The best antivirus software in 2025 for PC: ranked and reviewed
I've compared the best antivirus software solutions on the market

Welcome to my guide to the best antivirus software. Antivirus is used to protect digital devices from harmful files that can take over your device, steal your personal data, or encrypt your files until you pay a fee to get them back.
Bitdefender is the best antivirus software for most people, and has unrivaled scores in both industry trials and our own bespoke testing, which you can read about further down. Norton and Avast also provide excellent antivirus protection.
My team of experts at TechRadar Pro have over 30 years of experience testing and reviewing antivirus services, so you can rely on us to give you an expert recommendation.
I have also ranked and reviewed the best free antivirus and the best Mac antivirus, but here are my recommendations for the best antivirus:
The three best antivirus at a glance
Here are the three best antivirus solutions available today:
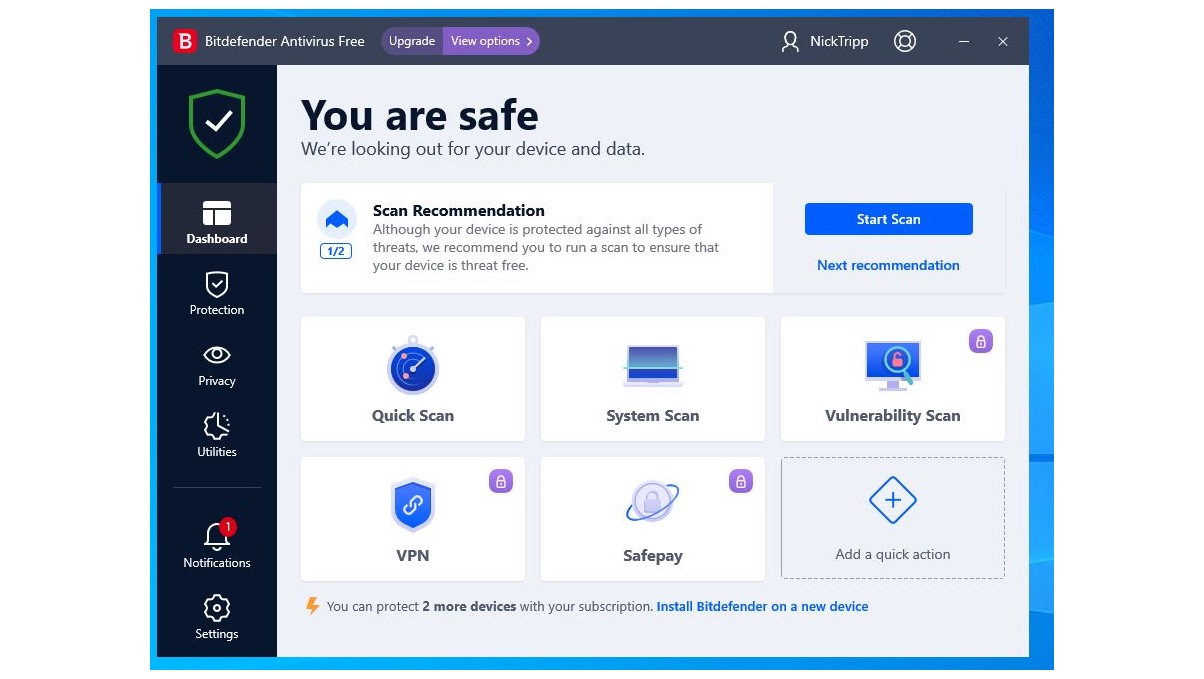
1. Bitdefender: today's best antivirus software
True to its name, Bitdefender puts a stop to both new and unknown malware, and acts so quickly that you won't even realize you're in danger. Bitdefender doesn't take up a huge amount of resources and packs a lot of value into reasonably priced plans.
The solution also comes with a VPN, safe banking tools, and a firewall. You can try Bitdefender Total Security free for 30 days before committing to a subscription.
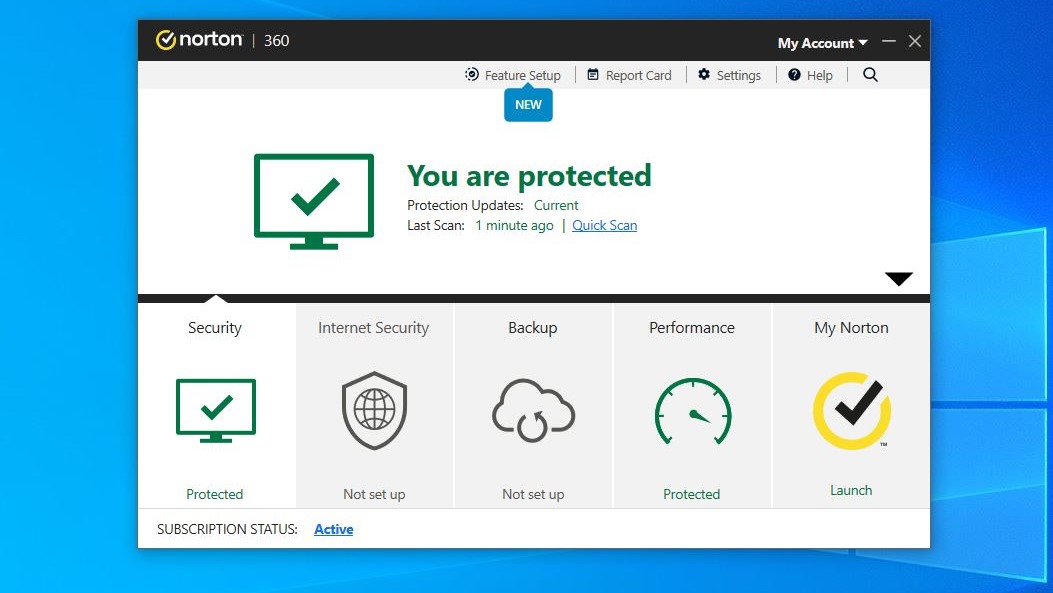
2. Norton: malware and identity protection
Access to LifeLock identity protection services makes a Norton subscription worth every penny—but you'll also get other impressive benefits. These include strong protection against malware, browser security and parental controls, and even a password manager.
Norton has a 60-day money-back guarantee and a Virus Protection Promise if you sign up for its auto-renewal program.
3. Avast One: the gamer's ally
Boot up a game and Avast will automatically put itself in gamer mode. This will keep you protected and ensure that you're not interrupted by popups, reminders, or other frustrating distractions.
Other perks include VPN access and a handy system scanner. Plus, a stripped-down free version is available to try, so you can get a feel for the Avast toolkit.

