Enterprises are putting too much faith in Single Sign-On, which is making breaches worse
Putting too much faith in SSO could be fatal for some businesses

Single sign-on (SSO) provides a quick and easy means of access across many applications by using a single set of login credentials, and helps employees save time by removing the need to log in to each individual account and removing the need for a password manager.
However, security researchers at Doyensec, in collaboration with Teleport, have found enterprises are becoming over reliant on SSO, and are failing to put in place additional layers of security between SSO and the applications they access.
For attackers, SSO can be a gold mine for infiltrating an organization, making companies reliant on the technology an attractive target for attackers.
Convenience is putting businesses at risk
In testing performed by the researchers against Azure Active Directory, Entra ID, Google Workspace, Github and Okta, they found that attackers use a wide range of techniques to gain access to an Identity Provider (IdP), including password spraying, access token leakage, prompt-bombing, spear phishing, social engineering, employee bribing, credential stuffing and session hijacking.
“No SSO provider should be assumed to be secure,” Ev Kontsevoy, CEO at Teleport said. “With SSO, if one individual’s identity is compromised, you could be handing over the master key to the castle. SSO does offer considerable convenience, but unauthorized access to one individual’s credentials exposes every platform and service for which that individual has privileges. Without additional defense in place, SSO by itself does not thwart identity-based attacks.”
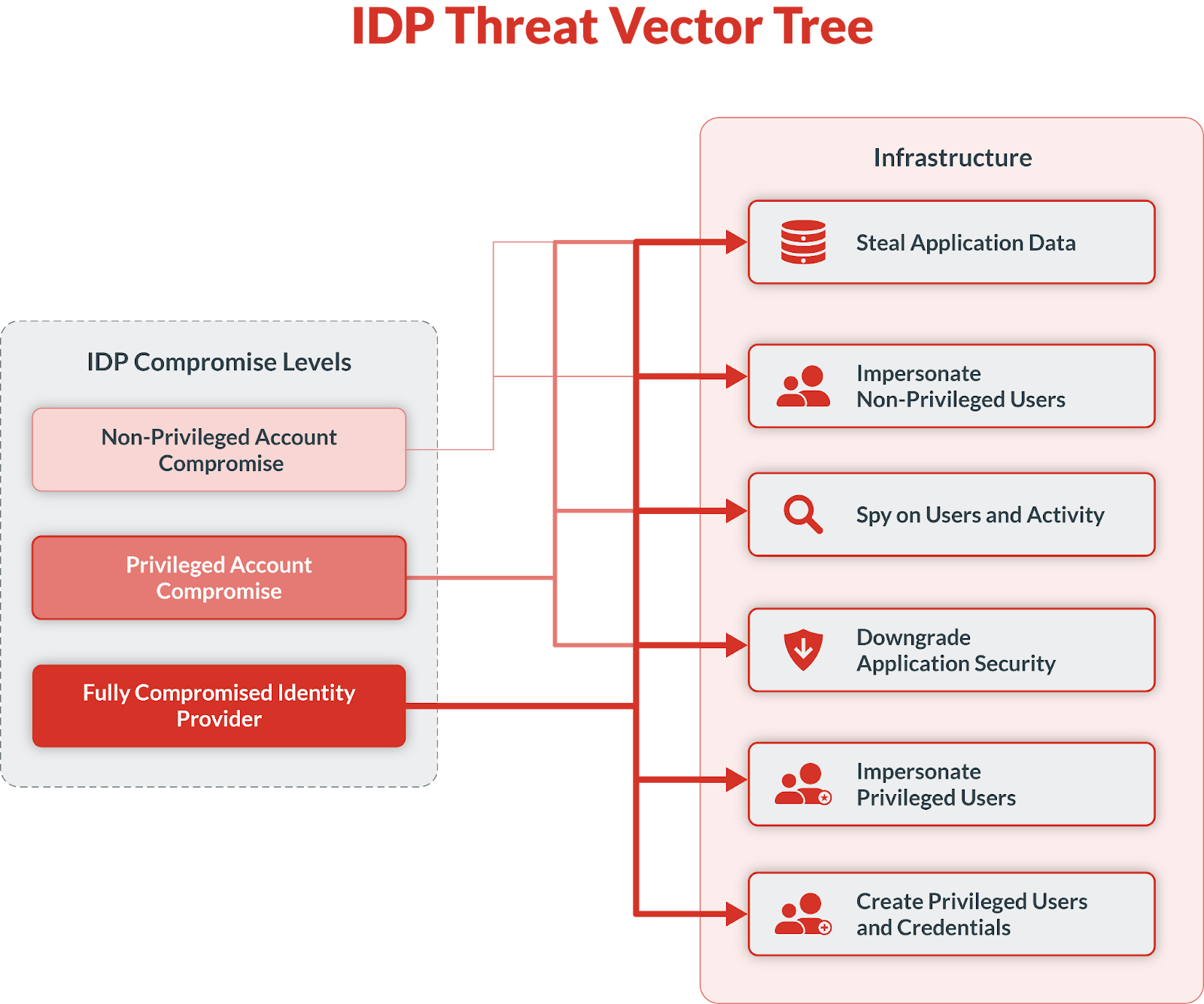
A successful attack against an IdP provider, especially if it goes undetected, can result in user impersonation, theft of sensitive company and user data, and the creation of new credentials for malicious use.
In order to mitigate the threats presented by compromised IdPs, the researchers recommend operating on a defense-in-depth model by layering phishing-resistant MFA-based features, access requests and dual authorization to enforce principles of least privilege, and putting mandatory MFA enrollment in place to make it more difficult for attackers to breach systems and move laterally.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
“What’s clear is that vulnerabilities in SSO and IdP platforms can have catastrophic impacts,” Luca Carettoni, CEO at Doyensec said. “Applying a defense-in-depth security layer on top of service providers can significantly limit the outcomes of a successful SSO provider compromise and reduce the impact against the protected infrastructure. The configuration of the defense-in-depth layer is extremely important to a company’s overall defense posture.”
More from TechRadar Pro
- These are the best endpoint protection services
- Security bug could have allowed anyone to spoof Microsoft employee emails
- Take a look at the best antivirus

Benedict has been writing about security issues for over 7 years, first focusing on geopolitics and international relations while at the University of Buckingham. During this time he studied BA Politics with Journalism, for which he received a second-class honours (upper division), then continuing his studies at a postgraduate level, achieving a distinction in MA Security, Intelligence and Diplomacy. Upon joining TechRadar Pro as a Staff Writer, Benedict transitioned his focus towards cybersecurity, exploring state-sponsored threat actors, malware, social engineering, and national security. Benedict is also an expert on B2B security products, including firewalls, antivirus, endpoint security, and password management.