TechRadar Verdict
Don't be put off by Threatlocker's fairly spartan UI: this is a very powerful platform for any network manager who takes endpoint security seriously. Setup and deployment takes minutes, there's a free trial and threat detection is instant and effective.
Pros
- +
Huge number of features
- +
Easy Setup
- +
Powerful threat detection
Cons
- -
Basic UI (Beta Available)
Why you can trust TechRadar
Threatlocker is a newcomer to the cybersecurity game - the Florida-based company was only founded in 2017, long after security giants like Symantec and Kaspersky. Still, at TechRadar we pride ourselves on our ability to find scrappy new contenders and were intrigued when a Threatlocker representative reached out to us about their endpoint protection security platform. Have we uncovered a diamond in the rough, or should this platform have stayed in its eponymous locker? In this guide, you'll decide.
Threatlocker: Plans and pricing
If you're looking for a pricing sheet with detailed tiers, Threatlocker will leave you disappointed. Unlike some other endpoint security platforms we've reviewed, there's no 'per seat' charge for monthly or annual subscriptions. Interested parties can contact Threatlocker's sales department via e-mail or telephone, proudly displayed on the main website.
This said, it's only too easy to provide an email address to book a product demo with one of the company's 'Cyber Heroes'. There's also a 30-day free trial of the platform, with no credit card information required.
Threatlocker: Features
Of all the endpoint security platforms we've reviewed, Threatlocker definitely has one of the most impressive array of features.
The main product page provides a very good overview of these and the platform includes basic features we'd expect to see such as black and whitelisting of applications. We were much more intrigued though to read about Threatlocker's 'Ringfencing' feature, which allows managers to set boundaries for how certain applications interact with each other.
