This sophisticated new phishing campaign is going after US government contractors
"Uncle Scam" campaign pretends to be a government agency looking for contractors

Cybercriminals have been spotted running a devious new phishing scheme targeting contractors looking for work with the US government.
Researchers from Perception Point revealed the “Uncle Scam” campaign bypasses security checks to deliver sophisticated phishing emails designed by LLMs to be extremely convincing.
The attackers use advanced tools, including AI-powered phishing kits and the Microsoft Dynamics 365 platform, to execute convincing multi-step attacks.
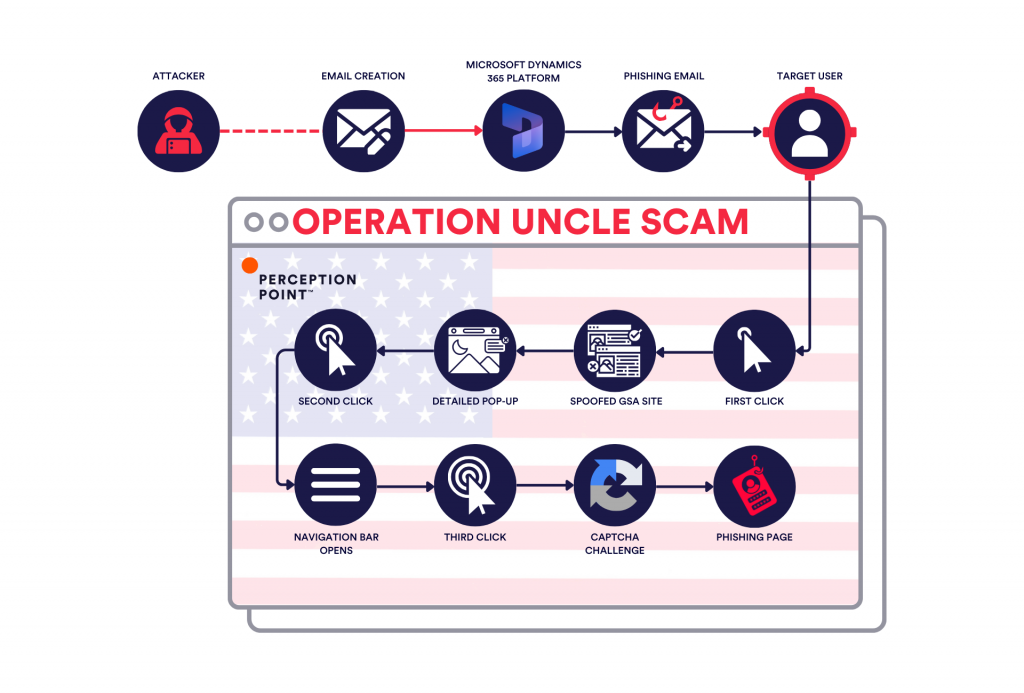
Abusing Microsoft Dynamics 365 & LLMs
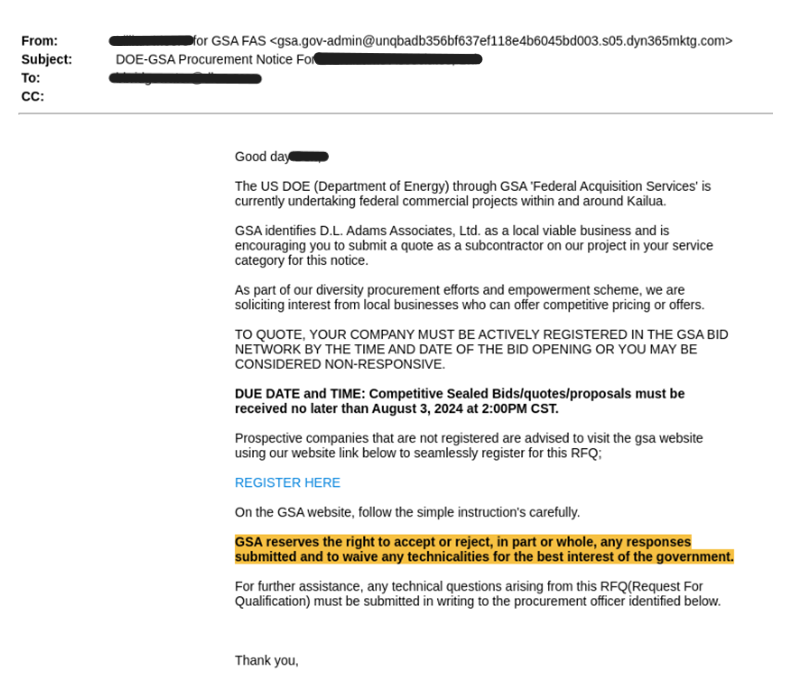
The campaign begins with a phishing email that appears to come from a legitimate US government agency, such as the General Services Administration (GSA).
