows users to gain access through the trusted email login source of their choice. Regardless of the selection, once the user enters his or her credentials in any of the above logins, the form will submit the stolen information through a php script of the same name as the popup htm. In each php, the attacker has written a code to send the collected information to this email address.
Malicious browser extensions and ads
According to a recent report, Google says it removed 3.2 billion ads from its platforms in 2017, nearly double the total number of “bad ads” from just a year earlier. That equates to removing about 100 ads per second.
Google also reported that cybercriminals infected more than 100,000 computers with browser extensions that stole login credentials, mined cryptocurrencies, and engaged in click fraud. The malicious extensions were hosted in Google’s official Chrome Web Store. These browser extensions and related HTML malware are often promoted via ads, search engines, and social media to trick users through increasingly sophisticated and trustworthy social engineering methods.
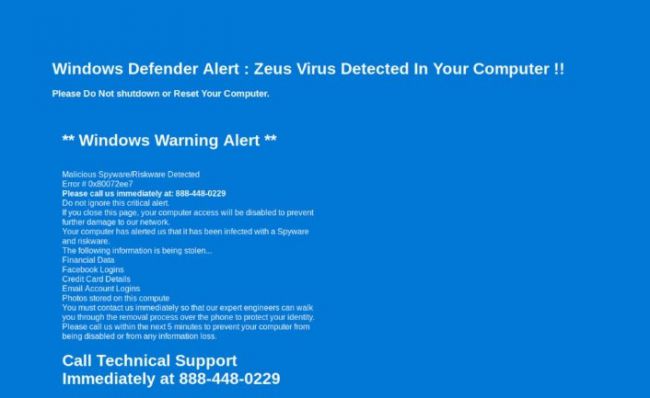
Tech support scams
Tech support scams use scare tactics to lure users into providing their information via phone or a web page, warning of data loss or irreversible computer damage. In the case below, when this URL is opened in a browser, it redirects to a scam page. This page plays loud audio (using text to speech) to say that your computer is infected with a virus and warning that you must call technical support immediately for removal of this virus. It also tells users to not turn off their computers or their important information stored on the computer (i.e. financial data, credentials, photos, etc.) can be stolen.
Rogue Software
Researchers at ESET have uncovered fake flash player attacks that are targeting embassies and consulates in eastern European post-Soviet states that have been attributed to Turla, a well-known advanced persistent threat group.
These type of phishing attacks usually trick users into downloading fake system cleaners and anti-virus tools by showing fake infections and malware activities on their computer or device. In some case, these types of phishing attacks lure their victims into installing fake videos players in an offer to watch a cool video. These attacks fundamentally try to exploit the users’ trust in global brands, with the end goal of getting them to unwittingly introduce socially engineered malware onto their systems. Increasingly, these are HTML-based malware that execute entirely within the browser’s memory. With no file artifacts or .exe files to examine, these attacks often elude AV and endpoint protections.
Games and prizes
Who doesn’t love online games and easy to enter contests? The potential victims get a sense of excitement and are willing to give up sensitive information just to claim a reward.
In a recently observed type of attack, the victim is promised one of several possible prizes – just spin the wheel to see what you will win. After spinning the wheel, the user will be asked to log-in to Facebook to claim a prize. However, the Facebook login page is fake and under control of the attacker. The purpose of the scam is simply to capture the user’s Facebook login credentials. Those credentials open the door for a subsequent attack on Facebook or many other personal and business systems which accept a Facebook login.
How to fight the evolving phishing threat landscape
As email phishing still poses a significant threat, that’s where the money keeps going to develop and deploy security tools at the corporate level. But increasingly the bad guys are realising it’s easier to get through defences of companies to phish users with tactics beyond email.
Security professionals and IT practitioners need to start thinking differently about how the phishing landscape has changed and what this means for their security strategy. The browser has truly become the new OS, and both the browser and users need increased protection from the growing number of phishing attacks beyond email. The solution for more effective phishing threat detection lies at the intersection of computer vision, OCR, NLP, and state-of-the-art machine learning to achieve truly effective and adaptive phishing threat detection capabilities to protect employees.
Atif Mushtaq, CEO of SlashNext
- Also check out the best antivirus