Although the platform doesn't incorporate a dedicated firewall for clients, it does include 'Dynamic Network Control'. This allows IT admins to regulate traffic, as well as open ports only for authorized applications using dynamic ACLs (Access Control Lists) or agent authentications. The Threatlocker website rightly points out that this is an often overlooked security gap when it comes to endpoint security platforms, which can spell disaster if a rogue device infiltrates your network.
The platform also has a very advanced policy engine, which can also be used in a 'firewall-like' manner to restrict what applications can do. Threatlocker refer to their 'Allowlisting' as a way to put you in control over what software, scripts, executables, and libraries can run on your endpoints and servers. This 'Allow List' can be exclusive, in that it can block any applications that aren't included on it.
Users can also set time-based policies, so applications can only be accessed and/or perform certain functions at an allotted time during the day.
Threatlocker claims their support team is available 24/7, 365 days a year via telephone or the main portal. The website asserts that calls are answered within 30 seconds. Although we can't speak to this, when we decided to test pilot this platform we received replies to our emails within minutes.
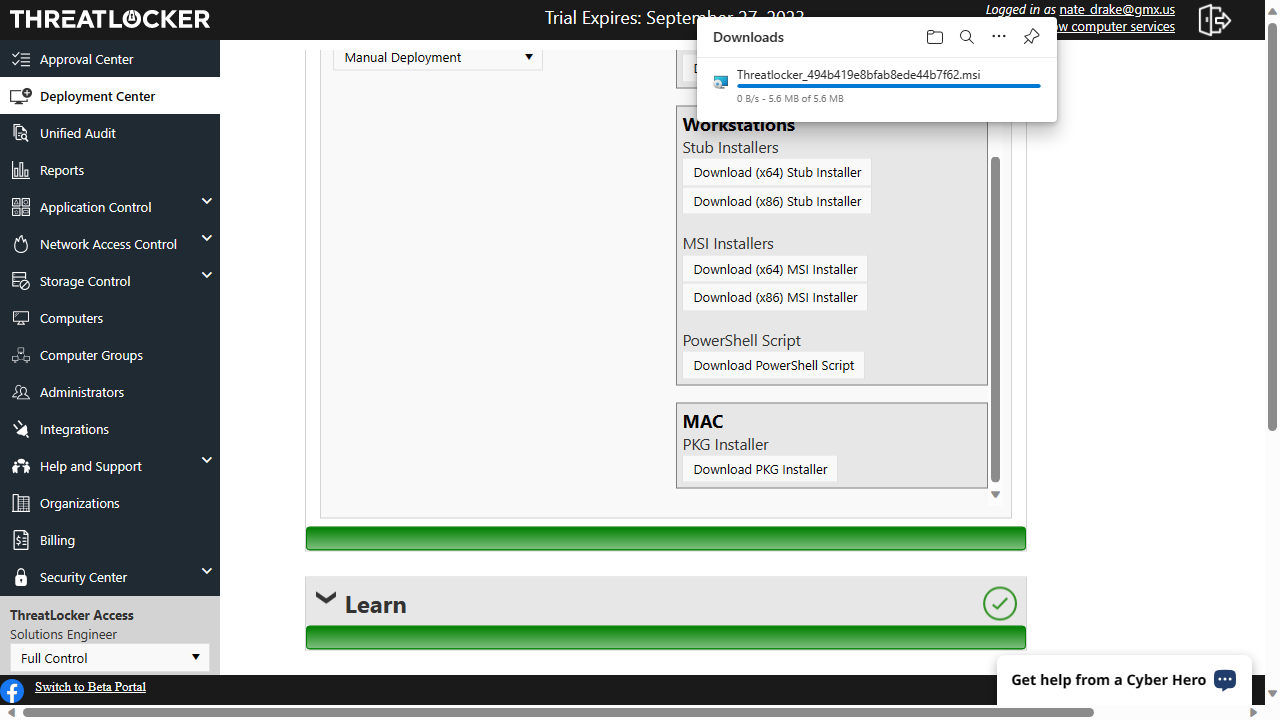
Threatlocker: Setup
We've previously mentioned Threatlocker's extremely friendly and helpful support team, who offered to contact us and set up a demo to walk us through the onboarding process. We appreciated the offer but decided to go it alone to see how easy the platform is to use. Nevertheless, it's good to know that help is on hand if needed.