The email invites recipients to submit bids for federal projects, mimicking real procurement notices, but upon clicking the link provided in the email, the user is redirected to a spoofed GSA website that closely resembles the legitimate one.
The attackers have gone to great lengths to replicate the official site, even including navigation links and a search bar that redirects users to real GSA pages. For reference, the legitimate GSA domain is www.gsa.gov, while the fraudulent domain may be in this form “gsa-gov-dol-procurement-notice(.)procure-rfq(.)online”.
Once landed on the phishing site, users are prompted to register for the RFQ (Request for Quotation) by providing their email and other details. This additional step is not just for show but is designed to make the phishing attempt more convincing and to evade detection. The attackers further complicate matters by including a CAPTCHA page, making it more difficult for automated security tools to access the credential harvesting page.
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
One of the key elements that makes this phishing campaign particularly effective is the abuse of Microsoft's Dynamics 365 Marketing platform. The attackers leverage the domain "dyn365mktg.com," associated with Dynamics 365, to send out their malicious emails. Because this domain is pre-authenticated by Microsoft and complies with DKIM and SPF standards, phishing emails are more likely to bypass spam filters and reach the inboxes of unsuspecting recipients.
This built-in credibility, coupled with the high deliverability of emails from this domain, makes the phishing attempt appear legitimate and increases its chances of success. The use of a trusted marketing platform like Dynamics 365 adds a layer of authenticity to the phishing emails, making them more convincing and harder to detect.
The "Uncle Scam" campaign also makes use of Large Language Models (LLMs) to craft phishing emails. These advanced models enable attackers to generate high-quality and contextually accurate phishing emails that mimic the tone and structure of legitimate communications. These emails are usually grammatically correct and have a professional tone because they integrate specific details of the impersonated departments.
The use of LLMs allows attackers to scale their phishing efforts efficiently. They can produce multiple versions of the same phishing email with minor differences. This scalability ensures that each email is unique yet consistent in quality, making it more difficult for victims to spot the scam.
To safeguard your organization from falling victim to sophisticated phishing attacks like "Uncle Scam," Perception Point recommends taking the following precautions:
- Double-check the Sender's Email: Always scrutinize the sender's email address for any signs of impersonation.
- Hover Before You Click: Before clicking any link, hover over it to reveal the actual URL and ensure it is legitimate.
- Look for Errors: Pay attention to minor grammatical mistakes, unusual phrasing, or inconsistencies in the email content.
- Leverage Advanced Detection Tools: Implement AI-powered multi-layered security solutions to detect and neutralize sophisticated phishing attempts.
- Educate Your Team: Regularly train employees on how to identify phishing emails and the importance of verifying unsolicited communications.
- Trust Your Instincts: If an email or offer seems too good to be true, it probably is. Always verify the authenticity of such communications through trusted channels.
The tactics of cybercriminals are evolving and the "Uncle Scam" phishing campaign is a reminder of this fact. Hackers have developed highly convincing and difficult-to-detect phishing operations with the help of trusted platforms like Microsoft Dynamics 365 and advanced AI tools. However, with vigilance and valid proactive steps, organizations and businesses can protect themselves from these threats.
More from TechRadar Pro
- Here is our guide to the best malware removal tools around
- Trump 2024 campaign allegedly targeted by Iranian hackers — Microsoft reveals apparent attack ahead of US election
- These are the best endpoint protection services on offer today

Efosa has been writing about technology for over 7 years, initially driven by curiosity but now fueled by a strong passion for the field. He holds both a Master's and a PhD in sciences, which provided him with a solid foundation in analytical thinking. Efosa developed a keen interest in technology policy, specifically exploring the intersection of privacy, security, and politics. His research delves into how technological advancements influence regulatory frameworks and societal norms, particularly concerning data protection and cybersecurity. Upon joining TechRadar Pro, in addition to privacy and technology policy, he is also focused on B2B security products. Efosa can be contacted at this email: udinmwenefosa@gmail.com