Why you can trust TechRadar
Setup
CUJO can be very challenging to set up, even for network geeks. Note that it may not even be possible to use with all hardware setups, so it's important to dig into the detail before you buy.
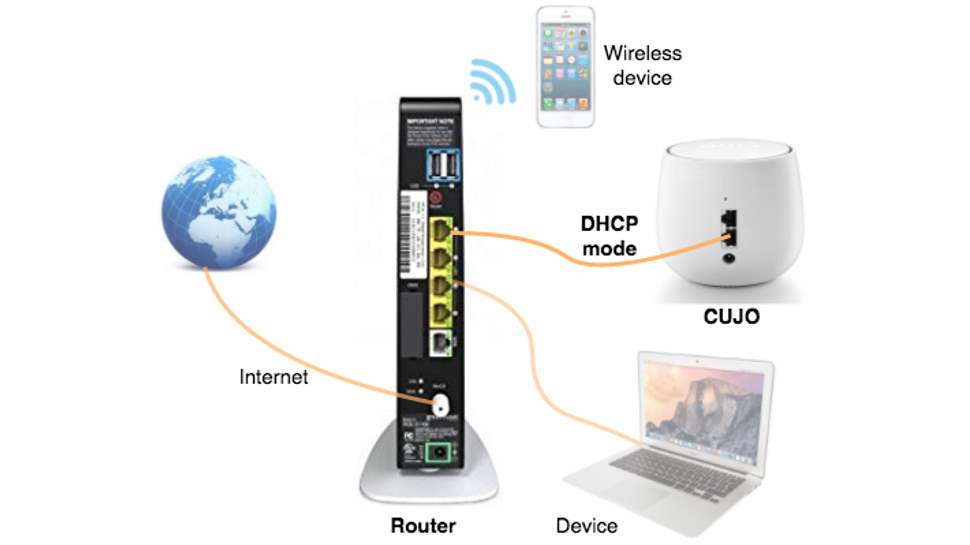
You have two main options. The first, 'DHCP Mode', can seem the simplest. Connect CUJO to your normal router, change your network settings to use CUJO as a gateway, and everything currently using your network connection will automatically be protected.
In some cases, CUJO can set this up for you. Download the iOS or Android app, give the setup wizard your router credentials and it will try to update your DHCP settings. If this works, great bash you're up and running right away.
Unfortunately, CUJO is only able to configure router models it knows about. Often you'll be told it doesn't know enough about your hardware to do this, and you're left to update the settings yourself. The app gives a list of items to change – IP addresses, DHCP leases – but it can't tell you how to find those options in your router.
There is some support available on the website. Check out this page for a list of compatible and incompatible routers, for instance.
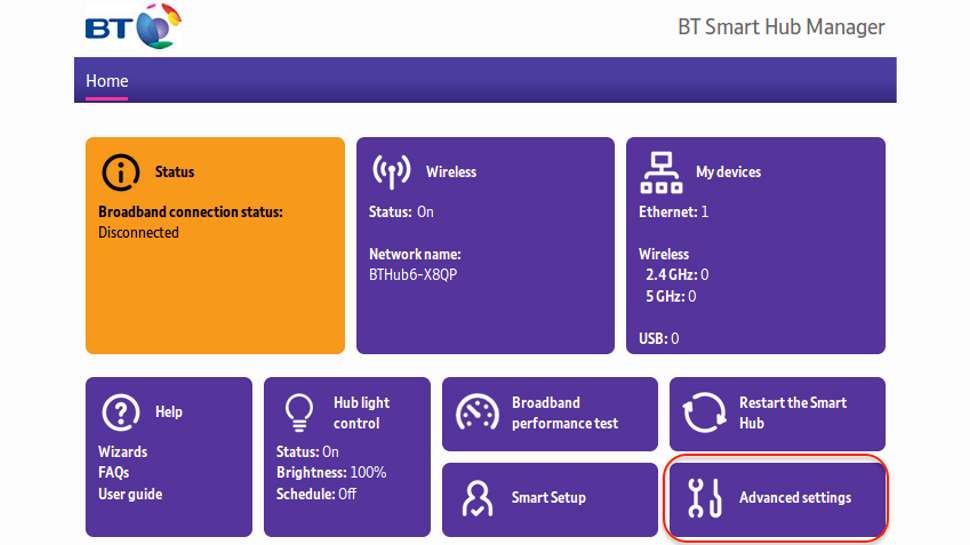
Life can become complicated, though, especially if the CUJO app doesn't support your router. This page on 'CUJO Modes' won't appeal to the technical novice, and as we write, the most useful-sounding link – 'Please refer to this manual to disable DHCP Server on your Router' – is broken.