Benedict has spent over 7 years writing about security issues, covering everything from major data breaches and cyber attacks, to the malware and credentials thefts that threaten livelihoods and personal security. He has a passion for security products that keep people safe, and the knowledge to help them make the right decision.
The best antivirus services in 2025:
Why you can trust TechRadar
The best antivirus overall
Specifications
Reasons to buy
Reasons to avoid
✔️ You want a full antivirus toolkit: Bitdefender's features hunt down malware and protect against ransomware without disrupting your browsing.
✔️ You don't want to sacrifice too many resources: Bitdefender doesn't take up a lot of storage space, so you don't need to worry about sacrificing system speed for security.
✔️ You're new to antivirus solutions: Bitdefender is easy to install and use. Its real-time protection is even enabled from the get-go.
❌ You want quick scans: initial and deep scans take almost an hour to complete (five times longer than other antivirus on average). Thankfully, you'll still be able to work, play, and browse when they're running.
❌ You need identity theft monitoring: Bitdefender has some monitoring tools to track online identities, but for real round-the-clock protection from identity theft, you'll want to check out Norton.
❌ You're already infected with malware: Bitdefender isn't as effective when it comes to removing threats already attacking your system. For current infections, try Malwarebytes.
🔒 Bitdefender is the best antivirus package on the market—and has been for a few years. It combines watertight security tools with straightforward apps and, best of all, offers fantastic value for money.
Our Bitdefender review explores all of its subscription tiers, the available tools, and digs into whether a cheaper plan is just as good as the all-in-one suite.
Bitdefender consistently impresses with its ability to identify threats and stop them in their tracks. Malware files are pinpointed even before they begin downloading, web trackers are likewise rooted out and blocked, and if you try to access a site with known threats you'll receive a warning that's hard to miss (or ignore.)
AV-Comparatives, a third-party test lab, reported positive results when it put Bitdefender to the test. The solution blocked 99.4% of threats (coming in second only to the likes of Norton and McAfee) and didn't have a huge impact on the speed of computer processes. When I put Bitdefender under the microscope myself, I saw it block real-world ransomware before it could wreak havoc. However, I did notice that the Ransomware Remediation feature isn't enabled by default—so you'll need to dive into the settings to ensure that your files remain secure.
▶ Try Bitdefender Total Security free for 30 days
In 2024, Bitdefender released a decryptor for the MortalKombat ransomware—free of charge, providing the company's commitment to countering cyberattacks. Victims across the US were targeted at random by ransomware, which spread through bogus emails containing a .ZIP attachment and a BAT loader script. To tackle this threat, the decryptor backs up affected files before attempting decryption, just in case, and can be executed via the command line.
There are three Bitdefender plans on offer, and they all come with useful security tools. If you really want to get your money's worth, however, you'll want to opt for the Total Security package, which includes safe banking tools, a (admittedly limited) VPN, social media protection, file shredder, parental controls, and much more. There's even a handy vulnerability scanner that'll find weak spots in your network and offer suggestions on how to resolve them. You'll be able to use Bitdefender on any device, too, thanks to user-friendly apps for Windows, Mac, Android, and iOS, and take advantage of multiple licenses (up to 10) to protect the entire family.
Bitdefender gets straight to work with a full scan when you start using it, and combs through your system in its entirety to look for threats and intruders. This is par for the course, although Bitdefender took almost a full hour to complete a scan of 50 Gb executable files. It's possible to configure scans, customize them, and set them to run on a schedule or on-demand, and Quick Scans can even be run once a day, or weekly, and dig into individual files.
I found Bitdefender incredibly easy to use—so even if you're new to the world of antivirus, you'll have no trouble navigating sleek and well-designed apps. You can even customize the dashboard by adding or removing default features. So, if you don't make use of the VPN, you can substitute it in a few clicks for the password manager or scan manager. Most of the features you'll need are already enabled by default, too, which means you won't have to spend ages configuring each and every setting. However, if you do need help with particular tools, you can count on Bitdefender's in-program tutorials to help you make the most of these privacy-enhancing functionalities.
Bitdefender's Total Security plan is available from $39.99 for a single year—although the price does jump to $95 after this introductory period. However, you can take advantage of a 30-day money-back guarantee to put the solution through its paces, run your own tests, and see whether its suite of tools is worth the investment.
Protect your devices with our Bitdefender coupons. Get top-notch cybersecurity at a discounted price and keep your online activities safe.
Features | Notes | Rating |
|---|---|---|
Protection | Consistently earns high marks from third-party security test labs | ⭐⭐⭐⭐⭐ |
Performance | Won't impact your speed or create noticeable slowdown | ⭐⭐⭐⭐⭐ |
Ease of use | Most key features are automatically enabled and apps are intuitive | ⭐⭐⭐⭐ |
Advanced tools | Safe banking features, webcam monitoring, and parental controls to name a few | ⭐⭐⭐⭐⭐ |
Customer support | Bitdefender lacks live support but has a library of video tutorials, how-to articles, and a helpful community | ⭐⭐⭐ |
Value | There are cheaper solutions out there, but you're getting a lot of functionality and value with Bitdefender | ⭐⭐⭐⭐ |
Best antivirus with ID protection
Specifications
Reasons to buy
Reasons to avoid
✔️ You need identity theft protection: the LifeLock feature monitors the dark web and stolen data banks, and will let you know if it finds any of your details in the wild.
✔️ You want multi-device protection: keep your mobile phones and tablets secure with sleek apps that include Wi-Fi security.
✔️ You need to secure your browser: Norton hides your VPN, and your browsing history, so you can surf the web without leaving an identifiable trail.
❌ You're on a budget: Norton is hardly a budget option—even with its new-user deals—and only gets pricer on renewal.
❌ You need backup: the cheapest plans come with 2 Gb of space, which isn't all that generous.
❌ You want a stellar VPN: while solid, Norton Secure VPN doesn't top our best VPN list.
🔒 Norton excels when it comes to basic malware protection and offers some awesome advanced tools—like its LifeLock identity theft monitoring service. These extras make it an expensive option, however.
Our Norton review takes an in-depth look at its LifeLock service, VPN, and antivirus suite.
Norton is tough on threats and has earned excellent scores in several third-party protection tests, including our own. Apps are available for just about all operating systems, too, so you can secure every internet-enabled gadget in the home with a single subscription. Regardless of the plan you choose, you'll have access to a long list of features designed to protect against malware, cybercriminals, and malicious URLs.
I was also impressed with Norton’s scan speed—it took 29 minutes for the solution to complete its initial scan of 50 Gb of files. It’s not the quickest antivirus I've seen, but still beats the likes of Bitdefender and Avast.
