Security update live blog - New Win 11 security tools, npm packages compromised
Breaking news about cybersecurity, ransomware, EPP, ZTNA, VPN and more

Share your thoughts on Cybersecurity and get a free copy of the Hacker's Manual 2022. Help us find how businesses are preparing for the post-Covid world and the implications of these activities on their cybersecurity plans. Enter your email at the end of this survey to get the bookazine, worth $10.99/£10.99.
Welcome to the security live blog from TechRadar Pro. This is the place where you will get your daily fix of security news, features, op-eds, reviews and other nuggets, brought to you by our experts and partners.
Our live blog looks to cover some of the more in-depth or intriguing security stories you might have missed - here's what we've seen recently...
Nordsec adds encrypted cloud storage for business offer

Just days after announcing it had received investments of $100 million, Nordsec, the holding company for the popular NordVPN, has added yet another product to its portfolio. Nordlocker for business is its second product that targets the multi-billion dollar enterprise security market.
After NordLayer, NordLocker is a secure cloud storage service that competes with the likes of Wasabi.
“We introduced NordLocker as a robust file encryption tool in 2019. Since then, the product has undergone a few solid development phases and is now positioned as an end-to-end encrypted cloud storage option with a file encryption solution,” said Aivaras Vencevicius, head of product at NordLocker. “It was only natural for us to move forward and launch an encrypted cloud service for business clients to offer a secure, convenient, and cost-effective way to store and manage their data.”
Oh hello, DuckDuckGo

We all love a plucky rival and Google may well have found its match in the shape of DuckDuckGo.
After challenging Google online with a privacy-focused search engine, the company has just announced the beta launch of its desktop browser, for Mac and Windows. From our article:
"Alongside its built-in private search engine, the company’s new browser for desktop also features a number of useful security features including a powerful tracker blocker, new cookie pop-up protection, a Fire Button for one-click data clearing, email protection and more, all free of charge."
128 bugs blitzed by big Microsoft patch release

Patch Tuesday is a monthly happening worth looking into if you're a sysadmin with a penchant for security.
Microsoft's latest sprinkling of vuln-busting code targets a whopping 128 bugs across a variety of applications including Defender, Office/Microsoft 365 and Windows., with several being actively exploited in the wild.
Cybersecurity M&A market sees $11 billion deals in 48 hours

Thoma Bravo took IAM specialist SailPoint private in a deal worth almost $7 billion while rival KKR bought Barracuda networks for a mere $4 billion.
Other recent cybersecurity deals include the $100 million investment in NordSec, the acquisition of Datto by Kaseya for just over $6 billion and Citrix going private in an eye-watering $16.5 billion deal.
A look at some of the top ZTNA solutions
We have compiled a list of the best ZTNA solutions currently on the market, covering not just plenty of well-known players, but also some lesser known ones as well.
All of this points to a very healthy cybersecurity market as businesses and organizations move away from traditional VPN-based security strategies to one where zero-trust is the tent pole.
There has been a surge in interest in ZTNA fuelled by the pandemic and the paradigm shift to hybrid working.
Got any questions about ZTNA?
What is ZTNA? Why is it so important to tackle the global ransomware epidemic and why is it so critical to mobile workers?
We’ve got these and dozens of other questions about SASE, business VPN and ZTNA covered.
Feel free to reach out to us via Twitter or LinkedIn and we’ll make sure to get an answer to your burning questions.
In the meantime, why not download our free bookazine that contains essential readings about the aforementioned topics from industry luminaries and thought leaders from the world of cybersecurity.
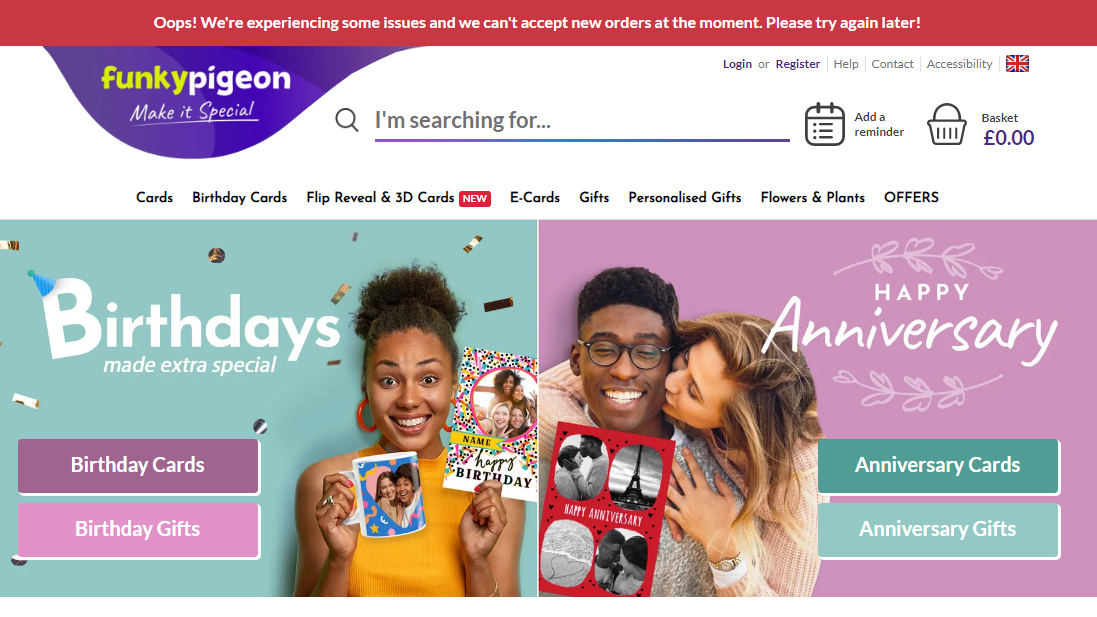
Funkypigeon.com suffers "cybersecurity incident"
In what may well be a textbook case of targeted attack over a long bank holiday weekend in the UK, popular e-card and stationery service provider Funkypigeon.com has posted a statement on its website, saying that "they're experiencing some issues and we can't accept new orders at the moment. Please try again later!"
Tens of millions of dollars lost in Crypto-currency heist
Decentralized, credit-based finance system Beanstalk disclosed on Sunday that it suffered a security breach that resulted in financial losses of $182 million, the attacker stealing $80 million in crypto assets. As a result of this attack, trust in Beanstalk's market has been compromised, and the value of its decentralized credit-based BEAN stablecoin has collapsed from a little over $1 on Sunday to $0.11 right now.
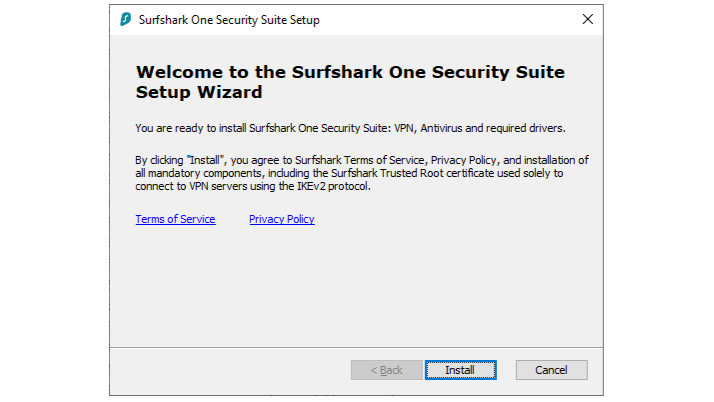
Trusted Root Certificates from VPN providers... But why?
New research reveals Surfshark, TurboVPN, VyprVPN are installing risky root certificates. Not what you'd expect from VPN providers that are amongst some of the most popular in the world. TechRadar Pro’s security expert, Mike Williams, stated “Installing trusted root certificates isn’t good practice. ‘If it’s compromised, it could allow an attacker to forge more certificates, impersonate other domains and intercept your communications.”

Remember the infamous SolarWinds hack? We talked to the man who knows it all
Below is an excerpt of the piece written by Joel Khalili about one of the biggest, most damaging Cyberattacks ever.
"Sudhakar Ramakrishna was sitting down to a birthday meal with his family when he received the call: SolarWinds had suffered a large-scale cyberattack. The date was December 12, 2020 and Ramakrishna was due to start as CEO in a few weeks’ time."

Only two customers impacted by hack says Okta
IAM giant Okta has confirmed that only two customers have been impacted by the Lapsus$ cyberattack from January 2022. From the report we published earlier today.
"In a blog post announcing the findings, Okta Chief Security Officer David Bradbury outlined that the incident was caused by the "compromise" of a third-party vendor, named only as a, "third-party forensic firm, engaged by our vendor Sitel".
Guess what brand hackers, cybercriminals and phishers like the most?
Apple? Nike? Google? No, Microsoft-owned Linkedin. Not surprisingly, the social network for business has attracted plenty of attention from scammers all over the world, eager to strategically connect with potential targets to infiltrate organizations. The professional social network was impersonated in 52 percent of all phishing attacks globally during Q1 which marks a dramatic, 44 percent increase from the previous quarter.

Ever wondered what DNS Filtering is? We've got the low down
From blacklisting to whitelisting, we've look at how this feature can help organizations keep cybersecurity threats abreast. In simplest terms, DNS transforms domain names into IP addresses, which internet users utilize to enter websites. Therefore, as its title implies, DNS filtering is the practice of filtering specific sites for a particular purpose, often with their content as the main criteria. Check out the rest of this feature

Look who's back on Tor
The Tor sites of the infamous REvil ransomware group have suddenly come back online following months of inactivity. While the group took down all of its websites and essentially shut down its operations back in September of 2021 before being dismantled by Russia’s FSB at the beginning of this year, its sites on Tor now redirect to a new ransomware operation that launched only recently.
Java weakness allowed anyone to be who they wanted to be
Be who you want to be thanks to a flaw that allowed cybercriminals to pass off for whoever they wanted. That vulnerability has now been patched by Oracle and Java users have been urged to do theirs before hell breaks loose.
From our news piece, "Tracked as CVE-2022-21449, the flaw was found in the company’s Elliptic Curve Digital Signature Algorithm (ECDSA) for Java 15 and newer. It allows threat actors to fake TSL certificates and signatures, two-factor authentication codes, authorization credentials and the like."


Facebook users warned of a new phishing campaign
People have been getting emails claiming their recent Facebook posts infringed on other people's copyright, and if they don't address the issue immediately, their accounts would be closed. While "addressing" the problem, the victims were being asked their login info.
From our news piece: The email carries two links: one that leads to a genuine Facebook post (probably to help bypass email protection services) and another that directs the victim to a website where they can “plead their case”.
This malicious page isn't host to any malware, but rather asks the victim to provide personal information, including their name, email address and Facebook password.

These are the top 10 SDP providers right now
Cybercriminals are steadily coming up with new cunning schemes to profit from someone else's downfall, forcing companies and individuals to catch up with security solutions capable of withstanding these attacks. An SDP is an approach to cybersecurity that enforces the zero-trust policy by applying user authentication and identity verification before allowing access to an organization's networks, apps and data included.
If you want to start building your zero-trust architecture with an SDP solution, here are some providers worth considering in 2022.

US Homeland Security systems had dozens of bugs
During a recent hackathon, cybersecurity researchers have found 122 vulnerabilities in select DHS systems. Of those vulnerabilities, 27 were deemed as critical.
From our news piece: The government organization recently kicked off its “Hack DHS” program, a three-phase event with the goal of tightening up network security.
The first phase was about discovering vulnerabilities on DHS endpoints, and the government has awarded researchers a total of $125,600 so far.
What is a Secure Web Gateway?
These gateways have revolutionized the way we implement unified security at remote sites and on the web, regardless of the number of users involved. To learn more about secure web gateways and how they can help you secure your digital premises, read our in-depth guide.
One of the largest-ever DDoS attacks blocked
Cybersecurity researchers from Cloudflare said they've blocked a distributed denial of service (DDoS) attack comprised of 15.3 million requests per second (RPS). The victim was a Cloudflare customer operating a crypto launchpad.
From our news piece: "The attack itself lasted approximately 15 seconds, and was launched by a known botnet. Out of 6,000 unique endpoints used in this attack, most of them came from data centers. The majority (15%) were located in Indonesia, with large numbers also hailing from Russia, Brazil, India, Colombia, and the US."
Android could soon run on RISC-V chips
Alibaba Cloud is making progress in its effort to port Android to the emerging instruction-set architecture (ISA). It enabled third-party vendor modules, bringing a number of new functions such as Wi-Fi, Bluetooth, and camera operation. RISC-V is open sourced which in theory makes it easier for researchers to find and solve any vulnerabilities.
From our news piece: To help facilitate these new functions, Alibaba Cloud has enabled more system enhancement features such as core toolsets, third-party libraries, and SoC board support package on RISC-V. Additionally, the company has successfully trialed TensorFlow Lite models on RISC-V to support AI functions like image and audio classification as well as Optical Character Recognition (OCR).

Free mobile antivirus apps sometimes more damaging than actual viruses
Google's app repository, Play Store, offers countless mobile apps that promise to keep the devices safe from viruses and malware. However, many of these apps contain such damaging data trackers that they're better left untouched.
From our news piece: "A lot of the free available options come at a hidden price – user data is being tracked, sold or plainly managed insecurely due to questionable coding and privacy practices of the application developers.”

Google's new update helps keep your passwords safe
Chrome users on Android can sleep peacefully now, knowing the browser will use the Duplex technology to automatically change any compromised passwords.
The tool that first appeared at Google I/O 2021 is now available to Android users everywhere.
From our news piece: "Whenever Chrome detects a password that it knows was compromised in a data breach, it will display an alert to the user. This pop-up will now include an option for Google Assistant to automatically change the compromised password, with the new addition added to the browser's built-in password manager."

Google Workspace getting more security controls for EU-based firms
Google Workspace is getting new tools to bring "digital sovereignty" to public organizations and private firms in the European Union, the company announced.
According to Google, Sovereign Controls for Google Workspace, as the tools are named, will help firms control, limit, and monitor data transfers across EU borders.
From our news piece: "The update comes as the data usage of a cloud computing market largely dominated by US providers continues to attract regulatory oversight from EU lawmakers. Google says the tools for its online collaboration software will build on its existing Client-side encryption, Data regions, and Access Controls capabilities. "

What is a CASB or Cloud Access Security Broker?
As companies moved their apps, data access, and data storage to the cloud, new security gaps started to emerge, such as how to overcome the lack of visibility with cloud apps, or how to compensate for incomplete control over who can access the data.
That's where Cloud Access Security Brokers come in handy. Learn more about them here.

Google Cloud Platform carries a misconfiguration that could result in full virtual machine takeover, researchers are warning. They're also saying that this is not a vulnerability, but rather a “dangerous functionality”.
From our news piece: The company noted that by (ab)using legitimate system features, potential attackers could read and write data from VMs which could, in theory, result in a complete system takeover.

GitHub users to be required 2FA
By the end of next year, all GitHub users will need to set up two-factor authentication to use the platform, it was confirmed.
According to the company, to better protect developer accounts, as well as code, everyone who contributes code to the repository will need to have 2FA active.
From our news piece: the software supply chain starts with developers and developer accounts are frequently targeted by social engineering and account takeover.
By protecting developers from these types of attacks, the company is taking the first and most critical step toward securing the software supply chain.

Protecting all your sensitive data solely by building a firewall around it can't cut it today.
The progress of cloud solutions was followed by the expansion of cloud-based security services introducing new technologies, firewalls included.
Enter firewall as a service (FWaaS), a stand-alone security solution, and a crucial component of any comprehensive security system.
To learn more about FWaaS, read our in-depth guide here.

Heroku confirms data breach
Cloud application platform Heroku confirmed that the recent cybersecurity incident resulted in the theft of customer credentials.
The Salesforce-owned company confirmed that OAuth tokens that were stolen in a cyberattack were used to obtain hashed and salted passwords, belonging to its customers, from “a database”.
From our news piece: "For this reason, Salesforce is ensuring all Heroku user passwords are reset and potentially affected credentials are refreshed. We have rotated internal Heroku credentials and put additional detections in place. We are continuing to investigate the source of the token compromise,” it said in a security advisory.
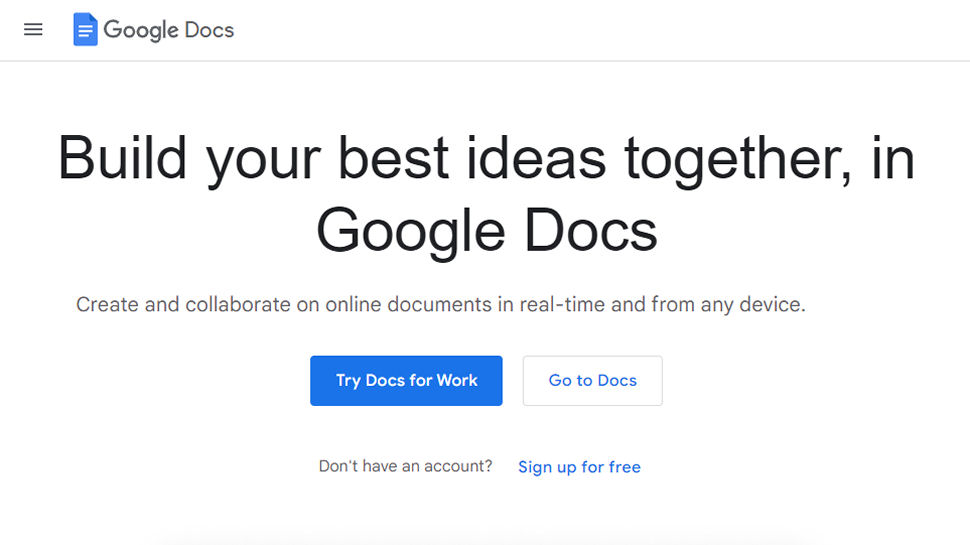
Crashing Google docs is easier than it seems
By typing the word "And" multiple times at the beginning of a new Docs file, a security researcher managed to crash the app completely. Google acknowledged the issue and has said to be working on the fix, right now.
From our news piece: "The flaw was discovered by Pat Needham, a poster on the Google Docs Editors Help forum, who found that typing "And. And. And. And. And." into a new document would cause it to crash.
Google Docs would display its usual "Something went wrong" error message, along with a pop-up stating that it was "unable to load file". Reloading the document appeared to cause the same issue, forcing the user to quit Google Docs entirely."

Microsoft goes for ransomware's throat
Microsoft announced the launch of a new line of managed security solutions, whose endgame seems to be - ending ransomware.
Combining human-led services with expert-trained technology, the new service is called Microsoft Security Experts.
From our news piece: "The company aims to deliver this new category of services across security, compliance, identity, management and privacy. Based on input from its partner ecosystem, Microsoft has designed three new managed services that allow organizations to scale their team of experts to fit their needs without the challenges of hiring and training new staff."

Elon Musk abused for crypto scams - again
There is a new scam scheme going around, tricking people into selling millions of dollars worth of cryptocurrencies. The victims are promised double their investment in a matter of days and reassured in the legitimacy of the whole ordeal with an edited video of Elon Musk and Jack Dorsey.
From our news piece: "The victims are promised double the investment if they send their cryptos to specific addresses. McAfee has found more than 26 websites promoting the scam, further saying that the number is probably bigger.
The websites seem to be showing a list of addresses participating in the scheme, as well as the funds sent, and funds received, to add credibility to the entire thing. However, researchers have found that the scammers actually used JavaScript code to generate a list of random cryptocurrency wallets and amounts paid."

What is a Firewall as a Service?
Today's firewalls are capable of enforcing various network security policies, monitoring user activity, and safeguarding networks from all sorts of outside cyber threats. However, protecting all your sensitive data solely by building a firewall around it can't cut it today.
The progress of cloud solutions was followed by the expansion of cloud-based security services introducing new technologies, firewalls included. Enter firewall as a service (FWaaS), a stand-alone security solution, and a crucial component of any comprehensive security system.
To learn more about FWaaS, how it works, and why you probably need it, read this.

One of the biggest flaws ever, found in F5 gear
BIG-IP, F5's suite of hardware and software, was found to be carrying a super high-severity vulnerability, researchers discovered.
The products, that act as load balancers and firewalls, can be fully taken over by attackers, it was said.
From our news piece: "The flaw is tracked as CVE-2022–1388 and carries a severity rating of 9.8/10. The products are used by 48 members of the Fortune 50 group of companies, with around 16,000 endpoints able to be discovered online. As these devices are used to manage web server traffic, they can often see decrypted contents of HTTPS-protected traffic, adding an extra level of threat."

Lincoln College permanently shut down due to ransomware
Illinois-based private liberal arts college Lincoln College has shut down, allegedly due to a ransomware attack. The institution will be closing its doors on May 13 this year, a date also marking the end of spring semester.
The organization was founded more than 150 years ago, and survived the Spanish flu, the Great Depression, and World War II.
From our news piece: "Lincoln College fell victim to a cyberattack during December 2021, which it said “thwarted admissions activities and hindered access to all institutional data, creating an unclear picture of Fall 2022 enrolment projections”.
The attack rendered all systems required for recruitment, retention, and fundraising efforts inoperable."

What is Device Posture Check?
Remote workers usually don't have the luxury of a tight cybersecurity perimeter provided by the company's security tech stack. Therefore, it's critical to find a suitable solution for this gap.
Meet Device Posture Check (DPC), a solution that collects and inspects security-related data from all connected devices allowing administrators to enforce application access, control policies, and disconnect any device that’s considered dangerous.
To learn how it can help your organization stay safe from cyberattacks, read this.

Windows and Linux servers targeted with cryptominers
Microsoft is warning of new attacks against Windows and Linux servers. Apparently, threat actors behind the Sysrv botnet are taking advantage of different WordPress and Spring Framework vulnerabilities to launch these attacks.
Microsoft's security team took to Twitter to explain how the threat actors deploys cryptominers and other malware onto target systems.
From our news piece: "The recent spate of attacks has been made possible by new facilities introduced to the Sysrv botnet that help actively hunt down vulnerable servers and kill off any competing malware present on a target system.
Once inside, Sysrv-K also spreads itself throughout a network using a combination of stolen credentials and brute-force password stuffing attacks, Microsoft says."

