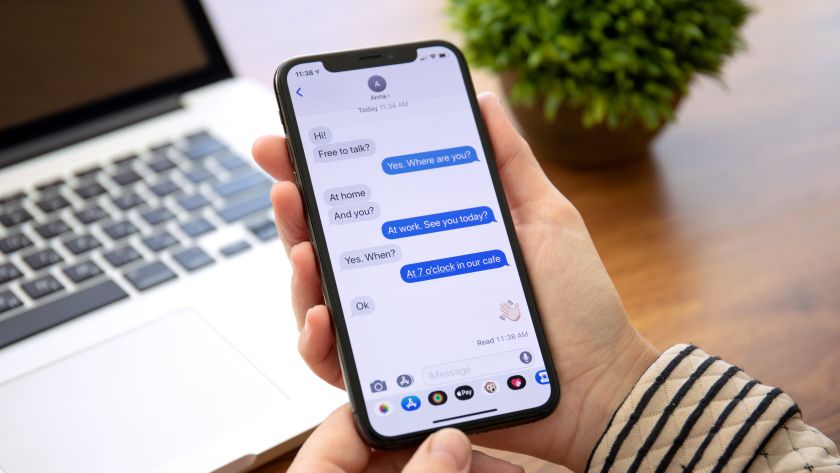
Ransomware operators have adopted a dastardly new strategy
Victims of ransomware attacks are being harassed over the phone

A number of different ransomware groups have adopted a new strategy designed to further intimidate victims: harassment over the phone.
Reports from multiple cybersecurity firms suggest the trend emerged in late summer and is targeted primarily at businesses suspected of using data backups to restore systems after an attack.
Ransomware operators known to have contacted victims via telephone include Sekhmet, Maze, Conti and Ryuk. According to security company Coveware, recurring call scripts suggest these groups may have outsourced the task to the same call center.
- Here's our list of the best antivirus services right now
- We've built a list of the best endpoint protection services on the market
- Check out our list of the best malware removal software available
“We are aware of a 3rd party IT company working on your network. We continue to monitor and know that you are installing SentinelOne antivirus on all your computers. But you should know that it will not help,” one victim was told over the phone.
“If you want to stop wasting your time and recover your data this week, we recommend that you discuss this situation with us in the chat or the problems on your network will never end.”
Evolution of ransomware
Since ransomware grew to prominence in the mid-2000s, attacks have become increasingly sophisticated and operators have deployed ever more dastardly tactics. The most significant development in the space can be seen in the frequency with which data is now exfiltrated as part of an attack.
Previously, ransomware simply encrypted files on a business’s network, making them inaccessible, but this problem could be resolved by restoring data from a backup. However, by lifting corporate data as well as encrypting systems, ransomware operators give themselves far greater leverage in negotiations, over which the threat of a data leak looms large.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
The use of phone calls as a means of intimidation can be seen as another step in the evolution of this highly effective form of cyberattack.
This year alone, multiple high-profile companies have fallen victim to ransomware, including Canon, Capcom, Kmart, Equinix and Cognizant. Operators also launched attacks against healthcare facilities at the height of the pandemic, preventing proper care from being administered.
Even in cases in which the business pays the ransom, there can be no guarantee the stolen data is deleted, opening the door to secondary extortion attempts.
- Here's our list of the best ID theft protection services right now
Via ZDNet

Joel Khalili is the News and Features Editor at TechRadar Pro, covering cybersecurity, data privacy, cloud, AI, blockchain, internet infrastructure, 5G, data storage and computing. He's responsible for curating our news content, as well as commissioning and producing features on the technologies that are transforming the way the world does business.