Chinese government hackers infiltrate at least two top US ISPs
Volt Typhoon strikes again

A Chinese state-sponsored hacking group has been observed using a zero-day exploit to infiltrate internet service providers (ISPs), managed service providers (ISPs) and IT sectors since at least June 12, 2024.
Lumen's Black Lotus Labs believes the group, tracked as Volt Typhoon and Bronze Silhouette, was observed using the vulnerability, labelled as CVE-2024-39717, to breach organizations in the wild.
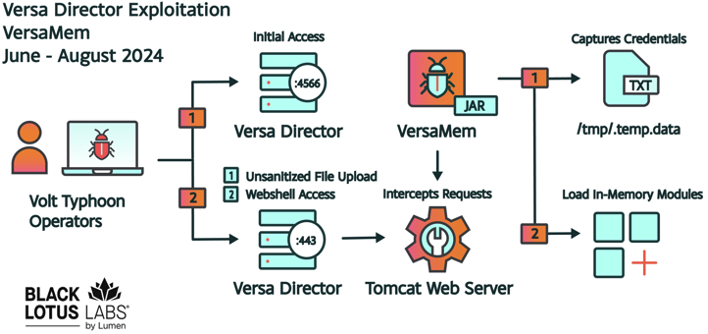
The vulnerability utilizes a complex process to inject malicious code into Versa Director servers, allowing the attacker to steal credentials in plaintext, “potentially enabling downstream compromises of client infrastructure through legitimate credential use,” Black Lots Labs said.
Breaching US ISPs
Versa Director servers are used by ISPs and MSPs to manage network configurations on software-defined wide area network (SD-WAN) software. The attackers used a custom JAR web shell - labeled “VersaMem” by Black Lotus Labs - that employs Java instrumentation and Javassist to inject code into the Tomcat web server process memory space on the victims Versa Director servers.
The web shell, named “VersaTest.png” and uploaded to VirusTotal on June 7, 2024, does not have any antivirus detections at time of writing, and can still be used to exploit unpatched Versa Director servers. So far, the vulnerability has been used to attack four victims within the US, and one non-US victim.
Douglas McKee, executive director, threat research at SonicWall, commented on the attack, stating, “The recent exploitation of a zero-day vulnerability in the Versa Director software by the Chinese state-backed hacking group Volt Typhoon highlights the critical importance of vulnerability research and product security testing. This attack, which targeted U.S. ISPs and MSPs, underscores how undiscovered and therefore unpatched vulnerabilities can be leveraged by sophisticated threat actors to infiltrate and compromise critical infrastructure. By performing third-party vulnerability research and internal product security testing, organizations can identify and mitigate these weaknesses before they are exploited.”
Black Lotus Labs recommends those concerned about compromise of Versa Director servers within their network to upgrade to version 22.1.4 or later and keep an eye out for the following indicators of compromise (IOCs):
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
- Searching for interactions with port 4566 on Versa Director servers from non-Versa node IPs (e.g. SOHO devices).
- Searching the Versa webroot directory (recursively) for files ending with a “.png” extension that are not valid PNG files.
- Checking for newly created user accounts and other abnormal files.
- Auditing user accounts, reviewing system/application/user logs, rotating credentials, analyzing downstream customer accounts and triaging lateral movement attempts if any indications of compromise are identified, or the management ports 4566 or 4570 were exposed for any period of time.
Further recommendations can be found on the Black Lotus Labs blog.
More from TechRadar Pro
- These are the best cloud firewalls around today
- Enterprise SaaS apps are still a major security risk
- Take a look at our pick of the best antivirus for PC

Benedict has been writing about security issues for over 7 years, first focusing on geopolitics and international relations while at the University of Buckingham. During this time he studied BA Politics with Journalism, for which he received a second-class honours (upper division), then continuing his studies at a postgraduate level, achieving a distinction in MA Security, Intelligence and Diplomacy. Upon joining TechRadar Pro as a Staff Writer, Benedict transitioned his focus towards cybersecurity, exploring state-sponsored threat actors, malware, social engineering, and national security. Benedict is also an expert on B2B security products, including firewalls, antivirus, endpoint security, and password management.