Passwords are still the most common, most widespread type of cybersecurity protection out there. Yet, they are also often disregarded, with people using easy-to-guess passwords for their most important digital accounts.
They also often use the same ones across a multitude of services, share them with their friends and family, rarely update them, and leave them on slips of paper, to float around the office.
They do all of these things because they either find it inconvenient to keep their passwords updated, or they don't think they're going to be targeted.
Having a strong password, however, is probably the best way to keep cyberattackers at bay, and with a good password manager, all of the above can be done - with ease.
Red our "Why a password manager could be your next vital security tool to keep you safe online" article to learn more.

Zyxel devices under cyberattacks
Vulnerable VPN and firewall devices from Zyxel are currently under attack, cybersecurity experts have said.
They're saying that the threat actors are using a critical vulnerability, tracked as CVE-2022-30525, to bypass authentication and remotely execute code.
From our news piece: "The vulnerability in Zyxel’s business VPN devices was first identified by security firm Rapid7, which assisted the company with the remediation.
In a blog post detailing the bug, Rapid7 warned that attackers could abuse the issue to establish a reverse shell, a type of session that facilitates communication between the attacker and the target machine and sets the stage for further attacks."

Crooks are abusing free trials to distribute ransomware
Free trials of Remote Monitoring and Management (RMM) tools are being abused to distribute ransomware.
Cybersecurity researchers have found cybercrooks logging into target devices with stolen VPN credentials, and installing free trials of RMM tools. With these tools, they're able to install various viruses, and even ransomware.
From our news piece: “The RMM companies need to have a lot more checks and balances on their free trial system—not just letting people download them with no background checks,” says Blackpoint Cyber founder and CEO Jon Murchison.
“I think a lot of the big ones do that, but there are some smaller ones, and foreign ones, that don’t. They need to make sure there is some sort of gate with the free trial. You can’t just sign up with a Gmail or some made-up account and get it. You need to talk to people. You need to know you are dealing with a real human and not a bad guy.”

What is a Software-Defined Perimeter?
With the rise of cloud computing and the heavy expansion of remote working, the "traditional" way of securing a corporate network no longer works. Gone are the days in which everyone outside the company perimeter is considered hostile, and everyone on the inside considered friendly.
With the lines blurred, and the security of cloud solutions becoming paramount, a new approach toward security was destined to turn up.
It's called software-defined perimeter (SDP), and you can learn all about it here.

Hackers can abuse Bluetooth to steal your Tesla
By using a Bluetooth Low Energy (BLE) relay attack, researchers managed to bypass all existing protections, and authenticate on a Tesla car as if they were the owners.
The attack works on all kinds of devices, from smartphones to smart locks.
From our news piece: "The attack works by squeezing the attacker in between the legitimate Bluetooth sender and receiver devices. That way, the attacker gets to manipulate the data going into the receiving device (in this particular case, the Tesla car). "

Fake NFT project site distributes infostealer
Fraudsters are impersonating a popular NFT project to distribute password-stealing malware, cybersecurity experts have warned. Researchers from MalwareHunterTeam found a fake Pixelmon site that claims to offer a playable demo of the game, but instead just distributes the Vidar virus.
Given that NFT enthusiasts are the victims, Vidar mostly looks for crypto wallets data.
From our news piece: "The legitimate website is pixelmon.club, but MalwareHunterTeam found pixelmon[.]pw, a seemingly identical site. However, instead of offering the demo version of the game, the site is offering a file named Installer.zip, which carries an executable file."

What is DNS filtering?
The internet is undoubtedly a menacing place, but businesses and individuals alike have numerous ways to protect themselves. One such way is Domain Name System (DNS) filtering. It's one of the most common methods of protection.
To learn more about DNS filtering, what it is and how it operates, read our in-depth guide here.

Crooks phishing for data with fake chatbots
Security experts have recently uncovered a creative phishing technique using a fake customer support chatbot.
Trustwave SpiderLabs found a fake DHL website with a chatbot-like application that tells people their parcels have been damaged and demands sensitive information to sort the issue out.
From our news piece: "It starts the usual way - the victim will get an email, saying they have a parcel pending with DHL, and that further instructions are needed.
If the victim takes the bait, they’ll be redirected to a fake DHL customer support website that seems to be running a chatbot. However, this is not a “real” chatbot, but rather an app with limited options and predefined responses. "

A switched-off iPhone can still run malware, researchers find
There is a way to run malware on an iPhone, even when it's turned off, security researchers are saying.
According to researchers from the Technical University of Darmstadt in Germany, there is a way to leverage iPhone's low-power mode (LPM) to track location and perform various malware attacks.
From our news piece: "LPM allows certain smartphone facilities - such as Bluetooth, near-field communication (NFC) and or ultra-wideband - to run even when the device is turned off or when its battery is depleted.
When an iPhone is shut down, it’s never truly off, as these components can still run 24/7. The idea is that people will still be able to their on-device wallets and keys, even when they are out of battery."

Top 10 SWG solutions in 2022
With data breaches and malware attacks looming behind every corner, it’s never been more imperative for businesses to implement more advanced security solutions to tackle these issues.
One of those solutions is a secure web gateway (SWG).
To learn more about what SWG solutions are, which players dominate the market, and how to choose the best partner for your business, read our list of the top 10 entrants here.

Linux malware spiking
XorDDoS, Linux malware that seeks to build a Distributed Denial of Service botnet, has grown 254% in the last six months, researchers are saying.
According to Microsoft, the botnet can also be used as a gateway for the distribution of additional payloads, therefore users are urged to patch their systems immediately.
From our news piece: "We found that devices first infected with XorDdos were later infected with additional malware such as the Tsunami backdoor, which further deploys the XMRig coin miner," Microsoft said in its announcement. "While we did not observe XorDdos directly installing and distributing secondary payloads like Tsunami, it's possible that the trojan is leveraged as a vector for follow-on activities."

QNAP tells NAS owners to apply new fix ASAP
QNAP NAS users have been urged to update their endpoints to the latest version immediately, to protect against a known vulnerability. As explained by the company, unknown threat actors are on the hunt for vulnerable NAS devices to deploy the Deadbolt ransomware.
From our news piece: "Among the vulnerable devices are those running on the QTS 4.3.6 and QTS 4.1.1 operating systems. That would include the TS-x51 series, and the ST-x53 series, although it’s probably not limited to these two."
Microsoft fixes a bug preventing Windows Store apps from loading
Microsoft has recently published a patch for a problem that prevented Windows Store apps from properly loading on a Windows device.
Users started experiencing the problem in late April this year, when a previous cumulative update broke how Control-flow Enforcement Technology (CET) works.
From our news piece: "All updates from April 25 onwards broke how the safeguard works, prompting the operating system to engage these CET capabilities against legitimate applications downloaded from Microsoft’s applications store.
Users affected by the problem should see 0xC002001B."

Android users targeted by Predator spyware
Google is warning Android users of a new spyware making rounds, called Predator. According to the company's Threat Analysis Group, a commercial company from North Macedonia, called Cytrox, developed mobile spyware that was discovered in dozens of devices around the world.
From our news piece: "In this particular case, while specific targets are not known, the researchers have found the spyware to be used at least by government-backed actors in Egypt, Armenia, Greece, Madagascar, Ivory Coast, Serbia, Spain, and Indonesia."
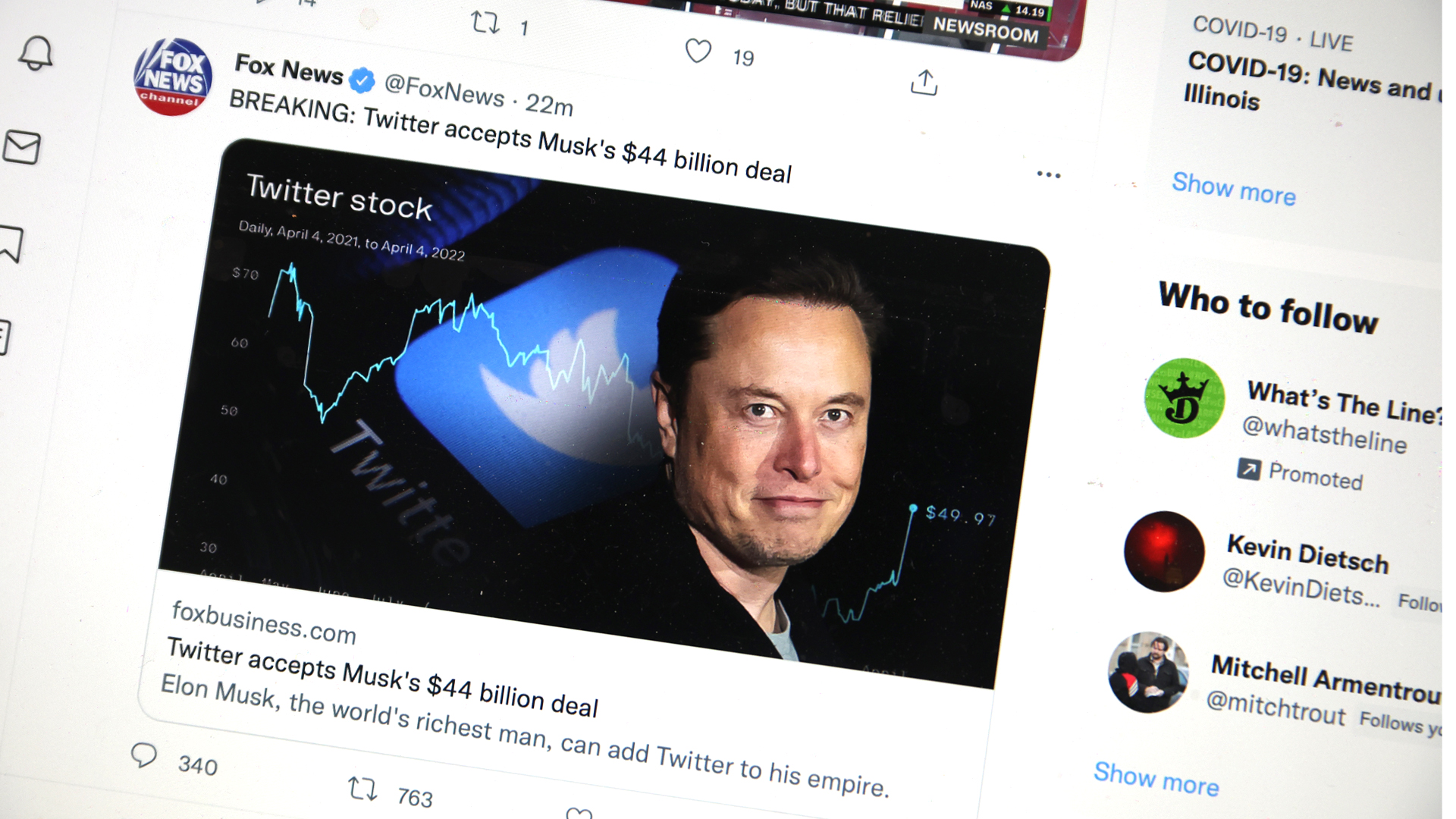
Elon Musk abused to promote a crypto scam again
There's a new cryptocurrency scam making rounds, and it's being promoted via a deepfake video of Tesla CEO, Elon Musk.
Researchers have discovered a fake exchange platform, promising up to 30% returns on people's crypto deposits. In reality, people depositing the money never see it again.
From our news piece: "It is being promoted with a deepfake video of Elon Musk, in which the eccentric billionaire and entrepreneur is seen discussing the business. The video does very little to add to the legitimacy of the whole ordeal, as the production of the multimedia is comically bad.
Still, the fraudsters have shared it via YouTube, meaning it can break into other people’s channels to distribute it in more places, with an Arabic gaming video channel already found to have been hijacked to promote the scam."

Latest scam scheme hits new moral lows
In a newly discovered scam scheme, fraudsters are using photographs of abuse victims to trick people into buying a non-existent service.
According to researchers, numerous fake services have popped up online, promising to cross-check registered accounts with known sex offender databases. To promote the service, scammers are creating fake social media accounts.
From our news piece: "They would demand their new love interest to register on one of these sites, to “confirm” they were not an abusive individual. Most of the sites (of which there are many, as the publication discovered), were registered to an entity in Cyprus, which was unavailable for comment."

Crooks can hack your account before you even make one
There is a way for hackers to crack open an online account without ever knowing the password, and it could even work on some of the world's biggest platforms.
According to researchers, all the attackers need to know is the victim's email address.
From our news piece: "Cybersecurity researchers from the Microsoft Security Response Center, together with independent researcher Avinash Sudhodanan, found a way to break into online accounts, basically by being the first there.
If the attacker knows the victim’s email address, and knows they don’t have an account registered on a service, they can create the account for them - using their email address (and hoping the victim dismisses the email notification as spam)."

Personal files of GM users revealed in data breach
Thousands of General Motors (GM) users have had their personal information revealed after cybercriminals brute-forced their way into the accounts, the company confirmed.
Besides snooping around personal details, the crooks also tried to redeem rewards points for gift cards.
From our news piece: "GM users have had their accounts compromised with a credential stuffing attack that took place between April 11 and April 29. The exact number of affected customers is unknown, although just in the state of California there are thought to have been around 5,000 victims."

Many Kubernetes servers left open to the Internet
Thousands of Kubernetes API endpoints are exposed to the internet, and as such, exposed to potential cyberattacks, researchers are saying.
Nonprofit The Shadowserver Foundation recently scanned 454,729 systems hosting Kubernetes and found 84% to be accessible via the internet.
From our news piece: "While being exposed to the internet does not automatically mean compromised, it is the first, and most important step, toward a data breach. What’s more all of these are most likely the result of misconfigurations, rather than intent. Of all the accessible instances, 201,348 (53%) were located in the United States."

New ransomware does not ask for money
An unknown threat actor is distributing ransomware that doesn't ask payment in crypto for the operators, Instead, the victims are forced into doing good deeds for those in need, in exchange for the decryption key.
From our news piece: "Cybersecurity researchers from CloudSEK recently discovered a ransomware strain named “GoodWill” that still infects companies, but instead of asking for payment, it’s asking for acts of goodwill against those less fortunate, all of which need to be documented and presented both publicly, and to the threat actor itself."

Cybersecurity researchers targeted by crooks
Researchers that analyze vulnerability proof-of-concepts have found themselves on the receiving end of a cyberattack, it was recently reported.
Apparently, threat actors posted fake PoCs that try and deploy Cobalt Strike beacons on the target endpoints.
From our news piece: "It’s common practice for researchers to publish a PoC of recently patched flaws on code repositories, such as GitHub. That way, they can test different solutions among themselves and force admins to apply the fixes as soon as possible. When Microsoft patched two remote code execution vulnerabilities, tracked as CVE-2022-24500 and CVE-2022-26809, a few PoCs popped up on GitHub, one of them coming from an account named “rkxxz”.

DuckDuckGo tracking deal with Microsoft uncovered
DuckDuckGo is facing a potential PR disaster after security researchers found a hidden tracking agreement with Microsoft.
The company, offering a privacy-oriented search engine, and a secure browser for mobile platforms, claims not to track people’s searches, or behavior, and also doesn't build user profiles that can be used to display personalized advertising.
Now, researchers have found that while some third-party trackers were being blocked, others were being allowed to operate freely.
From our news piece: "While Google’s and Facebook’s trackers are being blocked, those of Microsoft are allowed to continue running. Zach Edwards, the security researcher who first discovered the issue, later also found that trackers related to the bing.com and linkedin.com domains were also being allowed through the blocks."

MGM Resorts user data dumped on Telegram for free
Personal data on thousands of MGM Resorts users has been leaked, again. This time, however, it's been shared for free, on a Telegram group.
Researchers that investigated the matter are saying data on at least 30 million users leaked, although suspect it could be a part of the bigger batch that was stolen from the hotels and casinos chain back in 2019.
From our news piece: "Cybersecurity researchers from vpnMentor discovered the 8.7GB file dump earlier this week, finding it contained data on at least 30 million people. The data includes full names, postal addresses, more than 24 million unique email addresses, more than 30 million unique phone numbers, and dates of birth. "

Browser-hijacking malware grows big
The ChromeLoader malware is now a full-blown threat, researchers are warning.
Cybersecurity experts from Red Canary have said the threat from the browser hijacker rose significantly in these past few months, and that the threat actors are distributing it across both Windows and macOS.
From our news piece: "ChromeLoader is described as a browser hijacker that can tweak browser settings on the target endpoint(opens in new tab), making it show modified search results. By showing fake giveaways, dating sites, or unwanted third-party software, the threat actors earn commission in affiliate programs.
What makes ChromeLoader stand out in a sea of similar browser hijackers is its persistence, volume and infection route, the researchers said."

Android malware targets almost 500 apps
A known Android banking trojan, called ERMAC, was updated to version 2.0, bringing in more features, but also costing more money for the users.
As reported by cybersecurity researchers Cyble and ESET, ERMAC 2.0 now costs $5,000 a month, but it's capable of stealing login information from 467 apps, up from 378 in the previous version.
From our news piece: "When a victim installs ERMAC on its endpoint, the malware requests permissions to the Accessibility Service, which give it complete control over the device. Researchers have found that the trojan grants itself 43 permissions, including SMS access, contact access, system alert window creation, audio recording, and full storage read and write access."

Zyxel finds multiple flaws
Networking gear manufacturer Zyxel said it found a couple of flaws in its firewalls, AP, and AP controller products. Users should patch affected devices immediately, as the flaws allow threat actors to steal various data from the devices, crash them, run arbitrary OS commands and disable multi-factor authentication.
From our news piece: "The four flaws in question are tracked as CVE-2022-0734, a CSS vulnerability in the CGI component; CVE-2022-26531, an improper validation flaw in some CLI commands; CVE-2022-26532, a command injection flaw in some CLI commands; and CVE-2022-0910 (6.5), an authentication bypass vulnerability in the CGI component. "
Windows 11 update has hurt some antivirus apps
Trend Micro has warned its users that Microsoft's latest patch for Windows 11 actually breaks some of its products. Users opting for Trend Micro's security solutions should be wary of patch KB5014019, for Windows 11 and Windows Server 2022
From our news piece: "The affected Trend Micro products are as follows: Worry-Free Business Security Advanced 10.0, Worry-Free Business Security Services 6.7, Apex One 2019, Apex One as a Service 2019, Deep Security 20.0, Deep Security 12.0. The good thing is preview updates like KB5014019 are optional, and still in testing, so you don’t have to install them."

Phishing scam targets tax reporting software users
An unknown threat actor is trying to phish out sensitive data from QuickBooks users, the company has warned. Intuit, the firm that built the tax reporting software, warned its users of an ongoing email phishing campaing, in which users are asked for extra information in order not to have their accounts terminated.
From our news piece: "Apparently, victims will receive an email pretending to be from Intuit, which warns that the company has conducted an account review has not been able to verify some important information. For that reason, the email claims, the account has been put on hold until the information can be verified."

Vodafone wants to track you in new and unexciting ways
Telecommunications company Vodafone is currently piloting a new program which will allow it to track all of its users at the ISP level. The goal of the program is to be able to provide advertisers with enough data to serve everyone personalized ads.
From our news piece: "The operator is currently testing an advertising ID system dubbed TrustPid, which works by creating a fixed ID for every customer at the Internet Service Provider (ISP) level, and then associating all user activity with that ID. The profile, which will be formed with input from multiple parameters, will then be used for the distribution of targeted, personalized advertising. The company says that there is no way for the system to be bypassed at the browser level, by blocking cookies or masking the IP address. "

Businesses in the UK quite susceptible to online fraud
Compared to the global average, UK businesses are faring somewhat worse in terms of fraud and other economic crime.
A new PwC report says 64% of UK firms experienced such an incident in the last two years, compared to the global average of 46%.
From our news piece: "Of all the fraud types, cybercrime is the most common, with a third (32%) having fallen victim to a cyberattack. Although this figure is down since the previous 2020 poll, suggesting businesses are getting better at defending themselves, experts are under the impression that something entirely different is at play here."

Vulnerabilities capable of the next Solar Winds attack patched
Cybersecurity experts from Talos recently discovered eight vulnerabilities in the Open Automation Software which, claim the researchers, could have triggered another supply chain security disaster.
Among the eight flaws are two high-severity ones (score of 9.1 and higher) which could have enabled threat actors to change the configuration of the platform to create new security groups and run arbitrary code.
From our news piece: "Among its users are Volvo, General Dynamics, or AES, which use it to facilitate the transfer of data within their IT environments. OAS is described as essential to these organizations’ Industrial Internet of Things (IIoT) efforts. "

Russian government spending millions on VPN services
Since the start of the invasion on Ukraine, Russian government agencies have spent almost $10 million on Virtual Private Network (VPN) services, researchers have found. Russian government firms have signed 236 contracts in that time, with legislative agencies being the biggest spenders.
From our news piece: "State institutions and companies regulated by public procurement law based in Moscow spent 196 million rubles, or $2.4 million - more than any other region. Krasnoyarsk, with $1.8 million in spending, was the second-biggest region.
Breaking the data down by sector, the researchers found legislative agencies spending most ($2.3 million), followed by IT and communications ($1.9 million), and healthcare and emergency services ($1.5 million)."

Follina discovered in the wild
The recently discovered "Follina" zero-day vulnerability, which uses a Windows utility called msdt.exe to distribute malicious payloads, was now found in use, in the wild.
According to cybersecurity researchers from Proopoint, Chinese state-sponsored threat actor called TA413 used the zero-day against the international Tibetan community.
From our news piece: "TA413 CN APT spotted ITW exploiting the Follina 0Day using URLs to deliver Zip Archives which contain Word Documents that use the technique," Proofpoint noted. Campaigns impersonate the 'Women Empowerments Desk' of the Central Tibetan Administration and use the domain tibet-gov.web[.]app."

What is SSH access?
Secure Shell, or SSH, has become the standard for remote access for many organizations. System administrators use it to manage servers remotely or to securely connect to their personal computers.
It is also commonly used to tunnel traffic through untrusted networks, such as public Wi-Fi hotspots.
To learn more about what SSH access is and how it works, read our in-depth guide here.

Millions of MySQL servers exposed to the web
Researchers have found more than 3 million MySQL servers exposed to the internet and ready to be abused by cyber-crooks.
Nonprofit security organization, The ShadowServer Foundation, found that the servers were all using the default TCP port 3306.
From our news piece: "Most of the servers are found in the United States (more than 1.2 million), with China, Germany, Singapore, the Netherlands, and Poland, also hosting significant numbers of servers."

