Recover lost photos: how to repair corrupt images
We show you how to recover lost photos, with the best JPEG repair tools around
And the winner is...
Image repair tools can be alarmingly expensive, but if you're on a strict budget then Office Recovery may be a good place to start.
Its repair tools weren't up to the standard of the rest, and it's relatively awkward to use, but the service can still repair simple corruption issues for free.
And for sheer ease of use and an excellent trial version, JPEG Recovery Pro has to be worth a look. Image repair rates were reasonable, and unlike some of the competition, the trial build doesn't obscure recovered images with a massive watermark, which makes it much easier to confirm that it's worked.
Ultimately, there are three programs which stood out from the rest, though.
In third place was Picture Doctor. It's likeable, easy to use and has the best recovery rate here, but a high price and annoying watermark were issues.
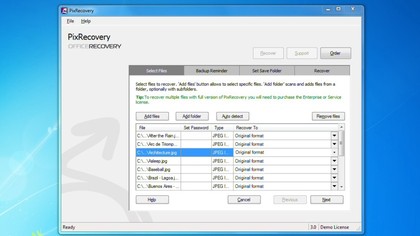
PixRecovery was our runner-up, thanks to its wide image format support and general configurability.
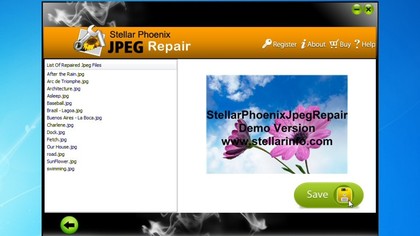
But first place has to go to Stellar Phoenix JPEG Repair. It almost matched Picture Doctor's recovery rate for less than half the price, with a far less intrusive watermark, and some useful extras, and this sheer all-round excellence makes it a worthy winner.
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.

Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided. Mike began his career as a lead software developer in the engineering world, where his creations were used by big-name companies from Rolls Royce to British Nuclear Fuels and British Aerospace. The early PC viruses caught Mike's attention, and he developed an interest in analyzing malware, and learning the low-level technical details of how Windows and network security work under the hood.