It's grand to think we're all being kept safe by GCHQ and the NSA recording every single communication we make, then stashing them in a five-zettabyte Utah-based storage facility for time immemorial?
While President Obama says they're not, the head of the NSA says they are.
Lurking between the legalese, it seems all voice and internet communications are being stored. But that's fine, isn't it? You didn't really want your privacy, now did you? Come on.
It might seem like we have joined the tinfoil-hat wearing brigade. Yes, it's true that many of us have food caches dotted around, but that's to fend off the munchies going to and from work, rather than planning for the apocalypse. Truth be told, we're somewhat less worried about the NSA running off with our emails - though surely that's an infringement of our intellectual property rights - than shady gents physically running off with our stuff, or even Russian hackers tapping their way into our systems.
Last issue we looked at TOR, which is a clever system that masks where you are in the world by obfuscating your original IP address. Alongside this, it attempts to use HTTPS servers as much as possible to encrypt internet traffic, but it's not foolproof and is only relevant for your online life.
What else you can do? Put simply, you can either encrypt all your stuff or take it offline. We'll ignore that second option for the moment and concentrate on hiding all your stuff with encryption.
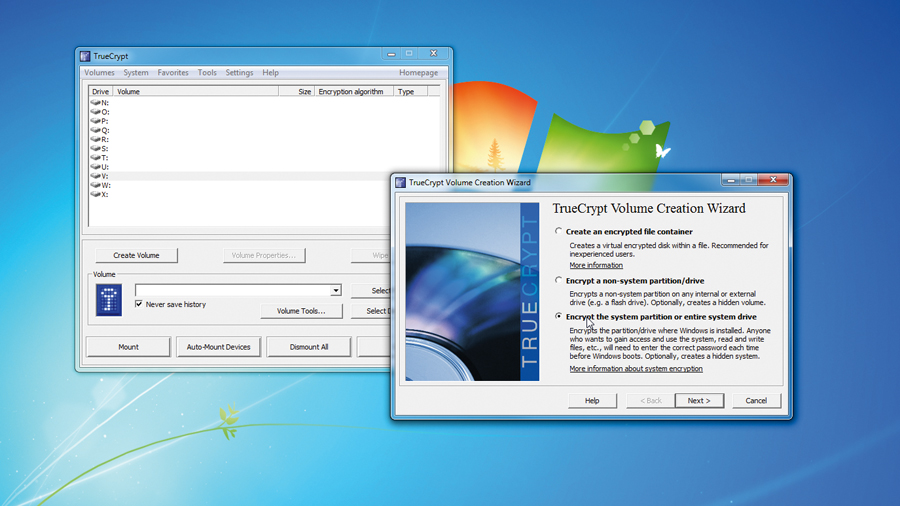
Modern high-speed, high-security encryption not only protects your data, but is largely unbreakable when used correctly. You can deploy it to protect everything from your entire hard drive to individual emails sent over the insecure internet. We understand you might be busy and not paranoid, so we'll start by protecting the important stuff before moving on to encrypting selected emails or dealing with your full system…
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.
We're glad you've made it this far, because frankly encryption is about as sexy as Alan Sugar gyrating in a pink g-string. It's also not helped by the usual set of questions. Isn't encryption a pain to use? Isn't it slow? Isn't it complicated to install? The short reply to these are no, no and no.
At its worst, we're talking about using an independent, open source, full-system with pre-boot encryption that requires you to create a password and rescue CD as part of a pretty standard installation. Beyond this, the encryption process can run in the background without hindering you at all.
Thanks to modern processors being kitted out with accelerated instructions, deploying encryption on a system has almost no impact on performance. Even the impact on older systems is small at best - around a 3-8 per cent reduction on pre-2010 processors. For newer processors, there's a set of hardware-accelerated instructions called AES-NI.
Excluding Core i3 models, you'll find these in all Intel's processors since Sandy Bridge, but also in the Core i5/7 Clarkdale and Arrandale models, being the Core i5/7-6xx and i5-5xx ones. AMD has similarly integrated the instruction set into all Bulldozer, Piledriver and Jaguar processors. This increases performance at least five-fold, reducing the impact to just a percentage point at worst.
One key design goal of the widely used AES was efficiency. On the Pentium Pro architecture, a byte can be processed in 18 clock cycles leading to 11MB/s at 200MHz. For hardware supporting AES-NI, this is reduced to just three clock cycles. The practical outcome is that any mid-range or better system built in the last three years won't even bat an eyelid at full-system encryption. Outside of this level you can expect at least a 10 per cent reduction in drive access speed, but it's doubtful that would be across the board or more importantly if it'd be noticed by most average users.