Norton shines when it comes to identifying threats, however. My tests, and those conducted by AV-Compatatives, found that it blocked all attacks before the malware could be downloaded. If you have the technical know-how, you can even use the Insight tool to check out reports on individual files to see if there are unidentified threats lurking on your system—and this is particularly handy when dealing with new strains of malware that Norton hasn't encountered.
▶ Try Norton 360 with LifeLock and get a 60-day money-back guarantee
Norton is also incredibly good at blocking dangerous URLs and preventing you from landing on a page that's determined to ruin your day. You'll see a warning message with additional information about the malware and a heads-up about other sites that contain the same threat. The Safe Web browser extension gives you even more peace of mind by adding site ratings to search results, helping you steer clear of dodgy domains.
Norton wants to help you get better at identifying and avoiding threats, too, as evidenced by the development of an AI-powered chatbot. Dubbed "Norton Genie", the bot can let you know whether that suspicious email you received is legitimate or a phishing attempt—and all you have to do is send it a screenshot or copy and paste some of the text.
The Norton Secure VPN isn't my favorite VPN on the market, but does a solid job of keeping your IP address hidden, your browsing private, and can even unblock a decent amount of streaming services. Combining the VPN with the intelligent firewall really maximizes your digital security, and you'll be alerted right away if an untrustworthy program attempts to connect to the internet. You can allow or block the connection, and Norton gives you plenty of detail (like the age of the program and the URL it's attempting to reach) to help you make a security-conscious decision.
Admittedly, Norton is a pretty pricey solution partially because of its LifeLock feature. This goes above and beyond the usual identity theft protection you get with other antivirus providers and will let you know if your details crop up on the dark web—and can even check to see if someone is using your identity as an alias. LifeLock even walks you through the process of restoring your identity if the worst happens.
It's worth noting that Norton's subscription prices do jump up after the introductory period. This isn't all that unusual, and you'll still be getting a huge amount of functionality in return for your investment. However, if you'd rather not commit to a long-term plan, you can try the antivirus software for free with a 30-day free trial—just remember to turn off auto-renewal to avoid being charged at the end of the month.
Features | Notes | Rating |
|---|---|---|
Protection | Excellent at detecting known malware, malicious URLs, and threats to your identity | ⭐⭐⭐⭐⭐ |
Performance | Slight lag when running, placing it right in the middle of the pack | ⭐⭐⭐⭐ |
Ease of use | Its dual dashboards can be tricky to navigate | ⭐⭐⭐ |
Advanced tools | An impressive tool set, including a solid VPN, password manager, and cloud backup | ⭐⭐⭐⭐⭐ |
Customer support | No problems reaching out to Norton via email, live chat, and even telephone | ⭐⭐⭐⭐⭐ |
Value | An undeniabley pricey product, but a plethora of tools ensure you're getting your money's worth | ⭐⭐⭐ |
The best antivirus security suite
Specifications
Reasons to buy
Reasons to avoid
✔️ You want the best malware protection: Avast came out on top in all of my malware-blocking tests.
✔️ Gaming is your priority: block untrustworthy incoming connections with a handy gaming mode—which is enabled by default.
✔️ You want to try before buying: Avast's free plan has its limitations, but effectively showcases the product's capabilities.
❌ You don't want to delete unwanted apps: Avast will do its very best to install its own internet browser and make it your new default, which is slightly frustrating.
❌ You need better VPN access: depending on your plan, you might experience bandwidth caps and a limited choice of servers
❌ You need clear warnings: at times, unwarranted warnings can pop up with no clear way to stop them
🔒 Avast One is a malware-blocking powerhouse that stops threats dead in their tracks. It won't slow your device to a crawl, either, and is incredibly easy to use—a great pick for antivirus first-timers.
Our Avast One review dives into the details, and perks, of each subscription plan.
Avast One is the newest offering from Avast, and comes packed with all of the malware protection, advanced features, and ease of use you'd expect from an industry veteran. You'll also be able to use the solution on any Windows, Mac, Android, or iOS device.
Avast One's scan speeds were pretty average, taking 32 minutes to complete a scan of 50 Gb of executable files. These scans are hugely customizable, too, and give you granular control over where you want the solution to focus. Smart Scans take a few seconds to check for malware and dodgy browser add-ons, Targeted Scans look at specified folders and files, and Full Scans comb through your entire system.
▶ Try Avast One Essential for free
Very few providers can keep up with Avast One when it comes to identifying and removing malware. None of my tests were able to crack its protection, and the latest report from AV-Comparitives revealed that it scored an outstanding 99.97% detection rate. So, you can rest assured that no threats will make it through to your device unseen.
Avast One shores up its security with a firewall that keeps tabs on your network traffic to thwart hackers, and can block your access to malicious websites to prevent infections. I also like that its Ransomware Shield was able to find folders containing user documents and automatically add them to its protect list.
The solution rounds out its antivirus package with useful extras—and the sheer amount of these features is what makes Avast One worth checking out. All of its paid subscriptions come with the HideMyAss!-powered SecureLine VPN, but if you're on the Essential plan, you'll have to deal with a limit of 5 Gb per week and a single server location. Despite these setbacks, this is still more than you need to catch up on your favorite Netflix shows.
Opt for a more expensive subscription and the VPN breaks free of these shackles. You'll have more than 50 server locations to choose from, and you'll also be alerted if you try to access a banking site, sensitive domain, or even a store without switching the VPN on first. This is a lifesaver if you want to go about your business without leaving an identifiable trail.
Avast One's features just keep coming. Subscribers get a password manager that'll check for compromised details, parental controls, webcam monitoring, and anti-phishing tools that ensure all aspects of your online life are secure.
If you're ready to take the plunge, there are three paid subscriptions to choose from. The Individual plan gets you access to all of the aforementioned tools and licenses for five devices, whereas the Family and Premium plans bump this number up to twenty five (the latter also comes with an identity monitory that'll let you know if your data ends up on the dark web). Thanks to the Essential plan, however, you can try a limited version of the product without paying a penny.
Features | Notes | Rating |
|---|---|---|
Protection | Top scores for malware protection from third-party test labs | ⭐⭐⭐⭐⭐ |
Performance | Doesn't create noticeable lag, and has an awesome gamer mode | ⭐⭐⭐⭐⭐ |
Ease of use | Friendly apps for all devices with a fresh design, and they're easy to use | ⭐⭐⭐⭐ |
Advanced tools | Paid users get the lion's share of features and access to an unlimited VPN | ⭐⭐⭐⭐ |
Customer support | No live chat, but you can typically get a response from support staff via email within 24 hours | ⭐⭐⭐⭐ |
Value | Subscriptions won't break the bank and come with a plethora of features, and the free plan is equally impressive | ⭐⭐⭐⭐⭐ |
The best antivirus for mobile
Specifications
Reasons to buy
Reasons to avoid
✔️ Mobile security is your priority: McAfee's mobile apps provide all-around protection that you can take on the go.
