Forget TPM chips for Windows 11, that’s not even the half of it
There's more to hardware security than TPMs
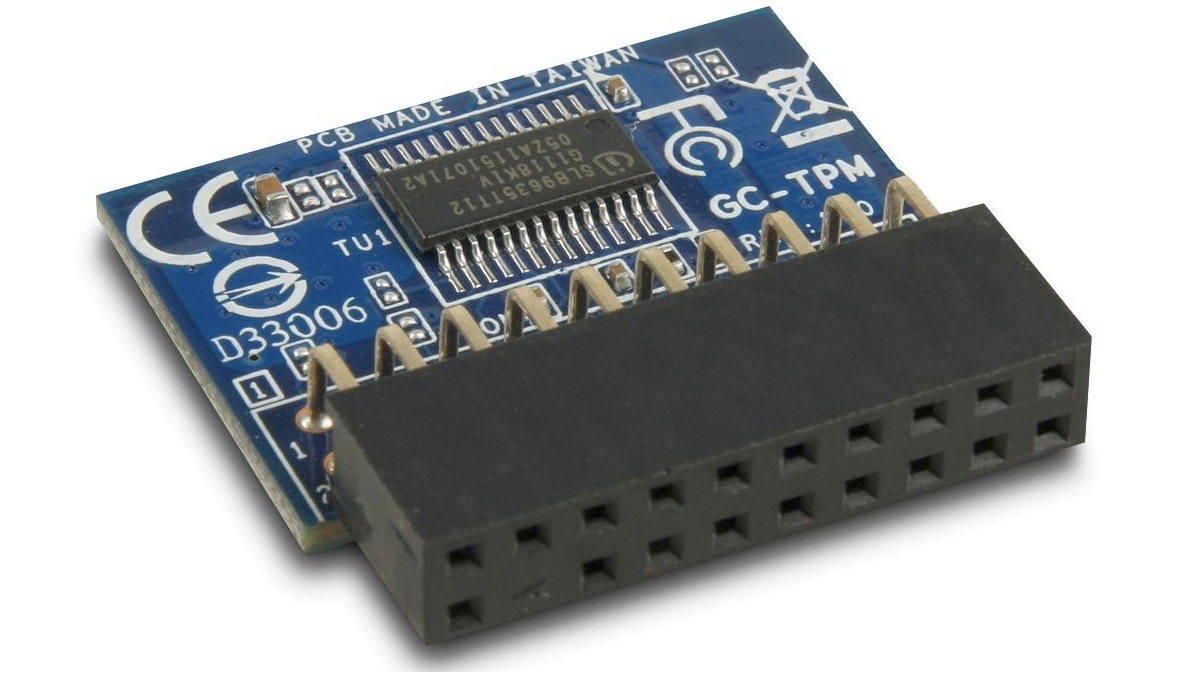
Microsoft has confused just about everyone with its minimum hardware requirements for Windows 11. At the heart of the confusion is a piece of technology known as a Trusted Platform Module, or TPM.
The job of TPM chips is to perform cryptographic operations that provide security at a hardware level and verify the authenticity of a system at launch. They also feature various mechanisms to make them resistant to tampering.
Among other specifications relating to the CPU, RAM and storage, Windows 11 will require all machines to feature TPM 2.0 support, either built into the CPU or in the form of an additional chip connected to the motherboard.
- Here's our list of the best antivirus services around
- Take a look at our list of the best ransomware protection out there
- Check out our list of the best endpoint protection software
The announcement sent PC owners scrambling to find out whether their device supports TPM and, in some cases, how to switch it on in the BIOS. And the subsequent revelation that Windows 11 can technically be installed on incompatible machines only added to the confusion.
However, one company is scratching its head over the TPM decision for a different reason. According to Jorge Myszne, founder and CEO of semiconductor startup Kameleon, TPM is already an anachronistic technology.
“TPM is from 2003; it was good enough 20 years ago, but think about everything that has changed in terms of infrastructure over the last two decades,” he told TechRadar Pro.
While the TPM standard has evolved significantly since its inception (the latest TPM 2.0 update was published in 2019) thanks to input from a range of organizations, Myszne suggests this approach to security suffers from a fundamental flaw.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
“The main challenge is that the TPM is a passive device; while you can store data there and nobody can see it, in order to do something with that data the software needs access. And if the software has access, an attacker can gain access too.”
