TechRadar Verdict
While Cisco Secure Endpoint passed our tests with flying colors, we also know that the platform is capable of much more, especially when combined with XSecure EDR. Truly this is an incredibly flexible and powerful endpoint security platform.
Pros
- +
Easy Deployment
- +
Well laid-out UI
- +
Advanced Threat Detection
Cons
- -
Unclear pricing
Why you can trust TechRadar
For the past 40 years Cisco has been wowing consumers with its dazzling range of technology and software products.
In the company's own words, Cisco Secure Endpoint (formerly 'AMP for Endpoints') is 'built for resilience'. Cisco even makes the bold claim that the platform blocks more threats than any other security provider.
Despite Cisco's world-famous reputation, it takes more than impressive words to develop a reliable and powerful endpoint security platform. Is this really one of the best endpoint security software solutions and another jewel in Cisco's crown?
Cisco Secure Endpoint: Plans and pricing
When it comes to brass tacks, we were unable find any specific pricing on Cisco's website, which asks interested parties to contact one of their sales representatives.
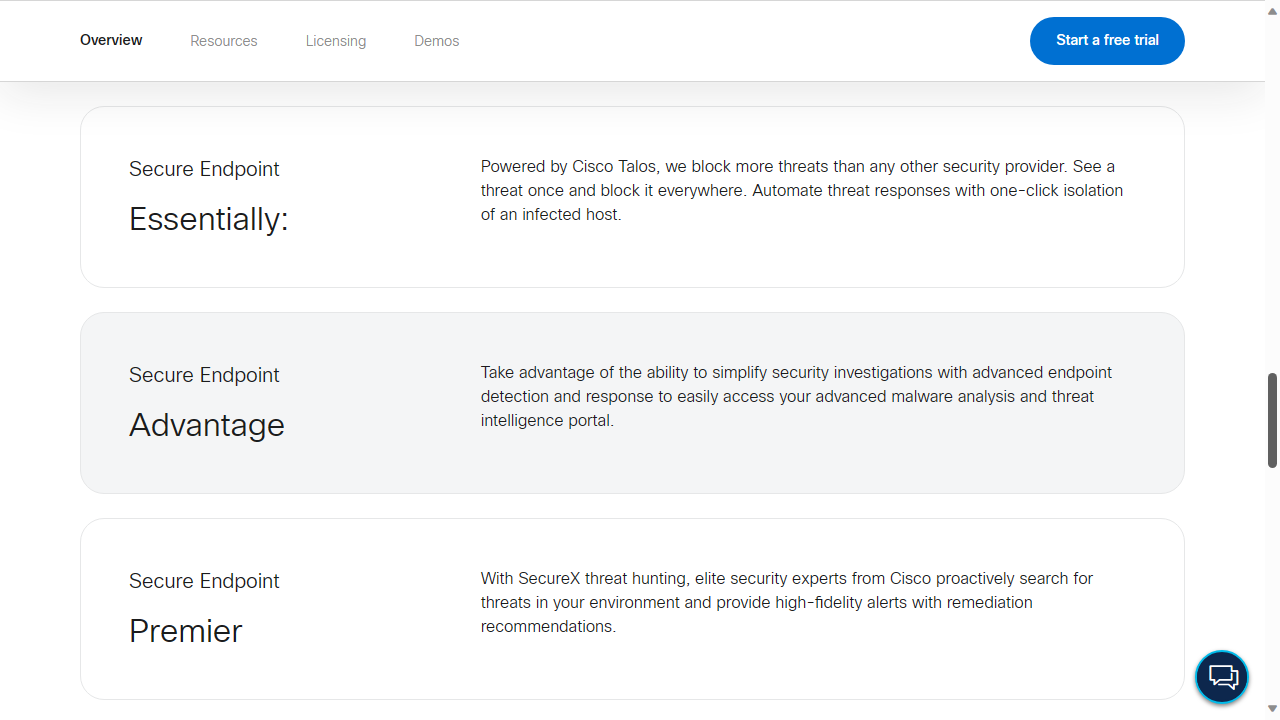
Cisco's License Comparison page, however, is much more forthcoming, detailing the three main tiers of the endpoint security platform.