WhatsApp accounts ripe for hijacking, researchers find
There's a way for a cybercrook to take over a person's WhatsApp mobile application, by abusing automated call forwarding and one-time password features, researchers have found.
It all starts with the victim being persuaded into calling a number starting with a Man-Machine Interface code.
From our news piece: The number is usually set up by the mobile carrier, and is used to enable call forwarding. Most of the time, it starts with either a star or hash symbol. These codes are easily found, and most of the major mobile network operators support them."

Here's all you need to know about phishing
Phishing has been around for ages, and it's still considered one of the best-performing cyberattack methods out there. But ever since its inception, in the early days of the internet, phishing has evolved into real science.
To learn everything there is to know about phishing, including its variants, targets, strategies, and most popular defense mechanisms, read our in-depth guide here.

Businesses not ready to tackle a supply chain attack
Should a supply chain cyberattack occur today, most businesses wouldn't be able to tackle it properly. These are the findings of Venafi, after polling 1,000 CIOs on their organizations' readiness to tackle supply chain attacks.
According to the company's report, 82% of CIOs believe they're underprepared for such a scenario.
From our news piece: "It does seem that CEOs are taking notice of such threats, with the report adding 85% of CIOs were specifically instructed by chiefs to “improve the security of software build and distribution environments”. At the same time, 84% said the budget dedicated to the security of software development environments increased in the last 12 months. "

Runescape players targeted
There's a phishing scam making rounds, targeting Runescape players and their high-value accounts. Malwarebytes has discovered a new campaign in which threat actors are trying to get their hands on the players' login information, as well as their in-game bank PINs.
From our news piece: "If the attackers get their hands on the login credentials, and the in-game bank PIN, they can easily log into the account from their endpoint, transfer these valuables to another account, where they can sell them to a third party for real cash. As usual, users are warned to always be wary of any incoming emails, especially those carrying links and attachments."

Tim Hortons illegally tracked users, investigators find
Tim Hortons' mobile app has been tracking its users, even when it was off, the investigation into the app's behavior has uncovered. Even though users were "misled" into thinking the app only tracks users when it's turned on, it's been gathering data on user movement, places of living, as well as places of work.
From our news piece: "What’s more, the app generated an ‘event’ every time the user would enter a competitor’s premises, a major sports venue, their home, or their office. No financial penalty, though, but the company said it would carry out the orders."

New Office exploit tricks even the best-trained on cybersecurity
Homograph attacks (those that abuse similar-looking characters for the purposes of deception - e.g. Micr0soft) grow a lot more potent when based on international domain names (IDN), and used against apps other than browsers, researchers have found.
Analysts from Bitdefender found that all Microsoft Office applications were vulnerable to the exploit, including Outlook, Word, Excel, OneNote and PowerPoint.
From our news piece: "A threat actor can force Outlook to display a link that looks absolutely legitimate, while the user wouldn’t be able to tell the difference until the site was opened in their browser. In some cases, that would be enough to trigger a malware download."

New ransom extortion tactic spotted
A relatively new entrant to the ransomware game was seen using a unique new strategy to force its victims to pay up. Besides locking up data, Industrial Spy would deface the victim's website, to exert additional pressure on the target company.
Researchers from MalwareHunterTeam recently discovered that the website of SATT Sud-Est, a French company, was defaced, following a ransomware attack.
From our news piece: "Besides the usual methods of persuasion, the group also broke into the company’s website (which is almost never hosted on the same server as corporate data) and defaced the homepage, leaving the following message:
“Your business data has been compromised. More than 200GB of data will soon be released on the market. Please contact us to avoid your reputational risks.”
The site has since been shut down, but the message can still be seen on Google’s search engine results page."

Crypto fraud a billion-dollar industry
People have lost more than a billion dollars on various cryptocurrency-related scams, since early 2021, the FTC discovered. The agency's latest report says the scams, among which "bogus investment opportunities" is the most popular one, tricked more than 46,000 people into giving away their precious digital tokens.
From our news list: "The report says the average reported loss for an individual was $2,600 worth of either bitcoin, tether, or ether. For almost half of the victims, the report noted that the theft started with either an ad, a post, or a message on a social media platform."

US Government close to a proper cybersecurity bill
Reports of new legislation, one with both bipartisan support, and the support of privacy advocates, are coming in. While it will take some time for the legislation to be signed into law, the initial reports do sound promising.
From our news piece: "The biggest stumbling block between the Democrats and the Republicans was whether federal law should preempt state laws. Republicans support this idea, saying anything else would make for a compliance nightmare for businesses. The Democrats, on the other hand, want consumers to be able to sue businesses playing with their customers’ data too much."

Bored Ape Yacht Club Discord server hacked, NFTs nabbed
A compromised Discord account of the Bored Ape Yacht Club (BAYC) social manager led to the theft of hundreds of dollars worth of non-fungible tokens (NFTs), the media reported earlier this week.
Boris Vagner has had his account compromised, and then used on Discord channels for both BAYC and Otherside, to promote phishing links.
From our news piece: "The attackers also posted phishing links in the Discord server of Spoiled Banana Society, an NFT project Boris runs with his brother, Richard. So far, the attack appears to have stolen around 200 Ether worth of NFTs, which equals to roughly $360,000 at current prices."

Cybercrime out of control, experts say
As the attack surface expands, and risk management grows harder, cybercrime is slowly but surely spinning out of control. This is the conclusion of a new report from cybersecurity experts Trend Micro.
From our news piece: "Surveying more than 6,000 IT and business decision-makers in 29 countries for its latest report, Trend Micro said 73% of respondents are worried about the growing attack surface. More than a third (37%) said their attack surface is “constantly evolving and messy”, while just half (51%) were able to fully define its borders. For 43%, it’s spiraling out of control."

Extremely potent malware discovered
Cybersecurity researchers have discovered an extremely potent malware being used to target high-profile Chinese individuals. Experts from Kaspersky are saying WinDealer, as the malware is called, is being distributed via man--on-the-side attacks, a type of attack that basically has no counter-measure.
From our news piece: "Cybersecurity researchers from Kaspersky have discovered malware they call WinDealer, distributed and used by a Chinese Advanced Persistent Threat (APT) actor called LuoYu. WinDealer, the researchers say, is capable of collecting “an impressive amount” of information. It can view and download any files stored on the device, as well as run a keyword search on all the documents."

Some security updates on Apple devices to no longer require restarts
Some security updates that Apple pushes onto its devices will get there sooner, as users will no longer need to wait for major bundles, and will no longer need to reset their gear to complete the process.
The company revealed the change during WWDC 2022, as it announced a new feature called Rapid Security Response. In the future, iPhones, iPads, and Mac endpoints should be more secure.
From our news piece: "Usually, iOS and macOS device owners would have to wait for a full system patch, to get improved security on their devices. Not only does that take plenty of time, but many users refrain from installing these updates altogether. With Rapid Security Response, however, key updates “can be applied automatically between standard software updates.”

Why it's time for your business to get on board with VPS hosting
Businesses upgrading to Virtual Private Servers (VPS) for the first time, often aren't exactly sure what they should be looking for. Usually, they've outgrown their current shared hosting solutions and are in dire need to expand.
If you're looking to get your business on board with a VPS, you should read our in-depth guide here. Among other things, you'll learn that VPS packages come as either managed or unmanaged, what role hardware plays, and how important it is to retain the freedom to make choices about other important hosting options, as well.

Follina spotted distributing Qbot
Cybersecurity researchers found threat actors using the Follina flaw to infect endpoints with Qbot, a known banking trojan and infostealer. The trojan can do all sorts of nasties, from logging keys, to dropping stage-two malware.
From our news piece: "Follina, also tracked as CVE-2022-30190, is a flaw found in the Windows Support Diagnostic Tool. It can be abused to remotely run code, by getting programs such as Office Word to bring up the tool from a specially crafted document, when opened."

The Chinese were listening to US telco traffic for years
Chinese APTs have been eavesdropping on US telecom providers for years, the country's security agencies are saying.
As per a warning issued by the NSA, CISA, and the FBI, multiple Chinese state-sponsored groups were compromising telecoms operators, and often leveraging their position to mount further attacks against public and private sector firms.
From our news piece: "Upon gaining an initial foothold into a telecommunications organization or network service provider, PRC state-sponsored cyber actors have identified critical users and infrastructure including systems critical to maintaining the security of authentication, authorization, and accounting," it was said in the warning."

Cloud security incidents growing more painful
A new report from Thales says rising dependency on, and complexities of, cloud computing, is resulting in bigger, and more painful, data breaches.
As per the report, almost half of businesses experienced a cloud-based data breach in the past 12 months, up 5% from 2021.
From our news piece: "The majority of IT professionals surveyed agreed it has become more complex to manage privacy and data protection in the cloud. Migrating to the cloud has also grown more complex. Right now, just 24% expect to be able to deploy “lift and shift” tactics, which are considered as the simplest of migration tactics, down from 55% just a year ago."
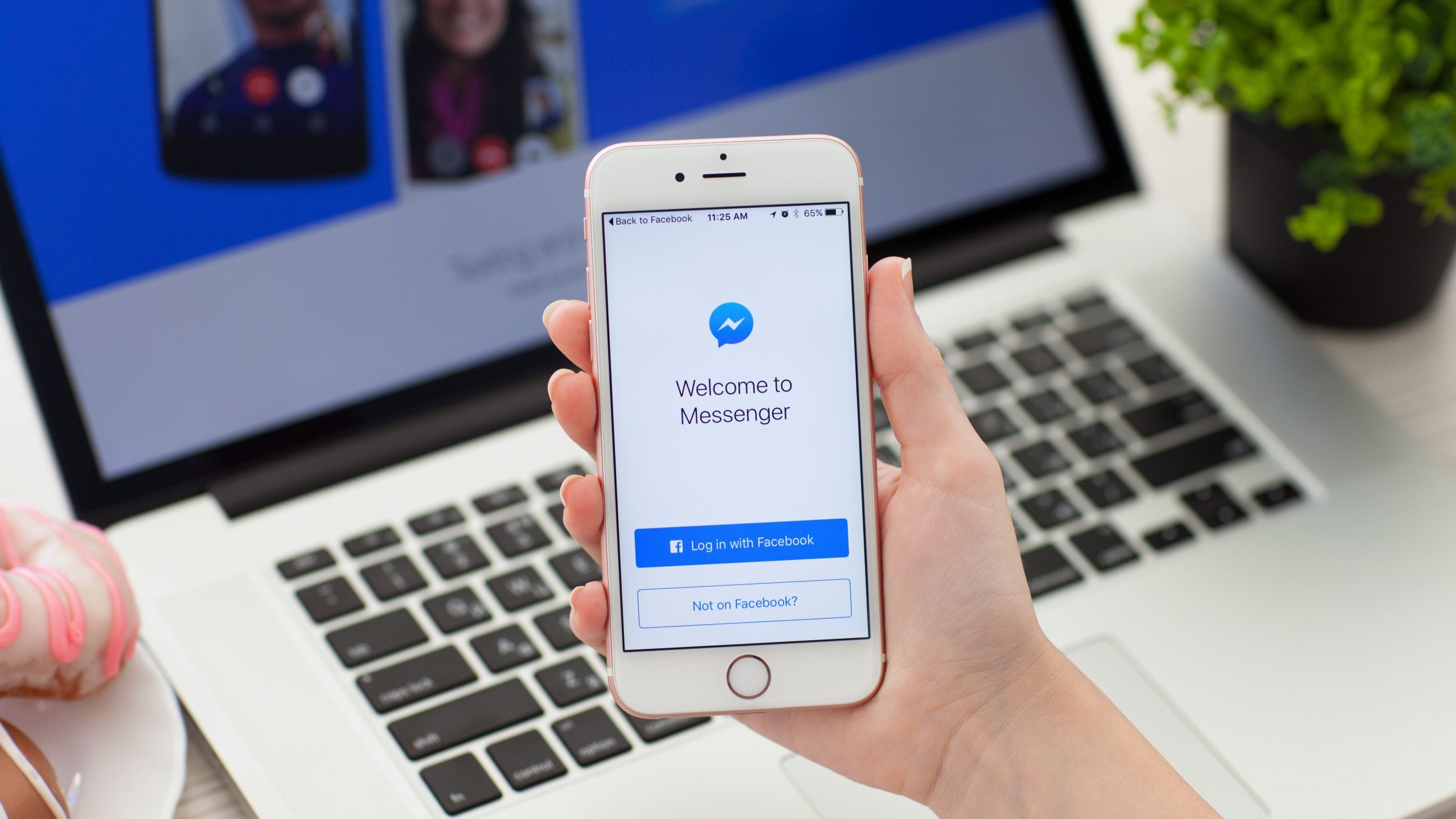
Facebook phishing scam earns its operators millions
A newly discovered phishing scam, that leverages Facebook's chat platform, Messenger, was found to have made its operators millions of dollars in profit.
The company that discovered the campaign, called PIXM, says the attackers used phishing pages to steal Facebook login credentials, then re-routed the victims to a website filled with ads, and surveys.
From our news piece: "The premise is simple: the crooks created numerous phishing sites where victims would be lured into giving away their Facebook credentials. After that, two things would happen. One - they would be redirected to a website with ads, surveys, and other means of revenue generation for the operators, and two - the victims’ Facebook accounts would be used to further spread the campaign, via Messenger."

Emotet seen stealing Chrome user profile data
The infamous Emotet botnet now has a module capable of stealing credit card data saved in Google Chrome user profiles. The module, discovered earlier this week, steals names, credit card expiration dates, and numbers, and sends the data to a command & control server.
From our news piece: "Today, it is able to steal sensitive and personally identifiable data, spy on traffic moving through compromised networks, and move laterally.
Cybersecurity researchers from ESET recently said Emotet has had a significant increase in activity this year, "with its activity growing more than 100-fold vs T3 2021."

Bluetooth leaves a unique, trackable "fingerprint"
Cybersecurity researchers from the University of California, San Diego, have discovered a unique property for each individual Bluetooth chip in existence, and believe it can be used to track people's whereabouts.
Each individual Bluetooth chip has a tiny imperfection created during the manufacturing process. In a sense, despite the fact that they’re being produced at scale, and have measures in place to prevent identification, all of these chips are somewhat unique.
From our news piece: "To track the chip, the potential attacker would first need to identify the device, or “capture” its unique “fingerprint”, in order to identify that tiny imperfection. After that, they need a radio receiver capable of recording raw radio signals. Apparently, this can be done with off-the-shelf gear costing no more than $150."

Identity theft protection - does it really work?
Identity theft is something that can happen to anyone. Consequently, one must ask the question: can we really protect against it?
Considering that multiple companies offer identity theft protection, as well as credit monitoring services, one might say the answer to that question is - Yes.
But are these companies really reliable? Are they truly offering a solid service, or nothing but vague promises? Also, can you protect your identity without signing up for one of these services? Read our in depth guide here, to learn more.

Apple's M1 chip has an "unpatchable" flaw, researchers warn
Apple's hugely popular M1 chip has a major security flaw that, according to researchers, can't be fix with a software update. Cybersecurity researchers from the MIT Computer Science and Artificial Intelligence Laboratory says the flaw exploits something known as pointer authentication code,
From our news piece: "PACMAN, the exploit that the MIT researchers designed, relies on a combination of software and hardware exploits that test whether a signature is accepted, and since there are only a finite number of possible signatures, it is possible for PACMAN to try them all, find out which one is valid, and then have a separate software exploit use that signature to bypass this final defense mechanism in the M1 chip."

Microsoft's update addresses key BYOD challenge
Microsoft has just upgraded its Defender for Endpoint (MDE) tool to be able to "contain" unmanaged and compromised Windows devices.
If a device on a corporate network is deemed infected, MDE can essentially lock it out, to prevent threat actors from moving laterally, and thus contain the threat.
From our news piece: That way, in case a threat actor managed to weasel their way into a network, they’ll be stopped in their tracks, before they can do any serious damage. Mapping out the target network, identifying key endpoints, and exfiltrating sensitive data from all the devices, is key, for example, in ransomware attacks.

Microsoft fails to renew a certificate, breaks site
Microsoft has failed to renew a certificate for one of its important pages, breaking it in the process. The certificate for the Windows Insider software testing program expired on Thursday, June 9.
From our news piece: "Those who tried to visit the site during that time were met with the usual “Your connection is not private” message, and users of Chrome, Firefox, or Safari, were advised by their browsers not to proceed."

Discovered flaw allows crooks to break into physical offices
Cybersecurity researchers from Trellix recently discovered multiple vulnerabilities in an industrial control system (ICS), which could have lead to crooks getting physical access to otherwise off-limits premises.
The flaws were found in Carrier’s LenelS2 access control panels, manufactured by HID Mercury. The researchers are saying these are used by organizations across healthcare, education, transportation, and government physical security.
From our news piece: "What they found was a total of eight vulnerabilities, one of which even has the maximum vulnerability score of 10. Trellix, whose product was vetted by the US federal government, urged all customers to apply vendor-issued patches immediately."

How to stay safe from identity theft
Criminals looking to steal people's identities have plenty of offers to choose from. With Covid-19 scattering people into a remote working environment, they've never been so susceptible to social engineering.
They're also no longer behind the thick walls of corporate cybersecurity.
That being said, it has never been more important to keep the remote workforce educated, safe, and productive.
To learn more about staying safe from identity theft, both as a corporation, and as an individual, make sure to read our in-depth guide here.

Firefox "most secure browser", Mozilla claims
Mozilla has rolled out a new upgrade for its Firefox browser, after which it boldly declared it as the most private and secure of all browsers.
The new version comes with Total Cookie Protection turned on by default for all users. The feature locks cookies only to the site where they were created.
From our news piece: Total Cookie Protection had been introduced back in 2021, but users had to toggle it on - although it was activated whenever a user switched on Firefox privacy mode.

New Linux rootkit found
Researchers have found a new Linux rootkit that can load and hide malware. Avast reports of a new rootkit called Syslogk, based on an old, open-source rootkit named Adore-Ng.
Syslogk is currently in active development, researchers are saying.
From our news piece: When the Syslogk loads, it first removes its entry from the list of installed modules, meaning the only way to spot it is through an exposed interface in the /proc file system. Besides hiding itself from manual inspection, it is also capable of hiding directories that host the dropped malware, hiding processes, as well as network traffic. But perhaps most importantly - it can remotely start or stop payloads.

How to protect your smartphone from ID theft
To say that a smartphone is a person's complete digital representation would not be an exaggeration, as people add things like bank accounts, payment apps, password managers, social media accounts, and tons of photos.
That also makes it a major privacy and identity risk. Should a phone get stolen, it could get mined for data, and that data used for identity theft.
To learn how to protect your smartphone from theft, make sure to read our in-depth guide here.

Microsoft issues a patch for Follina
Microsoft's June 2022 cumulative update for Windows addresses the dangerous Follina vulnerability, the company confirmed. In an advisory issued earlier this week, the company urged all customers to update their operating systems as soon as possible.
From our news piece: "Discovered by cybersecurity expert Kevin Beaumont, and dubbed “Follina”, the flaw leverages a Windows utility called msdt.exe, designed to run different troubleshooter packs on Windows."

Cloudflare stops record-breaking DDoS attack
The recently mitigated HTTPS DDoS attack against an unnamed website was the "largest one ever", according to the company that prevented it - Cloudflare.
The company's Product Manager Omer Yoachimik said the attack came with 26 million request per second (RPS).
From our news piece: "Such a powerful attack was made possible thanks to threat actors using hijacked virtual machines and servers, rather than Internet of Things (IoT) devices, to send the malicious traffic , the company said."

Android malware with millions of downloads spotted
Cybersecurity researchers have recently discovered malware being distributed through Android apps with millions of downloads. Experts from Dr. Web discovered a total of nine apps that were carrying infostealers, as well as adware.
From our news piece: "While some of these may have been removed from the Play Store, people that have downloaded them in the past are still at risk, until they remove them from their endpoints, using antivirus software, or other malware-removing solutions. "
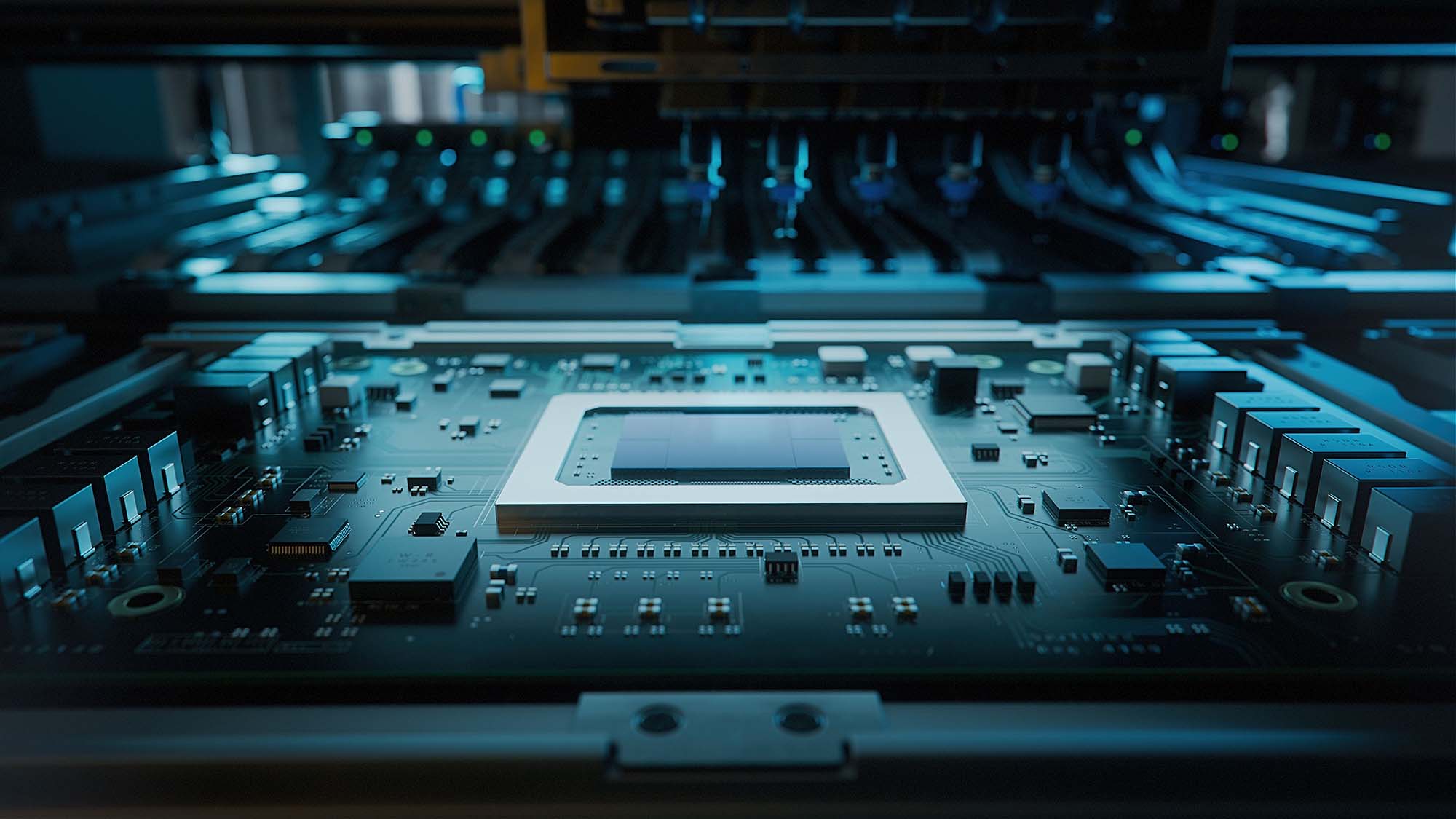
New flaw found in Intel and AMD chips
Security researchers have discovered a new type of attack that can be used against Intel and AMD chips to extract sensitive information. The attack revolves around measuring the power consumed during data processing. While a relatively old theory, the researchers have given it a new spin.
From our news piece: "Through dynamic voltage and frequency scaling (DVFS), attackers can track the time the server takes to respond to specific queries, effectively allowing them to spot changes in power consumption. It’s a relatively simple thing, researchers said. They’ve dubbed the vulnerability Hertzbleed, and it’s since being tracked as CVE-2022-24436 for Intel devices, and CVE-2022-23823 for AMD."

