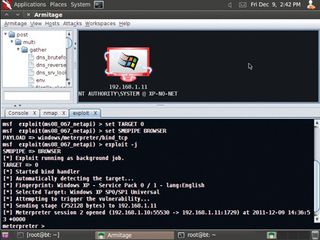
PWNED: A few key clicks and the target machine has been found, scanned and exploited. In the language of the hacker, it's game over for the target
Let's now comprehensively 'own' the target. Begin by right-clicking on the target's icon. There's an Attack menu. Under it, there are further submenus. Click 'Smb > ms08_067_netapi'. This command runs an exploit against the target to overflow a buffer with code. The target mistakenly then runs this code, which waits for Metasploit to send over a larger program called Meterptreter.
This program uses the exploited process to establish a temporary beachhead for further incursions into the host. A new tab opens in the Metasploit pane and after a few seconds, the target's icon goes red and acquires lightning streaks. This means the target is effectively compromised and running our code.
Let's now steal the target's encrypted password hashes and crack them. First, make sure your account on the target has a password. Make it a dictionary word, as the following activities will demonstrate why they must never be used.
In Armitage, right-click 'Meterpreter > Access > Dump hashes > Isass method'. After a few seconds, a pop-up tells you that the hashed passwords have been stolen.
Click 'View > Credentials' to view them in a tab in the lower pane. This tab has a button marked 'Crack passwords'. Click this, and the 'Launch' button on the resulting parameters window, and then watch as a utility called John The Ripper runs and attempts to crack the hashes. Dictionary words used as passwords stand no chance, and fall within a few minutes.
Gaining full access
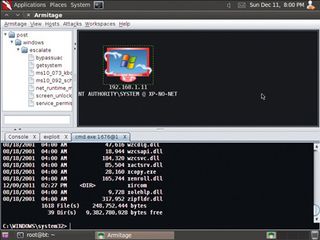
PASSWORD CRACK: Dictionary words make poor passwords - systems protected this way can be accessed in minutes
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.
We can go much further in our exploitation of the target computer. We can, for example, tell what's running on the target.
Simply right-click on the target and select 'Meterpreter > Explore > Show processes'. There they are: the processes running on the target.
What would be really great, however, is to be able to log into the target remotely as if it were Linux. We need to escalate the privileges of the Meterpreter session temporarily running on the target.
To do so, simply right-click the target and select 'Meterpreter > Access > Escalate Privilege'. Now we can tell Meterpreter to run cmd.exe on the target and to send the output back to Metasploit. Simply right-click on the target and select 'Meterpreter > Interact > Commands shell'.
After a few seconds, a new tab appears in the lower pane and, as if by magic, it's a command prompt! To prove it's running on the target and being 'shovelled' back to Metasploit, enter the command hostname and the target's hostname should appear. Try ipconfig, dir or any other command.
Keylogging
We can also log any keystrokes typed by the user of the target machine. Again, right-click the target and then select 'Meterpreter > Explore > Log Keystrokes'. Metasploit will open a tab and after displaying some verbiage, will tell you the name of the file to which it will log keystrokes.
Logged keystrokes are also available in Armitage by clicking 'View > Loot'. The files that have been saved are displayed. Double-click on one and it opens to display the keystrokes captured so far. Enter a few keystrokes on the target computer and click 'Refresh' in Armitage.
This comprehensive 'pwning' of the target PC is possible because we've attacked an unprotected XP machine. Hopefully, the ease with which we've completely exploited it has shown why it's vital to keep your computer supplied with automated updates as they become available.
It's boring waiting for computers to shutdown when installing major updates, but the alternative can be the loss of all your secrets.