Hook, line and sinker: how to detect and protect your business from phishing attacks
How can you protect your organisation against phishing and other constantly evolving cyber threats?

If you received an email from one of your trusted subscription accounts informing you that someone has tried to log in using your details, and therefore urging you to update your password and personal information, would you question its legitimacy? Probably not if the email seemed authentic, with the recognisable company logo, and follow through link incorporated. After all, the company is going out of its way here to inform you, so you can protect yourself.
Or could it be alerting you to a potential phishing attack? At first glance the email may appear helpful and trustworthy, but it may not be as it seems. For example, look at the screenshot below:
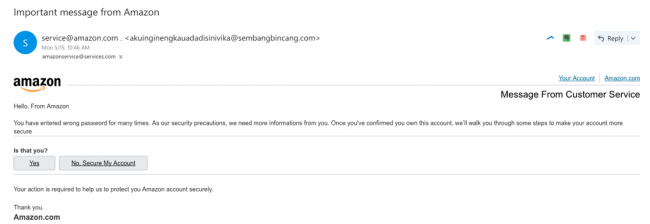
There are always a few tell-tale signs which reveal this as a classic phishing attempt: the correspondent’s email or web address is different to the genuine organisation’s address, clumsy spelling and grammatical errors are littered throughout and a non-specific greeting is used. Yet, despite worldwide increased spending on cybersecurity, phishing attacks remain a big problem. Inboxes continue to be cluttered with fake emails and scams trying to trick individuals into giving away their credentials.
More must be done to stop organisations falling victim to phishing scams, but not enough people are aware of what they are, how to spot them and how to critically close security gaps. It is time to change this.
So, why do phishing attacks still exist?
The concept of phishing is nothing new. Tricking individuals into handing over their credentials remains an old, but extremely effective scam that continues to work wonders for cyber criminals. Once records of data are stolen, the security advancements of the last 20 years can be easily evaded by using such minimal details. After all, it is difficult to tell the difference between a genuine login attempt and a malicious actor using valid, yet stolen credentials.
Large corporations such as Yahoo, Uber, eBay and more recently Dixons Carphone have all experienced a data breach where stolen user credentials ended up on the dark web. In the case of Dixons Carphone, the breach involved 5.9 million payment cards and 1.2 million personal data records being stolen. Therefore, it should come as no surprise that a recent report revealed that 81 per cent of data breaches involved weak, default or stolen passwords.
With stolen credentials an attacker can gain access to an account or system, establish a foothold, escalate privileges and move laterally to complete their mission. By sending emails with attachments that contain malware that records keystrokes to an unsuspecting user, attackers can log back into the corporate network to search for more valuable data.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Moreover, the attacker may use the compromised account to send an infected email to another employee, with the intent of harvesting their credentials for further prohibited activity. This opens up yet another weakness. Tech-savvy employees may be smart enough to spot a scam email or avoid opening an attachment from someone they don’t know, but when a corrupted email comes through from a trusted employee, it’s harder to detect.
156 million phishing emails continue to be sent out daily, but people are still unaware they are being targeted. At the same time, attackers are using more clever tactics to trick the user into thinking emails are from legitimate sources. While we may not be able to avoid receiving such emails, there are simple signs to look out for, so we can prevent ourselves from falling for such scams.
What can a phishing attack look like?
Attackers utilise a range of tactics that are designed specifically to exploit trust and can take a range of forms including:
1. Mimic Attacks
As bad actors know that legitimate brands are trusted, they will act to mimic actual websites and emails. These can include a brand’s logo and preferred format in order to trick users into entering their credentials on a spoofed page.
2. Legitimate email attachment or malware?
Many emails received from family, friends or co-workers often have an attachment and it is difficult for email applications to determine which of these attachments is real and which carry malware. Through social engineering, bad actors can access information that only a friend or co-worker would know, to appear more trustworthy in their communications.
3. Spear/Whale Phishing
These attacks are extremely targeted to people in the network, with ‘whale phishing’ referring to attacks on individuals with highly privileged access credentials. In either case, the attacker is looking to find enough information to appear more legitimate and trustworthy, so that malware is accepted by either a click, a download or by entering information.
How can we avoid a persistent threat like phishing?
While there is plenty of guidance on best password practice and how to spot a phishing attack, username and passwords are essentially obsolete. What businesses need is an efficient and effective approach to security that protects the user and the business, while not hindering user experience. Adaptive authentication dramatically improves security – more so than two-factor authentication – and is non-disruptive to users’ workflow. By combining techniques such as geographic location analysis, device recognition, IP address-based threat services, and phone number fraud prevention user validation can be achieved in a way that is invisible.
Performing security audits such as penetration testing allows security teams to evaluate the security of the infrastructure, finding vulnerable and exploitable environments. By emulating real tools that real attackers use to infiltrate an environment, security teams know where they need to perform an incident response plan.
Organisations should incorporate a company-wide policy to limit user privileges in the event of any suspicious activity and develop a clear strategy on what to do if they suspect their device has been infected. Updated email filtering tools and security malware defences should be made mandatory by businesses for all devices, including BYODs. Ongoing IT support for employees unsure about any suspicious emails should be provided and instate automatic patching.
In addition to technical solutions, user education and awareness programmes including Internal phishing campaigns, should be carried out to all at risk employees. The ability to feed the output from those campaigns into the authentication process, allows an organisation to increase the authentication around those users who appear to be more at risk. Ongoing user awareness and education programmes allows an organisation to adjust the end user authentication process, based on the output from activities such as an internal phishing campaign.
How we can close those critical security gaps?
It’s unlikely that phishing will disappear any time soon, as it is such a cheap and effective strategy. More can be done to stop and prevent such attacks and by bringing identity and security together, breaking down silos, having a holistic approach to cybersecurity, attackers can be prevented from gaining a foothold in the business.
With all the disparate technologies that could potentially be used, identity and security automation becomes crucial to mitigate risks, detect breaches, and protect the most valuable information in an organisation. By bringing together network, endpoint, vulnerability, and identity and access management, rather than treating them as separate tools, weaknesses caused by disparate architectures can be removed. This, in turn removes those blind spots previously exploited by malicious attackers to gain a foothold.
Phishing is constantly evolving to adopt new forms and techniques, but with a modern approach, security teams can dramatically narrow the threat surface area and secure the organisation, regardless of the stealthiest phishing attempt.
James Romer, Chief Security Architect EMEA at SecureAuth + Core Security
- We've also highlighted the best antivirus
James Romer has over 21 years of experience in the IT industry and identity security. He joined SecureAuth 4 years ago and is responsible for the technical consultancy aspect of the business advising prospective clients on authentication access. Prior to joining SecureAuth, James was the solution consultant / EMEA technical pre-sales manager at Courion Corporation and prior to that Senior IAM Consultant at Salford Software. He has over 21 years of working experience.