✔️ You want to protect your identity: check out a raft of tools and advanced features designed to safeguard against identity theft and phishing.
✔️ You need good network protection: keep hackers out of your home network system with an intelligent firewall for all of your devices.
❌ You're on a budget: McAfee is a big name with a big price tag, and particularly pricey on renewal.
❌ You use a Mac: although it does run on Mac computers, the solution still feels a little clunky compared to its Windows version.
❌ You want built-in parental controls: you'll need to pay extra to access parental controls, adding extra cost to a solution that's already pretty expensive.
🔒 McAfee is undoubtedly expensive, but earns its spot in my top picks with standout mobile apps, advanced features, and its prioritization of identity protection.
Our McAfee review goes into more detail about the solution's identity theft services—and how they're much better than simple ID monitoring.
McAfee has moved on from its Antivirus Plus and Total Protection packages with McAfee+. The McAfee+ subscriptions still include all of the standard malware protection while adding important identity theft monitoring tools.
The basic subscription, McAfee+ Essential, lets you protect up to 5 devices, and the good news is that it works on just about every platform—Windows, Mac, Android, iOS, and Chromebook included. Although it's a limited, first-level antivirus software, it still offers identity monitoring, a password manager, a firewall, a file shredder, and unlimited VPN access.
▶ Try McAfee+ with its 30 day money back guarantee
Two of the biggest independent test labs awarded McAfee top marks for online malware protection, which is incredibly encouraging. Still, I did notice slowdown when I put the apps to the test. McAfee is a pretty resource-hungry solution that takes up a lot of system resources—it won't slow you to a crawl, but other (cheaper) antivirus packages don't have this problem.
McAfee stands out from the crowd with a powerful identity theft prevention suite. The Online Account Cleanup tool can help you avoid being caught up in data leaks by pointing out which sites and services are holding onto your data. Then, it'll tell you which accounts you should keep, which you should delete, and even reduce the number of spam emails you receive—and that's in addition to alerting you if your information ends up on the dark web.
You can upgrade to a Premium or Advanced plan, although the Premium offering is somewhat disappointing. Its only advantages over the Essential plan are its system scans (it won't actually do any of the clean-up afterward, however) and unlimited device protection. I'd expect a lot more from a "premium" subscription.
However, I am impressed by McAfee's family protection. All family plans come with personalized insight and advice, and the Protection Score feature keeps tabs on everyone's digital security to generate that custom guidance. Armed with this information, you and your family will be able to navigate the web with more savvy, which is doubly important if you're sharing devices. McAfee's parental controls allow you to prevent children from accessing inappropriate content, manage screen time, and monitor their location.
One more important note, the VPN is available without any data restrictions regardless of the McAfee+ subscription you choose. However, it is only available if you agree to the McAfee autorenewal program.
Features | Notes | Rating |
|---|---|---|
Protection | Excellent protection and plenty of extra tools to help keep you secure | ⭐⭐⭐⭐⭐ |
Performance | Infrequent lagging, but not enough to interrupt what you're working on | ⭐⭐⭐⭐⭐ |
Ease of use | Mobile apps are pretty straightforward to use, desktop is a bit overwhelming when you first use it | ⭐⭐⭐⭐ |
Advanced tools | Many tools focus on protecting your identity including a VPN and personal data cleanup, but how well they work depends on what you're willing to pay | ⭐⭐⭐⭐ |
Customer support | Decent FAQs section on its website, and a support community, live chat is with a Virtual Assistant and not a live agent | ⭐⭐⭐⭐ |
Value | One of the most expensive antivirus programs, but you can use it on any number of devices | ⭐⭐⭐ |
The best antivirus with network protection
Specifications
Reasons to buy
Reasons to avoid
✔️ You have a lot of smart devices: F-Secure has one of the best network protection tools to secure every gadget connected to your home internet.
✔️ You value speed: scans balance speed with thoroughness without sacrificing either.
✔️ You need a VPN: the F-Secure VPN does have its limitations, but it's a useful tool to have in a pinch.
❌ You're new to antivirus: the dashboard is very text-heavy, which can be overwhelming, and it's not the easiest tool to install.
❌ You need Chromebook protection: unfortunately, F-Secure doesn't offer a Chromebook app—meaning you'll have to look elsewhere.
❌ You don't want to be slowed down: you might experience slower load times when opening programs or browsing the web, leading to serious frustration.
🔒 F-secure takes some getting used to, but all of the most important security and privacy tools are there—including incredible network protection and 24/7 live support.
Learn more in our F-Secure review, and explore how this antivirus solution protects desktops, mobile devices, and all of your smart gadgets.
F-Secure has had a makeover since I first started testing and evaluating antivirus software. It's better at detecting and blocking malware and is a lot lighter on device resources—but its star feature is its network protection.
Network protection keeps an eye on your internet connection, router movements, and everything that connects to your Wi-Fi, looking for anything suspicious. Ultimately, the feature acts as a shield against hackers attempting to break in through weak spots in the connection, and will warn you before they can do any real damage.
▶ Try F-Secure Total for 30 days free
F-Secure has plenty of tools to help protect against other digital nasties, too—and its antivirus suite has even won awards from testing organizations, like AV-TEST. The service puts a stop to ransomware, spyware, and trackers, and can even let you know if your password is weak or overused. I like that F-Secure also tells you if any services you use (or have signed up for) have been compromised, so you can take proactive steps to secure your most sensitive information.
As with most of my top picks, F-Secure comes with its own built-in VPN. It's not a showstopper, and can't really compare to the likes of ExpressVPN when it comes to quality and quantity of features, but if you need an extra layer of protection when you're shopping online, accessing your banking accounts, or connecting to public Wi-Fi networks, then it's well worth having.
Getting started with F-Secure isn't too difficult. It'll walk you through the download and install process, though there are a lot of pages to click through, which can be overwhelming to new users. On that note, configuring the various tools and options isn't the most intuitive process.
Thankfully, F-Secure is one of the few antivirus software companies that has 24/7 live support available. You can reach out to an agent via live chat and, if you encounter a particularly tricky issue, the agent can even connect to your device remotely to fix it from their device.
Features | Notes | Rating |
|---|---|---|
Protection | Excellent malware blocking and protects smart devices connected to your home network | ⭐⭐⭐⭐⭐ |
Performance | Some slowdown when launching programs or navigating the web | ⭐⭐⭐ |
Ease of use | Not the easiest to figure out, but the tutorials do help | ⭐⭐⭐⭐ |
Advanced tools | Not as many tools as other antivirus software, but the ones included are helpful | ⭐⭐⭐⭐ |
Customer support | Live support is available including remote support for difficult issues | ⭐⭐⭐⭐⭐ |
Value | First-time users get a great bargain, but the price jumps higher on renewal | ⭐⭐⭐⭐ |
The best of the rest
Specifications
Reasons to buy
Reasons to avoid
✔️ You bank or shop online: PayGuard, Trend Micro's secure banking feature, is one of the best in the industry.