The first, 'Secure Endpoint Essentials' includes access to Cisco's SecureX EDR (Endpoint Deployment and Response) platform. In brief, this allows managers to better manage and even automate responses to threats.
Subscribers also benefit from advanced endpoint protection using behavioral monitoring engines, as well as protection against fileless attacks and ransomware. Cisco also claims that all endpoints are continuously monitored for vulnerabilities.
The 'Essentials' tier also incorporates 'Dymanic Analysis' - in other words, the platform supports sandboxing of suspect files, as well as quick identification of software vulnerabilities. Managers can also isolate an endpoint with a single mouse click.
The next level tier 'Secure Endpoint Advantage' includes all of the above, plus 'Orbital Advanced Search'. Cisco claims this speeds up threat hunting, through using over 200 predefined threat hunting queries. Subscribers to the 'Advantage' tier can also access the 'Malware Analytics Cloud'. In the company's own words, this uses, 'advanced sandboxing techniques to perform in-depth dynamic file analysis and deep malware threat intelligence.'
The highest tier is Cisco Secure Endpoint Premier, which is also the basis of this review. It includes all the perks in the above two tiers, as well as 'Threat Hunting by Cisco'. Subscribers apparently benefit from 'integrated continuous hunting by elite Cisco threat hunters'.
As this is the only benefit beyond the 'Advantage' tier, we would have preferred to see a pricing table, so organizations can decide if having Cisco help in threat hunting is worth paying for.
Interested users can request a free 30-day trial of the platform without providing any payment information. The trial license supports up to 50 devices.
Cisco Secure Endpoint: Features
Unlike many endpoint security solutions we've reviewed, Cisco Secure Endpoint is truly cross-platform, supporting Windows, macOS, Linux, iOS and Android devices.
The company website includes an extensive datasheet on the main perks of the platform. Aside from being device agnostic, this includes an integrated 'file reputation' score. In simplest terms the platform maintains a database of every file it's scanned, allowing it to automatically block 'good' or 'bad' ones without intensive scanning.
Naturally this only applies to known threats, but Cisco Secure Endpoint also supports detection of polymorphic malware to stop bad actors from making small changes to viruses to avoid signature detection.
The platform also employs machine learning analysis to identify malicious files based on their behavior.
Once threats are detected, as readers will learn, the platform is also capable of performing sandboxing and/or advanced forensics.
There's no dedicated firewall for endpoints but given the platform allows managers to set any number of network and application policies, it's likely that these can provide much the same protection.
Cisco Secure Endpoint: Setup
As we mentioned, users can request a free trial of the platform. Upon registration, we were impressed to see that we had a choice of data center for trying out the cloud console: Americas, Europe and Asia Pacific. This is a first for the endpoint security platforms we've reviewed.
The website next requires users to sign in with or register a Cisco Security account. Clearly the company takes this seriously as upon providing our e-mail address, we were asked to set up multi-factor authentication. We did this by installing Duo on our iPhone 14 Pro Max but did see that other apps like Google Authenticator are supported.
On first login to the Secure Endpoint cloud console, we were immediately taken to the dashboard.
At this stage, we should stress that users have two options. If you simply want to get a feel for how the platform operates in a real environment, you can choose to 'Enable Demo Data'. This fills your console with real data from actual malware infections, so is an excellent way to gain an overview of how it all fits together.
There are also a number of 'demo computers' which provide a safe way to explore how the platform has responded to real world attacks in various ways, such as 'Command Line Capture', which shows how Cisco Secure Endpoint monitors and intercepts command line arguments as necessary.
