Learn from the hackers: how to avoid website exploits
Sign up for breaking news, reviews, opinion, top tech deals, and more.
You are now subscribed
Your newsletter sign-up was successful
When large data breaches are announced, the media can go overboard with its portrayal of hackers as uber-geeks with flashing fingers and skills that are almost supernatural in origin. In fact, nothing could be further from the truth.
By using basic tools and a logical approach, hackers turn websites into playgrounds full of interesting servers to explore, subvert and destroy. There are databases to plunder; there are pages to deface.
But just what is their approach, and how can we learn to avoid it?
Footprints on the web
Once a hacker finds a website that could be worth exploring, their first task is to create a detailed profile of the target, called a footprint. This identifies the basic building blocks of the site and enables the hacker to draw a map of how everything fits together.
Unfortunately, the way websites work provides hackers with lots of useful information without them having to do much. If there's a login process, for example, they know there's a database containing usernames and passwords. If the site has an ecommerce element, they know there's a shopping cart product in use, or some handcrafted and potentially vulnerable code to try to subvert.
Similarly, a catalogue of products indicates another database, which could link to a stock control server and possibly also a re-ordering application containing information about trade accounts. The hacker will also survey links to ad servers that feed content into the site. They will also consult the DNS records for the domain.
Sign up for breaking news, reviews, opinion, top tech deals, and more.
DNS is the only way to keep track of what's on the internet and where it all is. But it also gives information about all the publicly accessible servers owned by a domain, regardless of whether their addresses and names are meant for public consumption.
When I began working as a network security consultant, I found that it was easy to shock clients by showing them their DNS records, and then drawing a map of how I believed their servers were plumbed together. Some network admins had been naïve enough to think that all their important servers needed public IP addresses, making them easy to profile prior to an attack.
DNS information
Windows and Linux have tools capable of interrogating DNS, but they're fiddly command line utilities. Luckily, plenty of websites provide easy access to DNS information, including Kloth.net. Enter the name of a domain you're interested in (such as pcplus.co.uk) and press [Enter]. In the answers section that appears, you'll see lines containing the domain name and associated IP addresses.
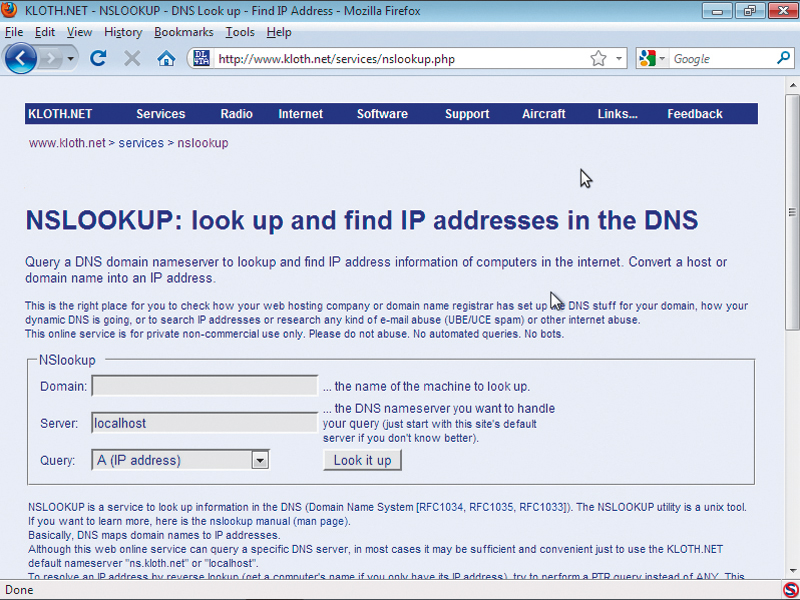
To search for a possible web server, add www. to the start of the domain and press [Enter]. This time you'll see the domain's web server. If you change the query type to 'MX' and click 'Look it up', the answers section will contain the name of the computer acting as the local mail server (technically called the mail exchanger).