✔️ You want web protection: Trend Micro has a robust URL blocker that will warn you if you stumble across a dangerous site.
❌ You're an avid gamer: Trend Micro has a noticeable impact on device performance, and can interrupt gameplay (and streaming.)
❌ You want to customize your experience: if you're looking for an antivirus solution you can customize, you're better off with Bitdefender.
🔒 Trend Micro doesn't come with a ton of added features, but if you need a boost of security for your banking and online shopping, Pay Guard is a fantastic option.
Read our Trend Micro review to discover more about its Pay Guard tool, how you can put it to use, and other security features.
Trend Micro Antivirus+ might not top my list, but it is a user-friendly solution with a clean interface—no clutter in sight. Simply hit the Scan button to get started, or use the navigation icons to find the features and tools you need.
In terms of protection, Trend Micro received an average score across test labs and our own research. While opinions are mixed, I saw that the solution does stop threats, like malware and ransomware, and didn't experience the increased amount of false positives that other reviewers reported. This leads me to believe that your mileage may vary with this antivirus package—even so, it has the basics covered.
▶ Try Trend Micro Antivirus+ Security for 30 days risk-free
One of its strongest features is the Pay Guard tool. Essentially, it acts as a shield on sites or services where you hand over financial and personal information—like your bank account and online stores. These transactions are constantly targeted by hackers and cybercriminals, hoping to make off with your credit card number or login credentials, so I'm glad to see Trend Micro tackle vulnerabilities head-on.
Wondering if there are weak points? Well, Trend Micro impacts system performance more than its biggest rivals and doesn't have the same long list of features. The latter isn't entirely negative, of course, seeing as it makes the solution more usable for newcomers. Advanced users won't find a lot to customize, unfortunately. Most of the tools simply toggle on or off.
You can increase the functionality slightly by opting for a more expensive plan. The next tier, Trend Micro Internet Security, throws in some interesting extras including parental controls and social media protection tools. However, for most folks, it’ll be worth spending a bit more on Trend Micro Maximum Security, which delivers protection for Mac and mobile devices as well as Windows (plus it adds a password manager and secure file vault).
Price-wise, Trend Micro Antivirus+ Security is cheap, and its Internet Security Maximum Security programs are also fairly priced. Bear in mind that you can only protect a single Windows device with its basic antivirus, but its top product gives you 10 licenses to share across any Windows, Mac, Android, iOS, or even Chromebook device.
Features | Notes | Rating |
|---|---|---|
Protection | Struggles a bit to stop brand new threats not included in malware databases | ⭐⭐⭐⭐ |
Performance | Causes some slowdown when downloading programs or launching an application | ⭐⭐⭐⭐ |
Ease of use | Very simple interface with essential security tools you need already turned on | ⭐⭐⭐⭐⭐ |
Advanced tools | Not a lot is included with its basic subscription, but Pay Guard comes with all antivirus subscriptions | ⭐⭐⭐ |
Customer support | Phone, email, and chat support are all available, but there may be some delays when trying to connect | ⭐⭐⭐⭐ |
Value | Not too bad for basic protection of a single Windows device | ⭐⭐⭐⭐⭐ |
Specifications
Reasons to buy
Reasons to avoid
✔️ You'd like to try before buying: Avira's free plan is limited, but gives you a good taste of what to expect if you choose to upgrade.
✔️ You want configurability: Avira gives users plenty of ways to tailor their security experience.
❌ You use a lot of locally saved apps: during my testing, I found that Avira causes apps to launch more slowly.
❌ You need mobile protection: most of Avira's packages aren't available for mobile devices—and those that are have a hefty price tag.
🔒 Avira has a lot of handy tools that can be configured down to the last detail and a free plan you can use to try before you buy—however, it's not the best pick for mobile devices.
In our Avira review, we take a closer look at the provider's Prime package and free plan.
Avira impresses right off the bat with one of the best free antivirus options on the market. It's more limited than the full internet security programs, but still protects your device against the likes of malware, ransomware, and phishing attacks. You'll also get access to an ad blocker and PUA shield, and even a price comparison tool that can help pinpoint bargains on the web—which is a nice bonus.
The free tier is a great way to get a feel for the service and its roster of features, but if you're ready to take your security to the next level, there are a few subscription tiers to choose from. The Pro and Internet Security plans are reasonably priced and come with all of the core functionality of a robust solution, but only the Prime plan includes the full scope of advanced features, including the unlimited VPN.
▶ Try Avira antivirus for free
Other standout features include a password manager that'll help you keep track of all your logins, a system optimizer, and safe browsing tools with specific protections for when you're banking or shopping online. You'll need to enable pretty much all of these features when you first launch Avira, but its primary real-time protection is automatically switched on.
Avita is very customizable, which is good news if you have some tech-savvy and want to tailor your antivirus experience. New users taking their first steps into the world of web protection might feel overwhelmed by the scope here, and the amount of manual input required, especially compared to a service like Bitdefender that you can, essentially, use right out of the box.
It's also worth noting that I saw some serious slowdown when using Avira. Pages were slow to load and apps took a while to boot up. In fact, during the installation process itself, I had to battle through lag and a system freeze before the program caught up.
All in all, Avira is a well-rounded service that you can try without parting with a penny—though its most expensive Prime plan is where the value is at if you do decide to commit to a premium subscription. Avita is also one of just a handful of antivirus software that offers a monthly subscription.
Features | Notes | Rating |
|---|---|---|
Protection | No problem stopping both known and new malware threats | ⭐⭐⭐⭐⭐ |
Performance | Slower at loading webpages and downloading software | ⭐⭐⭐⭐ |
Ease of use | Dark mode interface that is intuitively laid out, but most tools, including ransomware protections, have to be turned on | ⭐⭐⭐ |
Advanced tools | Includes some good advanced security tools, but not enough to be compared with other "internet security" suites | ⭐⭐⭐ |
Customer support | Some basic help articles are online, the only way to contact a live agent is through the email form | ⭐⭐⭐ |
Value | Decent price point and has a monthly subscription available | ⭐⭐⭐⭐ |
Specifications
Reasons to buy
Reasons to avoid
✔️ You want an antivirus you can configure: plenty of low-level configurability gives you granular control over setup and features.
✔️ You need multi-device support: with ESET, you can choose how many devices to include in your subscription.