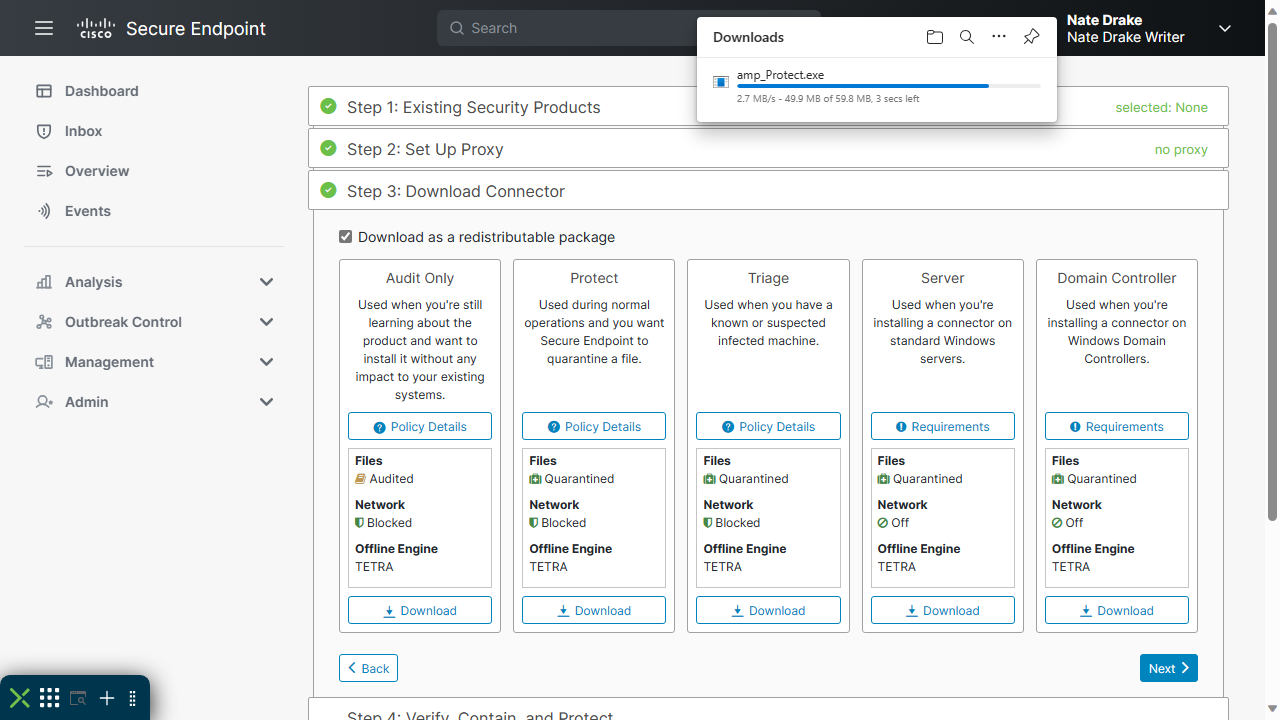
If, like the team at TechRadar, you prefer to run your own tests then you can also download a 'connector' (agent) from the main Dashboard for Windows, macOS or Linux.
If you choose this, the console displays a helpful wizard which allows you to configure the connector to work with other security software. From here, you can also specify a proxy server if necessary before downloading the agent itself.
The download and install of the 'Cisco Secure Client' took less than 60 seconds on our test machine. The agent immediately launched and prompted to run a 'Quick Scan'. When we examined the agent settings, we saw threat definitions were not current, so clicked to update them manually.