How to check if your ID has already been stolen
If you've ever done anything online, there's a slight chance your identity has already been stolen. With numerous data breaches occurring every month, and millions of data records flowing into the hands of threat actors, the risk has never been greater.
If you're looking to find out whether or not your identity has already been stolen, make sure to check out our in-depth guide here.
Microsoft criticized for slow patching
A number of cybersecurity companies have criticized Microsoft, saying the company's patching practices are too slow and lacking in transparency.
The likes of Orca Security and Tenable have slammed Microsoft for the way it handled issues regarding Azure's Synapse Analytics.
From our news piece: Tenable has also voiced its dissatisfaction with how the Synapse issue was resolved, the publication further found. In a LinkedIn post, the company’s Chairman and CEO, Amit Yoran, said there’s a “lack of transparency” Microsoft showed, just a day before the embargo on privately disclosed vulnerabilities lifts.

Microsoft has a new way for you to protect your devices
Microsoft has expanded its software subscription package and now offers better ways to protect against cybercriminals.
As reported in a blog post, Microsoft 365 now have access to Microsoft Defender for Individuals, “a new security app designed to keep individuals and families safer online”.
From our news piece: "The application gives users a way to both protect and monitor all their devices - across macOS, iOS and Android, as well as Windows - from a single, unified dashboard. It also offers up tips and suggestions to help users further strengthen their protections."

Capital One hacker convicted
Paige Thompson, a former employee of Amazon Web Services (AWS) was found guilty of the major data breach that Capital One suffered back in 2019. As per media reports, it was proved Thompson used her position within the company to exfiltrate data on millions of Capital One users.
From our news piece: "Using the alias “erratic”, she apparently built a tool that helped her search for misconfigured accounts on AWS. What she found was more than 30 such instances owned by Amazon clients, including Capital One. She then proceeded to mine that data and install cryptocurrency miners on some AWS servers."

Are you at riks of identity theft?
While the risk of identity theft only increased, since the internet's inception, it isn't equal for all participants. Your identity won't be stolen if you can keep a handle on it. Consequently, fraud cannot be committed in your name, if your name isn't stolen.
But can you know, with absolute certainty, if you are at risk of ID theft, and how big of a risk that is? To learn more, make sure to check out our in-depth guide here.
Major flaw puts millions of WordPress sites at risk
A high-severity vulnerability was recently discovered in a hugely popular plugin for WordPress, putting millions of websites at risk of total takeover.
Researchers have found Ninja Forms, a forms plugin for WordPress, have been carrying a major flaw, since version 3.0.
From our news piece: "According to Wordfence threat intelligence lead Chloe Chamberland, remotely executing code via deserialization allows threat actors to completely take over a vulnerable site. To make things even worse, the flaw was observed being abused in the wild."

QNAP NAS devices under attack again
Users of QNAP's network-attached storage (NAS) devices are under attack again, the company said. Similar to previous incidents, the ech0raix ransomware operator is behind the attack, infecting the endpoints with ransomware.
From our news piece: "Users first started recording being hit with ransomware on June 8, and since then, the number of ID Ransomware submissions has been quickly piling up. So far, a “few dozen” samples have been submitted, but the actual number of successful attacks is probably a lot higher since some victims won’t be using the ID Ransomware service to detect the strain that attacked them, the publication states."

Sophos Firewall flaw abused in the wild
A zero-day in the Sophos Firewall, which was spotted in late March this year, was being abused in the wild in the weeks following up to the patch, researchers have said.
Experts from Volexity said DriftingCloud successfully exploited CVE-2022-1040 against a number of unnamed entities.
From our news piece: "The group used the flaw to bypass authentication, and run arbitrary code on the victims’ endpoints. The flaw affects the User Portal and Webadmin of Sophos Firewall, and the threat actors managed to install webshell backdoors and other malware."

Chrome extensions could serve as trackers, researchers warn
Users could be tracked across the web - through the extensions they have installed on their browsers. Researchers are saying that the extensions could complement other characteristics, such as display resolutions, or GPU performance, as advertisers "fingerprint" visitors.
From our news piece: "A web developer going by the alias ‘z0ccc’ built a fingerprinting site called “Extension Fingerprints” that does just that: fingerprints people based on their Google Chrome extensions. Some extensions require the use of a secret token to access a web resource as a contingency measure, the researcher says, but there are still methods to learn if an extension is installed on the endpoint or not."

Windows Server updates breaks VPN setups
Microsoft's new Windows Server update is breaking a bunch of VPN setups, researchers have found. The company recently released four separate patches, KB5014746, KB5014692, KB5014699, and KB5014678. These have been triggering a "wide range" of issues, including some with VPN and RDP connectivity on devices with Routing and Remote Access Service enabled.
From our news piece: "One of the issues was quite severe, the publication further wrote, as it resulted in servers freezing for a couple of minutes, after a client connects to the RRAS server with SSTP."

BRATA gets new bells and whistles
One of the nastiest Android banking trojans, BRATA, has just gotten a huge upgrade, making it that much more dangerous.
Cybersecurity researchers from Cleafy found that the Brazilian Remote Access Tool for Android now has new means of obtaining GPS location data, new ways to send and receive SMS messages, and new methods of getting permissions.
From our news piece: Perhaps the biggest danger coming from BRATA is the fact that if it is successful in wiping the funds from a target account, or if it spots an antivirus scanning for it, BRATA will restore the device to factory settings, wiping all contents from the device.

Strengthen the security of your gear this summer
During summer, the volume of work for the majority of the workforce quiets down, making it an ideal time to tighten up on the security of the gear used for both work and play.
Those looking to freshen up their memory on how to best protect their devices this summer, need look no further than our in-depth guide right here.
The summer is right around the corner, why spend it worrying over data breaches?

Windows shortcut files abused to distribute malware
Cybersecurity researchers recently spotted two threat actors distributing malware through weaponized Windows shortcut files.
According to a report from Varonis, Emotet, and Golden Chickens, were seen distributing .ZIP archives via email, which carried .LNK files capable of triggering the download of malicious payloads.
From our news piece: "In this particular campaign, the threat actors replaced the original shortcut icon with that of a .PDF file, so that the unsuspecting victim, once they receive the email attachment, can’t spot the difference with a basic visual inspection."

Is Acrobat silently sabotaging your antivirus?
Is Acrobat silently sabotaging your antivirus? Cybersecurity researchers from Minerva Labs seem to think so. In their newest analysis, they found that the program is blocking most antivirus software from scanning PDF files at launch.
From our news piece: "Minerva spotted Adobe Acrobat scanning for DLL files from 30 security products, to see if they’re loaded into memory while it’s active. These products also include the industry’s heavy hitters, such as Bitdefender, Avast, Trend Micro, Symantec, Malwarebytes, ESET, Kaspersky, F-Secure, Sophos, and Emsisoft."

Here's an easy way to spot spam
There's an easy way to spot spam messages, researchers are saying. According to the Expel Quarterly Threat Report Q1 2022, most spam messages have one thing in common - an empty subject line. There are other common subject lines, such as "Fax Delivery Report”, or “Business Proposal Request”.
From our news piece: "There are other ways to spot malicious emails, as well, researchers further uncovered. Most of the threat actors distributing these messages come from non-English speaking communities, oftentimes resulting in emails marred with grammar and spelling errors."

NSA warns against turning off PowerShell
The US National Security Agency (NSA) has suggested organizations don't disable PowerShell, but rather use it as a tool against cybercrooks. In a security advisory, published alongside cybersecurity centers in the UK and New Zealand, the NSA says PowerShell can be used in forensics, and for incident response.
From our news piece: "The advisory comes with a number of recommendations, including leveraging PowerShell remoting, or using Secure Shell protocol (SSH) to improve the security of public-key authentication."

QNAP urges users to apply the latest patch ASAP
QNAP, the manufacturer of network-attached storage devices, has urged its users to apply the latest patch as soon as possible, as it plugs holes allowing threat actors to remotely execute malicious code.
The flaw is found in PHP, it was said, and affects QTS 5.0.x and later, QTS 4.5.x and later, QuTS hero h5.0.x and later, QuTS hero h4.5.x and later, and QuTScloud c5.0.x and later.
From our news piece: "Users are advised to patch to version QTS 5.0.1.2034 build 20220515 and later, as well as QuTS hero h5.0.0.2069 build 20220614 and later. The flaw isn’t exactly new, the company further clarified. It was known for approximately three years, but apparently, wasn’t a viable option to exploit until now. "

Open-source software in apps is risky business, researchers claim
Using open-source software to develop modern applications is a major security risk, researchers from cybersecurity firm Snyk have found. Together with the Linux Foundation, the researchers have also found businesses woefully underprepared to tackle such risks.
From our news piece: "Based on a survey of more than 550 respondents, as well as data pulled from 1.3 billion open source projects via Snyk Open Source, the report states that two in five (41%) firms are not confident in the security of their open source code."

New Windows update fixes broken VPNs
Three new patches from Microsoft, currently in preview mode, are aiming to fix connectivity issues that arose in the last patch.
With the earlier cumulative update, users started reporting issues with Wi-Fi hotspots and VPN connectivity.
From our news piece: "The fix is great news for those affected by the flaw, but for the time being, only these three versions of the OS resolve the issue. Meanwhile, people using Windows 10 other than 1809, Windows 8.1, or Windows 7 SP1 will have to wait a bit longer (probably until the next Patch Tuesday)."
HDMI dongle keeps your ports safe from intrusions
A security enthusiast going under the name "kingkevin" recently built a new dongle that prevents HDMI ports from being abused by threat actors.
The so-called HDMI Firewall blocks all communication going in and out of the HDMI port that is not directly related to audio or video.
From our news piece: "An HDMI connector allows for the passthrough of more than just audio and video data. A couple of parallel protocols are moving extra data through, including High-bandwidth Digital Content Protection, or HDCP. "

Potent Android malware discovered
A newly discovered Android malware strain has even Google's researchers worried.
In a recently published blog post, Google's researchers confirmed the existence of Hermit, malware built by an Italian software company, and used by state-sponsored actors to target high-profile individuals.
From our news piece: The malware is extremely potent, and once installed on the device, can reach out to its command & control (C2) server to pick up numerous modules, including call loggers, audio recorders (both ambient and phone calls), photo and video harvesters, SMS and email readers, and location trackers.

Malicious Python packages leaking AWS secrets
Cybersecurity researchers from Sonatype have found a number of Python packages that were leaking AWS secrets to the public.
According to the company's Ax Sharma, packages: loglib-modules, pyg-modules, pygrata, pygrata-utils, and hkg-sol-utils, were exfiltrating people’s secrets, such as AWS credentials and environment variables.
From our news piece: We don’t know exactly how many people have had their data exposed(opens in new tab), although Sharma said the researchers found “hundreds of TXT files containing sensitive information and secrets”.

Another crypto bridge hacked, millions lost
Cryptocurrency bridge company Harmony bridge was breached recently, with crooks making away with millions of dollars in the Ether currency.
"Bridges" are products that allow tokens to be interchangeable across various blockchains.
From our news piece: "The attack is the work of an as-yet-unknown cybercriminal who managed to siphon out 85,867 Ether tokens from the Harmony bridge, worth approximately $105 million at press time."

Ransomware costs schools and colleges billions
Ransomware attacks against schools and colleges in the US are costing these organizations billions of dollars, new research has found.
Comparitech says that in 2021, there had been 67 individual attacks, affecting almost 1,000 schools.
From our news piece: "Comparitech’s estimate is that these attacks had cost the institutions $3.56 billion in downtime alone, also adding that secondary expenses (recovery costs, restoring computers and data, reactivating systems, future incursion prevention, etc.) were likely to be “astronomical” to already-stretched budgets."

Major OpenSSL vulnerability found on Intel-powered devices
OpenSSL 3.0.4 was found to be carrying a bug that allows third parties to execute code at a distance. The vulnerability is only present on CPUs with the AVX512 extension, though.
From our news piece: "The version was released in an attempt to fix an earlier command-injection vulnerability (CVE-2022-2068) which, itself, wasn’t able to fix an even earlier issue - CVE-2022-1292."

Hybrid working exacerbates firmware cyberthreats
IT teams are fighting an uphill battle with firmware updates, security researchers are saying. The move to hybrid working has expanded the threat landscape by quite a lot, leaving IT teams struggling.
From our news piece: "The poll of 1,100 IT leaders discovered that for more than eight-in-ten (83%), firmware attacks against laptops and PCs are now a significant threat. Furthermore, for three-quarters (76%), firmware attacks against printers are also a major threat."

Excel files still found distributing Emotet
Cybersecurity researchers from Netskope have found hundreds of Excel files carrying the dreaded Emotet trojan, despite the fact that Microsoft restricted all macros, by default.
This means that many workers are yet to update their systems and, as such, pose a major risk to their organizations.
From our news piece: "After doing a search for similar files on VirusTotal, the team discovered 776 malicious spreadsheets, submitted in just a week and a half, during June. Most of the files share the same URLs and some metadata, drawing the researchers to conclude that it’s probably the work of a single threat actor."

New phishing campaign leverages Messenger's chatbot
Cybersecurity experts from SpiderLabs have discovered a new phishing campaign that leverages Facebook's Messenger to steal people's login credentials.
The campaign uses a chatbot to distribute the malicious link which would otherwise be picked up by email security tools.
From our news piece: "Thankfully, the content of the email contains a few red flags that should help users identify the message as fraudulent.
For example, there are a few spelling and grammar mistakes in the body of the message, and the recipient’s name appears as “Policy Issues”, which is not how Facebook handles such cases."

AMD looking into a potentially large data breach
Crooks are claiming to have obtained "450 Gb" of sensitive data from AMD, and are now looking to sell the data back to the company. To do that, they've employed a third party, a threat actor known as RansomHouse, serving as a middleman.
From our news piece: "The group says it has “more than 450Gb” of AMD data, including "network files, system information, as well as passwords", after a breach that took place in January. It is unclear whether the statement is meant to read 450 gigabytes (GB) or gigabits (Gb); if the latter, the group is claiming to hold roughly 56GB of AMD data."

Kids found selling malware on Discord
Cybersecurity researchers Avast have found a Discord server full of minors, where they build, distribute, and sell, different malware families. To join the group, and essentially become the user of the malware-as-a-service, one must pay a fee, which ranges from anywhere between €5 and €25. Avast says up to 100 accounts have paid to access one such group.
From our news piece: "The group in question builds and exchanges various types of malware, including those with password-stealing capabilities, infostealers, those capable of mining various cryptocurrencies for the attackers, and in some cases, even running ransomware attacks."

Microsoft patches flaw that allowed for container cluster hijacking
Microsoft has fixed a flaw sitting in Service Fabric, the company announced earlier this week.
The flaw, dubbed "FabricScape" is a high-severity vulnerability, as it allows threat actors to obtain root privileges on a node.
From our news piece: "Exploiting the flaw would require a little preparation; the attacker would first need to compromise a containerized workload, deployed by the owner of a Linux SF cluster. Then, the hostile code running inside the container needs to substitute an index file read by SF Diagnostics Collection Agent (DCA) with a symlink."

Employees keep using Shadow IT
Most employees don’t care that some apps are banned in the office. A new report from Cerby says more than half still use these apps, despite clear instructions from their IT departments. What’s more, they simply want the IT department to “get out of their way”.
From our news piece: “Cerby found that 60% of employees and managers believe that, by blocking an app, management actually shows it doesn’t exactly trust its employees. As a result, the employees would think less highly of their organizations.”

Google updates Workspace, limits disaster potential
Google has finally added new features to Workspace which just might save an IT manager or two, a headache. Announcing the news in a blog post, Google said that IT managers will now be getting notifications every time critical and sensitive” changes are made to their configurations.
From our news piece: “Administrators can expect to get an alert when the primary admin changes, when an SSO profile is added, updated or deleted, and when the password gets reset for super admins.”

Google blacklists dozens of hack-for-hire addresses
Search engine powerhouse Google expanded its domain blacklist, limiting the destructive potential of dozens of hack-for-hire groups across the world.
Announcing the news in a blog post, the company's Shane Huntley said 37 new domains and websites were added to its Safe Browsing feature.
From our news piece: "These domains, which include the likes of myproject-login[.]shop, mail-goolge[.]com, or rnanage-icloud[.]com, have been split into three distinct categories: groups from the UAE, India and Russia. The company’s CyberCrime Investigation Group, Huntley further explained, is sharing relevant details and indicators with law enforcement agencies."

Android users warned of new potent malware
Android smartphone users are being warned of a new malware that signs them up for premium services without their consent.
Microsoft says that toll fraud, as the scheme is known, is "one of the most prevalent" types of fraud, and that it just keeps on evolving.
From our news piece: "These apps use specific network operators, running their operations only if the compromised endpoint is subscribed to one of its target operators. If these conditions are met, the app will subscribe to a service, completely out of sight for the device owner, and will even intercept one-time password SMS messages and other notifications."

Email accounts used for OpenSea leaked
Email addresses that people used to register an account with OpenSea have been leaked, it was confirmed late last week. Now, the company issued a warning to all its users, to keep both eyes and ears open for potential phishing attacks.
From our news piece: "Announcing the news, the company’s Head of Security, Cory Hardman, said the leak happened when an employee of email delivery service Customer.io downloaded OpenSea’s email database. OpenSea users should now be extra careful when receiving emails claiming to be from the marketplace. Its official email domain is opensea.io, and everything else can be considered fraudulent. Hardman said that emails coming from domains such as opensea.org, opensea.xyz, and opeansae.io should be ignored."

Google addresses high-severity flaw in Chrome
Google has released a new version of its Chrome browser, as it moves to close a high-severity gap. In a recent announcement, the company said that its latest build 103.0.5060.114 addresses a high-severity heap-based buffer overflow weakness, tracked as CVE-2022-2294.
From our news piece: "Google Chrome is usually updated automatically, as soon as the browser is opened by the user, so there is a good chance many installations have already been patched. However, Google says it may take a number of weeks for the patch to make its way to the remainder."

Raspberry Robin found in hundreds of networks
Raspberry Robin, a nasty Windows worm that's being distributed through malicious thumb drives, has been spotted in "hundreds" of corporate networks Microsoft is warning.
The company has warned organizations subscribed to Microsoft Defender for Endpoint via a newsletter, the media reported. The good news is that the malware is yet to be leveraged by the threat actors.
From our news piece: "Raspberry Robin was first identified late last year, when researchers from Red Canary discovered a “cluster of malicious activity”. The malware is usually distributed offline, via infected USB drives. After analyzing an infected thumb drive, the researchers discovered that the worm spreads to new devices via a malicious .LNK file."

Sensitive data on a billion Chinese stolen, hacker claims
An anonymous threat actor is claiming to have stolen sensitive data on more than a billion Chinese citizens, the media reported earlier this week. If the database, 23TB in size, turns out to be legitimate, it will be the largest cyber heist ever recorded.
The threat actor claims to have taken the database from a Shanghai police department.
From our news piece: "The data is said to contain people’s names, addresses, birth places, national ID numbers, phone numbers, and information on any criminal cases the individuals be involved in. The Wall Street Journal claims to have verified at least a small portion of the data."

China nixes thousands of malicious mobile apps
The Chinese government has doubled down on malicious apps, blocking thousands of apps that were impersonating big brands and government agencies.
The country's Cyberspace Administration of China, the government organization tasked with overseeing the internet, said it had blocked more than 42,000 malicious apps since the start of the year.
From our news piece: "That brings the total number of apps banned to 514,000, while the number of blocked websites now exceeds 3.8 million. In the majority of instances, the crooks impersonated major brands, such as JD. Sometimes, the apps would entice victims into buying products at a cheaper price than available elsewhere, and sometimes they would advertise amazing investment opportunities. In other cases, they would simply infect victims with malware."

Department of Defense wants hackers' help to tighten up on security
The US government wants to tighten up its cybersecurity protections, and it's asking the hacking community's help to do so.
Three DoD departments: Chief Digital and Artificial Intelligence Office (CDAO), the Directorate for Digital Services and the Department of Defense Cyber Crime Center (DC3) announced a new bounty hunting program, called "Hack U.S."
From our news piece: "The Department of Defense (DoD) has a budget of some $110,000 for white-hat hackers that discover dangerous flaws. Critical severity reports will earn hackers $1,000 a piece, high severity ones $500, and there's a $3,000 reward for those in additional special categories."