❌ You need a wide array of tools: ESET isn't as feature-rich as its closest competitors, though its advanced tools are still solid.
❌ You want iOS support: if you want to secure your iPhone or iPad, I'd recommend checking out Bitdefender's mobile apps.
🔒 ESET is easy to install, though a little more difficult to figure out once it's up and running. Plus, some important security features are reserved for its most expensive product.
Our ESET review highlights the highs, lows, and advanced functionalities of this antivirus software.
Depending on the plan you choose, ESET Antivirus protection ranges from the solid but basic to more expert-level. Its stripped-back "Essential Security" tier will take care of malware, ransomware, and phishing attacks for you, and nothing else, whereas the "Premium Security" plan includes extras like a password manager, banking tools, and data encryption.
One of the most useful ESET tools is its network protection. Generally, network protections are included in antivirus packages as a way to monitor your internet connection and the data traveling through it. ESET, however, protects any device connected to the internet, including mobile phones and tablets, and even IoT gadgets like Amazon Echo and Google Home. This is awesome coverage, and will secure a whole household of devices from digital intruders.
▶ Try ESET Internet Security for 30 days free
ESET's overall protection is good, though it doesn't quite match up to Avast or Norton. Third-party test labs agreed that ESET comes up short compared to the big players in the antivirus sphere, especially when it comes to blocking new threats.
Zero-day malware detection is reserved for the more expensive ESET subscriptions—which is a huge part of why it didn't crack our top five. New-threat protection is an essential part of any antivirus offering in my book, and one that should be included across all plans. Luckily, the majority of antivirus software firms share my opinion.
I'd also like to see ESET introduce a quick scan tool. Currently, you're limited to Full System, Removable Devices, and Custom scans—the good news, however, is that all of these scans are pretty speedy.
You might experience some drag on your system when using ESET—I certainly did. I could still work, browse the internet, and check emails without being slowed to a crawl, but the impact was noticeable enough that I wouldn't recommend the solution to anyone who's an avid online gamer.
Features | Notes | Rating |
|---|---|---|
Protection | Slightly below average of the industry average in some independent tests, doesn't include new threat detection in all programs | ⭐⭐⭐ |
Performance | Definitely can feel the lag when using this antivirus | ⭐⭐⭐ |
Ease of use | The interface feels outdated with a lot of text that gives it an overwhelming, busy look | ⭐⭐⭐⭐ |
Advanced tools | Missing some important tools like a password manager and data encryption, but the number of security features is impressive | ⭐⭐⭐⭐ |
Customer support | Not the easiest to find answers to questions and even harder to figure out how to get a hold of a live person | ⭐⭐⭐ |
Value | An overall good deal, though we wish more was included | ⭐⭐⭐⭐ |
Specifications
Reasons to buy
Reasons to avoid
✔️ You have an existing malware infection: when it comes to getting rid of threats that are already on your computer, Malwarebytes is unbeatable.
✔️ You want to see real-time security reports: check out what the antivirus is doing, at any time, with detailed insights.
❌ You need flawless detection: Malwarebytes can struggle to pinpoint, and resolve, new threats.
❌ You want to protect more than Windows devices: while the solution is compatible with other operating systems, it's also more limited.
🔒 Malwarebytes excels at removing malware already on your device, but falls short of real-time protection.
Visit our Malwarebytes review for more insight into its Free and Pro plans, their features, and major differences.
If you've heard of Malwarebytes, you've probably also heard of its free plan—which is a pretty powerful malware removal tool in its own right. Malware will do its best to redirect you away from antivirus software sites, making it difficult to remove once it's got a foothold. Because Malwarebytes is a removal tool and not an antivirus, it can get onto your device, without being blocked, and pick out all of the threats giving your device a hard time.
Unfortunately, the free software doesn't come with any extra virus protection once those threats are dealt with. For that, you'll need to upgrade to the paid Premium subscription. You'll get a limited trial of the Premium plan when you install the solution, which is rather generous, so you can trial the features in your own time—including basic real-time security and ransomware protection, and more advanced tools like Play Mode, which redirects resources away from the security suite to your computer whenever you boot up a game or watch a movie.
▶ Get Malwarebytes free edition
The antivirus software doesn't just monitor threats in real-time—you'll also get real-time reports on your security status. These insights are hugely valuable, as they'll let you know if there are any vulnerabilities in your network connection. I also like that Malwarebytes can give you a heads-up about websites that are known to contain malware or phishing scams, so you can avoid them, risk-free.
Malwarebytes is compatible with most platforms and its malware removal tools are as effective on mobile devices as they are on desktops. However, some of its antivirus tools are only available for Windows—like Brute Force and Uninstall Protections designed to keep hackers at bay and prevent malware from removing the software from your system.
In our tests, and during third-party evaluations, Malwarebytes wasn't as effective as stopping malware as some of the other names in this list. The solution couldn't pick up on our simulated ransomware attack, for example, and was slow to react to malware. Hopefully, the company is working on this—and I'm confident that it'll shoot up the rankings once it's able to balance its excellent removal tools with a solid antivirus program.
You can protect up to 10 devices with Malwarebytes, which should be more than enough to cover all of the most important gadgets in the house, and even add a VPN to your package for just an extra $3 per month.
Features | Notes | Rating |
|---|---|---|
Protection | Not as effective at blocking malware as it is at removing current infections | ⭐⭐⭐⭐ |
Performance | Fairly light on resources, so not a problem to run it in the background | ⭐⭐⭐⭐⭐ |
Ease of use | Basic use is easy to figure out, but it gets harder when you need to customize settings | ⭐⭐⭐⭐ |
Advanced tools | Doesn't have the level of advanced features we'd expect in a Pro program | ⭐⭐⭐ |
Customer support | All support links redirect you to its extensive knowledgebase rather than provide live support options right away | ⭐⭐⭐ |
Value | Monthly subscription prices are about right for what is offered | ⭐⭐⭐⭐ |
Specifications
Reasons to buy
Reasons to avoid
✔️ You're a Mac user: Intego is designed specifically for Mac machines.
✔️ You need parental controls: you won't find many other antivirus solutions for Mac that include configurable parental controls.
❌ You need mobile protection: unfortunately, this antivirus offering is only available for desktops.
❌ You're looking for powerful extras: Intego doesn't have the quantity, or quality, of advanced features as our other picks.
🔒 Intego is a great pick for Mac machines, and can clean up your system to keep it running efficiently.
Read our full Intego review to learn how it stacks up against other Mac antivirus software.
If you're a Mac loyalist, you'll want to check out Intego Mac Premium Bundle X9—it's a bit of a mouthful, but it's a solid service that's easy to download, install, and navigate. You can use the Windows version, if you prefer, but I found that it performs a lot better on Mac machines.
