All of us know the importance of having adequate antivirus protection before venturing online. But how exactly does a virus work?
What makes viruses differ from worms, and how has the sophistication of both increased over the years?
Ever since it started to develop alongside the first home computers, malware has become an increasingly virulent and ingenious threat. But that threat is evolving fast.
Nowadays, it's not only internet users who are at risk, but also website owners, whose poorly written web applications are being exploited and used to plant malicious code that infects others through the browser.
Vectors of infection
There's a saying in nursing that 'germs don't jump'. That is, they can't escape the Petri dish and spread by themselves. Human viruses such as influenza, for example, require poor hygiene to help them spread. This is called an 'infection vector'.
In a similar way, computer viruses need to be shifted from one place to another by users, accidentally or not.
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.
When the first modern viruses hit home computers in the 1980s, the infection vector was the boot sector of floppy disks. One of the first such viruses was Elk Cloner, which was written in 1981 by a 15-year-old high school student from Pittsburgh, Rich Skrenta.
Elk Cloner lived in the boot sector of Apple II system disks. When the machine booted up using an infected floppy disk, it would run as part of the operating system and then stay running, watching for the insertion of any subsequent disks.
This form of operation makes it a 'resident' virus. When a second user booted his own machine with the copied disk, the virus would run on that system, too. With every fiftieth boot of an infected machine, Elk Cloner would display a little poem. This was the virus's 'payload'.
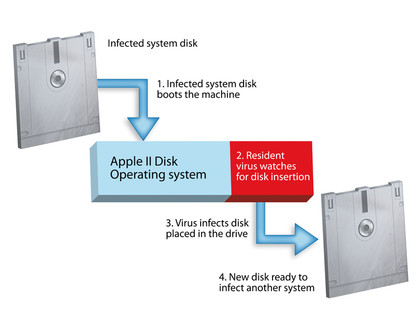
ELK CLONER: Ironically, one of the first 'viruses' was written for the Apple II
The subroutine within Elk Cloner that watched for a new floppy disk insertion is now generally known as a 'target locator' (or sometimes a 'finder module'). The target locator in a resident virus waits for the OS to perform a specific task. Executing a file is a good example. When this happens, the target locator knows that the file in question can be infected.
Infection itself is handled by code called the 'infection propagator'. Unlike today, early antivirus software didn't always check RAM properly for resident infections before scanning files, so opening executables to scan them could also infect them.
As well as resident viruses, there are also 'non-resident' viruses. These attach themselves to executables and wait for them to be run.
When the user starts an infected application, the target locator runs first and finds other executables to infect. It then hands control to the infection propagator, which infects the found executables. Finally, the virus hands control to the application as if nothing had happened.
Because of this, reinstalling a fresh copy of an infected application on a system infested with a non-resident virus makes little difference, because it can quickly become reinfected by other applications.
With the rise in popularity of Microsoft Office in the early 1990s, virus programmers began to use another non-resident virus technique. Office documents allow you to embed macros written in Word Basic that run automatically when you open the file. If the macro is malicious, you're in trouble.
This is how the Concept virus of 1995 worked. This virus is thought by some to be the most widespread virus infection of all time. Social engineering has always played a huge part in spreading viruses. Everyone loves free stuff, and virus writers often infect pirated software in order to spread their work. Others write Word documents purporting to contain passwords for porn sites and infect them with macro viruses.
The Melissa virus of 1999 was a good example of this ploy. Its payload tried to mass-mail the infected document to the first 50 people in the infected user's Outlook Express address book.
While true viruses only infect files on a single system (unless users decide to swap files), Melissa could copy itself to new computers without human intervention. Because of this, it's classed as a computer worm.
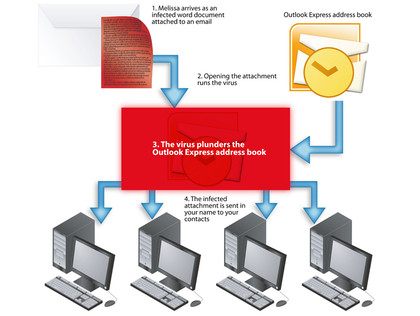
MELISSA: Modern viruses can not only infect your machine but it could infect everyone in your Outlook file
The same basic technique was used to spread the famous I Love You virus of 2000, whose malicious payload also made changes to infected systems.