QR codes are being hijacked to bypass MFA protections
Quishing attacks leverage QR codes to target employees

By now, most of us have become accustomed to seeing QR codes everywhere, from cafes and pubs, to businesses and public services. But how often do you check the URL it is directing you to?
This is just one of the weaknesses of QR codes - the implicit trust that the code will take you where you want to go.
New Sophos research has explored how an attack plays out after one of its own employees was targeted in a ‘quishing’ attack which utilized malicious QR codes hidden in seemingly legitimate internal emails.
Squishing quishing isn’t easy
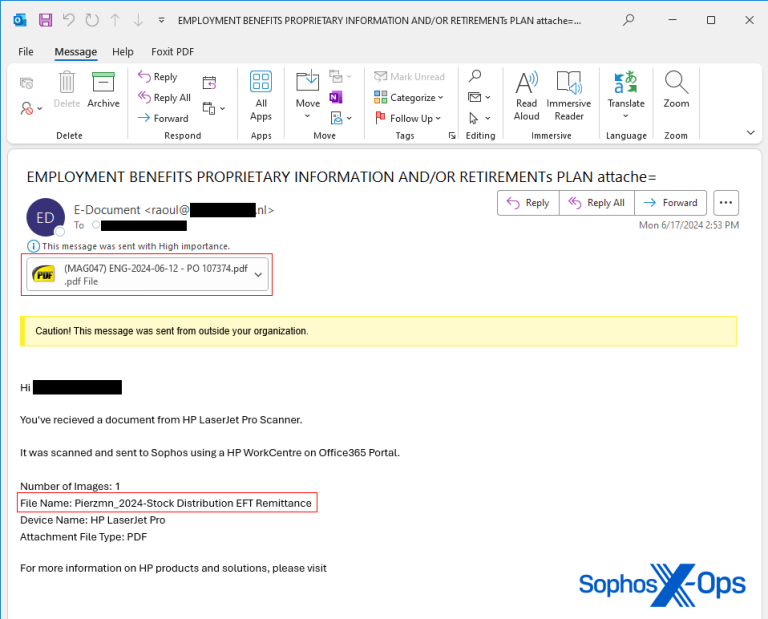
In June 2024, several Sophos employees received a fairly mundane email from legitimate external email accounts, with subject lines written to appear as though the email was sent from an office printer/scanner with an employee benefits PDF document attached.
The PDF was fairly plain, containing the Sophos logo at the top, followed by a QR code and a message at the bottom stating that the QR code contained a secured link to DocuSign which required the employee’s digital signature, and that the file would expire in 24 hours.
When scanned, the QR code directed the employee to a Microsoft 365 sign-in box, where the employee duly signed in and completed a multi-factor authentication check. In almost real time an attacker used the credentials and a stolen MFA token to attempt to access an internal application. Luckily, Sophos’ internal network settings prevented access and the account was secured.
So, how could a quishing attack such as this be spotted and stopped? Well, if you pay particular attention to every detail of an incoming email, you may just stand a chance. For one, Sophos points out, the file name contained within the body of the email did not match that of the attached PDF. Moreover, the subject line read “Remittance Arrived” - something that a file received from a legitimate officer scanner would not say.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
The subject line also ended with “retirements plan attache=”. Whether this was a mistake on behalf of the attacker or a clever use of the ‘=’ sign to make the header appear cut off is not known.
The false sense of urgency proposed by the 24-hour expiry timeline should have also been a giveaway, as well as the URL displayed when the QR code was scanned. However, as anyone who has scanned a QR code before will know, sometimes the full URL isn’t shown or disappears before it can be fully read and checked for clues such as random letters or a homoglyph domain.
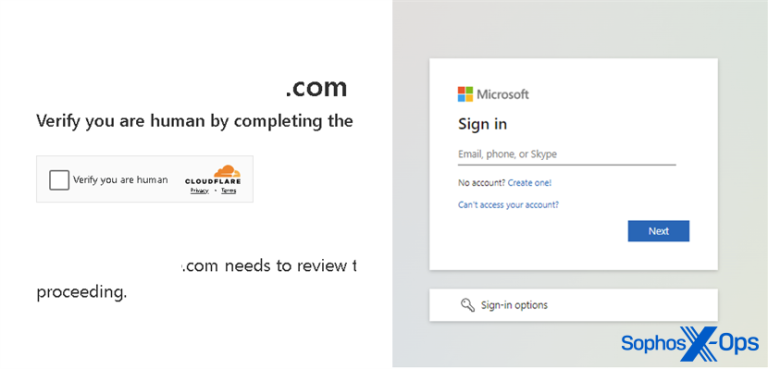
As for the stolen MFA token, the Microsoft 365 sign in page was actually a spoofed dialogue box controlled by the attacker that was not picked up due to a lack of URL filtering software on the victim’s phone.
Quishing, Sophos points out, is fast becoming a growing threat to organizations with phishing-as-a-service (PhaaS) brokers such as the ONNX Store increasingly offering QR code-based attacks in their offerings.
As QR codes are typically image based attachments that can be placed within PDF documents, they can easily slip through email filters and the typical endpoint security protections employed by many businesses, as all of the URL processing happens on the victim’s mobile device that may not be subject to the same level of protection.
Andrew Brandt, principal threat researcher at Sophos said, “While there was some fear surrounding the rise of QR codes when they first became popular during COVID, the risk for most people was actually quite small. However, now we’re seeing attackers leverage these QR codes for highly targeted phishing attacks—and they’re effective.”
“QR codes are incredibly flexible, and with quishing kits, attackers can essentially create a series of targeted quishing emails en masse, customizing them for employees of different companies. And, unfortunately, if attackers manage to steal both login credentials and MFA authentication tokens for a company employee, in many many cases, they have gained the ability to infiltrated highly privileged assets,” Brandt said.
For recommendations on how best to protect your organization from quishing, and the key signs of a quishing email, take a look at Sophos’ suggestions here.
More from TechRadar Pro
- These are the best business VPNs
- Proton unveils new business VPN features
- Take a look at our guide to the best business firewalls

Benedict has been with TechRadar Pro for over two years, and has specialized in writing about cybersecurity, threat intelligence, and B2B security solutions. His coverage explores the critical areas of national security, including state-sponsored threat actors, APT groups, critical infrastructure, and social engineering.
Benedict holds an MA (Distinction) in Security, Intelligence, and Diplomacy from the Centre for Security and Intelligence Studies at the University of Buckingham, providing him with a strong academic foundation for his reporting on geopolitics, threat intelligence, and cyber-warfare.
Prior to his postgraduate studies, Benedict earned a BA in Politics with Journalism, providing him with the skills to translate complex political and security issues into comprehensible copy.