Protection-wise, Intego consistently earns high marks for its performance in third-party tests. It can tackle Mac and Windows threats, and while the latter won't harm your device, they can be inadvertently passed on to Windows users connected to the same network or via email attachments. So, it's a great preventative measure to have running in the background.
Intego used to cause a lot of slowdown, and I'm glad to see that this is no longer the case. I'm just as impressed by the Mac Washing Machine, which helps you find and tidy up potential threats on your system that could be leveraged by hackers. This could be anything from old versions of software, remnants of deleted files, unused apps, and more.
Opt for the Mac malware bundle and you'll also have access to ContentBarrier which is, essentially, your parental controls. Keeping your children away from inappropriate, adult, and dangerous web pages is straightforward and simple—you can click on the various filters to prevent access or add specific URLs to the blacklist.
Getting Intego's tools set up isn't quite as stress-free. Each one is a separate program, which means each one has to be downloaded, installed, and set up individually—which, as you can imagine, gets tedious pretty quickly. There are shortcuts on the VirusBarrer dashboard that'll point you in the direction of the tool you need when you need it, which is a nice touch, but it'd be so much easier if Intego could figure out a way to combine everything into a single download.
Unfortunately, Intego isn't available for iPhones or other iOS devices, which means you won't be able to take your antivirus protection with you on the go. If that's not a deal-breaker, and you're fine sticking to your desktop and laptop, then Intego is still a solid choice with a good number of tools.
Features | Notes | Rating |
|---|---|---|
Protection | Misses a few threats, but does score higher than average for malware detection | ⭐⭐⭐⭐ |
Performance | We noticed a bit of lag with the app itself, but it didn't seem to affect our working and browsing too much | ⭐⭐⭐⭐ |
Ease of use | Each tool is a separate download with its own dashboard making it harder to navigate the entire package | ⭐⭐⭐ |
Advanced tools | A bit limited, but the system cleaner and parental controls are effective | ⭐⭐⭐ |
Customer support | Lots of pages to navigate through the find the support email form, live chat is sometimes available | ⭐⭐⭐ |
Value | It's expensive, other Mac antivirus is available for cheaper and with more tools | ⭐⭐⭐ |
TechRadar's antivirus rankings
There are more antivirus solutions on the market than we can count—but only ten spots in our list of favorites. Below, you can check out our rankings at a glance, including some honorable mentions that just missed out on a spot in our shortlist.
Provider | Summary |
|---|---|
1. Bitdefender | Sets the standard for all antivirus to reach for |
2. Norton | Good protection and great identity theft services |
3. Avast | Easy to use, great advanced security, excellent gaming mode |
4. McAfee | Good for mobile, and decent on other devices, too, but expensive |
5. F-Secure | Protects smart devices, such as TVs and Amazon Echo connected to your network |
6. Trend Micro | Good protections for banking and shopping online |
7. AVIRA | Decent tools with a good free antivirus available |
8. ESET | Okay for basic protection, but feels outdated and falls behind better options |
9. Malwarebytes | Not the best as a first defender malware blocker, but is excellent at removing threats already on your device |
10. Intego | Specifically designed for Mac computers, does well at blocking threats, but awkward to use |
11. AVG | Easy, simple interface, and good protection, but you need to enable real-time protection and other important protection tools |
12. VIPRE | A good value and very basic if you don't need more than bare minimum antivirus |
13. Sophos | Requires internet connection to use properly, which means offline threats have a chance to sneak through |
14. Webroot | Lots of potential, and great security tools, but hard to validate security claims since it doesn’t allow third-party testing |
Comes free with Windows, but there are definite gaps in protection that make using a secondary program necessary |
How to choose antivirus software
How do you decide on just one antivirus solution when there are dozens of viable candidates out there? The obvious answer is to consult our rankings—our shortlist is the result of pooled expert knowledge, in-house testing, third-party security labs testing, and thorough, continually updated reviews of the top antivirus players.
Perhaps more importantly, however, you need to consider your own needs and use case. Do you have a ton of devices to protect? Do you need advanced features or specific tools? Do you want a service with a built-in VPN to save money on subscription fees?
These considerations will vary from person to person and might mean that our number one pick isn't your match made in heaven. Our recommendations can point you in the direction of some stellar options, but you'll need to modify these based on your individual requirements.
For more thoughts on this, check out our article exploring how to choose the best antivirus.
How we test antivirus software - our review methodology
To get a clear, accurate, and thorough picture of each antivirus, I take a multi-faceted approach to my testing—and I make sure I get hands-on experience with each product.
Some of my tests involve attempting to access websites known to harbor threats or downloading malware. In these cases, I'm trying to see if the antivirus can recognize, and resolve, the threats, and how quickly it springs into action.
Thanks to our team's background in IT, we're able to create malware files for specific use in testing environments. We keep these files on a short leash and let them wreak a little havoc—nothing that we can't control, of course—but this is an important part of the process, seeing as they're new threats that no antivirus software will be familiar with.
Lots of provide a test file called EICAR that simulates a threat that isn't a threat. The problem with relying on this file during testing is that antivirus companies have made sure that their software recognizes it. Using our own bespoke malware helps us evaluate how well these services deal with the unknown.
We don't rely solely on our findings, however. There are all sorts of ways to test antivirus and some fantastic labs out there that do it a lot more frequently than we do. That's why we refer to results from AV-Comparatives and AV-Tests to paint a broader picture of the antivirus software's capabilities and assign a fair protection score.
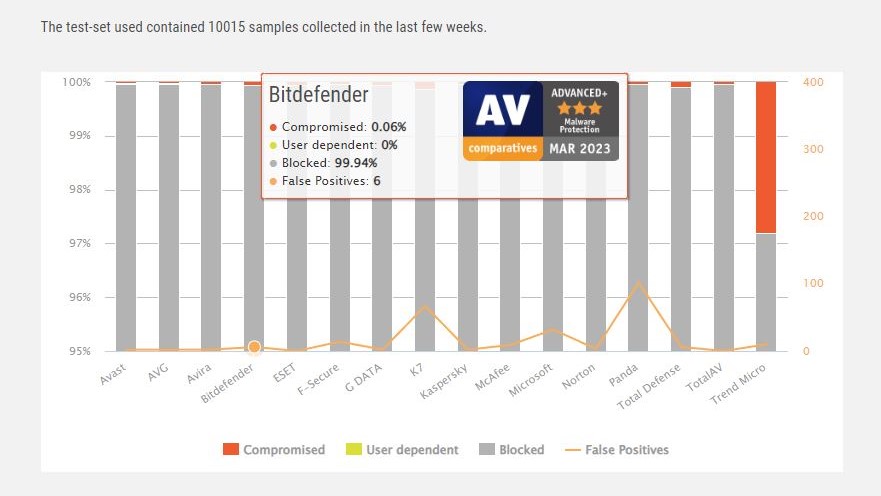
Performance is a critical consideration during our testing. We need to know how much slowdown is caused by installing and running the antivirus, and how much it's going to impact your day-to-day activities. After all, an antivirus that zaps every threat known to man, but slows your machine down to a crawl, won't be much use to anyone.
