Meta kicks out 7 hacking-for-hire companies - It includes an Indian one
No surprises: It's BellTrox

Meta, which has been under fire for turning a blind eye to companies pursuing 'digital espionage' on its platform, finally seems to have cracked the whip. Meta has kicked out seven “surveillance-for-hire” companies, including an Indian one, that apparently used the platform to target at least 50,000 individuals across 100 countries for unlawful sleuthing operations, some of which included the deployment of spyware.
Meta has culled hundreds of accounts belonging to firms known as Israeli Cobwebs Technologies, US companies Cognyte, Black Cube, Bluehawk CI, Macedonia-based Cytrox, an unknown entity in China, and India-based BellTroX. Meta has sent cease and desist letters to the six named companies.
"While these 'cyber mercenaries' often claim that their services only target criminals and terrorists, our months-long investigation concluded that targeting is in fact indiscriminate and includes journalists, dissidents, critics of authoritarian regimes, families of opposition and human rights activists," Meta said in a statement.
- Are you a target of Pegasus spyware? Get an iPhone and stay safe
- Pegasus Spyware: Is your mobile ever really safe from being hacked?
How surveillance-for-hire companies operate
The global surveillance-for-hire industry targets people to collect intelligence, manipulate and compromise their devices and accounts across the internet. And this move by Meta comes on the back of larger attempts by American tech companies, and civil society in general against purveyors of digital espionage services, notably the Israeli spyware company NSO Group, which was blacklisted earlier this month.
Meta itself had earlier sued the NSO Group in 2019 for allegedly using its messaging app WhatsApp to deploy malware used for spying on 1,400 mobile devices. NSO Group has disputed the claim.
Giving a broad overview of how these seven blacklisted companies operated, Meta sliced their surveillance activities into three phases: Reconnaissance, Engagement and Exploitation.
"Each phase informs the next. While some of these entities specialize in one particular stage of surveillance, others support the entire attack chain," Meta said.
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.
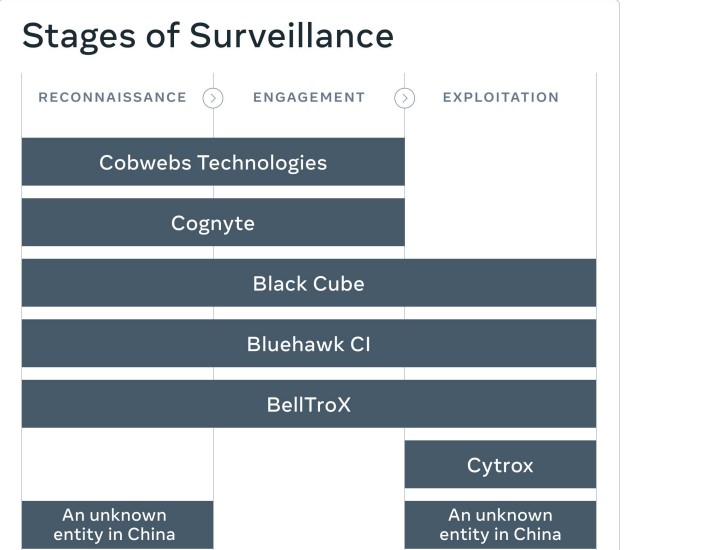
It added: "As a result of our months-long investigation, we took action against seven different surveillance-for-hire entities. They provided services across all three phases of the surveillance chain to indiscriminately target people in over 100 countries on behalf of their clients."
Only the unidentified Chinese firm and Cytrox had gotten to the exploitation stage, as per Meta.
Meta has shared its findings with security researchers, other platforms, and policymakers so they can take appropriate action. It also alerted around 50,000 people who it believes were targeted by these malicious activities. Meta could not identify how many of the possible victims were attacked with malware or other exploitation software.
The BellTrox story
BellTroX InfoTech Services being banned by Meta as a cyber mercenary does not come as a surprise. For, in June last year, the Toronto-based internet watchdog Citizen Lab, in an investigation report, had claimed that BellTrox, owned by one Sumit Gupta, and headquartered in New Delhi, had hacked into, and spied on, over 10,000 email accounts of targets across countries and professions, including lawyers, doctors, activists, and members of the clergy in countries including Australia, Angola, Saudi Arabia, and Iceland.
"We removed about 400 Facebook accounts, the vast majority of which were inactive for years, linked to BellTroX and used for reconnaissance, social engineering and to send malicious links," Meta said in its yesterday report.
BellTrox's activity on Meta platform was limited and sporadic between 2013 to 2019, after which it paused.
"BellTroX operated fake accounts to impersonate a politician and pose as journalists and environmental activists in an attempt to social-engineer its targets to solicit information including their email addresses, likely for phishing attacks at a later stage," Meta said in its report.
This activity, based on the exact same playbook, re-started in 2021 with a small number of accounts impersonating journalists and media personalities to send phishing links and solicit the targets’ email addresses.
Interestingly, at least going by Meta's report, BellTrox had not hacked into any Indian target.
- Protect your devices with these best antivirus software
Follow TechRadar India on Twitter, Facebook and Instagram for the latest updates.

Over three decades as a journalist covering current affairs, politics, sports and now technology. Former Editor of News Today, writer of humour columns across publications and a hardcore cricket and cinema enthusiast. He writes about technology trends and suggest movies and shows to watch on OTT platforms.