To run Process Explorer, right-click its icon and select 'Run as administrator'. Starting in this way gives Process Explorer more access to important information. Click 'Yes' on the 'User account control' window that pops up.
If you're running on a 64-bit CPU, you'll notice that a second executable suddenly appears in the directory containing Process Explorer. This is called 'procexp64', and is a wrapper that the original 32-bit executable creates to satisfy conditions for running on a 64-bit machine. It's a temporary file and should disappear when you close the running program, though you might have to press [F5] to refresh the directory to see this.
Process Explorer works the same in 32-bit and 64-bit environments. It provides far more detail than Task Manager, and it can manage tasks just as well as the Windows 7 offering.
To begin, click the 'Process' column until the display changes to an indented hierarchy. This makes it easy to see which processes are the parents of others. 'Wininit', for example, is the ancestor of a large number of processes, including those multiple instances of 'svchost.exe'. Now we have a better view of the running OS, we can begin to look for malicious processes masquerading as legitimate ones.
With all those svchost processes running, it's relatively easy for malware to call itself something that will look like 'svchost' to the untrained eye. For example, it might call itself 'svch0st.exe' (with a zero), 'svhost.exe' (without the 'c'), or any other combination of letters and numbers that attempt to subtly resemble the original file name. These are all malicious impostors.
To make it easier to spot such files, you can click the 'Process' column heading until you get an alphabetical listing. To get more details of any process, double-click it. You can verify that the process hasn't been tampered with or infected by malware by selecting the 'Image' tab.
Next to the process's icon are the words 'Not verified'. Clicking the 'Verify' button verifies the image against a stored signature. Process Explorer uses the running process to generate its own signature and compares the two. If they match, it changes the text to read 'Verified'.
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.
When verifying images, pay particular attention to processes that have no entry in the 'Company name' column, those whose description is blank or meaningless, and those whose name is a jumble of letters.
If verifying the image of a seemingly legitimate process produces the message 'Unable to verify', don't panic. It's likely that the manufacturer isn't a verified signer of images. Some very old software, like Microsoft Office 2000, has no signature to check, which will lead to an 'Unable to verify' message.
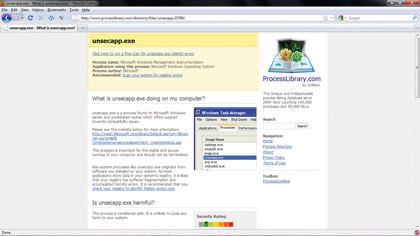
For cases like this, Process Explorer also has a handy feature for checking the validity of any running process by using the knowledge of the wider community of Windows 7 users.
Right-click a suspicious process and select 'Search Online'. Your web browser will then open and Process Explorer will perform an online search.
One particularly good, authoritative source of information for each process is www.processlibrary.com. If this site is not in the search results, using Google Search, you can add the phrase 'site:www.processlibrary.com' to the end of the search term to just return results from that site.
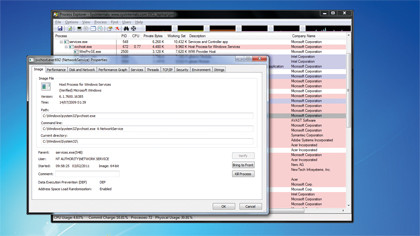
Another good way of verifying that a process is malware is to examine the path leading to its executable. By double-clicking on a suspicious process and clicking the 'Image' tab, you can see the full path to the executable, the options used to start the process, and the working directory it uses.
System directories in Windows 7 are all well protected by default, so any malware will have to use a temporary directory outside of the system area. Any process that isn't an application you've started (or a service related to an application you've installed) and which shows a path or working directory outside of the C:\Windows directory tree should be treated as possible malware, especially ones that use the 'Temp' directory.
Spying on spyware
Discovering what a suspicious process connects to, if anything, is a good way of deciding whether it's malicious. If a botnet client has infected your computer, it'll need to phone home to receive orders on a regular basis, for example.
In Process Explorer, double-click the suspicious process, then click the 'TCP/IP' tab. To convert the IP addresses listed into DNS names, ensure that the 'Resolve Addresses' tick box is selected. Note down any unknown sites and search for them online.
Many of the processes you interrogate in this way will be listening to the local machine. You can tell because rather than the local or remote address being an external DNS name, both will be your PC's name, a colon, and the port number. Many processes use ports to communicate locally; it's nothing to worry about.
Sometimes normal processes can go wild and suddenly take nearly 100 per cent of the CPU time. If you have a dual core processor or better, you can still access the system and kill the process using Process Explorer.
It's a good idea to keep Process Explorer open in the background for a few days to get a feel for what's normal for your PC based on your typical usage. You'll see your anti-malware update itself, discover what uses most CPU, see which applications hog your memory and much more.
You can also add columns to the display by right-clicking a column heading and selecting 'Select columns'. The range of columns covers memory, disk and network use, threads, DLLs and even .NET components.
------------------------------------------------------------------------------------------------------
First published in PC Plus Issue 252. Read PC Plus on PC, Mac and iPad
Liked this? Then check out 10 tips for removing stubborn malware
Sign up for TechRadar's free Weird Week in Tech newsletter
Get the oddest tech stories of the week, plus the most popular news and reviews delivered straight to your inbox. Sign up at http://www.techradar.com/register