After signing up for the Threatlocker trial, users are asked to provide their company and contact details. Next, you're logged straight in to the Threatlocker portal. We immediately headed over to the 'Deployment Center' to install the agent software on our test machine.
Threatlocker offers a number of ways to do this, including RMM (Remote Monitoring & Management), software deployment tool, Active Directory and Power Shell. We opted to install the agent manually using the Windows installer. There's an MSI version but we opted instead for the tiny 'stub' utility, which Threatlocker advises will install the most current version of the ThreatLocker Agent.
Agents are available for both Windows (Servers and Workstations) and macOS. We couldn't find any mention of Linux or mobile devices.
Threatlocker: Interface
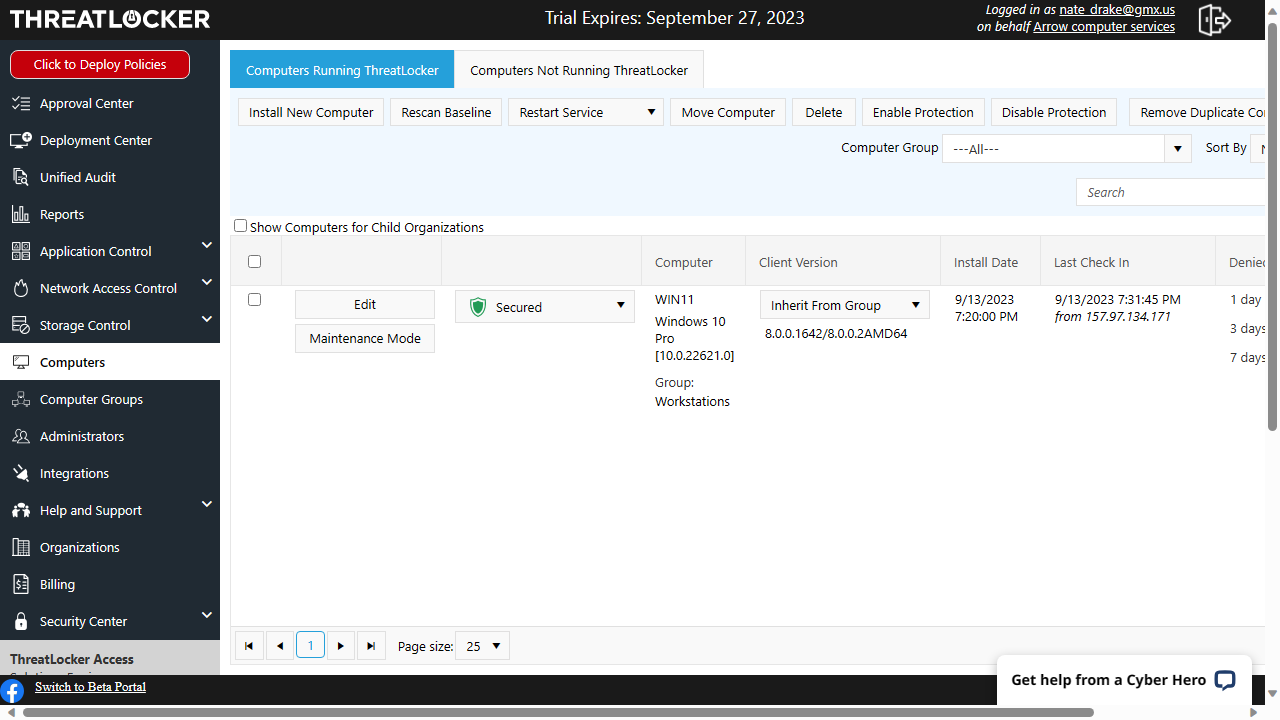
As impressed as we were by the vast array of features available, we couldn't help but feel the main interface is a little spartan. At times it feels more like editing a database rather than editing an online portal.
That said, the left hand pane is logically laid out and it's easy to expand sections to see further options. For instance, expanding 'Application Control' lists clear choices like 'Policies', 'Permitted Applications', 'Applications' and 'Tags'.
We felt the interface was most wanting in terms of the main dashboard - or lack thereof. Unlike other endpoint security platforms we've reviewed there's no area where you can see a quick heads up of device status, threats blocked and so on, accompanied by some helpful pie charts and other infographics.
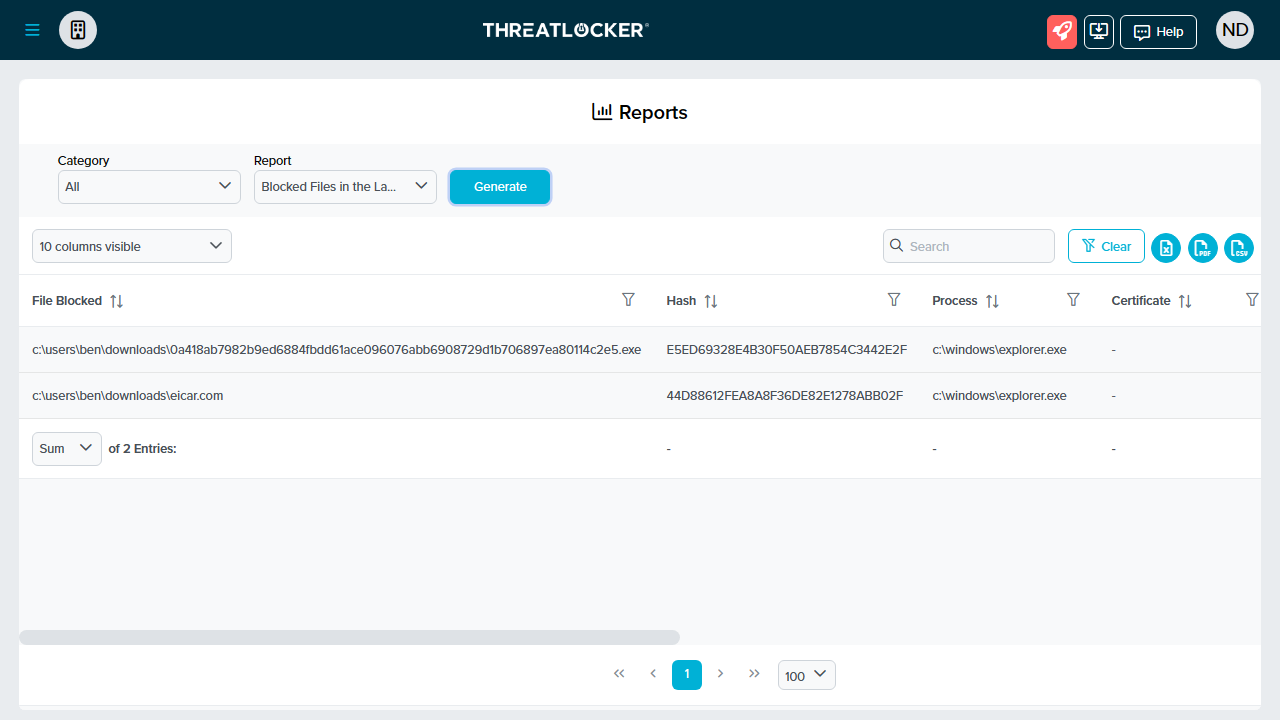
The report generating feature allows you to summon any amount of data e.g. Blocked Files in the last 24 hours but these appear in a spreadsheet-like format, so you may have to do some click and dragging in order to view all the information.