Lazy zero-day fixes create new problems
When businesses move too fast to address a zero-day, they often create secondary issues, Google has reported.
Researchers from Google Project Zero have found that out of 18 zero-days found in major software this year, half were just repurposed zero-days patched last year.
What’s more, four of the zero-days discovered this year are spin-offs of bugs originally identified in 2021.
From our news piece: "In total, there were more zero-days discovered in 2021 than in the past five years. But while sloppiness may be a contributing factor, it’s not the only cause of this rise, it was said. Google itself has patched four zero-day vulnerabilities in its Chrome browser, this year alone."

Hive migrates to Rust
Popular Ransomware-as-a-Service, Hive, has fully migrated its code, from Go, to Rust, researchers have found. This move has made it more resilient to antivirus software, and improves its encryption.
From our news piece: "The new variant also uses string encryption, making it somewhat harder to detect, and the underlying algorithms have changed too. The Rust version of Hive uses Elliptic Curve Diffie-Hellmann (ECDH), with Curve25519 and XChaCha20-Poly1305 (authenticated encryption with ChaCha20 symmetric cipher)."

Supply chain attack compromises hundreds of sites
Threat actors known as IconBurst have created a couple of malicious NPM modules, which have since been downloaded thousands of times, researchers have said. By downloading and using malicious modules, the developers have essentially compromised their web products.
From our news piece: "This is a popular attack technique known as typosquatting. The attackers essentially try and assume the identities of legitimate developers. Then, developers who are in a hurry, or who don’t pay attention to details such as NPM names, download the modules and embed them in their work."

US chooses encryption algorithms for the post-quantum world
The U.S. government has chosen four new encryption algorithms which should protect its communications from being decrypted by quantum computers.
The four encryption algorithms will become part of the National Institute of Standards and Technology's (NIST) post-quantum cryptographic standard, the organization said in its announcement, adding that the standard should be finalized in “about two years”.
From our news piece: "The algorithms are designed for two main tasks: general encryption, and identity authentication. For the former, NIST selected the CRYSTALS-Kyber algorithm, which operates relatively small encryption keys, and moves relatively fast. The remaining three algorithms are dedicated to digital signatures, and those include CRYSTALS-Dilithium, FALCON and SPHINCS+."

Marriott suffers yet another data breach
Marriott hotels have had their data stolen, once again. An unknown threat actor compromised the hotel's network for less than a day, which was enough time to steal data on some 400 people, the company confirmed.
The information was in archived files that weren't detected by scanning tools Marriott usually uses to protect its digital valuables.
From our news piece: "Apparently, the threat actor targeted the BWI Airport Marriott, in Maryland, USA. It obtained reservation documents for flight crews, as well as corporate credit card numbers for an airline or travel agency. Marriott further said that most of the data was “non-sensitive internal business files regarding the operation of the property.”

Over half of G20 government websites have tracking cookies
Government websites of most countries in the G20 group are brimming with third-party tracking cookies, researchers are saying. After analyzing more than 5,000 government websites, IMDEA found that 90% allowed its visitors to be tracked.
Of those cookies, more than half belong to third parties, such as social media networks. In some cases, as many as 90% came from known third-party trackers.
From our news piece: "These websites should not serve cookies at all, IMDEA argues. Not only does that ruin any trust people might have in their governments, but it also allows for “large-scale surveillance, monitoring, and tracking. If this takes place from third parties it is worrisome as it shows bad website design that relies on external entities that can monitor interactions [between] the public [and] the government," the organization said."

Microsoft Azure VMs get a new security feature
Microsoft has introduced a new feature in its Azure offering, allowing users to create disks on local virtual machine storage, that's not saved to remote Azure storage.
Called Ephemeral OS disks, the feature's goal is to improve data confidentiality, as with Ephemeral OS disks, the data never makes it to an offsite data center. The feature is available in all regions, the company confirmed.
From our news piece: "Microsoft says Ephemeral OS disks are ideal for stateless applications, where no client data generated in one session is used in the next session. In addition, Microsoft explained these discs can be ideal for use cases that require lower latency, similar to a temporary disk, or the ability to fast reset or reimage VMs and to scale set instances to the original boot state."

Microsoft postpones blocking macros in Office apps
Microsoft has recently decided to postpone blocking Visual Basic for Applications (VBA) macros in Office applications by default, but it seems the decision is only temporary.
Explaining the decision in a blog post, Microsoft principal product manager, Kellie Eickmeyer stated that the company made a decision after receiving user feedback. It will now look to make additional changes to enhance usability.
From our news piece: "The company reportedly planned to have Office users enable macros by specifically needing to unblock the option in the file’s properties. These steps, it claims, will require user training, which is something Microsoft is now allegedly looking to simplify."

Free VPN services. Useful, or risky?
Right now, almost two-thirds of TechRadar Pro readers from the States have switched from a paid VPN subscription, to a no-fee plan. This is according to a TechRadar Pro exclusive report, which also states that in countries with tough internet restrictions the number of people considering a free tool is even bigger.
From our news piece: "After gathering insights from 2,000 internet users across China, Saudi Arabia, Vietnam and United Arab Emirates (UAE), research conducted by no-fee VPN provider Hola together with market research firm Vanson Bourne revealed that about 80% of respondents would consider using a free tool to bypass online censorship. At the same time, many freebies are also infamous for failing to protect their users' privacy."

Mangatoon leaks user data
Mangatoon, a mobile app available on both iOS and Android, has leaked personal data on 23 million of its users, the media are reporting.
The breach allegedly happened in may, and included email addresses, genders, social media account identities, auth tokens, and salted MD5 password hashes.
From our news piece: "The instigator behind the attack was apparently a hacker known as “pompompurin", who has previously claimed responsibility for the 2021 FBI email hack, where the FBI’s external email system was used to send thousands of emails warning of fake cyberattack."

Ransomware operators add a search engine
Ransomware operators BlackCat have added a search engine to their website, allowing other cybercriminals, victims, as well as other visitors, to search through the stolen databases and verify the authenticity of the data, themselves.
They can also look for incriminating data to use in second-stage attacks, as well.
From our news piece: "Multiple ransomware operators are reportedly now adding the feature to their leak sites - and while some have done a poor job, as their engines didn’t exactly work as intended, others appear to have successfully pulled it off."

Honda cars hackable with a portable radio
Cybersecurity researchers from Star-V Lab recently uncovered a new flaw in Honda cars, which might result in grand theft auto. Due to a vulnerability in the car's keyfob, a threat actor can use a handheld radio and open the doors, as well as start the engine.
From our news piece: "A number of leading Honda models released between 2012 and 2022 are apparently affected by the flaw, including the Accord, Civic, C-RV and X-RV. The issue is contained within the rolling codes mechanism, including within the keyless entry system (aka the keyfob) in order to prevent replay "man-in-the-middle" attacks. "

UK pensioners' data sold on Facebook
Personal data on UK's pensioners is being sold online, and in no other place than - Facebook groups. This is according to BBC Breakfast Live, whose hosts managed to purchase the details of 1,000 British people for less than $200.
The personal data was said to include names, home addresses, email addresses, estimated net worth as well as estimated income bracket.
From our news piece: "The BBC laid the blame squarely on Meta for not scrubbing its platform clean from this type of illegal activity. Meta has responded to the allegations, saying: "We remove this content when we become aware of it and have taken down the groups in question". Unfortunately being young and a long way from home ownership might not protect you from cybercrime."

Major flaw found in AMD and Intel chips
Cybersecurity researchers from ETH Zurich have recently discovered a new vulnerability, similar to the Spectre/Meltdown flaws that sent the entire chip industry into a meltdown four years ago.
According to the researchers, the flaw allows threat actors to access kernel memory, meaning access to sensitive data such as passwords and security keys.
From our news piece: "The flaw is dubbed Retbleed, and revolves around the chips’ speculative calculations. “When computers execute special calculation steps to compute faster, they leave traces that hackers could abuse,” the researchers said."

Namco Bandai suffers a ransomware attack, threat actors claim
A known ransomware threat actor, BlackCat, announced it breached Namco Bandai, the popular Japanese video game publisher. The news was confirmed by two malware-watching groups, but not by Namco Bandai, just yet.
Namco Bandai is a well-known publisher, standing behind AAA titles such as Elden Ring, Tekken, or Dark Souls. BlackCat, on the other hand, is a major ransomware operator that's even drawn the attention of the FBI.
From our news piece: "In April 2022, the FBI issued a warning that BlackCat’s “virulent new ransomware” strain infected at least 60 different organizations in two months’ time. Back then, the FBI described BlackCat as “ransomware-as-a-service”, and said its malware was written in Rust."
Patches for Microsoft 365 on Windows 7 to end next year
Microsoft will stop patching its cloud collaboration suite, Microsoft 365, on devices running Windows 7 and Windows 8.1, early next year, the company confirmed.
The official end-of-life date is January 10, 2023, and by then, users are expected to shift to at least Windows 10, or potentially - Windows 11.
From our news piece: "For most people, support for Windows 7 - which launched in 2009 - ended in 2020. In recognition that many companies preferred to run Windows 7, Microsoft offered Extended Security Updates, a paid service that would continue to offer security patches for the dated OS. Early 2023 will see the end-of-life as security updates end for Windows 7, Windows 8.1 and Microsoft 365 apps. “New installations of Microsoft 365 Apps will [also] be blocked on Windows 8.1 devices,” according to the company."

Major firmware flaws found in Lenovo laptops
Lenovo has recently discovered, and remedied, three major vulnerabilities found in the UEFI firmware, the company confirmed. The vulnerabilities, should they be exploited, would allow threat actors to bypass any installed antiviruses and deploy malicious code on the devices.
The Yoga, IdeaPad, Flex, ThinkBook, V14, V15, V130, Slim, S145, S540, and S940 Lenovo lines are all affected, counting more than 70 endpoint models.
From our news piece: "The vulnerabilities, tracked as CVE-2022-1890, CVE-2022-1891, and CVE-2022-1892, reside in UEFI firmware, and as such, are quite dangerous. Exploiting them allows threat actors to run malware during boot, effectively circumventing any antivirus programs. It also makes malware more persistent, as wiping the disk, which is considered the Hail Mary of virus elimination, doesn’t help."

Microsoft patches countless Azure DR bugs
Azure Site Recovery, Microsoft's disaster-recovery tool for Azure, has had 32 vulnerabilities patched as part of this month's Patch Tuesday.
In total, 84 vulnerabilities were addressed in the cumulative updates, including two that allowed potential remote code execution in Site Recovery, and 30 that allowed threat actors to elevate their privileges.
From our news piece: "Most of the privilege escalation flaws were caused by SQL injection vulnerabilities, Microsoft explained, adding that there were DLL hijacking vulnerabilities discovered, as well. The latter, discovered by vulnerability management experts Tenable, is tracked as CVE-2022-33675, and comes with a severity score of 7.8. "

Hackers can use Word to compromise your macOS device
A new vulnerability was discovered in macOS that, should it be abused, allows crooks to run code on the device, remotely. Using the vulnerability allows threat actors to work around macOS' App Sandbox rules and enable macros in Word documents.
"Despite the security restrictions imposed by the App Sandbox’s rules on applications, it’s possible for attackers to bypass the said rules and let malicious codes “escape” the sandbox and execute arbitrary commands on an affected device,” the company explained.
From our news piece: "The flaw was discovered by the Microsoft 365 Defender Research Team and reportedly fixed by Apple on May 16. The problem starts with Word’s backward compatibility. To make sure it works, the app can read or write files with an “~$” refix. By leveraging macOS’s Launch Services, to run an open -stdin command on a specially crafted Python file with this prefix, the attacker can bypass the sandbox."

Most powerful botnet ever discovered
A newly discovered botnet just might be the most powerful, ever. That is, at least, what cybersecurity experts from Cloudflare are saying. The company has recently discovered an evolved version of Meris, and dubbed it Mantis.
This botnet may be smaller, as it makes up around 5,000 bots, but given that the majority of the devices are servers and virtual machines, its destructive capability is unmatched.
From our news piece: "The biggest Distributed Denial of Service attack on record is 26 million generated requests per second (rps), which Cloudflare says it successfully mitigated. To make things even more impressive - the requests were not done via HTTP, but rather HTTPS - a more expensive type of attacks, given that this type of attack needs extra computing power to establish a secure TLS connection. "

BlackCat ransomware grows stronger
A popular ransomware strain, known as BlackCat, is expanding its arsenal, becoming even more deadly than it previously was. This is according to new research from cybersecurity experts Sophos, which claim BlackCat's operators added Brute Ratel to the mix.
Brute Ratel is a penetration testing and attack simulation tool, similar but lesser-known that, for example, Cobalt Strike.
From our news piece: “What we’re seeing with BlackCat and other attacks recently is that threat actors are very efficient and effective in their work. They use tried and true methods, like attacking vulnerable firewalls and VPNs, because they know these still work. But they show innovation to avoid security defenses, like switching to the newer post-exploitation C2 framework Brute Ratel in their attacks,” said(opens in new tab) Christopher Budd, senior manager, threat research, Sophos.

WordPress sites hacked, used to target PayPal users
A newly discovered phishing scam was found targeting more than 400 million potential PayPal customers. According to cybersecurity researchers Akamai, which first discovered the campaign, WordPress websites with poor protection are being targeted.
From our news piece: "The scam begins with a CAPTCHA popup, helping it to lie mostly undetected. Users proceed to log into their PayPal accounts, before confirming payment details including their address, mother’s maiden name and social security number. Users are then implied a false sense of security as the scam enables them to link their email address to the account, but all this does is give the scammers access to individuals’ mailboxes."

Homeland Security spies on US citizens, ACLU claims
The Department of Homeland Security (DHS) has been using smartphone location data to spy on people, the American Civil Liberties Union (ACLU) is saying.
The Union filed a Freedom of Information Act (FOIA) lawsuit, which gave it access to 6,000 pages of records. These records are showing, the ACLU says, the DHS was able to sidestep US civil rights, by buying user data with taxpayer money.
From our news piece: "The DHS was able to bypass the law by purchasing information from two data brokers: Venntel and Babel Street. According to one highlighted document, Customs and Border Protection (CBP), a division of Homeland Security, once spent over $2 million to obtain location data from Babel Street. The ACLU also published a Venntel marketing brochure that details how the company collects data and it’s pretty insidious."

OpenDocument files used in phishing attacks
Hotels in Latin America are under attack from a threat actor using OpenDocument text files to compromise their systems. Cybersecurity researchers are saying the method is rarely seen, and that these files have a zero detection rate on VirusTotal.
OpenDocument is an open, vendor-neutral file format, recognized by the majority of productivity programs, such as Word, LibreOffice Writer, or Apache OpenOffice Writer as one of the most popular Microsoft Office alternatives.
From our news piece: "These files were being distributed, via email, to hotels in Latin America, and were presented as guest registration documents. Should the victim download and run the file, they’d be prompted to “update fields with references to other files”. The researchers describe the prompt as a “cryptic message”, and say that if the victim confirms, an Exel file opens."

Retbleed fixed on Linux, boss confirms
Linux devs have addressed Retbleed, a recently discovered Spectre-like flaw. The news was confirmed by the kernel's boss, Linus Torvalds.
In a blog post, Torvalds explained what the team did, saying the fix wasn't easy to release, and that the next version of the kernel will have to be postponed by a week.
"When we've had one of those embargoed [hardware] issues pending, the patches didn't get the open development, and then as a result missed all the usual sanity checking by all the automation build and test infrastructure we have," Torvalds wrote.
From our news piece: Last week, two researchers from ETH Zurich discovered the flaw, saying it allowed potential threat actors access to kernel memory of an endpoint(opens in new tab), which essentially means access to sensitive data such as passwords, and similar. The flaw is particularly risky in cloud environments, the researchers further said, where multiple companies share the same systems. In other words, one vulnerability could expose the secrets of multiple companies."

Fake crypto apps stealing millions, FBI warns
The FBI has warned Americans of fake cryptocurrency apps stealing millions. In a recently published report, the law enforcement agency says it spotted at least two different apps being distributed across the web, raking in more than $42 million out of 244 victims.
From our news piece: "While there are bound to be more, the FBI pointed its finger toward two unique apps - Yibit, and Supayos as some of the main culprits. Active since October and November 2021, respectively, the app operators managed to convince gullible retail investors to deposit their money into these apps, only later to withdraw them themselves. What’s more, since late 2021, some of the attackers impersonated US financial institutions for the same goal."

Creepy macOS malware discovered spying on people
Cybersecurity researchers from ESET recently discovered a malware, targeting macOS users. The malware is quite sophisticated and spies on its victims, stealing documents, email messages and attachments from them, but also logging their keystrokes and grabbing screenshots.
From our news piece: "Dubbing it CloudMensis, the ESET team further added that its relatively limited distribution suggests a targeted operation, rather than a widespread attack. The attackers, whose identities are yet unknown, did not leverage any zero-day vulnerability for their campaign, leading the researchers to conclude that macOS users whose endpoints(opens in new tab) are up-to-date, should be safe. "

Roaming Mantis moves to France
Malware known as Roaming Mantis, which has so far targeted users in Germany, Taiwan, South Korea, Japan, the US, and the UK, has roamed to France, researchers are saying.
Cybersecurity experts from SEKOIA analyzed the malware's campaign, and discovered that it's being distributed via SMS, and that is works differently, depending on whether the user runs an iOS, or an Android device.
From our news piece: "Apple users would be redirected to a phishing page where the attackers would try and trick them into giving away their credentials, while Android users would be invited to download XLoader (MoqHao), powerful malware that allows threat actors remote access to the compromised endpoint, access to sensitive data, as well as SMS apps (possibly to expand the operation further)."

Popular vehicle GPS tracker can be used to shut down cars
A popular GPS tracker, used by millions of vehicles around the world, has a couple of major vulnerabilities, cybersecurity researchers are saying.
Experts from BitSight have said the MiCODUS MV720 GPS Tracker, used by government, military, law enforcement agencies, and Fortune 1000 companies, has multiple flaws that allow threat actors to keep track of the vehicles’ location, turn the vehicles off completely, cut off their fuel, and control the devices remotely.
From our news piece: "To make matters even worse, the manufacturer doesn’t seem to be interested in fixing the flaws, at all. A report by BitSight said the MiCODUS MV720 GPS Tracker, a Chinese product, carried six high-severity vulnerabilities. These are now tracked as CVE-2022-2107; CVE-2022-2141; CVE-2022-2199; CVE-2022-34150; and CVE-2022-33944, one of which holds a severity score of 9.8."

Hackers stole two billion passwords last year
Last year, threat actors stole more than two billion passwords. This is the conclusion published in ForgeRock's new report. Besides passwords, crooks have been stealing sensitive data needed for identity theft attacks, including people’s names, addresses, Social Security numbers, dates of birth, protected health information (PHI), and payment or banking details.
What’s more, the two billion is an increase of more than a third (35%), compared to just two years ago.
From our news piece: "Most of the time, hackers sell the data on the black market, such as underground web forums and trading sites. While the passwords themselves often aren’t that expensive to purchase, they do open the gates for a number of potential attacks, from identity theft, to ransomware, and everything in between. Two years ago, there had been more than 15 billion passwords on sale, on the dark web, the same report claims. "

Neopets hacked, data on 96M people stolen
Virtual pet playground Neopets was recently breached, and sensitive data on some 69 million people stolen, the company behind the product confirmed.
The database is now for sale on the black market, with the threat actors asking for 4 bitcoin (roughly $91,500 at press time) for the information. The attackers are also offering access to the live database, for an additional fee.
TNT, the company behind Neopets, confirmed the breach in a Twitter post and said it notified law enforcement agencies, and brought in leading forensics firms to help with the investigation.
From our news piece: “It appears that email addresses and passwords used to access Neopets accounts may have been affected. We strongly recommend that you change your Neopets password. If you use the same password on other websites, we recommend that you also change those passwords," the thread states.

Microsoft to "sunset" Windows Information Protection tool
Windows Information Protection (WIP), a built-in data leak prevention tool, is being killed off, Microsoft confirmed. Instead of this feature, users will be offered Purview Data Loss Prevention (DLP), for a small fee.
"Certain capabilities within the solution known as Windows Information Protection (WIP), previously referred to as Enterprise Data Protection (EDP) will be discontinued over time," the company announced earlier this week.
From our news piece: "Unlike WIP, DLP is "deeply integrated with Microsoft Purview Information Protection to help your organization discover, classify, and protect sensitive information as it is used or shared,” he further said, suggesting that WIP’s big brother, capable of protecting data on multiple endpoints, cloud services, and third-party SaaS solutions, will take it from here. "

Atlassian finds a bunch of flaws in its products
Jira, Confluence, Bamboo, and a whole lot of other Atlassian products are carrying a number of high-severity vulnerabilities, the company confirmed earlier this week.
The flaws allow potential threat actors to remotely execute code, and escalate privileges on affected devices.
From our news piece: "Atlassian recently issued a warning, which details “Servlet Filter dispatcher vulnerabilities”. The first vulnerability is tracked as CVE-2022-26136, an arbitrary Servlet Filter bypass, allowing threat actors to bypass custom Servlet Filters that third-party apps use for authentication. All they’d need to do is send a custom, malicious HTTP request."

FBI returns money taken in ransomware attacks
The FBI said it managed to recover roughly half a million dollars, that multiple entities, including two hospitals, were forced to pay in ransom, last year.
To make things even better, it also managed to analyze the ransomware sample used in the attack, and identify the attackers as Maui, a North Korean, state-sponsored threat actor.
From our news piece: "The Kansas hospital had paid some $100,000 in cryptocurrencies in exchange for the decryption key, while another medical services provider in Colorado had paid $120,000 shortly after. Following the money helped the FBI identify an “undisclosed number” of additional payments, amounting up to $280,000, with the total amount seized in May 2022 amounting to some $500,000."

Windows 11 gets a new security feature
From now on, Windows 11 has Account Lockout Policy activated by default, in a move which should limit Remote Desktop Services attacks.
Microsoft recently said that it introduced the feature with Windows 11 Insider Preview 22528.1000. It locks down Windows accounts for 10 minutes, if the user fails to submit proper login data ten times in a row.
Microsoft hopes this move will limit brute-force attacks.
From our news piece: "Win11 builds now have a DEFAULT account lockout policy to mitigate RDP and other brute force password vectors," David Weston, Microsoft's VP for Enterprise and OS Security, tweeted. "This technique is very commonly used in Human Operated Ransomware and other attacks - this control will make brute forcing much harder which is awesome!"

