
Gone are the days of the lone teenage hacker breaking into computers for fun. Botnets are the only game worth their time now. Serious hackers with rent to pay have abandoned their anarchic principles to build vast global armies of home computers – perhaps even including yours, or that of someone you know.
Cloaked by increasingly sophisticated security, these so-called botmasters dodge justice to claim bragging rights from their peers – and, of course, to make a fortune by renting their creations to hardened criminals.
Stealing your credit card and banking details, spamming, phishing, extorting money through DDoS (distributed denial-of service) attacks and even hosting child pornography can all now be carried out with just a few mouse clicks. Depending on the payload that's downloaded to each of the enslaved 'zombie' computers, these activities are only the tip of a growing iceberg.
While a botnet's zombie software may take only tiny amounts of your CPU's time, individual botnets are becoming so huge overall that some experts are starting to seriously worry about the sheer power that botmasters are making freely available for criminals to rent.
"In terms of power, the botnet utterly blows all of the supercomputers away," says Matt Sergeant of MessageLabs. What's more, sophisticated construction kits are now being packaged into point-and-click products, ready for use by non computer-literate criminals to build their own botnets.
A growing market for add-on packages that can expand a botnet's functionality is also developing, and botnet software that can even replace one infection with its own is already in the wild.
The state of the art in malware design has never developed faster. And yet judging by infection rates and the sheer amount of stolen information available for sale online, home users are oblivious to the risks they run every time they use the internet. Most have never heard of botnets or botmasters, but with an average detection rate currently standing at around 47 per cent for the most widespread type of botnet software, your computer could be infected right now and you wouldn't know it.
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.
So just who is controlling our computers and how exactly are they making money out of doing so? To find out, we sought out the botnet hunters who fight back.
The scale of the problem
Sitting at his desk at Trend Micro, Rik Ferguson taps at his keyboard. "We've got one vendor here who has 8,000 UK cards in stock," he says, "and they're priced by BIN [back identification number], and they're priced at $10 per card. If you buy in bulk, if you buy 100 cards, you get them for $350. Bank accounts are normally priced at a percentage of the available balance in the account, rather than a fixed price." He then reels off a list of accounts at UK high street banks being openly advertised on the underground forum he's infiltrated.
Calculating how many botnets and zombies there are is very difficult, as Luis Corrons, Technical Director of PandaLabs Security, explains. "Most of the time we cannot know the exact number of bots," he says "If you can gain access to the C&C [command and control] servers, you can see the stats; otherwise you can only guess.
"In the case of [the Mariposa botnet], we believed it was around 100,000 to 200,000 computers. However, once we had the ability to redirect the traffic from the C&C to our sinkhole, we found out that the amount of different IP addresses connecting there were in the millions."
The Mariposa botnet is now known to contain 12.7 million infected computers, and this is just one botnet in a sea of many thousands of others. "Zeus Tracker right now is tracking 1,400 command and control servers of one particular Zeus botnet," says Ferguson.
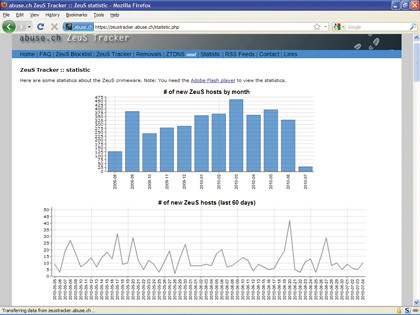
"There are somewhere over 1,000 different Zeus botnets out there, and that's one piece of crimeware. The figures are scary. The number of spam bots – that is, compromised IP addresses that are sending spam which we track – we're tracking about 23 million unique IP addresses. That's just spam bots, so you could say that there's probably a similar number of information-stealing bots out there as well."
The total number of zombies Corrons and Ferguson alone track is near to 60 million, and the sizes of other botnets mean that they already outclass even huge computing facilities.
The massive Conficker botnet easily dwarfs Google's one-million-CPU cloud computing facility, with its mere 1,500 Gb/sec bandwidth. Conficker is thought to contain at least 18 million hijacked CPUs with a total bandwidth of 28Tb/sec. What it does next depends entirely on who rents it, and renting is both very easy and very cheap.
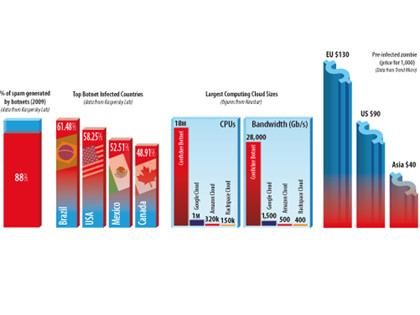
According to iDefense, VeriSign's security intelligence service, an average of $9 (roughly £6) currently buys an hour of botnet time to use as you wish. Just $67 (under £45) will buy you a full 24 hours, and brings the hourly rate down to just $2.79 (about £1.83). The potential payback, however, is absolutely huge.
"Mindboggling sums make their way into the pockets of people in the botnet business," comments Yuri Namestnikov of Kaspersky Lab. "In [2008], spammers made about $780million sending messages. An impressive result for adverts that nobody wants, isn't it?"
"It's now accepted by many that botnets can and do make serious money," agrees Dale Pearson of Security Active. "There have been many under-20s who have set up botnets earning in excess of £30,000 per rental session. Obviously, the amount a botmaster earns is very dependent on the size and processing power of the army they control."
The range of sophisticated uses for botnets makes them the Swiss Army Knife of online crime, as Catalin Cosoi, Head of the BitDefender Online Threats Lab, explains. "Many botmasters now employ a 'middleman' approach – renting out their botnets for just a couple of dollars to launch large-scale spam campaigns, to automatically ping pay-per-click systems, or to use for several other features.
"These could include hosting phishing and pornographic websites on different infected computers, performing 'brute force' password attacks against different websites, using the networks as an anonimisation tool and so on."