This name may be the same as the web server, but if it has a different name, enter it into the 'Domain' input box to see its details.
Another important part of this process is the use of a port scanner such as nmap to discover what services are running on each internet-facing server. See nmap in action at www.nmap-online.com. The default IP address is your own computer.
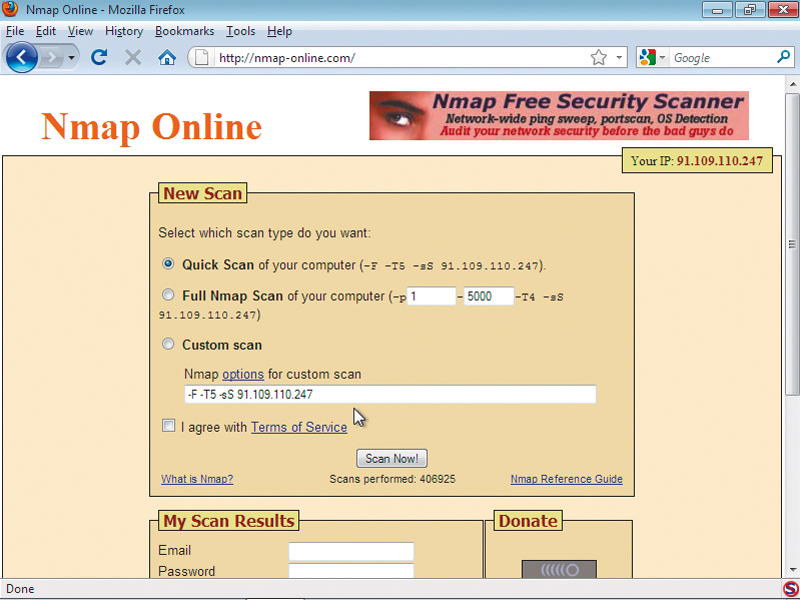
To scan it for open ports, click the 'I agree with terms of service' and then click 'Scan now'. Enter an email address for the site to notify when the scan is complete, along with a password to access the results.
Nmap sends carefully crafted packets to each potentially open port and analyses the information returned to discover not only what's running, but sometimes even detailed information about the running operating system and its TCP/IP stack. This can aid hackers in profiling a website and formulating a coming attack.
If a mail server is also running port 80, there's a good chance that connecting to it via a web browser will reveal a web mail interface that may have exploitable bugs. However, if the hacker is met by a default Apache web server installation page, it may be that system administrator installed the web server but has forgotten about it. It's likely that the software has never been patched and is vulnerable to a range of exploits.
By examining the verbiage returned with the web page, the hacker can determine the exact release of the software and any extra modules installed. Finding a NetBIOS service running (ports 137 and 139) indicates that the server runs Windows. An SQL service (port 1143) indicates that there's a database engine running, and so on.
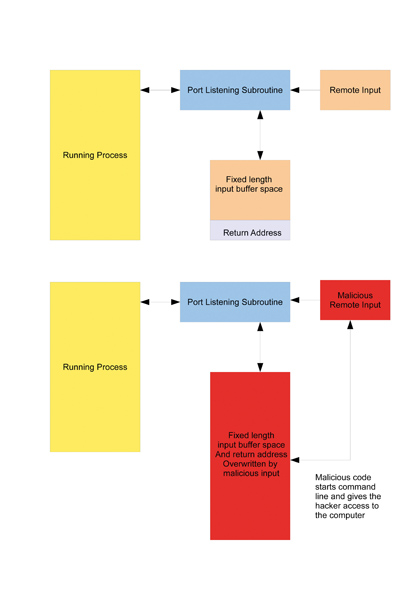
It's possible to build a detailed map of a domain's capabilities and vulnerabilities from this process.
- 1
- 2
Current page: Avoid web exploits: learn their approach
Next Page Avoid web exploits: learning about apps