Simple solutions for message encryption
Technologies and apps to scramble those messages

The revelations that the US National Security Agency (NSA) and the UK's Government Communications Headquarters (GCHQ) have been intercepting internet traffic highlight an important fact: many forms of communication are not secure from prying eyes and ears.
The worry is that if the US and UK intelligence communities can snoop on your confidential business communications, then perhaps other governments' intelligence agencies may also do so - not to mention business competitors and criminal gangs.
A partial solution is to encrypt you communications - email, instant messages, mobile phone calls and text messages. Good encryption ensures that no-one who intercepts your communications can read or change the contents. But it's only a partial solution because encrypted messages usually still provide some information, such as who you are communicating with.
Encryption is also a signal that the content is worth hiding - a sure-fire way to attract the attention of eavesdroppers. A foreign intelligence service could store any encrypted communications it intercepts in the hope that in the future new technology will enable their decryption.
PKI encryption
Many encryption systems need two keys: a public one which you make freely available to anyone who wants it, and a private one which you keep secret. A person with your public key can use it to encrypt a message to you - and the message can only be decrypted using your private key.
In the same way, you can encrypt messages to anyone whose public key you have, and it can only be decrypted with their corresponding private key.
This type of solution, known as public key infrastructure (PKI), is extremely secure but far from straightforward to use. It involves acquiring and managing - or at least knowing where to find - the public keys of the people with whom you want to communicate. That's assuming that they even have one.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
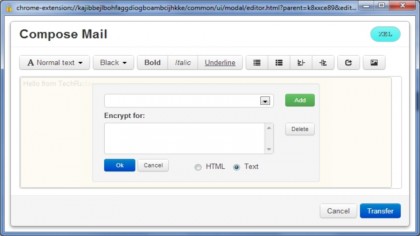
If you're a Microsoft Outlook user you can generate your own keys and encrypt your emails with a plugin called Outlook Privacy Plugin. You can also use the PKI encryption with popular webmail systems including Gmail, Yahoo! Mail and Outlook.com using a browser extension for Firefox or Chrome such as Mailvelope.
Easier use
The good news is that there are plenty of products around offering good encryption which are easy to use and avoid the problem of managing keys altogether.
Many are free and open source while still being up to scratch for business. In fact there's a good argument for saying that you should use open source encryption products whenever possible. That's because it's only possible to verify if a product is as secure as the developers say if the source code is open for inspection.
Encrypted email
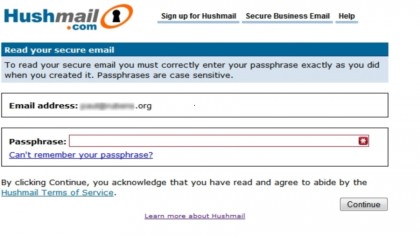
Hushmail is a simple webmail service which uses strong encryption to protect messages.
If you are sending an email to someone who has never used Hushmail before then you are asked to add a question to the email (such as "Where did we eat last night?" or "What is the password that we arranged?") that the recipient must answer correctly to decrypt the message. They will then be prompted to supply their own passphrase that can be used to unlock any subsequent emails.
Read our full Hushmail review.
Encrypted instant messaging
Cryptocat is a free, open source add-on to the Firefox, Chrome and Safari browsers that provides an encrypted instant messaging and file transfer application.
You can use it to chat to colleagues securely in a pre-arranged conversation room from anywhere in the world. Each time you log on and join a conversation the software generates new encryption keys which are exchanged with other users automatically, so there is no possibility of Cryptocat being able to intercept and read your messages.