The Kremlin’s pursuit of winning its ‘special military operation’ knows no bounds, as Russia-linked group resorts to spamming Ukraine into submission
Russia-linked groups send questionable recipes and advice to Ukrainian civilians

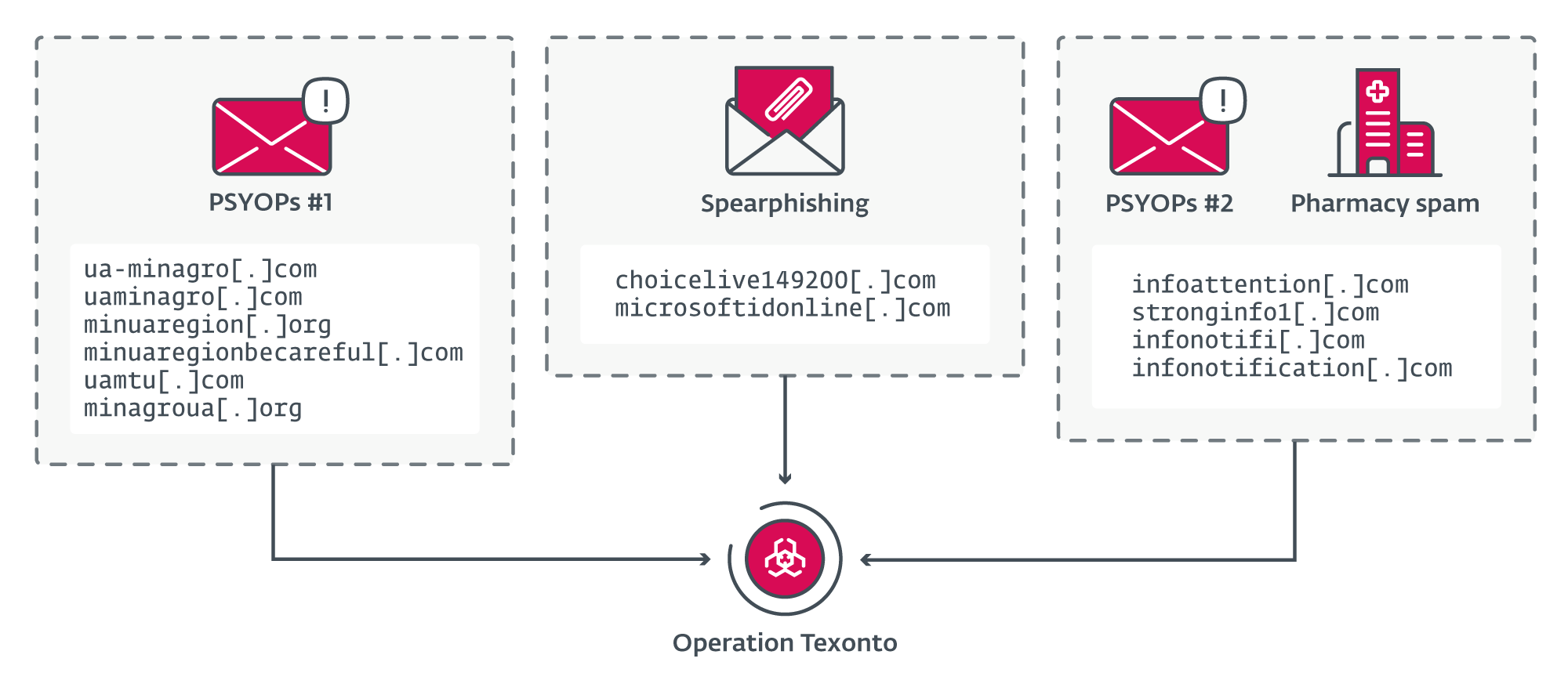
Recent research by ESET has uncovered several waves of psychological campaigns, known as Operation Texonto, that seek to demoralize and disrupt the Ukrainian population.
The email spam psyops spread doubt and distrust in the form of exaggerated claims of power, heating, and healthcare disruptions through the winter of 2023.
Interestingly, the server used to distribute the mass-spam campaign was later used again to distribute fake Canadian pharmacy emails advertising male-targeted pills for a “cheerful life.”
Nettle soup and pigeon risotto a la Kremlin
Several of the emails identified as part of Operation Texonto bear the identifying features such as the Ukrainian Trident, and are designed to look like official distributions from the various energy, healthcare and agricultural ministries.
In machine translations provided on ESET’s WeLiveSecurity blog, the first wave of psyop emails that arrived in November 2023 stated that energy shortages caused by Russia’s targeting of energy infrastructure meant that the temperature inside houses could be “several degrees below the permissible values.”
One fake email from the Ministry of Agriculture included a PDF detailing recipes for nettle soup and “pigeon risotto,” which was sent with the advice to combat food shortages by “eating fresh, juicy leaves of herbs in the form of salads.”

In an astounding self-criticism, the fake Ministry of Health emailed Ukrainians to tell them that there would be severe drug shortages and delays as “Ukraine completely refused Russian and Belarusian pharmaceutical drugs companies.”
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
While it is important to recognize that these are machine translations and are not exact, the general content of the emails themselves are a common theme among Russian psychological and propaganda operations targeting Ukraine.
The second round of Operation Texonto occurred in December 2023, again targeting Ukranians, but extending its reach to the populations of European countries as well. The translation of one of the emails included a heartwarming New Year's message stating that, “only together we will be able to drive out the Satanists from the USA.”
A second email from the same campaign was apparently written to target soldiers or potential recruits, attempting to convince them to cut off one of their own limbs as “this means that you won't meet a Russian soldier in a trench,” with the email signing off with, “Remember that sometimes one is better than two!”
“The strange brew of espionage, information operations, and fake pharma messages can only remind us of Callisto, a well-known Russia-aligned cyberespionage group,” said the ESET researcher responsible for uncovering Operation Texonto, Matthieu Faou.
“While there are several high-level points of similarity between Operation Texonto and Callisto operations, we haven’t found any technical overlap, and we currently do not attribute Operation Texonto to a specific threat actor.
“However, given the TTPs, targeting, and the spread of messages, we attribute the operation with high confidence to a group that is Russia aligned.”
More from TechRadar Pro

Benedict has been writing about security issues for over 7 years, first focusing on geopolitics and international relations while at the University of Buckingham. During this time he studied BA Politics with Journalism, for which he received a second-class honours (upper division), then continuing his studies at a postgraduate level, achieving a distinction in MA Security, Intelligence and Diplomacy. Upon joining TechRadar Pro as a Staff Writer, Benedict transitioned his focus towards cybersecurity, exploring state-sponsored threat actors, malware, social engineering, and national security. Benedict is also an expert on B2B security products, including firewalls, antivirus, endpoint security, and password management.