Over 1TB of confidential US company data accidentally exposed
Even redacted details could potentially be uncovered, experts warn

Cybersecurity researchers have helped seal a breach that exposed millions of documents of US businesses stored in misconfigured Amazon S3 buckets.
Data breach watchdogs WizCase ran across over eighty such misconfigured cloud storage data silos that exposed data totaling over a terabyte.
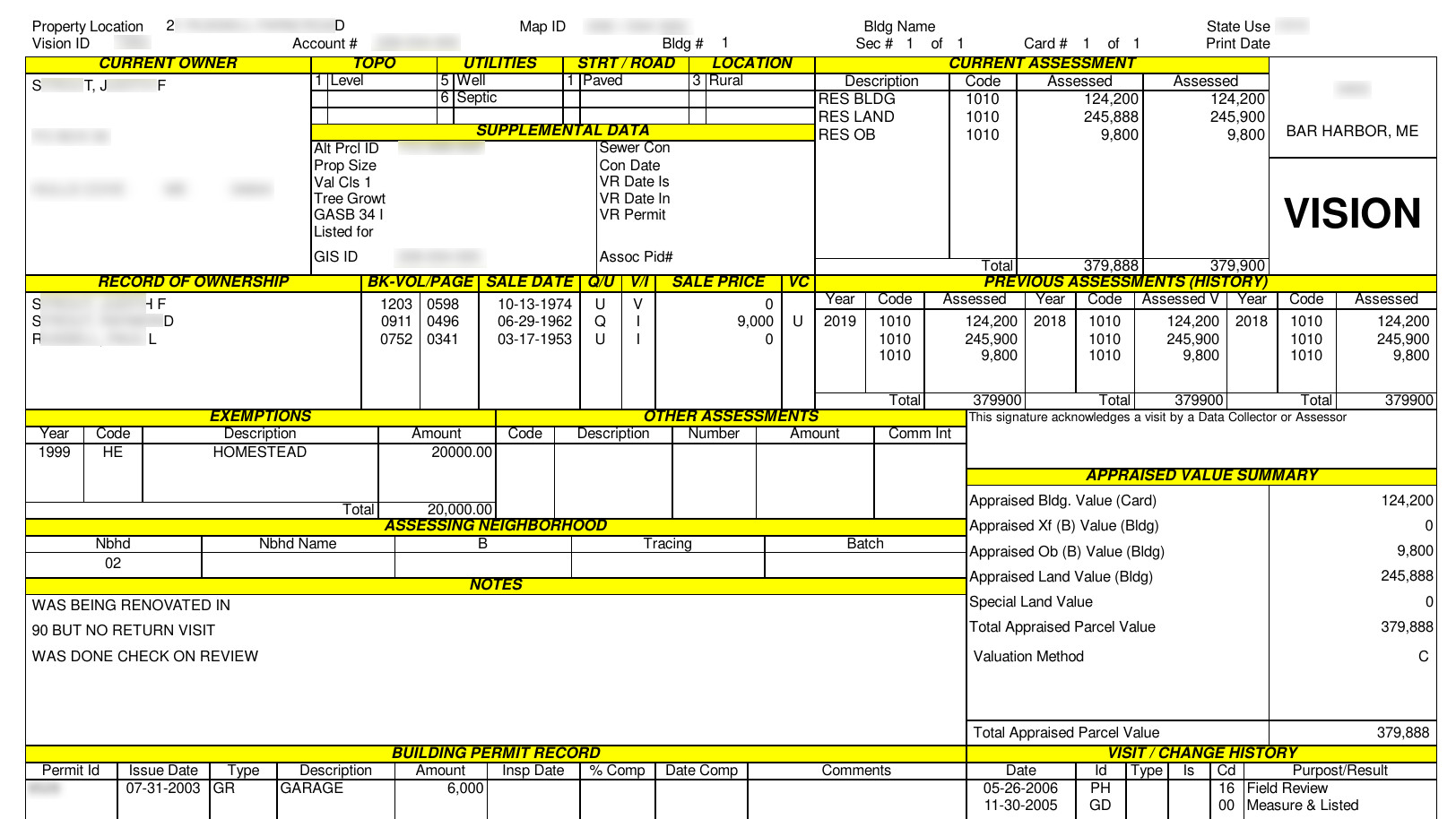
According to redacted versions of the files seen by TechRadar Pro, the documents include real estate tax information about businesses, along with photographs of the properties, as well as the building and city plans from various municipalities, mostly in the state of Massachusetts.
