DNS-over-QUIC becomes proposed standard: Why it is good news for your privacy
Better equipped to meet the challenges of the digital age

DNS-over-QUIC, abbreviated as DoQ, became a proposed standard last month. It did so without much fanfare, but it is an occasion worth celebrating.
Andrey Meshkov is co-founder and CTO of Adguard.
In mid-May, DoQ was published as an RFC (Request for Comments, a document that describes online protocols, methods, programs, or research applicable to the Internet), was assigned the number 9250 and since then has been treated as a proposed standard.
The protocol has been five years in the making, and it won’t become a full-fledged Internet standard overnight. However, the industry has sufficiently warmed up to DoQ to start implementing it already, because it is much superior to the existing try-and-trusted protocols.
Without going into technicalities right from the get-go, let’s say that DoQ, thanks to it being a relatively new kid on the block, is far better equipped to meet the challenges of the digital age. Whereas previous transport layer network protocols did a stellar job of transmitting data in near-perfect conditions of stable broadband connection, they came up short once you ushered into the wilderness of 4G, LTE, and mobile data.
DNS
Before we delve into the intricacies of QUIC, and, consequently, DoQ, let’s brush up on our knowledge on how the internet works, starting with DNS. DNS or the Domain Name System is the “address book” or the dictionary of the internet. Machines don’t understand human readable domain names, e.g yahoo.com, so they have to send a special request to a DNS resolver to translate the human gobbledegook into a machine readable IP address for them.
In a nutshell: it's a DNS resolver that facilitates human-machine interaction by converting a domain name that you type in a search bar to an IP address and by sending it back to your device.
Before QUIC
QUIC did not appear out of the blue, rather the shortcomings of its predecessors paved the way for its creation. TCP transport layer protocol has been predominantly used on the web over the last years and even decades. Other protocols — SSL, TLS and HTTP — were running on top of it.
TCP does its job well, but for several drawbacks, and head-of-line blocking (HOL blocking) is one of them.
The problem with TCP is that packets of data are transmitted in batches. When your browser sends a bunch of packets to request a connection, the server responds with a bunch of packets of its own, acknowledging the receipt. These packets are batched together in a specific order. More recent packets of data cannot be processed until the older ones are.
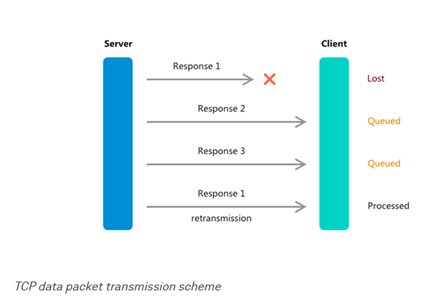
That means that if one of the response packets gets lost because of the weak connection, the rest of them will have to wait in line until the lost packet is re-sent, hoping that it gets through this time. This can slow the traffic speed down significantly, and as the demand for uninterrupted Internet connectivity across different networks grew, so did the need for a new, faster and more reliable solution. That’s when QUIC entered the scene.
QUIC
QUIC is a transport layer network protocol built on top of UDP, which transmits packets of data between servers or between a server and a client. It lives up to its name by doing things quicker than its established analogues.
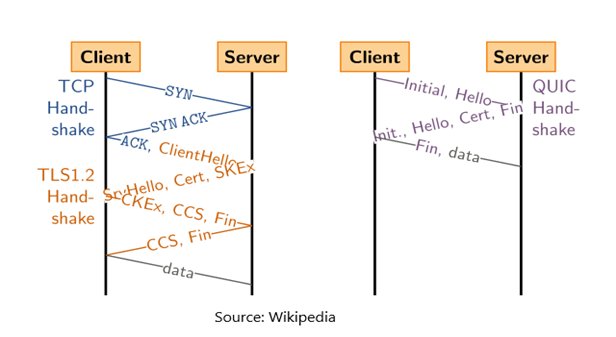
First and foremost, it is due to the fact that QUIC provides security features, like encryption and authentication, from the transport protocol itself. These features are typically performed by a higher-level protocol, such as TLS. A typical handshake you get consists of two round-trips: first, a TCP connection is established and then the TLS layer encrypts the connection. With QUIC the number of round-trips is reduced to one.