We know that resources will be used, seeing as the antivirus programs are saved locally on the device, but we still measure things like how long it takes to open a browser, navigate to a website, attach a file to an email, or how long it takes a webpage to load fully.
Online speed test websites give us a hand with this process by providing the nit-picky numbers to supplement our real-time testing. That way, we can balance solid statistics with our individual experiences, to get a real feel for how the antivirus behaves outside of a lab.
As you'd expect, real-time testing involves us installing and using antivirus programs on our home devices. We'll keep track of anything out of the ordinary, the highs and lows, and how easy the software is to navigate. This is also where we'll dig into the tools and settings to see if they do everything that they're supposed to do—think password managers, file encryption, VPN add-ons, and parental controls.
Customer support is another important aspect of any review. Usually, it's easy enough to follow along with the on-screen instructions provided by the installation wizard when you download new antivirus software, but that doesn't mean there aren't times when you'll need a little extra help from an agent.
We evaluate each company's support options, ranging from the live chat support and email ticketing systems, if available, and the online library of resources. We measure how quickly agents respond to our inquries, how detailed their reply is, and how accessible the company's resources are—particularly for new users.
Tested by

Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided.

Sead is a seasoned freelance journalist based in Sarajevo, Bosnia and Herzegovina. He covers all things cybersecurity, including ID theft, ransomware, and data breaches, as well as laws and regulations related to the field.
The best antivirus FAQs
What is the best antivirus of 2025
I put all of today's top dogs to the test and found that Bitdefender is the best antivirus software in 2025.
It's a superb bit of kit—from its entry-level Bitdefender Antivirus Plus and its cast-iron malware defenses, excellent threat detection and genuinely value-adding extra features, right up to its all-singing, all-dancing Total Security that adds an array of maintenance tools and can be used to protect your family's computers, tablets and phones.
What does antivirus do? How does virus protection work?
An antivirus app sits on your device like a guard dog, watching over the entire system and sniffing out suspicious intruders. In short, it offers real-time defenses against viruses or other threats, which, if detected, are immediately dealt with, preventing them from carrying out their destructive payload. As well as this automated protection, you can run manual virus scans whenever you wish.
Antivirus applications use what are called virus ‘definitions’ to catch intruders. Think of these as the fingerprints of malware, and if something is spotted coming onto your system that has a matching fingerprint, the antivirus leaps into action, quarantining the offender. As another line of defense, antivirus programs also use what are called ‘heuristics’ that look for any file or process exhibiting suspicious behavior—this allows the app to potentially catch any freshly made malware that isn’t yet in its definitions database.
For more details on this topic, see our full breakdown of exactly how antivirus software works.

Do I really need antivirus in 2025?
The internet is jam-packed with threats, like ransomware, cooked up by cybercriminals willing to do whatever it takes to get what they want. Security breaches are commonplace, unfortunately, and hackers use malware to crack a company's system and make off with important files—including customer information. Unfortunately, that means that you're the ultimate victim of these attacks, seeing as they can lead to identity theft.
Today's best antivirus programs can help prevent identity theft by keeping an eye on the dark web, where all sorts of personal information is bought and sold. You'll also get protection against phishing scams, and block messages designed to trick you into handing over personal information to dodgy third parties.
More and more antivirus software includes a VPN, too, which will safeguard your browsing sessions regardless of the device you're using. You'll be able to bypass geo-restrictions and blocks, and avoid cookies, trackers, and invasive ads.
You may have heard arguments that if you’re prudent about where you browse on the web, and what you download or click on, you’ll be fine—and that’s true to a certain extent, but I really wouldn’t risk it. Even well-known websites might occasionally be victims of malware being peddled via their adverts (in other words, the ad networks they work with), for example, so no matter how cautious and tech-savvy you are, it’s worth having an antivirus app as a fall-back defense.
Fortunately, the best antivirus products are getting more and more affordable—and free antivirus keeps improving, too.
Is free antivirus enough?
Unfortunately, there's not a simple yes or no answer to this question.
A good free antivirus can boost your digital security, and a lot of folks will rely on Microsoft Defender to do the job. The good news is that Microsoft Defender is a decent option that'll cover all of the basics when it comes to putting a stop to viruses and malware.
You'll find that most free antivirus use the same protection engine (the central tech that monitors your device and thwarts threats) as their paid counterparts.
However, premium antivirus programs offer extra features above and beyond the fundamentals. A robust system of parental controls could be a huge win for those with kids, for example. Or, a dedicated anti-ransomware layer of protection that only comes with the paid-for product could help catch one of the most dreaded infections and halt it in its tracks.
Given how cheap some premium antivirus apps are—particularly with the various deals on offer—it’s well worth considering going this route instead to get extra features that could give you more peace of mind.
For more on this, read our full piece on whether free antivirus is enough to protect you.
March 2025 Update
Recent updates
March 2025 Update - In this update I have made the introduction more concise to help you access the information you need, faster. I have also checked pricing and deals to ensure you get the best deal possible on the best antivirus. I have also made sure that all of the features offered by each service are still available, and double checked the platforms and devices each antivirus service supports.
Editors' note: Kaspersky Anti-Virus used to appear on this list. However, considering the current climate, and the recent ban of the sale of Kaspersky software in the US, we've made the decision to remove the provider.
Although much of the company's core processes now take place in Switzerland, the fact that its headquarters remain in Moscow, and that there are prior allegations around government coercion, it feels prudent to urge caution when considering the provider.
What's more, with so many excellent alternatives to choose from, it's impossible to wholeheartedly recommend Kaspersky at this time.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!

Benedict has been writing about security issues for over 7 years, first focusing on geopolitics and international relations while at the University of Buckingham. During this time he studied BA Politics with Journalism, for which he received a second-class honours (upper division), then continuing his studies at a postgraduate level, achieving a distinction in MA Security, Intelligence and Diplomacy. Upon joining TechRadar Pro as a Staff Writer, Benedict transitioned his focus towards cybersecurity, exploring state-sponsored threat actors, malware, social engineering, and national security. Benedict is also an expert on B2B security products, including firewalls, antivirus, endpoint security, and password management.
- Mike WilliamsLead security reviewer
- River HartTech Software Editor