We're looking at how our readers use VPNs with streaming sites like Netflix so we can improve our content and offer better advice. This survey won't take more than 60 seconds of your time, and you can also choose to enter the prize draw to win a $100 Amazon voucher or one of five 1-year ExpressVPN subscriptions.
- We've put together a list of the best endpoint protection software
- Here’s our list of the best password managers
- Check our list of the best firewall apps and services
“The breach could lead to massive fraud and theft from citizens of those municipalities. The highly-sensitive nature of the data contained within a local government’s database, from phone numbers to business licenses to tax records, are highly susceptible to exploitation by bad actors,” suggests WizCase in a blog post sharing details about the misconfigured buckets.
Mapping the source
WizCase says its researchers noticed that the name of the misconfigured buckets suggested they were used by the same software, which led them to the Massachusetts-based information management software developer, PeopleGIS.
In addition to business licenses, the silos also contained several pieces of personally identifiable information (PII) in residential records such as deeds, tax information, and resumes for applicants to government jobs.
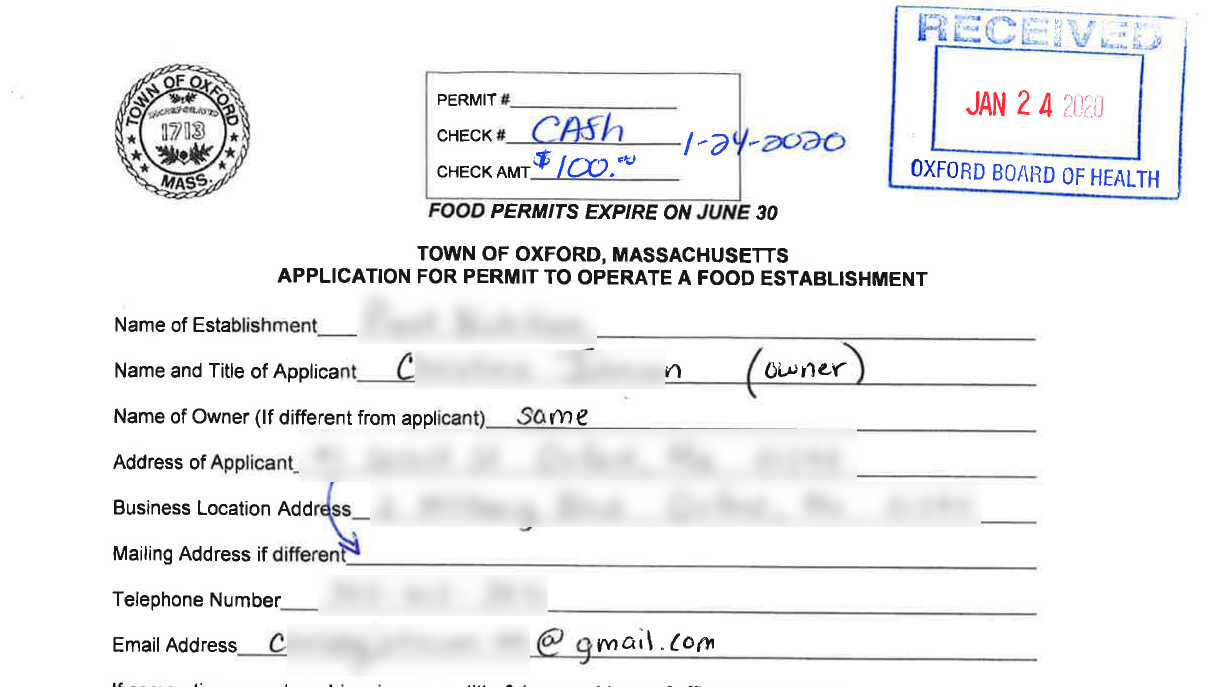
“Some of the vulnerable documents were redacted, but they were digitally redacted using transparent tools like a marker. This means whoever found them could change the contrast level of the document in a photo editor and see the redacted information,” suggests WizCase.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
In all, WizCase researchers could access 86 S3 buckets without having to contend with any password or encryption. PeopleGIS has since secured the buckets, once WizCase alerted them about the misconfiguration.
- Protect your devices with these best antivirus software
With almost two decades of writing and reporting on Linux, Mayank Sharma would like everyone to think he’s TechRadar Pro’s expert on the topic. Of course, he’s just as interested in other computing topics, particularly cybersecurity, cloud, containers, and coding.