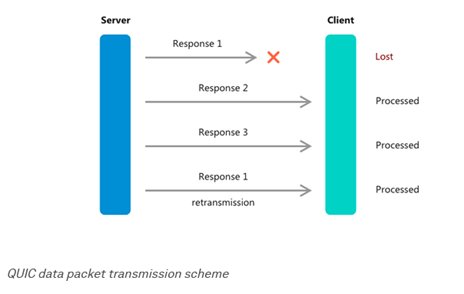
Second, unlike its predecessors that handle requests on a per-queue basis, QUIC implementation allows data to be processed without any specific order. If, say, your internet connection is glitchy and the first data packet is lost due to a poor signal, the remaining packets will be processed without delay.
Thus, the first data packet won’t be holding up the queue — and the issue of head-of-line blocking will be eliminated.
QUIC also solves the problem inherent to the extremely fast pace of life. We are constantly on the move and on the internet: in the morning we connect to the home router to scan the latest news, once we leave the house to go to work our phone switches from Wi-Fi to 4G and has to reconnect to the website and DNS servers, and when we finally reach office, our smartphone has to connect to the office Wi-Fi.
Older protocols could barely jump through all these hoops and hurdles, but QUIC can. When QUIC is in use, your phone will survive switching from one IP address to another, an event that's called "Connection Migration", without inconveniencing you as a user.
We must note that nobody has implemented “Connection Migration” yet, but judging by how it is described in the standard, we expect someone to take on the challenge of becoming a trailblazer, sooner or later.
Why DNS-over-QUIC is the future
In short, DNS-over-QUIC is a DNS protocol that uses the QUIC transport layer protocol to transmit DNS requests. Its goal is to provide maximum privacy with the minimum latency.
With DNS-over-QUIC implemented, the connection is established much faster than with DNS-over-TLS(DoT). In addition to better speed and a lesser packet loss rate, QUIC also offers more encryption options. This allows DoQ to compare favorably with DNS-over-HTTPS (DoH).
Since DoH was not originally designed as a transport layer protocol, it does not offer robust privacy protections. Using HTTP to transfer DNS requests leads to HTTP cookies, other HTTP headers (Authentication, User-Agent, Accept-Language) that convey specific information about the user, giving malefactors more opportunities for tracking and fingerprinting.
These issues could be dealt with on the client side at the DoH level, but it’s virtually impossible to have a custom solution for all the clients, that include browsers, operating systems and all kinds of software. So while DoH will also be able to support QUIC at one point thanks to the future deployment of HTTP/3 protocol, the future is still to come and the flaws inherent to its design will continue to haunt it.
Moreover, compared to the earlier versions of the draft, the final version allows for DoQ to be used not only for recursive DNS servers, but also for authoritative ones. Authoritative DNS servers provide recursive DNS servers with answers about where to find a particular website. Remember that dictionary or the address book of the internet analogy?
Authoritative DNS servers have the dictionary in their possession, while recursive DNS servers ask authoritative servers to have a look before sending (the information to the computer that requested it. Thus, the implementation of DoQ will make it possible to encrypt not only the traffic from the client (your computer or phone) to the recursive server, but also all DNS traffic in general.
DoQ deployments so far
DoQ hasn't been around that long, and it makes sense that so far only a few DNS resolvers have begun implementing and deploying it.1,217 DoQ-verified resolvers as of late January, noting a steady growth of their number since last year. According to the paper, nearly half (45.19%) of the DoQ-verified resolvers are operated in Asia, while the EU accounts for just over 32% and North America for 17.8% of the total number.
AdGuard DNS became the first public resolver to support the new DoQ protocol in December 2020. It now offers DoQ support on its Android and iOS mobile apps, as well as on all of its Windows and Mac desktop apps. Additionally, AdGuard clients can set up their own DoQ server with AdGuard Home, a network-wide open source software for blocking ads and trackers in home networks.
Another resolver that has been already using DoQ in production systems is nextDNS. As of January this year, nextDNS operated 199 DoQ-verified resolvers spread across 6 continents and 66 countries.
There have also been several implementations of DoQ: Quicdoc, written in C and based on Picoquic; aioquic, library for the QUIC network protocol in Python, and Flamethrower, a DNS tool for functional testing written in C++. AdGuard also offers DoQ support for its DNS proxy, DNS library and a DNS lookup tool.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Co-founder and CTO of Adguard.