Twitter accounts for sale
A hacker going by the name "devil" is selling details on 5.4 million Twitter accounts, the media reported earlier this week. Apparently, the person behind the sale managed to abuse a vulnerability that Twitter patched earlier in the year, and used it to get email addresses and phone numbers associated with various Twitter accounts.
"Devil" is selling the database for at least $30,000 and claims it includes details from celebrities and "OGs".
From our news piece: "The database includes public-facing data, email addresses used to register the account, and phone numbers. While not having passwords included in the data set definitely helps with security, email addresses and phone numbers could still be used for other forms of phishing, identity theft, and maybe even full account takeover.

Macros in downloaded Office files finally blocked
Microsoft has started rolling out an update for its Office suite, in which any macros found in downloaded files will be blocked. The company announced the change earlier this year, but then decided to postpone it as it worked on usability issues.
From our news piece: In an announcement following the rollout, Microsoft explained what “enhanced usability” actually meant, and it would seem that it came down to the language of the warnings: “Based on our review of customer feedback, we’ve made updates to both our end user and our IT admin documentation to make clearer what options you have for different scenarios,” Microsoft explained. “For example, what to do if you have files on SharePoint or files on a network share. Please refer to the following documentation: For end users, A potentially dangerous macro has been blocked; For IT admins, Macros from the internet will be blocked by default in Office."

Malware found hiding in cracks and keygens
Amadey Bot, malware capable of stealing sensitive information and dropping additional malicious payload, was found hiding in cracks for pirated software, as well as keygens.
The discovery was made by cybersecurity researchers from AhnLab, which are saying the malware is quite persistent, too.
From our news piece: "These cracks and keygens often trigger false positive alerts with antivirus solutions, which makes them an ideal mule to carry malware, especially if the malware can act fast enough, before the victim re-enables the antivirus program. That’s exactly the case here, as AhnLab spotted that through keygens and cracks, threat actors have been distributing SmokeLoader, a malware dropper coded to infect the endpoint with Amadey Bot."

Calculator abused to run malware
Calculator, one of the oldest and most beloved Windows tools, was found being abused by threat actors to distribute Qbot. This old and popular malware is usually used to infect the target devices with Cobalt Strike beacons.
From our news piece: "It is also worth mentioning that this attack does not work on Windows 10, or Windows 11, but works on Windows 7, which is why the threat actors bundle the Windows 7 version. The campaign has been active since July 11, and apparently, is still active at press time.

Dutch schools limiting the use of Google's products
Until Google makes changes to the way it handles user data, schools and other educational institutions in the Netherlands will only be able to use its tools under certain conditions. The Dutch Ministry of Education has given the orders, after consulting with both Google, and other tech giants, as well.
From our news piece: "Google, specifically, said new versions of its OS and browsers would be released next year. Until then, schools and education institutions are to adhere to the abovementioned orders. When Google releases the new versions, they will be evaluated, and next recommendations given."

Anti-vax dating site exposes user data
Unjected, a dating site designed for people who did not want to get vaccinated against Covid-19, leaked personally identifiable data on all 3,500 of its users, the media reported.
A cybersecurity researcher GeopJr discovered that the site was published live with the debug mode activated, which gave free access to the dashboard to whoever knew where to look.
From our news piece: "As an admin, the user can change pretty much anything on the site, add or remove pages, edit, or delete, all of the posts, as well as the site’s backups. The admin also has access to the entire user database and all of the details listed in there which, in this particular case, include names, dates of birth, email addresses, and (optionally), postal addresses. This data can be abused for identity theft, for example."

Chrome wants to help you with your passwords
Google's famed browser, Chrome, will soon get a new feature that will help users create strong passwords. Instead of relying on third-party services, as it was the case until now, users will be able to check the safety of their login by having Chrome tell them just how strong their passwords are.
From our news piece: "The tool is included within an upcoming build of ChromeOS, where it is given the self-explanatory name "Password Strength Indicator". "Enables password strength indicator when typing a password during a sign-up and password change flows," the description reads, suggesting that the tool will only apply for users creating new passwords, or when changing an existing one. The feature is noted as being "approved(opens in new tab)", meaning it will currently be in testing and development, with a wider public release expected sometime soon."

32-bit Linux to miss out on a major security update
64-bit Linux kernels were recently patched against Retbleed, a variant of the dreaded Spectre vulnerability. It was now announced that 32-bit kernels will not be getting the same update. This was confirmed by Intel’s Pawan Gupta, who answered a couple of hot questions on the lore.kernel.org mailing list.
From our news piece: "Intel is not aware of production environments that use 32-bit mode on Skylake-gen CPUs. So this should not be a concern.” Intel’s Peter Zijlstra chimed in to add: "Yeah, so far nobody cared to fix 32-bit. If someone *realllllly* cares and wants to put the effort in I suppose I'll review the patches, but seriously, you shouldn't be running 32-bit kernels on Skylake / Zen based systems, that's just silly."

Microsoft finds new zero-days
Microsoft has recently found an Austrian company, posing as a risk analysis and business intelligence service provider, to actually be selling spyware. The company called DSIRF, which Microsoft tracked as KNOTWEED, has allegedly developed Subzero, a potent malware capable of remote code execution, as well as other nasties.
From our news piece: "The company, known as DSIRF, was found allegedly abusing zero-days exploits in both Windows and Adobe Reader to provide its customers with remote code execution capabilities, among other things. Before identifying the threat actor, Microsoft was tracking it under the codename KNOTWEED."

Data breach costs rising
The cost, and the impact, of a data breach, is hitting new records, IBM claims. The computing giant recently surveyed 550 organizations around the world on the impact of cybersecurity incidents, and found that the global average cost of a data breach is now $4.35 million, and at an all-time high.
From our news piece: "However, it’s not just the affected businesses that feel the sting of a data breach - everyone else does, too, albeit passively. IBM says that there is a chance that the rising costs of goods and services could be tied back to these incidents, as well. The company bases these conclusions on the fact that almost two-thirds (60%) of the respondents claimed to have raised the prices of their products or services, due to a data breach."

Hackers start scanning for security flaws 15 minutes after disclosure
After a vulnerability gets disclosed to the general public, it takes cybercriminals an average of 15 minutes to start scanning internet-connected devices for the flaw. This is according to a new report from Unit 42, Palo Alto Networks' cybersecurity arm.
The report highlights the importance of patching, both systems, and software, as soon as possible, as cybercrooks move fast when a flaw is discovered.
From our news piece: "Scanning in itself isn’t a threat, and knowing a vulnerability exists is one thing, while actually exploiting it is another. However, crooks still conduct these reconnaissance tasks as they can, if all else fails, sell the intel on the black market, the researchers said. Some of them move fast, too - Unit 42 says that “within hours”, the first active exploitation attempts can usually be seen."

PayPal abused to distribute phishing email
Payment service provider PayPal was observed being abused to distribute phishing messages, cybersecurity researchers are saying. Experts from Avanan have uncovered threat actors creating fake PayPal accounts, in the name of a major brand, and send malicious invoices and payment requests to unsuspecting victims.
From our news piece: "Given the (legitimate) nature of PayPal, email service providers can do nothing else but let the email through. The invoice will look legit. It will have the brand logo, proper wording, but also - a phone number for the victim to call. Unless they ignore the invoice altogether, there are two things the victims can do: either pay the invoice or call the listed phone number. Avanan calls this attack a “double spear”, as in some cases, not only will the hackers have the victim’s email, but also their phone number, which can later be used for new attacks."

Hackers getting creative following the death of the macro
Microsoft has officially killed macros in downloaded Office files, forcing hackers to look for alternative solutions. According to cybersecurity experts Proofpoint, they've managed to come up with three working solutions.
Instead of trying to get people to open Office files with embedded macros, they'll distribute container files (.ZIP, .RAR files, or similar), shortcuts (.LNK files), or HTML files.
From our news piece:" From October 2021 until today, the number of macro-powered Office files used to distribute malware drooped by a whopping two-thirds (66%). On the other hand, the use of container files (ISO files, ZIP, RAR files, and similar) rose by approximately 175%. Container files are a great way to avoid antivirus solutions, and if they also come with a password, their perceived legitimacy grows that much bigger. As for shortcut files (.LNK), their use exploded in February 2022, rising by 1,675% since October the year before."

Ransomware payments on the decline as businesses refuse to pay
Ransomware operators are having a hard time making victims pay for the decryption key, researchers are saying. Coveware's latest report says that the median ransom payment was $36,360 for Q2 of the year, down 51% compared to Q1.
Average ransom payment, on the other hand, rose 8%, suggesting that individual payments are increasing.
From our news piece: "This change doesn't appear to be a one-off, but a trend that started in the fourth quarter of 2021, when payments were at their highest (average was $332,168, and median was $117,116).
“This trend reflects the shift of RaaS affiliates and developers towards the mid-market where the risk to reward profile of attack is more consistent and less risky than high profile attacks,” the report reads."

Apple and Google to explain how they review crypto apps
A US senator asked Apple and Google to explain the review process for crypto mobile apps, at the time when fraud in the space grows bigger.
Senator Sherrod Brown (D-OH) says while many of the apps are legitimate and offer users an easy and convenient way to trade the nascent asset, there are some with malicious intent, which make it through the companies' gateways.
From our news piece: "Brown also wants to know if the companies monitor the apps they list in the stores, and how they stop them from “transforming” into phishing scams, as well as if the two companies notified their users about fraudulent crypto apps in the past."

Microsoft servers hijacked for bandwidth
Hackers have been installing malware on Microsoft SQL servers, in a bid to steal, and re-sell, their bandwidth, researchers are saying. This type of malware, called proxyware, turns the compromised endpoint into a proxy, which users can leverage, for a fee. Allegedly, some people earn as much as $6,000 a month for selling excess bandwidth.
From our news piece: "Besides for a few hiccups, and a general slowdown in internet speeds, the servers’ owners shouldn’t experience much of a difference, the researchers said. Another reason why Microsoft SQL servers are an interesting target for cybercriminals is due to the fact that the endpoints’ IP addresses are not blacklisted."

US court system hit with "incredibly significant" cyberattack
Two years ago, the US federal court system fell victim to a cyberattack. In late July, it was discovered that the attack was a lot more destructive than initially thought.
During a hearing at the House Judiciary Committee, Chairman Jerrold Nadler (D-NY) said that the data breach that was first publicly disclosed by the Administrative Office of the Courts, in early January 2021 was "incredibly significant and sophisticated".
From our news piece: "It was only in March of this year the committee first learned of the startling breadth and scope of the court's Document Management System security failure,” Nadler said. “And perhaps even more concerning is the disturbing impact the security breach had on pending civil and criminal litigation, as well as ongoing national security or intelligence matters."

Nomad blockchain bridge fails, $200m stolen
A broken update for the Nomad blockchain bridge resulted in the theft of pretty much everything the company had on the project. The project's authors confirmed that a recent update allowed users to spoof any transaction they wanted. As a result, the project has been drained of tokens of approximately $200 million in value.
From our news piece: "This wasn’t the work of a single hacker, or a group of actors, looking for a hole in the code to exploit. This was the project’s developers messing up, and the entire community seizing the day and grabbing what they can."

Hackers find new way to steal Discord accounts
With the help of malicious npm packages, and a few solid ransomware variants, unknown threat actors have been stealing Discord accounts from countless users. Cybersecurity researchers from Kaspersky recently discovered a campaign they dubbed LofyLife, which involves four malicious packages spreading two malware variants: Volt Stealer, and Lofy Stealer.
From our news piece: "These packages have been distributed through the repository, where they’re being adopted by various developers. Once integrated, the malware will seek to harvest different information from the victims, including Discord tokens, credit card information, and other types of sensitive, and potentially identifiable data."

Elaborate crypto fraud scheme uncovered
Cybersecurity researchers from Group-IB have uncovered an elaborate scam scheme, seeking to steal at least €250 from unsuspecting cryptocurrency investors. The researchers have found a fake crypto investment platform, and a whole network of promotional domains, trying to lure in as many victims as possible.
From our news piece: "The premise is simple: the fraudsters created a fake investment platform where people can “invest” in different cryptocurrencies. The platform *guarantees* earnings and high gains for everyone who signs up and uses the service. When the victim makes the deposit, it shows up in their dashboard, where they can track their earnings. The platform, obviously, shows bogus numbers, which sometimes even motivate the victims into depositing even more of their investment budgets, expecting even more earnings."

Twitter accounts at risk following API keys leak
More than 3,000 apps are leaking Twitter API keys, researchers are saying. These keys, which allow apps to use Twitter on behalf of the user (for posting, and similar), can also allow threat actors to read and send tweets, as well as direct messages.
From our news piece: "In theory, CloudSEK explains, a threat actor could amass an “army” of Twitter endpoints that would promote a scam or a malware campaign by tweeting, retweeting, reaching out via DMs, etc."

Xeon Sapphire Rapids delayed yet again
Intel has delayed the release of its 4th Generation Xeon Scalable server chips again, citing security issues that need ironing out. However, it turns out there are quite a few of these security issues. Around 500, to be more precise.
It now seems that the processors won't see the light of day before spring 2023.
From our news piece: "The rollout of Sapphire Rapids has been punctuated by repeated delays. Originally slated to launch in 2021, the new Xeon chips were first pushed back to early 2022, then to the middle and end of the year. The company delivered on its promise to put the new chips in the hands of select customers in Q1, but it now appears that most will have to wait until the end of Q1 2023 to gain access to the silicon."

Facebook ads abused to spread malware
McAfee's researchers have found an aggressive ad campaign on Facebook, promoting more than a dozen adware apps. The campaign promoted smartphone optimization apps that promise to rid the devices of ads, spyware, and other malicious programs. Instead, the apps were pushing ads to the device, changing their names and icons in the meantime, to avoid detection.
From our news piece: "The apps managed to serve the ads by abusing the Contact Provider Android component, meaning every time the user installs a new app, the adware uses this subsystem, and begins the ad-serving process. As a result, the user thinks the ads were being served by the newly installed app. The adware apps also create a permanent service for displaying the advertisements, and if user terminates the service, it just restarts. "

VMware patches critical flaw
VMware has patched a major vulnerability that affected a number of its products. CVE-2022-31656, an escalation of privilege flaw, was discovered in VMware's Workspace ONE Access, Identity Manager, and vRealize Automation.
It was patched together with nine other vulnerabilities. This one carries a severity score of 9.8.
From our news piece: "At the moment, there’s no evidence of the flaw being exploited in the wild, VMware said. Still, it urged its users not to wait for someone to get hurt before applying the patch: "It is extremely important that you quickly take steps to patch or mitigate these issues in on-premises deployments," VMware says. "If your organization uses ITIL methodologies for change management, this would be considered an 'emergency' change."

Windows 11 tightens up on security
Microsoft is currently working on releasing the next iteration of Microsoft Defender for Endpoint which should be better at defending Windows 11 users from ransomware and other advanced attacks.
The company recently pushed the next version of Windows 11 to the Beta Channel which, as many users noticed, comes with improvements to the endpoint protection tool
From our news piece: "Other fixes and improvements include the ability to compress a file regardless of its size, if Server Message Block (SMB) Compression is configured, as well as improved storage replication that occurs over low bandwidth or congested WANs. Microsoft fixed a handful of issues, as well, including one that causes Windows to display tablet mode features for devices without touchscreens, and one that causes some application windows to have blank sections in the Task View Preview."

Crypto wallet hacked, $4 million stolen
At least $4 million worth of cryptocurrency was stolen in yet another compromise in the blockchain world. This time around, it seems that an unknown threat actor discovered a flaw in one popular cryptocurrency wallet and manage to drain more than 9,000 instances.
In most cases, the token of the Solana network was stolen, together with a little USDC (U.S. dollar-backed stablecoin).
From our news piece: "Initially, it was thought that just the Phantom Solana browser wallet was affected, but the problem seems to be a lot bigger, with MetaMask one of the most popular crypto wallets/browser add-ons, also affected. Experts seem to agree - the only way to stay safe right now is to move the funds into cold storage (an offline hardware wallet)."

Chrome fixes major flaws
Chrome 104, the next iteration of the globally popular internet browser, will fix a couple of high-severity flaws, Google confirmed. The version, now available for Windows, Mac, and Linux, addresses 27 flaws, 15 medium-severity ones, and 7 high-severity ones.
Even though they're not yet being exploited in the wild, Google is withholding details, not to give fraudsters any new ideas.
From our news piece: "The high severity flaws affect the Omnibox, Safe Browsing, Dawn WebGPU, as well as Nearby Share, and among the medium severity flaws is a side-channel information leakage issue affecting the keyboard input. The Omnibox issue, a memory-related “use after free” flaw, is tracked as XCVE-2022-2603, with Google reportedly paying a $15,000 bounty to the finders. The Safe Browsing flaw is tracked as CVE-2022-2604, while the Nearby Share is tracked as CVE-2022-2609."

GitHub users attacked with cloned, malicious projects
Unknown threat actors have been cloning legitimate GitHub projects, tweaking them to carry malicious code, and releasing them for unsuspecting developers to use. This is according to cybersecurity researchers who spotted more than 35,000 potentially malicious repositories.
From our news piece: "The repositories were designed to siphon user environment variables, steal API keys, tokens, crypto keys, but also execute arbitrary code on affected endpoints. This kind of information can be used in identity theft attacks or ransomware campaigns. GitHub has since removed the malicious repositories and issued a short statement via Twitter, saying: “GitHub is investigating the Tweet published Wed, Aug. 3, 2022. No repositories were compromised."

Another crypto wallet hijacked to attack users
Atomic Wallet, one of the more popular cryptocurrency wallets and exchanges, is being impersonated by crooks looking to steal people's money. Cybersecurity researchers recently spotted a fake Atomic Wallet site where users, if they were to download the Windows version of the wallet, would actually be downloading the Mars Stealer dropper.
From our news piece: "Mars Stealer is a classic infostealer malware. Once it lands on an endpoint, it will look for credentials saved in the browsers, as well as cryptocurrency extensions, wallets, and two-factor authentication plugins. At press time, the site is still online, the publication claims. To stay safe, always double-check you’re downloading from the official source, which you can do by navigating directly to the website, rather than clicking on links in emails, advertising campaigns, or direct messages."

Fake holidays offer flood the internet
Cybersecurity researchers from Kaspersky recently spotted a surge in fake holiday offers, attempting to steal people's money. These offers range from fake travel tickets, to rental services, accommodation, ticket lotteries, and anything else related to the travel and leisure industries.
From our news piece: The cybersecurity firm said it found “numerous fake websites” that claim to offer users the chance to buy airplane tickets cheaper. Usually, these sites are “well-made” phishing pages, impersonating famous airline services and air ticket aggregators. To make the sites even more believable, the fraudsters sometimes display the details of real flights, pulled from legitimate data sources.

Classic hijacking technique spotted in the wild
Cybersecurity researchers from Inky recently uncovered that threat actors have been using open redirects to steal Microsoft 365 credentials from unsuspecting users.
Cybersecurity researchers from Inky recently discovered more than 6,800 phishing emails posing as Snapchat, and more than 2,000 posing as American Express.
From our news piece: "Open redirects allow threat actors to use other people’s domains and websites as temporary landing pages, before sending the victims to the phishing page. That way, when the attacker sends a phishing email, the link in the email’s body might look legitimate, further encouraging people to click.
"Since the first domain name in the manipulated link is in fact the original site's, the link may appear safe to the casual observer," Inky says. "The trusted domain (e.g., American Express, Snapchat) acts as a temporary landing page before the surfer is redirected to a malicious site."

Twitter exposes user data after coding blunder
An error in Twitter's coding gave everyone the ability to associate email addresses, or phone numbers, with people's accounts, the company recently confirmed. When someone tries to log into the platform with an email or phone number, even if the password is incorrect, Twitter will display the user handle of the associated account.
The flaw, first introduced a year ago, was quickly patched, but not before someone used it.
From our news piece: "The flaw was first spotted in mid-2021. At the time, Twitter said it couldn’t find any evidence of abuse. “This bug resulted from an update to our code in June 2021,” the company wrote. A year later, Twitter learned through a press report that someone had actually compiled a list of user accounts with this method and tried to sell it. Twitter apologized for the inconvenience, said it fixed the issue as soon it was unveiled, and said it will directly notify account owners that were impacted by this problem. "

Hackers using the Coinbase name to distribute malware
Cybersecurity researchers from Malwarebytes recently spotted the infamous Lazarus Group conducting what's known as a "fake job" attack. In this attack, they impersonate Coinbase, one of the world's largest cryptocurrency exchanges, and offer people fake jobs.
Those that take the bait are sent a file that looks like a PDF, but is, in fact, an EXE.
From our news piece: "The criminals then reach out to blockchain developers with a job offer for the role of “Engineering Manager, Product Security", and even conduct a few interviews, to make the whole campaign more believable. At one point, however, the attackers will share a file, seemingly a PDF, with details on the alleged job position. The only thing this file has with a PDF is the icon, however, as it’s, in fact, an executable - Coinbase_online_careers_2022_07.exe. Besides the .exe, the threat actor will also deploy a malicious DLL.

Twilio employees and customers attacked by fraudsters
Twilio has recently had data on its employees and customers stolen, and those people later targeted with phishing attacks, the company confirmed. An unknown threat actor, which the company described as "sophisticated", managed to trick certain employees into giving away their login credentials. These were later used to obtain a larger database of employees and users.
From our news piece: "Once enough data was collected, the attackers then used it against Twilio users and employees. The company said that recently, both current and former employees started getting text messages, seemingly from the company’s IT department. The threat actors are able to match employee names from sources with their phone numbers, which Twilio describes as a “sophisticated” move. "

US Emergency Alert System flawed, can be abused to create panic
The US Emergency Alert System (EAS), used to deliver urgent messages to the American people, is flawed and can be abused to send false warnings, it was said.
According to the Department of Homeland Security (DHS), the flaw is confirmed, and a proof-of-concept is in the works. EAS is usually used to deliver alerts via TV, radio, and other forms of media.
From our news piece: "While the DHS did not go into details about the flaw, The Register found reports of holes being found in the Monroe Electronics R189 One-Net DASDEC EAS device. The system is run by the Federal Emergency Management Agency (FEMA), Federal Communications Commission (FCC), and National Oceanic and Atmospheric Administration."

