Ransomware gang deals double damage to victim by complaining to the SEC about their own attack
A ransomware gang took it upon itself to enforce the latest rules from the SEC

From December 15, publicly traded companies in the US will be required by the Securities and Exchange Commission (SEC) to disclose cybersecurity breaches within four working days of the incident.
The ALPHV/BlackCat ransom group has taken it upon themselves to enforce this law early, by submitting a complaint to the SEC that their breach of software company MeridianLink had not been publicly disclosed.
In the group’s report to the SEC, they stated that MeridianLink had suffered a “significant breach” that it did not disclose as required by the new rules.
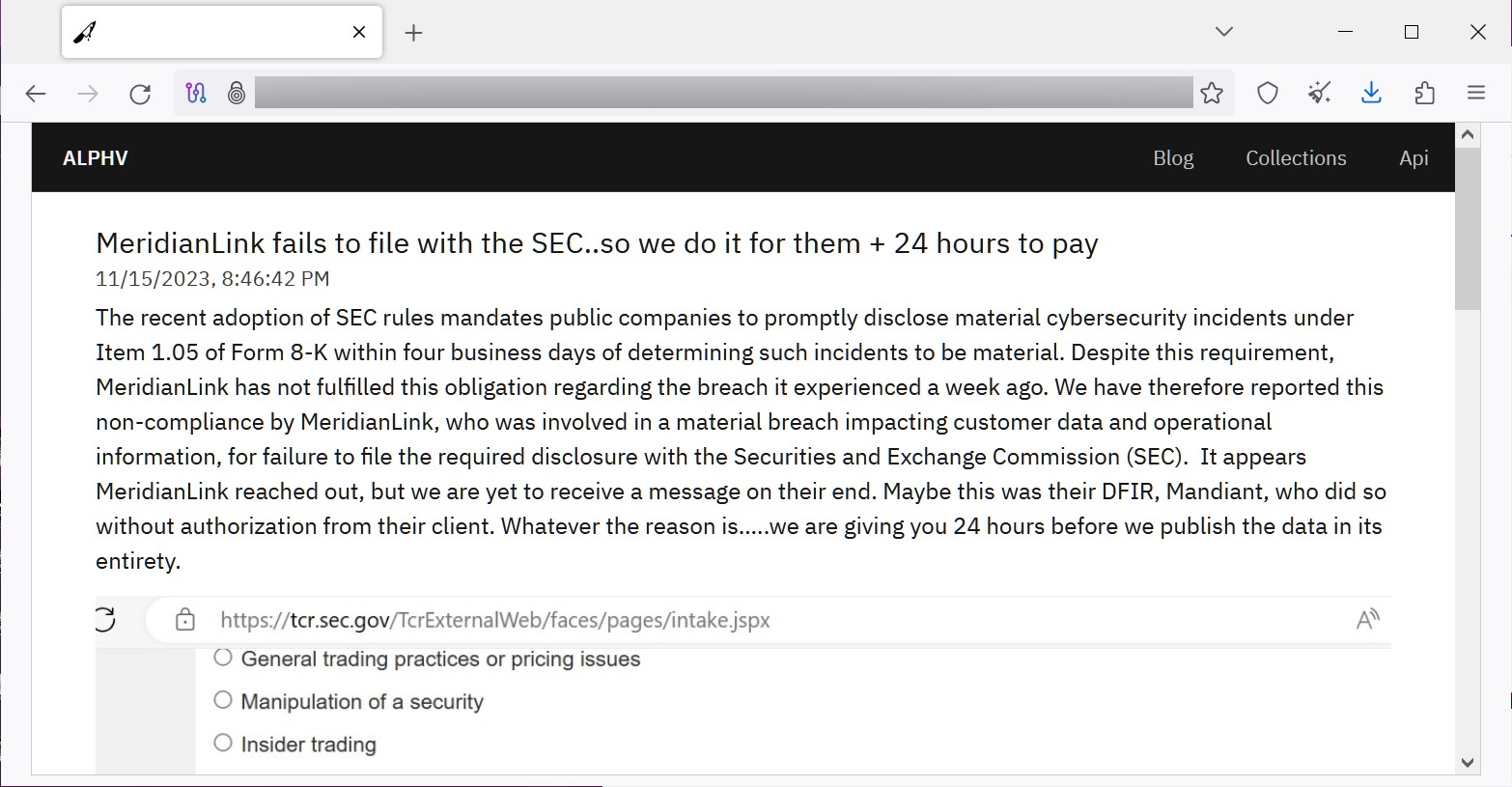
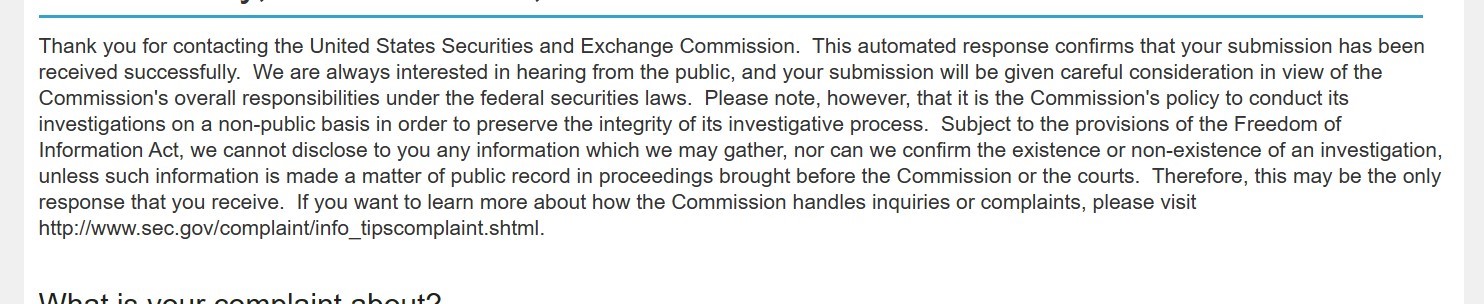
Snitches get… an automated response that their complaint was received
ALPHV/BlackCat listed MeridianLink as a victim of data theft yesterday, claiming that the alleged breach occurred on November 7. They claim to have stolen company data without encrypting MeridianLink’s systems.
The group released images of both their complaint to the SEC, and the automated response they received from the regulatory body in acknowledgement of their complaint.
In response to the attack, MeridianLink released a statement saying, “Based on our investigation to date, we have identified no evidence of unauthorized access to our production platforms, and the incident has caused minimal business interruption.”
While it is traditional for ransomware groups to add an extra layer of extortion by threatening to let their victims’ customers know their data was stolen, this is the first incident of its kind where an attacker has complained to an authoritative body about their own attack.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
Dr. Illia Kolochenko, Chief Architect at ImmniWeb and Adjunct Professor of Cybersecurity & Cyber Law at Capitol Technology University commented that, “Misuse of the new SEC rules to make additional pressure on publicly traded companies was foreseeable.