Having trashed the interface for being a little too Nineties, we should draw readers' attention to Threatlocker's new 'Beta' portal, which has a much richer UI. There's still no handy dashboard per se but options are much more colorful and text is better laid out. The left hand pane has also been axed in favor of a drop down menu which users can launch from the top left.
Sadly the Threatlocker Agent has yet to get the 'Beta treatment' so if, for instance, you want to view blocked files you're stuck with the spreadsheet-style layout again.
Threatlocker: Performance
Despite our misgivings about the Threatlocker's current UI, what it lacks in looks it more than makes up for in functionality.
When reviewing endpoint security solutions, our first step is always to try to download a fake computer virus, provided by the good people of EICAR. We opened Microsoft Edge on our test machine and downloaded the fake virus in compressed (ZIP) format.
On our first attempt, we found we were unable to extract the file as the permissions had been changed. We decided to be cunning and downloaded the test virus uncompressed and tried to run it. We immediately saw a pop-up from the Threatlocker Agent to say the file had been blocked from executing. Interestingly, the agent does include a 'Request Access' option, which may be useful if an endpoint user wants to request permission to run a legitimate program.
Our next test was to try to copy a new, real computer virus we'd caught in the wild to the test machine's 'Downloads' folder, to see how Threatlocker would react. We do this test to check if an endpoint security platform can detect suspicious files based on their behavior, not just by checking their signature against a known database of threats.
Once again, Threatlocker didn't let us down, immediately detecting and quarantining the real trojan virus.
Our final test is always to log in to the cloud console of an endpoint security platform, to check if the threats had been correctly logged. We decided to use Threatlocker's beta cloud console to list these, and were pleased to see that the full file names were displayed without any fine tuning via the mouse.
Threatlocker: Final verdict
A bare-bones interface is a small price to pay for a platform as powerful and as versatile as Threatlocker. While its creators aren't always mentioned in the same breath as long-established cybersecurity vendors like Malwarebytes, we were pleased how easy it was to register and try out the platform. We also were delighted with the level of support offered to help users with onboarding and defining policies.
Security-wise, while a dedicated firewall would have been ideal this is effectively made up for by fine tuned application control, as well as dynamic network control. We were particularly impressed that the platform takes port control seriously.
Threat detection was absolutely flawless, with both the fake and real virus being spotted and quarantined within moments. We would have appreciated a more graphically-rich agent but imagine this will get an overhaul in future, along with the introduction of Threalocker's new beta portal.
The only major criticism of the platform is that if you employ Threatlocker to protect your endpoints, you'll need to find another solution for mobile devices as the platform doesn't seem to support it. We did find, however, that there's a Threatlocker mobile app available for IT Administrators who want to manage endpoints from an Android or iOS devices.
Nate Drake is a tech journalist specializing in cybersecurity and retro tech. He broke out from his cubicle at Apple 6 years ago and now spends his days sipping Earl Grey tea & writing elegant copy.