Amazon gift registries leak sensitive data
Amazon gift registries were mostly unprotected, despite holding a treasure trove of sensitive, personally identifiable data. The media are reporting that registries such as those for weddings, birthdays, newborns, and similar, have had the default visibility settings preset to public, offering the data to anyone who knew where to look.
From our news piece: "For a wedding registry, for example, the company takes the first and last names of both partners, the wedding date, the number of guests attending, and a mailing address. Not only is this data then set to public, but it’s also automatically sent to The Knot service. For baby registries, on the other hand, Amazon takes first and last names, expected due dates, whether the baby is the parents’ first child, and a mailing address."

Pharmacy accounts under attack for Oxy prescriptions
Pharmacy websites and accounts are under attack by cybercriminals looking for Adderall and Oxycodone prescriptions, researchers are saying. According to Kasada, crooks are conducting credential stuffing attacks in an attempt to take over such accounts, and later sell them on the black market.
From our news piece: "Kasada spotted that since April 2022, the number of pharmacy accounts sold on the black market started to rise. Over the past 60 days, the number of stolen accounts increased fivefold, they said, reaching “tens of thousands”. What’s more, these are not accounts on third-grade pharmacies, with some of them among the biggest in the US."

Some Windows 11 users at risk of data loss
Microsoft is warning that some devices with the latest chips, running Windows 11 and Windows Server 2022, are at risk of data loss. "Windows devices that support the newest Vector Advanced Encryption Standard (AES) (VAES) instruction set might be susceptible to data(opens in new tab) damage," the company warned. While the company did not detail how the flaw manifests itself, it did say a patch is available.
From our news piece: "The fixes do come with quite a large caveat, with some reports claiming they will slow the endpoints severely, with AES-based operations possibly twice as slow as before applying the patch. Apparently, BitLocker, Transport Layer Security (TLS) (specifically load balancers), and disk throughput (for enterprise customers, mostly) are most affected."

Microsoft patches two-year-old flaw
More than two years after its first disclosure, DogWalk finally gets patched on Windows. The Redmond software giant released its August Patch Tuesday cumulative update, and in it, the fix for the path traversal weakness found in the Windows Support Diagnostic Tool.
From our news piece: "The flaw is tracked as CVE-2022-34713, and if abused, can give attackers the ability to run any code on a target endpoint. It was first discovered by a researcher called Imre Rad more than two years ago, but back then, Microsoft said it wasn’t really a security vulnerability, and as such, it won’t be fixed. Fast forward to today, and the flaw has been put back into the spotlight by a different researcher, going by the name j00sean."

The death of macros put more sinister attacks in the spotlight
Microsoft's struggle to protect its users from dangerous macros attacks has made cybercriminals turn towards novel methods, and one is gaining popularity fast - shortcut files. According to a new report from HP Wolf Security, shortcut-based attacks have gone up 11% in the last quarter.
From our news piece: "There are two key elements to shortcut files that make them an ideal weapon for malware distribution: they can be made to run pretty much any file, and they can have any icon that comes preinstalled with Windows. That being said, threat actors can give it an icon of a .pdf file, and have it run a .exe, .log, or a .dll file, which could load pretty much any virus. In some cases, the hackers would even abuse legitimate Windows applications, such as the good old Calculator, for their nefarious purposes."

Exchange servers need extra protection, Microsoft warns
Despite numerous Exchange Server flaws being fixed in the August Patch Tuesday, Microsoft has still warned IT teams to enable Extended Protection if they really want to stay secure. Extended Protection enhances existing Windows Server authentication, and mitigates man-in-the-middle attacks
From our news piece: "Customers vulnerable to this issue would need to enable Extended Protection in order to prevent this attack," Microsoft said. "Please note that enabling Extended Protection (EP) is only supported on specific versions of Exchange (please see documentation for a full list of prerequisites)."

Messenger getting more secure
Facebook Messenger's owner, Meta, announced plans to add end-to-end encryption to all conversations, by default. So far, the feature was available, but only as an opt-in. According to the company, "some people" have already begun testing the new feature.
Once integrated, the feature would move Messenger closer to Facebook-owned WhatsApp, which has been offering end-to-end encrypted messaging for quite some time now.
From our news piece: "Along with the Facebook-based Messenger, Meta is also testing end-to-end encryption in direct messages sent through Instagram. End-to-end encryption has become a favoured default by many thanks to its security enhancements: while hackers can still gain unwanted access to a certain degree, sensitive data like locations are much harder to crack."

SMBs losing money on Apple's privacy changes
Privacy changes that Apple recently made are affecting many small and medium-sized businesses, and not in a good way. Since iOS 14.5, the company's App Tracking Transparency (ATT) allows users to opt-out of app tracking across third-party apps and websites, which means many users would stop getting personalized ads.
From our news piece: "This caused a 13% dip in revenue in Q2, 2022 for companies that relied on these targeted mobile ads to acquire new customers, according to data from software firm Varos which surveyed over 1,300 businesses."

Emotet reigns supreme, but is being challenged
Emotet, a global powerhouse among malware, has had its global impact cut in half during the summer, researchers are saying. According to cybersecurity experts from Check Point Research, its global impact is now 7%, down by 50% compared to June this year.
Despite this drawback, runners-up aren't exactly breathing down its neck, as second-placed Formbook has a global impact of 3%.
From our news piece: "Emotet continues to dominate our monthly top malware charts,” said Maya Horowitz, VP Research at Check Point Software. “This botnet continually evolves to maintain its persistence and evasion. Its latest developments include a credit card stealer module, meaning that enterprises and individuals must take extra care when making any online purchases. In addition, with Microsoft now confirming that it will block macros by default, we await to see how malwares, such as Snake Keylogger, may change their tactics.”

Xiaomi patches major payments flaw
Chinese smartphone giant Xiaomi recently patched a major flaw in its devices, which allowed hackers to steal people's cash. According to Check Point Research, a flaw was found in the mobile payment mechanism, allowing threat actors to sign fake payments.
From our news piece: "Xiaomi’s Trusted Environment, a tool that stores and manages sensitive information, such as passwords, or security keys, was vulnerable. There were two ways to go about stealing people’s cash: by having them install malware, or by stealing and tinkering with the device itself. "

Thousands of VNCs left unguarded
Cybersecurity researchers from Cyble recently found roughly 9,000 Virtual Network Computing (VNC) endpoints connected to the internet, and without a password or any other means of user authentication. That means, whoever knew where to look, could have accessed the devices and tinkered with them.
Given that some of these VNCs were industrial control systems, the problems could have ended up being much, much worse.
From our news piece: "Of the 9,000 vulnerable, the majority were located in China and Sweden, with a notable number of instances also discovered in the United States, Spain, and Brazil. Cyble’s researchers managed to find an exposed VNC that gave them access to an HMI for controlling pumps on a remote SCADA system. "

Python libraries compromised with malware
Cybersecurity researchers from Spectralops recently discovered ten malicious packages on the PyPI platform, preying on careless Python developers. The packages were carrying names almost identical to those of legitimate ones, in hopes that unsuspecting devs wouldn't spot the difference between the real and the fake.
From our news piece: "This type of attack is called typosquatting, and is a common occurrence among cybercriminals. It’s not used just on code repositories (although we’ve seen numerous instances on GitHub, for example, in the past), but also in phishing emails, fake websites, and in identity theft."

Who causes most data breaches?
Most data breaches are the result of hack attacks, researchers are saying. According to Flashpoint, 60% of all data breaches that happened in H1 2022 were due to hacking, while the number of misconfiguration incidents split in half.
From our news piece: "The report also discusses the danger of insider attacks. Apparently, just 23% of all incidents with confirmed origins came from insiders, and of that number, two-thirds (61%) were the result of mistakes with handling data.
In total, 54 breaches have been confirmed as coming from an insider, with some being relatively painless for the company (credit card theft at the point of sale), and some being outright monstrous (the stealing of proprietary source code and similar)."

Popularity of Zero Trust soars
Zero Trust is getting immensely popular, researchers are saying. After polling 700 decision-makers in organizations worldwide, Okta found that 97% now have a Zero Trust initiative, or are planning for one within the next year and a half. That's up by more than five times compared to just four years ago.
From our news piece: "While the popularity of the Zero Trust security framework seems to be going off the charts, not every region in the world shares the same enthusiasm. While 59% of North American businesses have a strategy set up, as well as 50% of those in the APAC region, just 36% of businesses in the EMEA region can say the same. European businesses will catch up to their North American counterparts soon enough though, as the investment in the region grows bigger (90% are increasing their budgets, compared to 83% in APAC and 77% in North America)."

ShitExpress hacked, data leaked
When a hacker decided to prank his arch-nemesis and send him a box of animal faeces, he went to the only place in the world offering such a service - ShitExpress.
But when he got there, he saw the site was vulnerable to SQL Injection and simply couldn't help himself. Soon afterward, he leaked website customers data to a hacking forum.
From our news piece: "ShitExpress is an online service that allows people to send actual faeces, through the post, to whomever they desire. It’s designed to be a prank site, where people can purchase a piece of animal faeces and have it delivered to someone’s door, in a box, together with a personalized message. You can imagine the type of messages someone would send together with a piece of animal dung to their cheating former partners, horrible ex boss, or noisy neighbor - hence why this leak might be troubling to many customers."

VPNs on iOS are putting users at risk
Virtual Private Network (VPN) service providers are putting their users at risk by not securing the data properly, inside the VPN tunnel, a researcher is saying. According to a blog posted by Michael Horowitz, Apple has known about the issue for more than two years, but decided to turn a blind eye.
From our news piece: "He ran a total of four tests from his iPad, every time changing iOS version (15.4.1, 15.5 and 15.6), VPN provider (he tried with ProtonVPN, OVPN and Windscribe), VPN protocol (IKEv2, WireGuard and OpenVPN) and server network. Even though at first the VPNs all seem working, a deeper inspection revealed the same disappointing result."

Chrome squashes multiple bugs
Google has released a new patch for its Chrome browser, which fixes almost a dozen vulnerabilities. Among them is CVE-2022-2856, a high-severity flaw allegedly being actively exploited in the wild.
As is common, Google doesn’t want to say much about the flaw, until the majority of Chrome instances have been patched. What it did say, though, is that this is an improper input validation bug, further described as "insufficient validation of untrusted input in Intents."
From our news piece: "Google paid out at least $29,000 to bounty hunters who found and disclosed these vulnerabilities. The highest payout, of $7,000, went to researchers who found CVE-2022-2854 and CVE-2022-2855. Last year, the company paid out almost $9 million for numerous bug disclosures."

Oracle audits TikTok for snooping
Oracle has started analyzing TikTok's algorithms, to see whether or not the Chinese government is abusing the social media giant's enormous popularity. According to Axios, both its algorithms and content moderation models are under inspection.
From our news piece: "A TikTok spokesperson told Axios that the new partnership would allow Oracle to carry out, "regular vetting and validation" of the company's content recommendation and moderation models. Past reports had claimed that TikTok blocks or marks down certain videos critical of the Chinese government, as well as censoring videos that mention subjects such as Tibetan independence or the Tiananmen Square massacre."

Tens of shapeshifting Android apps discovered
Cybersecurity researchers from Bitdefender discovered 35 shapeshifting apps which serve malicious content to their victims, and then change their appearance to avoid deletion. The apps, the researchers are saying, have all made it into Google Play Store, and have been downloaded more than two million times.
From our news piece: "Simply serving ads to the endpoints isn’t malicious in itself, the researchers explained, but the problem lies in the fact that these apps do it through their own framework, meaning nothing’s stopping them from serving more dangerous malware, too, or even ransomware. What’s more, if the ads are served aggressively (which they are), they hurt the user experience, as well. Another aspect that makes these apps malicious is that they hide from the victims in order to avoid being deleted."

Lame Office security threat making rounds
There's a crude and quite backward cybersecurity threat that seems to be performing quite well. Cybersecurity researchers from Atheniem have spotted USB drives, being sent through the post, seemingly carrying Microsoft Office Professional Plus, a business-oriented variant of the popular productivity suite. However, instead of actually holding the suite, it holds malware.
From our news piece: "After plugging in the USB drive, a warning appeared saying that a virus had been detected, and to call a toll-free number to get this removed. However doing so passed the victim through to the scammers, who pretended to remove the "virus" before looking to complete the subscription process by taking the victim's payment details."

Janet Jackson is breaking old PCs
Cybersecurity researchers have discovered a rather odd flaw - the music video of Janet Jackson's 1989 song Rhythm Nation is crashing some PCs. As it turns out, this has nothing to do with the devices' music tastes, but rather with the fact that the song resonates a specific frequency.
From our news piece: “It turns out that the song contained one of the natural resonant frequencies for the model of 5400 rpm laptop hard drives that they and other manufacturers used," the researcher noted. "The manufacturer worked around the problem by adding a custom filter in the audio pipeline that detected and removed the offending frequencies during audio playback.”

Apple fixes major flaw in more OS variants
Apple has now fixed CVE-2022-32893 in both macOS Big Sur, and Catalina. The out-of-bounds write flaw in WebKit has previously been patched on macOS Monterey, as well as the latest versions of iOS and iPadOS. Safari 15.6.1 for macOS Big Sur and Catalina is available to download now, with anyone using those versions advised to upgrade immediately.
From our news piece: "An out-of-bounds write flaw happens when a threat actor forces an input program to write data before the beginning, or after the end, of the memory buffer. That crashes the program, corrupts the data, and allows threat actors to remotely execute code. The fix for Big Sur and Catalina is in the same vein as the one for Monterey - through improved bounds checking."

More malicious packages spotted on PyPi
A dozen of malicious packages were recently spotted on PyPi, the largest code repository for Python developers. According to cybersecurity researchers from Snyk, the attackers are looking for Discord login data, as well as data stored in passwords. PyPi is the biggest Python code repository out there, with more than 600,000 active users.
From our news piece: "The packages were uploaded almost a month ago, by a threat actor called “scarycoder”. They claim to provide the users with various functionalities, Roblox tools, thread management, and others. Instead, the researchers have found, all the packages do is steal sensitive information."

Major DDoS attack stopped, says Google
Google says it blocked one of the largest Distributed Denial of Service (DDoS) attacks ever seen, before it could do any meaningful damage. According to two senior leaders, Emil Kiner, and Satya Konduru, the company managed to prevent a Layer 7 HTTPS DDoS attack that peaked at 46 million requests per second (rps). That makes it 76% larger than the second-biggest attack, ever.
From our news piece: "The attack reached its peak some ten minutes in but lasted more than an hour (69 minutes). The researchers speculate that the attackers stopped when they saw that their efforts weren’t producing the desired outcome. From the technical side of things, it seems the botnet used in the attack was relatively powerful. All in all, 5,256 source IPs were used, originating from 132 countries."

Cryptojacking going strong despite bear market
Even though cryptocurrencies are in a deep bear market, cybercriminals are still looking to acquire more, by any means necessary. Microsoft's recent report says cryptojacking, a form of cyberattack in which a device is "hijacked" to mine cryptocurrencies for the attackers, is still as popular as ever.
From our news piece: In a blog post, Microsoft explained it detects cryptojackers on “hundreds of thousands” endpoints every month via its in-built Windows antivirus service. Among the most popular cryptojackers is XMRig, a piece of malware mining the Monero token (XMR). Monero is a relatively old cryptocurrency, one that promises full anonymity to its users and, as such, is immensely popular among crooks and people dealing in illegal trade."

New tactics for Microsoft 365 account theft exposed
Cozy Bear, a known Russian state-sponsored cybercrime group, has come up with new strategies as they try to compromise Microsoft 365 accounts belonging to high-level individuals in the West. As per a new Mandiant report, the likelihood of regular users being targeted is relatively small, but large businesses will need to be on the lookout.
From our news piece: "Cozy Bear is using three techniques to execute (and disguise) the attacks: Disabling Purview Audit before engaging with a compromised email account; Brute-forcing Microsoft 365 passwords that are yet to enroll in multi-factor authentication (MFA); and covering their tracks by using Azure Virtual Machines via compromised accounts, or by purchasing the service"

Illegal sports stream sites a hotbed for malware
Websites offering sports streaming services illegally are infecting their visitors with all kinds of dangerous malware, researchers are warning. A new report from Opentext Security Solutions even states that some of these malware variants are even capable of stealing people's money.
From our news piece: "Opentext recently analyzed 50 “popular” illegal streaming sites and discovered that “every single one” contained malicious content. Furthermore, four in ten did not have the necessary security certificates. To top it all off, users are also “bombarded” with explicit and extreme pop-up ads."

New hacking tool downloads email inboxes
A hacking group linked to the Iranian government has apparently built a new tool that is capable of downloading the entire email inbox, and seems to be using it against high-profile individuals in the country.
Cybersecurity researchers from Google's Threat Analysis Group (TAG) discovered a tool called HYPERSCAPE, built by the Iranian state-sponsored group Charming Kitten.
From our news piece: "According to Google, the tool works on the attacker’s endpoint, which means victims don’t have to be tricked into downloading any malware. They do, however, need to either have their account credentials compromised or session cookies stolen, as the attacker first needs to log into their account."

Thousands of Hikvision cameras vulnerable to cyberattacks
Cybersecurity researchers from CYFIRMA have discovered some 80,000 Hikvision cameras that don't have the latest updates and as such are vulnerable to major exploits. As per the report, the patch, available since last year, fixes CVE-2021-36260, a command injection vulnerability in the web server. However, many organizations are yet to apply the fix.
From our news piece: "Some 80,000 cameras, used by some 2,300 organizations all over the world, remain vulnerable. The security camera exploit isn't just a proof of concept, either. Reports suggest there have so far been two attacks in the wild, one of which was used to expand Moobot, a botnet that used the compromised cameras for distributed denial of service (DDoS) attacks."

Ransomware operators hit by DDoS
Ransomware operators LockBit suffered a distributed denial of service (DDoS) attack over the weekend, after trying to leak data stolen from Entrust in an earlier ransomware attack. After the negotiations, in which LockBit demanded $8 million, broke down, the group sought to leak the stolen data online, but was met with an unusual problem.
From our news piece: "At that time, the Tor data leak site was brought offline by a DDoS attack powered by more than 1,000 servers, with LockBit laying the blame on Entrust. While it's possible Entrust may be behind the attack, this would likely be the first time a legitimate company used illegal means to force a ransomware operator into compliance."

Malware hiding in pirated software
Cybersecurity researchers from Zscaler recently found two infostealer variants hiding among cracked software, keygens and activators. The malware was being distributed via legitimate-looking websites, who made it high on search engines thanks to SEO poisoning.
From our news piece: "An unknown threat actor (or multiple actors) is using SEO poisoning techniques to have their websites appear high up on Google results pages for popular software-related queries such as Adobe Acrobat Pro, 7-Data Recovery Suite, and several other programs. These websites most often appear on .com domains, but also on less popular domains such as .xyz, or .cfd."

SaaS platforms abused for phishing
Hackers are using Software-as-a-Service platforms to launch and manage their malicious campaigns, experts have found. Palo Alto Networks' Unit 42 says the abuse of file sharing sites, hosting tools, form and survey builders, and similar SaaS tools, rose by 1,100% in a year.
From our news piece: "Unit 42 says the rising popularity of these tools among crooks can be attributed, first and foremost, to the fact that they are legitimate, and as such, often pass through various fraud and scam filters, including email security solutions. But it can also be attributed to the fact that they’re super easy and convenient to use, and allow for the quick upscaling and downscaling of campaigns."

Binance exec's image abused in fraud
A sophisticated scam, leveraging artificial intelligence and deepfake technology, was just spotted. In it, a threat actor tried to scam cryptocurrency projects out of their money, by posing as Binance chief communications officer (CCO), Patrick Hillmann.
From our news piece: “It turns out that a sophisticated hacking team used previous news interviews and TV appearances over the years to create a “deep fake” of me,” Hillmann said in a Binance blog post . “Other than the 15 pounds that I gained during COVID being noticeably absent, this deep fake was refined enough to fool several highly intelligent crypto community members.”

Hackers targeting Microsoft 365 accounts
Hackers are targeting Microsoft 365 accounts with a new business email compromise (BEC) campaign, experts are saying. The goal of the campaign is to divert any payments to the bank accounts owned by the criminals. Experts from Mitiga, which first spotted the campaign, said crooks were able to bypass multi-factor authentication, as well.
From our news piece: "The idea is simple in theory: the attackers would first compromise a business email account through the use of phishing. Then, they’ll land into the inbox and lurk there, monitoring various email chains and threads, until they identify one where a wire transfer is being planned. Then, when the planning is done, and just before the victim sends the funds, the attacker will reply to the email chain asking for the funds to be sent elsewhere, saying the original bank account was frozen due to a financial audit."

DuckDuckGo introduces new privacy features for its email service
The beta version of DuckDuckGo's latest email privacy tool is now live, the company confirmed. The company's Email Protection is a forwarding tool that allows users to hide their email addresses when signing up for online services. What's more, it eliminates tracking artefacts usually sent together with such emails.
From our news piece: "The new service from DuckDuckGo can be seen as a hybrid between traditional email forwarding services, which route messages through to an inbox without exposing the address, and private email services like ProtonMail.
The ambition is to shield against user profiling by obscuring identity information and combat covert tracking techniques deployed by digital advertising firms, online retailers and other web players."

Block sued for December 2021 data breach
Digital payments giant Block and its subsidiary Cash App are being sued for the 2021 data breach in which more than 8 million people had their sensitive data stolen.
Two people are suing the company, saying the breach resulted in "unauthorized charges" in their Cash App accounts, and that they were forced to spend hours fixing the issue.
From our news piece: "These unauthorized charges came as a result of a data breach in December 2021, when a former employee logged back into Cash App’s systems and downloaded internal reports which held personal information. The data the culprit took includes customers' full names, brokerage account numbers, brokerage portfolio values, brokerage portfolio holdings, and in some cases, stock trading activity for one trading day."

Fake crypto sites stealing people's tokens
Researchers from Netskope are warning crypto users to stay vigilant, as fake versions of their favorite websites are popping up. Apparently, websites such as Coinbase, Gemini, Kraken, and others, have multiple fake versions that, in some instances, even rank better than the legitimate ones, on search engines.
From our news piece: "According to Netskope, criminal groups are using search engine optimization (SEO) techniques, that involve an extensive network of bots posting links to phishing pages on other websites (mainly blogs) to boost their rankings in search engines such as Google. In some instances, the researchers claim these fake websites are ranking better than the legitimate sites being copied."