“Moreover, ransomware actors will likely start filing complaints with other US and EU regulatory agencies when the victims fail to disclose a breach within the timeframe provided by law. Having said that, not all security incidents are data breaches, and not all data breaches are reportable data breaches.
“Therefore, regulatory agencies and authorities should carefully scrutinize such reports and probably even establish a new rule to ignore reports uncorroborated with trustworthy evidence, otherwise, exaggerated or even completely false complaints will flood their systems with noise and paralyze their work.
“Victims of data breaches should urgently consider revising their digital forensics and incident response (DFIR) strategies by inviting corporate jurists and external law firms specialized in cybersecurity to participate in the creation, testing, management and continuous improvement of their DFIR plan.
“Many large organizations still have only technical people managing the entire process, eventually triggering such undesirable events as criminal prosecution of CISOs and a broad spectrum of legal ramifications for the entire organization. Transparent, well-thought-out and timely response to a data breach can save millions.”
Via BleepingComputer
More from TechRadar Pro
- Protect yourself from ransomware with our guide to the best ransomware protection
- Samsung warns some customers their data may have been stolen by hackers
- Looking to upgrade your online protection? Take a look at our list of the best firewalls

Benedict has been writing about security issues for over 7 years, first focusing on geopolitics and international relations while at the University of Buckingham. During this time he studied BA Politics with Journalism, for which he received a second-class honours (upper division), then continuing his studies at a postgraduate level, achieving a distinction in MA Security, Intelligence and Diplomacy. Upon joining TechRadar Pro as a Staff Writer, Benedict transitioned his focus towards cybersecurity, exploring state-sponsored threat actors, malware, social engineering, and national security. Benedict is also an expert on B2B security products, including firewalls, antivirus, endpoint security, and password management.