How to secure a wireless network
Top tips for securing your businesses wireless network

Just as you don't allow complete strangers to help themselves to your gas, electricity, water, telephone or cable TV for free, by the same token you should also stop freeloaders accessing your wireless network. Why? Well, there are a number of reasons. They could gain access to your private data on your network, simply steal bandwidth thus slowing down your connection, use up your data allowance or they might be using your internet connection for nefarious reasons, such as downloading copyright material.
Likewise, if you connect to an open network, you might be exposing your PC to security risks. To put it bluntly, an open WiFi network is nothing more than another channel for anyone wanting to get access to your precious data.
So while WiFi might be the perfect partner for your iPad, tablet, smartphone or, indeed, computer, you should never lose sight of the fact that WiFi is by default inherently insecure – it's tantamount to dangling a network cable out of your window with a prominent 'Help Yourself' label attached to it.
Unfortunately, the earliest attempt at WiFi security, Wired Equivalent Protocol, or WEP, proved deeply flawed and very easy to hack. WiFi Protected Access (WPA) and in particular WPA2 (which features tough AES encryption) has gone a long way to rectifying this glaring defect. Even so, too many wireless networks (WLANs) remain unprotected and open to intruders.
WiFi Security Dos
Because many WLAN lack security by default it's absolutely essential to change all the default security settings on your wireless access point or broadband router.
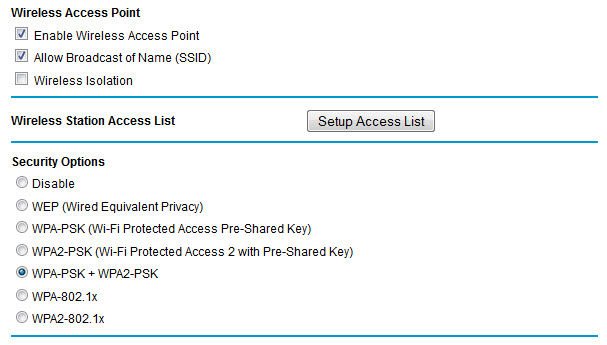
So, change the default SSID (Service Set Identifier or network name) on your router/access point (AP). The default SSIDs of common network hardware eg NETGEAR or DLINK are well known to hackers.
Your SSID ideally should not contain information that would give away your company name or location - something bland or innocuous is best.
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.
Without fail you should also change the administrator's password, too. Hackers know the default passwords for all of the major brands of hardware and with your password could easily remotely reconfigure your AP. Similarly, if your router supports SNMP, change the community names, e.g. 'public' to something much less obvious. This will prevent hackers from managing your device using standard community names and SNMP management software.
Always turn on the highest level of security your hardware supports. Use WPA or better still WPA2 encryption if it's available.
WPA passphrase keys aka 'passwords' have to be a minimum of eight characters long – a truly random mix of 13 characters should defeat most brute force attacks. Having to manually enter 13 random characters might encourage you to use the 'one-touch' WiFi Protected Setup that some routers offer but this has recently been found to contain security weaknesses.
Finally, some routers permit scheduled 'sleep' periods, say daily between midnight and 8am, so consider using this feature. It's hard to hack a router that's switched off.
WiFi Security Maybe Nots
Encryption unavoidably incurs a bandwidth overhead and some prefer to rely on controlling access to their WLANs based on the Media Access Control (MAC) address of the device requesting access. It's simple to set up an 'approved' list of PCs and works very simply: as we all know, 'if your name ain't on the list, you can't come in'. The major flaw with this approach is that the MAC address is just a 12 digit long HEX number that can be viewed in clear text with a network 'sniffer' program. All the hacker has to do is to wait and watch until a PC connects to the WLAN, the hacker then duplicate the permitted MAC address and gains entry. So it's not that secure.
Some recommend hiding the AP's SSID. Turning off SSID broadcasts does make it awkward for casual hackers (and genuine users wanting to roam) to find your WLAN but like MAC filtering, it's not the ultimate in security. Why? Because the SSID is still broadcast by other mechanisms on the AP, such as probe requests and responses. Again, turning off SSID broadcasts doesn't make your WLAN quite as stealthy as you might imagine.
Finally, there is some debate over the real value of disabling auto-connect features such as DHCP, which automatically doles out IP addresses to new users joining the network, thus making the life of the hacker just that bit easier. Again this is likely to deter casual hackers but the seasoned variety won't be too fazed by it: in reality it shouldn't take more than a minute to figure out the IP scheme of any network and simply assign your own IP address.