Microsoft says that it is making progress in its Secure Future Initiative — but there is still work to do
Microsoft reveals latest update to Secure Future Initiative program
- Microsoft has released the November update for its Secure Future Initiative
- New security oriented solutions have been introduced across environments
- Microsoft also announces a new Windows Resiliency Initiative
Microsoft has released the second update to its Secure Future Initiative - a program introduced to address critical security challenges and vulnerabilities experienced by the company which led to state-sponsored threat actors compromising US government data.
Microsoft has built upon progress made in its September 2024 update, where it introduced a number of security-oriented changes, including tying security to performance evaluations and introducing the Security Skilling Academy.
The company says further progress has now been made across Microsoft’s six engineering pillars to ensure “security above all else” to help protect users, businesses and contractors.
More progress across the pillars
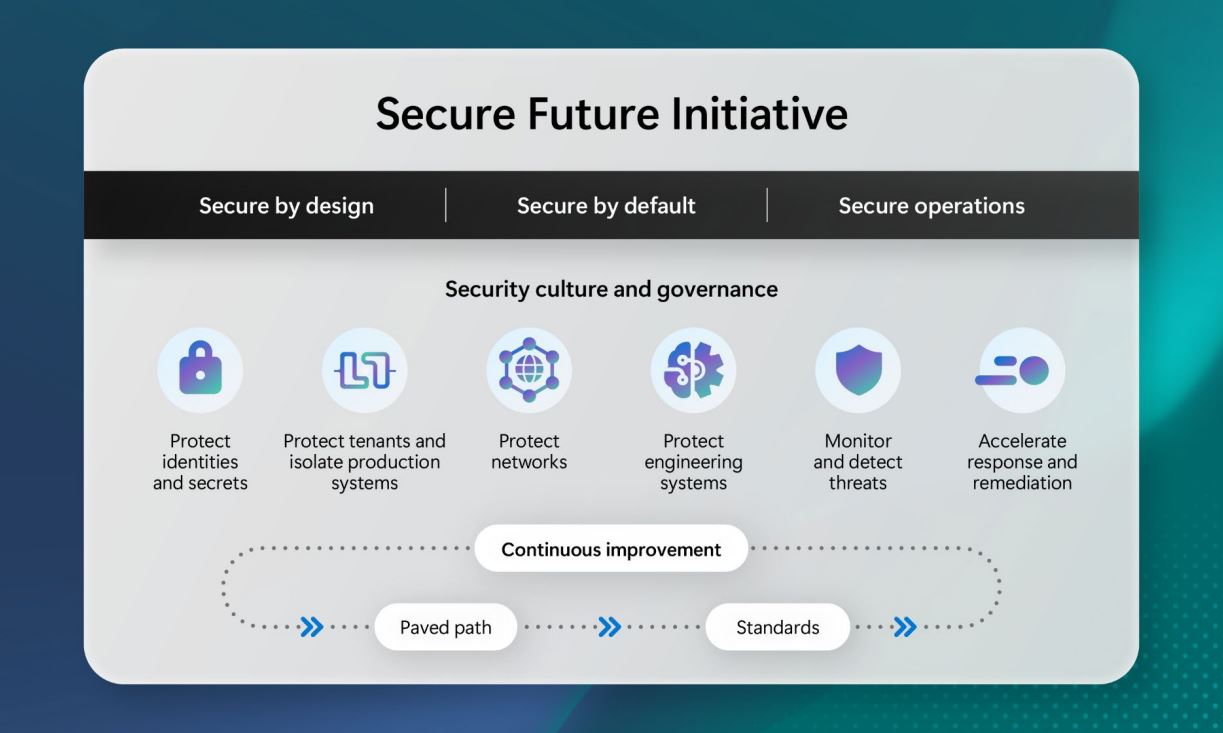
In the September 2024 update, Microsoft advanced the security of its first pillar, ‘protect identities and secrets’, by boosting the protection of access token signing keys on Microsoft Entra ID, Microsoft Account, and Microsoft Active Directory Federation Services. Microsoft also introduced phishing resistant credentials across the productivity environment.