Lazarus targets US energy firms with Log4j
Infamous North Korean state-sponsored threat actors Lazarus Group (AKA APT38) is using the log4j vulnerability to target energy providers in the US, and elsewhere around the world, researchers are saying. Cisco Talos Intelligence says Lazarus is looking to establish long-term access, and later exfiltrate data, for its bosses in North Korea.
From our news piece: "Although the precise targets have remained unnamed, the attacks once again show the threat that North Korea and Lazarus can pose via destabilization efforts. According to Talos, this campaign involved the exploitation of vulnerabilities in the VMWare Horizon virtual desktop product to gain an initial foothold in targeted organizations."

Cisco to stop supporting some SMB routers with new patches
Three vulnerabilities, found in some of Cisco's SMB routers, will not be getting their patches, the company recently confirmed. The RV110W Wireless-N VPN Firewall, the RV130 VPN Router, the RV130W Wireless-N Multifunction VPN Router, and the RV215W Wireless-N VPN Router, have reached their end of life earlier this year, and as such, will not be supported any longer. Cisco hasn't sold these models since 2017.
From our news piece: "Cisco recommends possibly impacted users should migrate to Cisco Small Business RV132W, RV160, or RV160W routers. For those currently low on funds, unfortunately, there are no workarounds that address this vulnerability according to Cisco. Users of the routers in question may have at least gotten a good amount of bang for their buck. The networking giant hasn't sold the RV110W and RV130 since 2017, and only officially ended support for them in 2022."

WeTransfer abused in a new malware campaign
Unknown threat actors are growing their distribution of the Lampion trojan, and they're abusing a popular, legitimate file transfer service to do it. Cybersecurity researchers from Cofense recently spotted a new campaign in which Lampion is being distributed via a WeTransfer link.
From our news piece: "What makes this campaign more dangerous than other, similar campaigns, is the use of WeTransfer. This is a legitimate file transfer service, making it extremely difficult for email security systems to flag it as malicious. What’s more, this is not the only legitimate service the crooks are abusing - they’re also leveraging Amazon Web Services (AWS)."

VoIP software abused in ransomware attacks
Ransomware operators Lorenz were spotted abusing a known vulnerability in VoIP software, to distribute their malware, steal, and encrypt, sensitive company data. This is according to a new report from Arctic Wolf Labs, which claims Lorenz is abusing CVE-2022-29499, a known remote code execution vulnerability, found in Mitel MiVoice VoIP appliances.
From our news piece: "The researchers did not name any specific firms being targeted, but explained, "Initial malicious activity originated from a Mitel appliance sitting on the network perimeter," they say. “Lorenz exploited CVE-2022-29499, a remote code execution vulnerability impacting the Mitel Service Appliance component of MiVoice Connect, to obtain a reverse shell and subsequently used Chisel as a tunneling tool to pivot into the environment."

New Linux malware found targeting endpoints of all types
A brand new malware, targeting Linux devices, was recently discovered. Dubbed Shikitega, by researchers from AT&T Alien Labs that first discovered it, the malware can do all sorts of things, from controlling the webcam on the target endpoint, to stealing credentials, to installing a cryptojacker.
From our news piece: "Shikitega comes with a super tiny dropper (376 bytes), using a polymorphic encoder that gradually drops the payload. That means that the malware will download and execute one module at a time, making sure it stays hidden and persistent. The command & control (C2) server for the malware is hosted on a “known hosting service”, making it stealthier, it was said."

U-Haul confirms breach, stolen data
American moving and storage rental company U-Haul confirmed suffering a data breach that resulted in the theft of some customer sensitive information. The company recently notified its customers of the breach, saying someone compromised two "unique passwords" that gave them access to the company's contract search tool.
From our news piece: "Through the use of the tool, the attackers managed to steal certain personally identifiable information: "After an in-depth analysis, our investigation determined on September 7, 2022, the accessed information includes your name and driver's license or state identification number," the announcement reads."

Apple's newest security tool can be removed
Apple's Rapid Security Response security tool can be removed from iOS 16, the company confirmed earlier this week. As it turns out, the feature can be turned off, the updates manually removed, and reinstalled at a later date, if needeed.
The patches pushed through Rapid Security Response are downloaded automatically, however, Apple will now also allow users to block Rapid Security Response from downloading and installing security patches, as well as deleting them.
From our news piece: "To do so, users should navigate to Settings > General > About, tap on the iOS version, and then tap on Remove Security Update. Anything admins delete can be reinstalled at any point in time, otherwise, the changes will be implemented when the endpoint updates to the latest version of iOS."

Steam accounts targeted
Cybersecurity researchers from Group-IB have uncovered a new phishing campaign that targets high-profile Steam accounts. Apparently, a group of threat actors is using an elusive phishing kit to try and lure pro gamers and other high-profile Steam account holders to join a fake tournament. To do that, they need to log into Steam first, and that's when the theft happens.
From our news piece: "The thefts can allegedly be rather lucrative, with some of the more high-profile accounts reportedly selling for as much as $100,000 to $300,000 apiece. The group gathers either on Discord or Telegram and uses a phishing kit capable of “browser-in-browser” attacks, something not as widely distributed among the cybercrime community as some other tools. "

Phishing made even worse with sock puppeting
Fraudsters have started engaging in "multi-persona impersonation" to get people to download malware, researchers are saying. Experts from Proofpoint have spotted TA453, an Iranian state-sponsored group, creating multiple fake email accounts and starting an email thread with the victim cc'ed. That way, they're hoping the victim will see the conversation as legitimate and download the malicious attachment.
From our news piece: "That way the victim, essentially caught in the middle of an email thread, could lower their guard and get a fake sense of legitimacy about the whole thing. After a short back-and-forth, one of the participants would send an attachment to other participants, and should the victim download and run it on their endpoints, they’d get a .DOCX file filled with dangerous macros."

McAfee consolidates efforts, introduces McAfee+
McAfee has merged all of its key security products into a single package, and is calling it - McAfee+. The new offering, it says, encompasses all new privacy, identity, and protections. The company believes such a solution would enable users to “confidently and securely live life online”.
From our news piece: "For starters, it includes features such as Personal Data Cleanup (revealing which high-risk data broker and people search sites collects and sells customer private data, requests their removal, and follows the process throughout the way), as well as "Unlimited Secure VPN" which automatically connects on public Wi-Fi networks, Ransomware Coverage which reimburses up to $25,000 for losses and ransom fees, Credit Lock, which reduces the chance of becoming a victim of identity theft, and much more. "

Microsoft releases new Patch Tuesday cumulative update
Microsoft has just released the cumulative security update for September, and it includes, among other things, fixes for two zero-day vulnerabilities being exploited in the wild.
The two flaws are tracked as CVE-2022-37969, and CVE-2022-23960. According to Microsoft, an attacker who successfully exploits this vulnerability "could gain SYSTEM privileges".
From our news piece: "Besides these two vulnerabilities, Microsoft has patched a total of 61 flaws, excluding the 16 flaws fixed in Microsoft Edge prior to the release of this cumulative update. These flaws include 18 elevation of privilege vulnerabilities, 1 security feature bypass vulnerability, 30 remote code execution vulnerabilities, seven information disclosure vulnerabilities, seven denial of service vulnerabilities, as well as 16 Edge - Chromium vulnerabilities (excluding the 16 mentioned earlier)."

Old malware revived
Old malware is being recycled as threat actors try to cut down on their expenses and avoid being detected by cybersecurity solutions. This is according to a new report from Symantec, which says threat actors Webworm revived at least three old malware variants.
From our news piece: "While it’s difficult to know exactly which threat actor is behind Webworm’s revival, Symantec seems to believe it’s the same group as Space Pirates - a Chinese threat actor discovered by Positive Technologies in May this year. Back then, Positive Technologies analyzed Gh0st RAT and named it Deed RAT."

Most companies suffered a cloud incident last year
Roughly 80% of companies have suffered at least one major cloud security incident in the last year, researchers are saying. Cybersecurity experts Snyk are saying that between poor cybersecurity tools and inexperienced staff, businesses are suffering data breaches, leaks, as well as perimeter breaches.
From our news piece: "Many of the problems businesses are seeing with cloud security today happen as a result of poor collaboration between different departments, as well as poor training that doesn’t help with the organization’s digital transformation. In fact, 77% of firms see this as a “major challenge."

Hackers after healthcare payments, FBI warns
Hackers are going after payments made by healthcare providers, the FBI says, claiming that so far this year, more than $4 million had been stolen in a couple of incidents. Breaching healthcare portals and websites, cybercriminals would change payment information in the accounts, diverting payments to bank accounts under their control.
From our news piece: "Of the three incidents, one happened when credentials from a “major healthcare company” were used to replace a hospital’s direct deposit banking information with that belonging to the attackers. In total, $3.1 million were lost. In another incident, the thieves made away with some $700,000, while in the third, an attacker impersonated an employee, changed the Automated Clearing House (ACH) instructions, and took $840,000."

YouTube videos used to spread malware
Cybersecurity researchers from Kaspersky have found a new malware campaign that uses YouTube videos to distribute the RedLine infostealer. According to researchers, the campaign targets gamers, as the videos fraudulently explain how to install cracks and cheats for some of the most popular games today.
But instead of the cracks, the gamers would receive multiple malware bundled together.
From our news piece: "In the bundle is RedLine Stealer, one of the most popular infostealers nowadays, capable of stealing(opens in new tab) passwords stored in people’s browsers, cookies, credit card details, instant messaging conversations, and cryptocurrency wallets. The bundle also holds a cryptojacker, essentially a cryptocurrency miner which uses the computing power of the compromised endpoint to mine certain cryptocurrency for the attackers. Cryptocurrency mining usually requires significant GPU power, something most gamers usually have."

Browser spellchecker leaks sensitive data
Researchers from JavaScript security firm otto-js recently discovered that Chrome's and Edge's advanced spellcheckers are leaking personally identifiable information to their respective parent companies.
As it turns out, both of these browsers have built-in spelling checkers that don't send data back to Google and Microsoft. However, more advanced features, coming with Chrome's "Enhanced Spellcheck" and Edge's "Microsoft Editor" were found to have been sharing things such as usernames, emails, passwords, and more.
From our news piece: "Working in conjunction with most text fields on a webpage, both tools have access to “basically anything”, says otto-js. This means that any data you input online, including your date of birth, payment details, contact information, and login credentials could all be being sent back to Google and Microsoft."
Tech support scammers in Edge's newsfeed
Malwarebytes claims to have found malicious advertisements in Microsoft Edge's news feed. Publishing the findings in a blog post, the company said the scheme's goal is to direct victims to tech support scam pages. Apparently, the campaign has been going on for at least two months.
From our news piece: "This particular scam operation has been particularly effective because of Microsoft Edge’s news feed doubling as the web browser’s homepage, increasing the chances that users may be lured by “shocking or bizarre stories” that have been placed there by attackers."

Zoom meetings could be compromised with - eyeglasses
Researchers have discovered that webcams have gotten so good that video conferencing participants could pick up what their peers are looking at, from the reflection in their eyeglasses. Researchers from the University of Michigan in the US and Zhejiang University in China said it is possible to reconstruct and recognize, with more than 75% accuracy, on-screen texts that have heights as small as 10mm, all while using nothing more than a 720p webcam.
From our news piece: "The experiment was done in a controlled lab setting, meaning results in real-life use might differ. In fact, the researchers are saying there are many factors that can contribute to the accuracy of the method, including the participant's skin color, how well-lit the room is, the brightness of the display the contrast between the text and the background on the display, as well as the eyeglasses."

Uber shares more details on recent hack, blames Lapsus$
Uber has disclosed more details about the recent data breach, and claims infamous extortion group Lapsus$ is behind the attack. The group is known for breaching major companies, successfully stealing sensitive data from the likes of Microsoft, Cisco, Samsung, Nvidia, and Okta before Uber.
From our news piece: "In a security update, Uber said a threat actor purchased an Uber EXT contractor’s login credentials from the dark web, and managed to log into the account after the contractor accepted a two-factor login request from the secondary endpoint. From there, the attacker accessed “several other employee accounts” (Uber does not go into details on how this happened), which gave them elevated permissions to a couple of tools, including Google Workspace and Slack."

Piracy sites overwhelm visitors with malvertising
Piracy sites, where people go to consume commercial content for free, are brimming with malicious ads, tricking people into downloading malware, viruses, and even ransomware. According to a new report published by the Digital Citizens Alliance, White Bullet, and Unit 221B, almost four in five piracy sites serve malicious ads to their visitors.
From our news piece: "Malvertising on piracy sites has grown into a major industry, too, the report claims, saying piracy operators generate an estimated $121 million in revenues this way. They also make up some 12% of all ads shown on piracy sites, while more than half of the $121 million ($68.3 million) came from U.S. visitors. In fact, piracy sites are doing so well with malvertising that almost 80% of these sites serve malware-ridden ads to their users."

Horse racing under ransomware attacks
The New York Racing Association (NYRA) has recently confirmed suffering a ransomware attack. In a statement published earlier, the company said it discovered “suspicious network activity” in late June 2022 that resembled a potential cyberattack.
From our news piece: "After a few weeks of investigations, NYRA found that the damage was limited, and that it was not connected to day-to-day racing operations. Customer wagering activity, NYRA Bets, as well as NYRA television, have all remained secure."

2K Games helpdesk hacked, abused to spread malware
Popular games published 2K Games has had its helpdesk platform hacked recently, and the attackers tried to use it to distribute a dangerous infostealer. The company recently took to Twitter to announce someone getting "illegal access" to the credentials of one of its vendors to the helpdesk platform.
"The unauthorized party sent a communication to certain players containing a malicious link. Please do not open any emails or click on any links that you receive from the 2K Games support account," the company warned.
From our news piece: "The attackers would first open up a fake support ticket, and soon after, reply to it. In the reply message, they’d share a file named “2K Launcher.zip”, inviting the players to run it on their endpoints. The file turned out to be RedLine Stealer, a known infostealer that’s capable of, among other things, grabbing passwords stored in the browser, stealing banking data, as well as cryptocurrency wallets. Furthermore, RedLine can grab VPN credentials, web browser history, and cookies."

Another crypto firm suffers hack
Crypto market maker Wintermute suffered a damaging cyberattack recently, but has reassured its users that it remained solvent and will remain operational in the future. The company's CEO, Evgeny Gaevoy, recently published a Twitter thread, confirming the attack, and stating that the attackers got away with $160 million in various tokens.
From our news piece: "The attack was in relation to our wallet used for DeFi proprietary trading operations, which are completely separate and independent from our CeFi and OTC operations. Our internal systems in both Cefi and Defi are not affected, as well as any internal or counterparty data,” he added."

LockBit ransomware leaks online
A developer angry with the leadership of the LockBit ransomware has decided to leak the encryptor to the internet, sources are saying. At first it seemed to be a hack, followed by a leak, but according to VX-Underground, it was the work of a disgruntled employee.
From our news piece: "A brand new Twitter account named Ali Qushji claimed their team hacked the servers of LockBit and found a builder for the LockBit 3.0 ransomware encryptor. Following the tweet, malware source code library VX-Underground chimed in, saying they were contacted by a user named “protonleaks” on September 10, with the same content. "

Windows 11 gets better at defending from brute-force
Microsoft has upgraded the Windows 11 SMB server service to make it more resilient against brute-force attacks, the company confirmed in a recent security advisory.
With the latest update for the operating system, the Insider Preview Build 25206, recently pushed to the Dev Channel, SMB authentication rate limiter is enabled by default. What’s more, a couple of other settings have been tweaked to make these attacks “less effective”.
From our news piece: "With the release of Windows 11 Insider Preview Build 25206 Dev Channel today, the SMB server service now defaults to a 2-second default between each failed inbound NTLM authentication," Ned Pyle, Principal Program Manager in the Microsoft Windows Server engineering group, said in a blog post announcing the news. "This means if an attacker previously sent 300 brute force attempts per second from a client for 5 minutes (90,000 passwords), the same number of attempts would now take 50 hours at a minimum."

Morgan Stanley pays millions in fines for not encrypting drives
As part of a settlement with the US Securities and Exchange Commission (SEC), Morgan Stanley has paid $35 million in fines. The SEC claimed the company failed to properly protect customer-sensitive data. Morgan Stanley did not deny, nor confirm these allegations.
From our news piece: "The SEC found Morgan Stanley failed to protect customer data by poorly handling the decommissioning of some of its storage units. This included apparently hiring a moving and storage company “with no experience or expertise in data destruction services” to decommission thousands of hard disk drives (HDD) and servers, which were carrying unencrypted personally identifiable information on millions of Morgan Stanley clients, as far back as 2015."

Optus breached, data taken
Major Australian telecoms operator, Optus, confirmed suffering a data breach and losing sensitive customer data. Issuing a press release recently, the company said an unknown threat actor stole customer names, dates of birth, phone numbers, as well as email addresses.
From our news piece: "Some customers have also had physical addresses, ID document numbers such as driver's licenses or passport numbers exposed, as well. Payment details and account passwords are safe, however."
Fake Zoom websites distributing malware
Cybersecurity researchers from Cyble have recently spotted a number of fake websites, pretending to offer the Zoom client when, in fact, distributing malware.
The popular video conferencing platform has had its identity stolen in at least six occasions, as threat actors seek to spread the Vidar Stealer.
From our news piece: "The visitors would be redirected to a GitHub URL that shows which applications they can download. If the victim chooses the malicious one, they receive two binaries in the temp folder: ZOOMIN-1.EXE and Decoder.exe. The malware also injects itself into MSBuild.exe and pulls IP addresses hosting the DLLs, as well as configuration data, it was said."

Android spyware updated, attacks millions of users
Banker, a known Android malware, has been spotted in the wild, carrying new bells and whistles. This is according to Microsoft, which says that the malware's operators are looking to steal banking details, and possibly even money.
The researchers are saying that the threat actors are engaging in smishing attacks (SMS phishing) to trick people into downloading Banker, capable of extracting all sorts of sensitive information, including two-factor authentication (2FA) codes, account login details, and other personally identifiable information (PII).
From our news piece: "Once the user downloads the malware, they need to grant certain permissions, such as MainActivity, AutoStartService, and RestartBroadCastReceiverAndroid. That allows it to intercept calls, access call logs, messages, contacts, and even network information. By being able to do these things, the malware can also receive and read two-factor authentication codes coming in via SMS, and delete them to make sure the victim doesn’t suspect anything fishy."

Windows 11 to warn users when they type out a password
Microsoft has introduced a new feature to help Windows 11 users keep their passwords secure. The upcoming 22H2 update will thus feature a new Enhanced Phishing Protection feature that will give users a heads up when they type out their passwords in applications, or websites, which are a potential security risk (Notepad included!).
From our news piece: "In a blog post announcing the launch, Microsoft says that the new tool should stop unsuspecting users from accidentally writing out their passwords in plain view, and keep them safe from hackers or scammers. It uses the company's SmartScreen protection platform to spot any saved passwords from being entered, displaying a warning that "It's unsafe to store your password in this app...we recommend removing your password from this file".

Multiple crypto npm packages compromised
Researchers have found a couple of npm packages from a reputable cryptocurrency exchange carrying malicious code. As it turns out, the packages, belonging to the decentralized exchange dydX were hijacked and updated to carry unwanted code.
From our news piece: “At 6:14AM EST, we identified malicious versions published to a number of dYdX NPM packages that were quickly removed,” its tweet reads. “All funds are SAFE, our websites/apps have NOT been compromised, the attack did NOT impact smart contracts.”
Slack and Teams hold major security flaws
Online collaboration giants Slack and Teams allow users to integrate hundreds of third-party apps, each of which is a potential security incident, researchers are warning.
As per experts from the University of Wisconsin-Madison, third-party apps are usually not thoroughly scrutinized by owners Microsoft and Slack, while those that do, only get a superficial analysis.
From our news piece: "With these platforms becoming the defacto operating systems of corporate productivity, this is a major security risk, researchers claim.
“Slack and Teams are becoming clearinghouses of all of an organization’s sensitive resources,” Earlence Fernandes, one of the study’s authors, and a professor of computer science at the University of California at San Diego, said. “And yet, the apps running on them, which provide a lot of collaboration functionality, can violate any expectation of security and privacy users would have in such a platform.”

Malware hiding in fake gaming cheats
Cybersecurity researchers from Cluster25 have recently discovered a new malware distribution campaign, in which the malicious files are being passed under gaming cheats. In their latest report, the researchers said they spotted "Erbium", a malware-as-a-service, capable of stealing all kinds of sensitive information from its victims.
From our news piece: "When it comes to features and prices, Erbium is similar to the infamous RedLine Stealer in its abilities, but is available for a fraction of its cost. The researchers are saying it can steal information stored in popular browsers (passwords, cookies, payment data, autofill information, etc.), data from cryptocurrency wallets (Atomic, Exodus, Electrum, and many others), two-factor authentication codes from a number of tools (Trezor Password Manager, EOS Authenticator, Authy 2FA, Authenticator 2FA), as well as grab screenshots, take Steam and Discord tokens, and Telegram authentication files."

More deepfakes coming, Microsoft warns
Microsoft’s chief science officer, Eric Horvitz, recently published a new research paper in which he warns of incoming dangerous deepfake attacks. The paper, titled "On the horizon: Interactive and compositional deepfakes", claims interactive and compositional deepfakes are coming.
From our news piece: "He also says that in the near future, it will be almost impossible to distinguish fake videos and fake content from authentic ones: “In the absence of mitigations, interactive and compositional deepfakes threaten to move us closer to a post-epistemic world, where fact cannot be distinguished from fiction.”

Adware found in Play Store and App Store apps
Researchers have found almost a hundred apps on both Android, and iOS, engaging in advertising fraud. According to a report from cybersecurity firm HUMAN security, there are at least 80 Android apps, and nine iOS apps, carrying software development kits (SDK) that made the apps serve malicious ads to their users.
From our news piece: "Research from cybersecurity firm HUMAN Security found that by targeting advertising software development kits (SDK), the unknown threat actors were able to compromise these apps for their own personal benefit, in multiple ways: by pretending to be apps they’re not; by rendering ads in places where users wouldn’t be able to see them; and by faking clicks and taps (keeping track of real ad interactions and faking them later)."

