North Korean hackers hijack Google's Find Hub to find and wipe target devices
Google Find Hub hacked to become an unwitting ally
- KONNI hackers use KakaoTalk to deliver malware and harvest account credentials from victims
- Attackers exploit Google Find Hub to remotely wipe Android devices and evade detection
- Compromised PCs spread malware to contacts while mobile devices are repeatedly factory reset
North Korean threat actors with ties to the government were seen resetting target Android devices to factory settings to cover their tracks.
Researchers from Genians said they saw these attacks in the wild, targeting primarily individuals in South Korea, carried out by a group called KONNI (named after a remote access tool it is using)
The researchers say KONNI has “overlapping targets and infrastructure” with both Kimsuky, and APT37, known North Korean state-sponsored actors.
Official IdentityForce® | Identity Theft Protection - save up to 68% annually
Many people don’t know how to protect their ID. Don’t be one of them. Get your ID Action Plan here. Get a personalized step-by-step Action Plan & ID Safety Score based on YOUR dark web hits.
Wiping the device
The attack starts on KakaoTalk messenger, one of the most popular instant chat messaging platforms in the country, where KONNI’s agents impersonate trusted entities like the National Tax Service, or the police.
During the conversation, they send a digitally signed MSI file (or a ZIP archive with it) which, if the victim runs it, launches a script that ultimately downloads different malware modules, including RemcosRAT, QuasarRAT, and RftRAT.
These RATs harvest all sorts of information from the compromised device, including Google and Naver account credentials which are then used to log into the victim’s Google account.
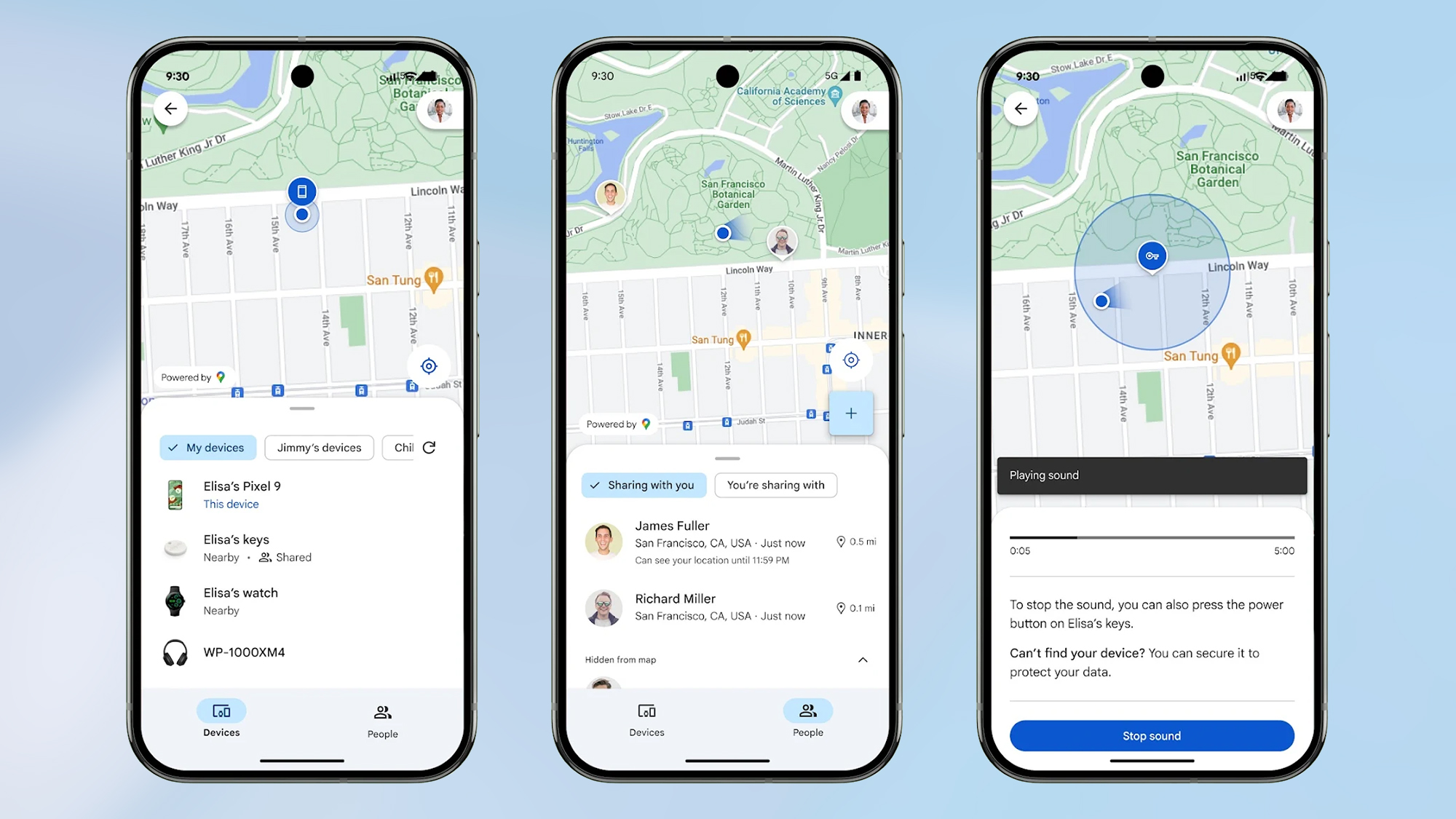
From there, they access Google Find Hub, a built-in tool that lets users remotely locate, lock, or wipe their devices, and use it not only to view all other registered Android devices, but also to track the victim’s location.
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
When they see the victim out and about, and unable to quickly address an attack, they send remote factor reset commands to all devices, erasing data, disabling alerts, and disconnecting the victim from the KakaoTalk PC sessions. The wipe is done three times.
With the mobile device wiped but the KakaoTalk PC session still active, the hackers use the compromised computer to send malicious files to the victim’s contacts, spreading the infections further.
The motive behind the attack is unknown at the time, but state-sponsored threat actors are usually engaged in cyber-espionage and disruption.
Via BleepingComputer

➡️ Read our full guide to the best antivirus
1. Best overall:
Bitdefender Total Security
2. Best for families:
Norton 360 with LifeLock
3. Best for mobile:
McAfee Mobile Security
Follow TechRadar on Google News and add us as a preferred source to get our expert news, reviews, and opinion in your feeds. Make sure to click the Follow button!
And of course you can also follow TechRadar on TikTok for news, reviews, unboxings in video form, and get regular updates from us on WhatsApp too.
Sead is a seasoned freelance journalist based in Sarajevo, Bosnia and Herzegovina. He writes about IT (cloud, IoT, 5G, VPN) and cybersecurity (ransomware, data breaches, laws and regulations). In his career, spanning more than a decade, he’s written for numerous media outlets, including Al Jazeera Balkans. He’s also held several modules on content writing for Represent Communications.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