Firmware security
Founded in 2019 and backed by Xilinx, a pioneer in the field of programmable SoCs, Kameleon’s objective is to reverse the dynamics of cybercrime, by handing the advantage to the defender.
Although the company is yet to bring a product to market, it is working on a piece of hardware called a Proactive Security Processing Unit (ProSPU) that it hopes can combat the threat of firmware attacks, which are increasing in volume and sophistication.
“The most common types of attacks take the form of applications that target the upper layers, but these have been fairly successfully blocked,” Myszne explained. “As a result, attackers are becoming more specialized, heading down the stack towards the firmware; attacks here are both difficult to detect and persistent.”
Recent figures from Microsoft show that 80% of organizations have suffered at least one firmware attack over the last couple of years. However, less than a third of security funding is set aside to protect firmware, and 21% of security chiefs even admit that firmware goes totally unmonitored.

The problem with attacks of this kind is that they cannot be identified and blocked by software. At launch, a system is booted in increments, starting with a small footprint of code that loads into the CPU, followed by a larger pool of code, then eventually the operating system loads from the hard drive or network.
“Any compromise that takes place during this process is completely undetectable. Software isn’t even running yet, so it has no way of checking what’s going on,” noted Myszne.
The solution to this problem, he says, is to have a dedicated device in charge of the security of a system. In the same way GPUs handle graphics and TPUs handle AI workloads, a security processor is tasked with establishing a “root of trust” by checking that all firmware is authentic.
A dedicated security processor
Designed for servers and data center use cases, Kameleon’s ProSPU aims to remedy the kinds of problems that arise as a result of the reliance of TPM chips (and other equivalents) on software for instruction.
Whereas TPMs are passive, creating an opportunity for infiltration by an attacker, the ProSPU is master of the system, performing active checks to verify each element of the boot process is authentic. Many chips on the market already perform their own secure boot, Myszne concedes, but there’s nothing out there that “pokes around in all the different places”.
As well as establishing this root of trust, the ProSPU provides crypto services to software (e.g. key generation, key management, encryption and decryption), and runtime security to detect and prevent attacks.
With direct access to the memory, beneath the OS, the ProSPU can operate outside the view of potential hackers. Because it doesn’t rely on APIs for access, there is nothing for an attacker to infect.
“The first thing an attacker does is attempt to understand the system and defences. In this case, the defence is running on a different system entirely, with direct access beneath the software,” said Myszne.
“The attacker doesn’t know what’s going on and now needs to attack the system without an understanding of the defences. And because attackers don’t like risk, they will go elsewhere.”
Future of hardware security
Asked whether he thinks Microsoft made the wrong decision by mandating TPM 2.0 support for Windows 11, Myszne nodded in agreement.
“If I was working on an enterprise-level operating system, then yes, but for a generic OS like Windows it’s a big bet, because there will be problems,” he said.
“Usually, TPMs are disabled by default, because they are difficult to manage; you need to know what you’re doing or else risk bricking your computer. How many people know how to fiddle with the BIOS safely?”
Although Myszne concedes that a TPM is better than nothing from a security perspective, he suggests the combination of poor user experience and an insufficient level of protection mean the requirement will be more hassle than it’s worth.
“The system is not a single chip device as it used to be 20 years ago. We need hardware security infrastructure to evolve for the needs of today, as well as the needs of the next five to ten years.”
Kameleon expects an alpha version of the ProSPU to land by the end of the year, and to be inside servers by H1 2022. Although applications of the technology are most urgent in data center contexts, due to the concentration of risk, Myszne predicts ProSPU-style hardware will filter down into the consumer, industrial and automotive markets within the next two to three years.
“There’s a lot to defend out there,” he said.
Update: September 13, 10:00am BST
This article has been updated to reflect the continued evolution of the TPM standard.
- Here's our list of the best cloud backup services

Joel Khalili is the News and Features Editor at TechRadar Pro, covering cybersecurity, data privacy, cloud, AI, blockchain, internet infrastructure, 5G, data storage and computing. He's responsible for curating our news content, as well as commissioning and producing features on the technologies that are transforming the way the world does business.