Cisco Secure Endpoint: Interface
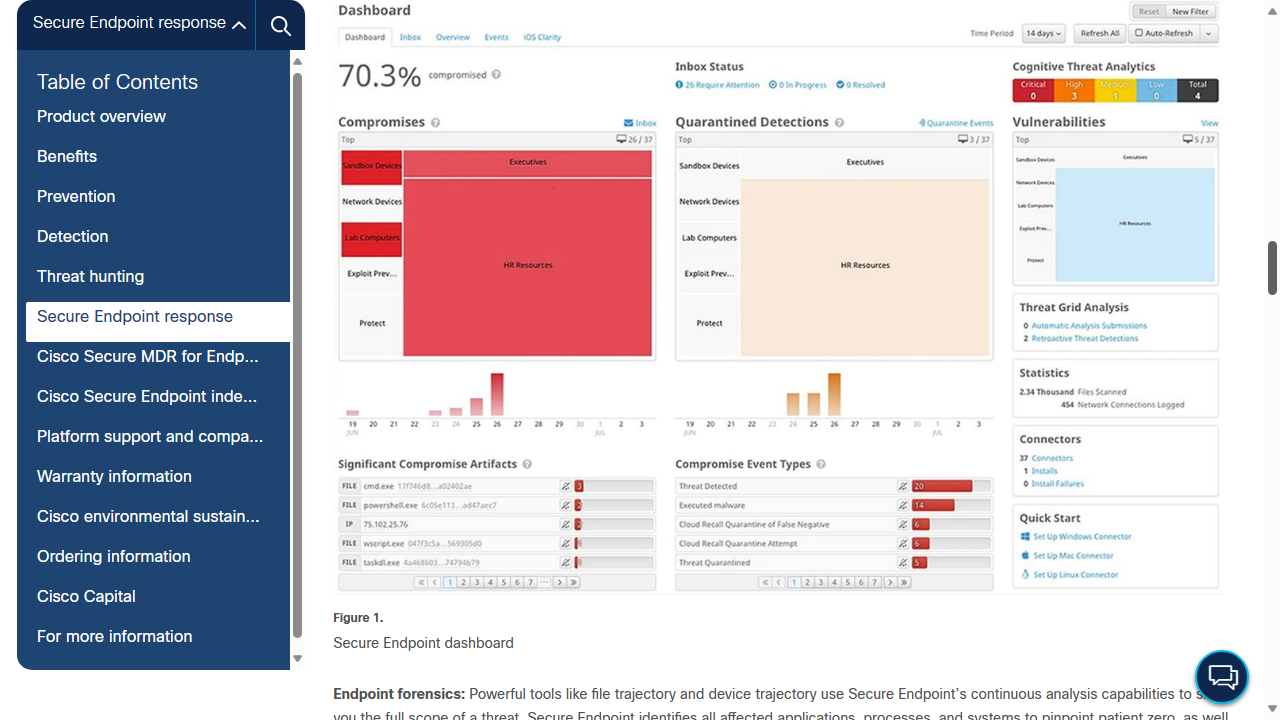
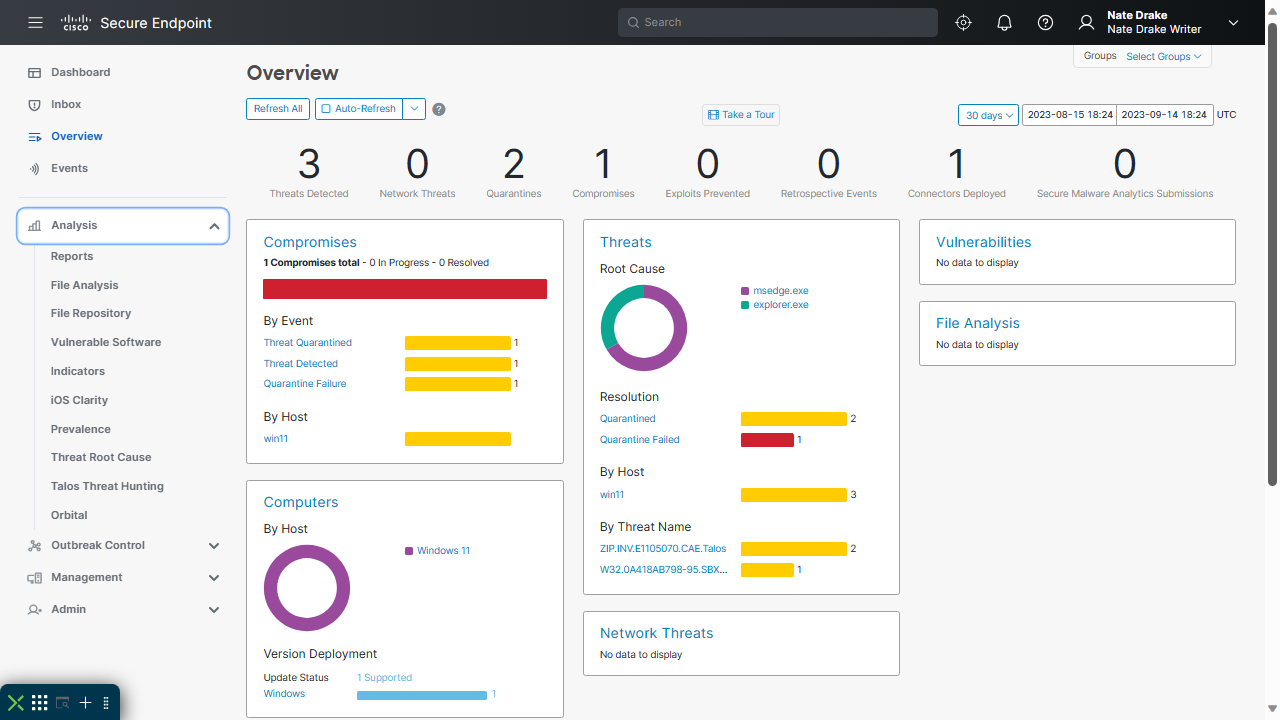
We've already touched on the main dashboard in the Cisco Secure Endpoint console, which provides an excellent overview of compromises, quarantined infections and compromised devices complete with helpful infographics.
Significant compromises are also listed below the main overview and can be clicked into, to provide more detailed information.
While we're talking overviews, there is actually a separate section of the console with that name. It also provides a broad brush summary of threats detected, quarantines, compromises etc. in number format, as well as helpful pie charts breaking down the threats by type.
It's not clear to us why there needs to be two sections listing much the same information in slightly different ways, but the interface itself is clear and colorful, so we aren't knocking off points.
The left hand pane contains other sections, with expandable menus. For instance the 'Analysis' section can be clicked to list options like 'Reports' and 'File Analysis'. This makes the console very simple to navigate and the main categories are logically arranged.
The agent (or 'Cisco Secure Client' as they call it) has a more basic interface but can display important statistics like the policies in place and detection engine, as well as update status. We were particularly impressed by the small scan window which nestles snugly into the bottom right of the desktop.
Cisco Secure Endpoint: Performance
When testing endpoint security platforms, our first test is always to try to download a fake computer virus, provided by the good people of EICAR. We fired up our test machine running Windows 11 and tried to visit the EICAR website using Microsoft Edge. Edge tried to block the download of the virus in compressed (ZIP) format but when we insisted and told it to 'keep' the file the Cisco Secure Client stepped in to block it from downloading.
We next manually copied the file (again in ZIP) format onto the test machine's hard drive, only for it to be immediately detected and quarantined by the agent software.
Our next test was to try to copy a new, real computer virus that we'd caught in the wild into the machine's 'Downloads' folder. We do this to make sure that an endpoint security platform can detect threats based on a file's behavior, not just by comparing its signature against a database of known threats. Once again, Cisco Secure Endpoint didn't let us down - the file was immediately detected.
