HummingBad malware is infecting devices with fake ads - here's how you can protect yourself
Fake ads are a highly lucrative business

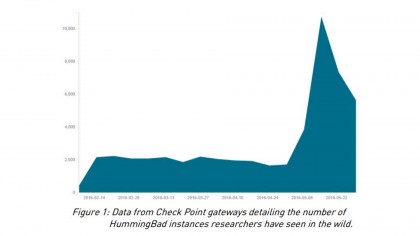
10 million. That's how many Android devices have been infected globally by the HummingBad malware, according to cybersecurity firm Check Point.
If you haven't heard of HummingBad before, you're not alone. The malware was only discovered to be blighting Android devices in February of this year. Originating from China, HummingBad injects infected ads and installs fraudulent apps on users' devices. Check Point's security researchers found the malware created a persistent rootkit (an undetectable backdoor), which helped generate fraudulent ad revenue and plagued users with malicious apps.
A group of 25 cybercriminals by the name Yingmob is behind HummingBad, according to Check Point. Yingmob skirted detection by working alongside a legitimate Chinese analytics business, allowing the group to share the company's resources and technology. The analytics company has been complicit with Yingmob's malicious software in order to generate more clicks for its ad servers, reports Motherboard.
HummingBad's fake ads are particularly pernicious: they trick users into clicking on them by refusing to close, resulting in an unusually high 12.5% click-through rate. Smart Insights says US users only click on 0.10% of legitimate mobile ads overall, making HummingBad's rate incredibly high. Check Point estimates Yingmob is making approximately $300,000 (about £230,203, AU$402,420) per month from this fraudulent ad revenue.
How HummingBad changes the malware game
HummingBad shows just how fast cybercriminals are adapting to a mobile-first world. Yingmob quickly achieved self-sufficiency, and showed that a small group of criminals could launch a widespread attack to create a large network of infected phones called "bots." These bots have the ability to generate targeted attacks against governments or businesses since infected phones are at the mercy of criminals.
Yingmob also doesn't discriminate. The group is responsible for the Yispecter, an iOS malware that targeted a porn player that installed fraudulent apps to gain revenue.
Since Yingmob works alongside a legitimate Chinese ad analytics company, the line between legitimate and fraudulent apps becomes blurred. Check Point estimates 85 million devices are running Yingmob's apps, but only about 10 million of them are malicious.
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.
What makes HummingBad so scary is that it can run undetected. Rooted users won't be able to detect if malicious software is being installed as it can be performed remotely and silently. And if you're not rooted, HummingBad will repeatedly try to get you to install apps, though it's unclear whether uninstalling the apps will remove them completely.
How to protect yourself
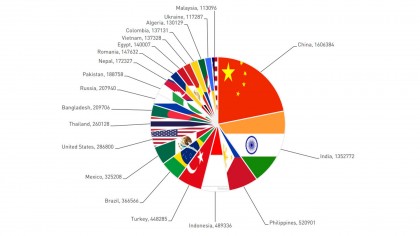
The HummingBad malware is a global one, but has the biggest hold over China and India. The US has approximately 286,800 devices running malicious apps. The UK and Australia weren't listed as being substantially affected by HummingBad.
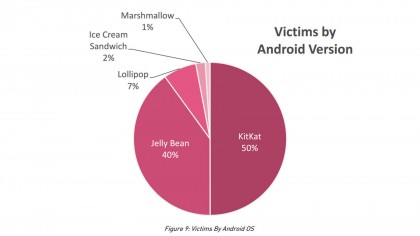
A majority of infected Android users are running the outdated KitKat version (4.4) of Android with the most current version, Marshmallow (6.0), making up only 1% of affected devices.
HummingBad is certainly worrisome, but there are steps you can take to prevent yourself from falling victim.
1. Don't root your Android device: HummingBad scans if your Android device has root access and will install infected apps silently without your knowledge, if you are in fact rooted. If you don't have root access to your phone, HummingBad will try to trick you into allowing it to install software by imitating a legitimate app. This installation process will, at the very least, give you a red flag that something's wrong.
2. Don't allow installation from "Unknown Sources": Some Android users will check the option to install software from "Unknown Sources" in the settings to install apps that aren't available in the Google Play Store. Amazon's Android app store requires this option to be enabled, but it poses a security vulnerability if users aren't closely monitoring what apps are being installed. It's best to leave the "Unknown Sources" option unchecked.
3. Update your phone to the latest software: If you've been dismissing that nagging notification to update your phone's software, don't. Android's software updates contain security fixes and improvements that will help you avoid falling victim to HummingBad. Check Point's data shows most affected devices are running outdated versions of Android.
4. Install an antivirus app: While antivirus apps can't stop all attacks, they can be an additional security layer, alerting you to apps that are asking for excessive permissions or blocking app installs.
HummingBad proves cybercriminals and their methods of attack are becoming more sophisticated. Phone makers and antivirus companies have an increasingly challenging task of securing our phones, but taking common-sense precautions like the ones listed above should help you avoid falling victim.
- Best antivirus for Android apps: download these apps now