A number of major changes have also now been revealed, with the Microsoft Azure Portal, Microsoft Entra admin center, Intune admin center, and Microsoft 365 admin center all getting multifactor authentication enabled by default for new tenants.
MFA is also being enforced across Microsoft’s productivity environments to reduce the risk of phishing and credential theft.
For pillar two, ‘protect tenants and isolate production systems’, the September update saw Microsoft introduce lifetime management and secure defaults for Microsoft Entra ID accounts, alongside removing management from legacy platforms such as the Azure Service Management API. These updates saw 5.75 million tenants eliminated and 440,000 resources removed.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
The company says its progress since September has seen Microsoft introduce the Entra Conditional Access template which requires users to meet a certain level of device compliance. Moreover, Microsoft says it has rolled out almost 100,000 ‘locked-down’ devices, with 28,000 high-risk users moved to secure virtual machines.

September’s update to the third pillar, ‘protect networks’, saw Microsoft configure over 99% of its network devices to a baseline standard, with physical devices continually monitored for vulnerabilities and security hygiene. All Microsoft services had service tags added to help identity owners of traffic in the Microsoft network, and centrally configured network policies were introduced.
Since then, Microsoft has made Azure Virtual Network Encryption available, with Domain Name System Security Extensions support in public preview. Microsoft also refined its ‘over 99%’ number to 99.3%, and highlighted the implementation of mandatory access control lists to isolate physical assets and prevent lateral movement in the event of network compromise.
September saw Microsoft increase security for pillar four, ‘protect engineering systems’, by tracking software assets in production environments, applied new policies to harden code repositories, as well as a number of changes to pipelines, testing environments and derived credentials.
Microsoft has now introduced GitHub Advanced Security to allow customers to scan Azure DevOps Git repositories for secret exposures, as well as blocking new secrets from being exposed at push. More work is to be done here, however, as Microsoft is still working towards removing secrets from code, but the report highlights the introduction of authentication protocols to eliminate exposed credentials and secrets.
For ‘monitor and detect threats’, Microsoft's fifth pillar, September saw Redmond introduce service-level security audit logging in standard libraries, as well as a centrally enforced security log retention period. Microsoft also said it was working to add new methods for detecting known threat actors’ tactics, techniques and procedures to red teaming tools, and expanded the availability of Microsoft 365 audit logs.
November’s update shows that Microsoft has also introduced consistent audit logging across all services with a retention period of two years, with logging also expanded to Microsoft’s cloud services.
Finally, September's update to the sixth pillar, ‘accelerate response and remediation’ saw the reduction of Microsoft’s time to mitigate critical cloud vulnerabilities, the introduction of cloud common vulnerability and exposures (CVE) publishing, and the launch of the Customer Security Management Office that provides updates and advisories on unfolding security incidents.
Now, Microsoft has released figures showing that they successfully addressed 90% of high severity cloud vulnerabilities within their reduced time to mitigate and published 800 cloud CVEs. Microsoft is now looking to issue security reports on nation-state actors direct to customers through Azure, Microsoft 365, and Dynamics 365.
Microsoft has also announced it is introducing the Windows Resiliency Initiative which is aimed at increasing the security of business devices, addressing the lessons learnt from the Crowdstrike outage, and increasing the usage of Windows 11.
The new initiative is aimed at reducing the number of admin privileges applications require in order to run, introducing better security controls for running apps and drivers, and boosting phishing resistance.
You might also like
- Take a look at the best firewalls around today
- These are the best antivirus services around
- Microsoft accused of creating a monopoly on US government systems through free upgrades

Benedict has been writing about security issues for over 7 years, first focusing on geopolitics and international relations while at the University of Buckingham. During this time he studied BA Politics with Journalism, for which he received a second-class honours (upper division), then continuing his studies at a postgraduate level, achieving a distinction in MA Security, Intelligence and Diplomacy. Upon joining TechRadar Pro as a Staff Writer, Benedict transitioned his focus towards cybersecurity, exploring state-sponsored threat actors, malware, social engineering, and national security. Benedict is also an expert on B2B security products, including firewalls, antivirus, endpoint security, and password management.