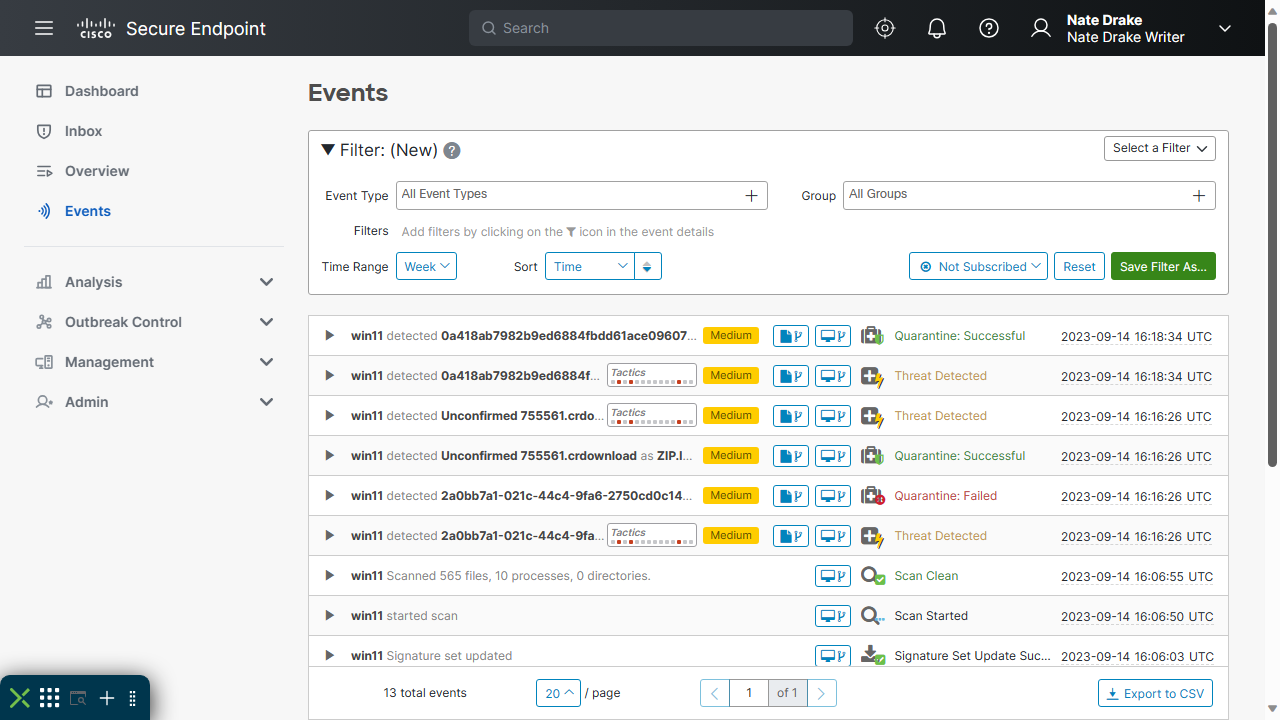
The Cisco Secure Client didn't show any kind of notification when detecting and quarantining files. However, when we logged into the 'Dashboard' or 'Overview' sections of the cloud console, we saw a detailed list of the quarantined files, with further information on the system resources they'd tried to compromise.
Cisco Secure Endpoint: Final verdict
It's not often that we cannot find any fault with a product we review. True, it was something of a nuisance setting up a new authenticator app on an iPhone just to log in but this reflects on how seriously Cisco takes security.
While the platform passed our tests with flying colors, we also know that Cisco Secure Endpoint is capable of much more, especially when combined with XSecure EDR. The sandboxing and advanced threat analysis features also mean this platform offers next level security.
Our only slight gripe (for which we're deducting half a star) is that Cisco hasn't provided a clearer pricing model for Secure Endpoint. Although this is common for endpoint security solutions, even a basic minimum price would help organizations device if this product is for them.
Nate Drake is a tech journalist specializing in cybersecurity and retro tech. He broke out from his cubicle at Apple 6 years ago and now spends his days sipping Earl Grey tea & writing elegant copy.