That's less than helpful, but if you keep looking, you will find specific instructions elsewhere. For example, BT Home Hub is covered on this page.
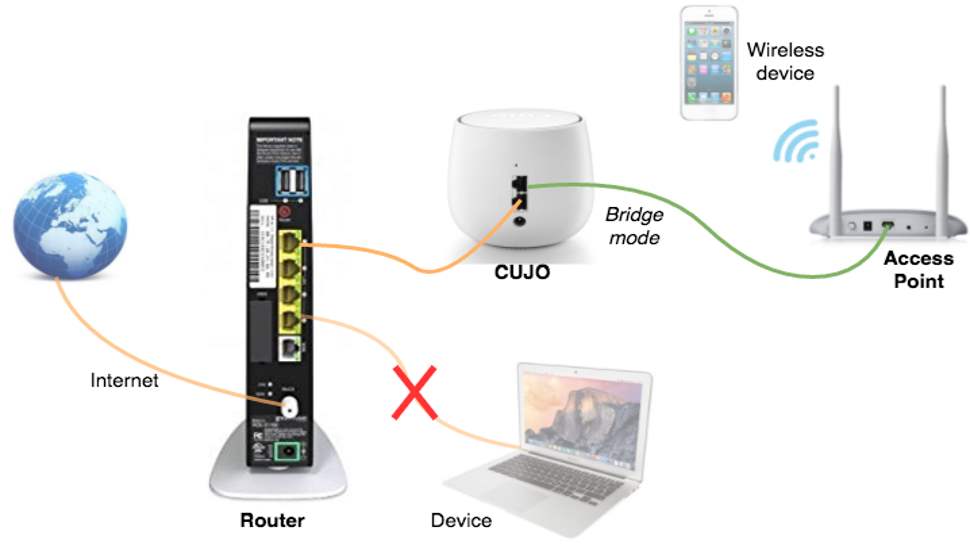
The second option is to use 'Bridge Mode', which requires two routers. Your internet connection comes in to router A; this connects by cable to CUJO; a second cable goes from CUJO to router B; all your devices must also connect via router B to be protected.
Not everyone has two routers available, of course. Even if you do, you'll still need to disable DHCP on router B, so you're not escaping the technicalities. And some routers may not allow DHCP settings to be changed, in which case you won't be able to use CUJO at all.
To be fair, you aren't left all on your own – far from it. CUJO's tech support team is available via email and phone (US and UK). They're so eager to help that we had a phone call soon after signing up. We also had multiple emails offering help and pointing us to web tutorials, and we've seen many positive reviews about the time the company has spent helping people get set up. We suspect that the large majority of users will be able to get CUJO running, but there's a good chance it will be more complicated than they expected.
Performance
Once CUJO is up and running, you can carry on using your devices as normal. Your traffic is filtered through CUJO, analyzed, and any threats blocked, but generally everything should work much as it always did.
If anything dangerous appears, CUJO's apps register the threat and display a notification telling you more. You'll also be warned on your local device in some situations, perhaps if access is blocked to a phishing site. That will probably be enough, most of the time, but we're a little concerned that there's no browser management interface. If your phone breaks or goes missing, you won't be able to check up on your CUJO or manage what it's doing.
One small advantage to using CUJO is it gives you basic parental controls. You can create a profile, define the types of website you'd like to block (adult, shopping, social media), optionally add some safe sites to a whitelist, then apply those settings to a device. Simple reports show you any violations when you review them later on.
This might be useful in a few situations, although there are some major limitations. In particular, the rules are being enforced at the network level rather than the device, so if your kid takes his tablet to a friend's house, he'll be able to do whatever he likes.
The CUJO website also says the parental controls feature helps you "avoid inappropriate apps", "manage access schedules" and "set time limits", but we didn't see any of those in our Android app. The parental controls feature was flagged as a beta, so it's possible they'll be added later, but when they're trumpeted on the website we'd say you're entitled to expect them now.
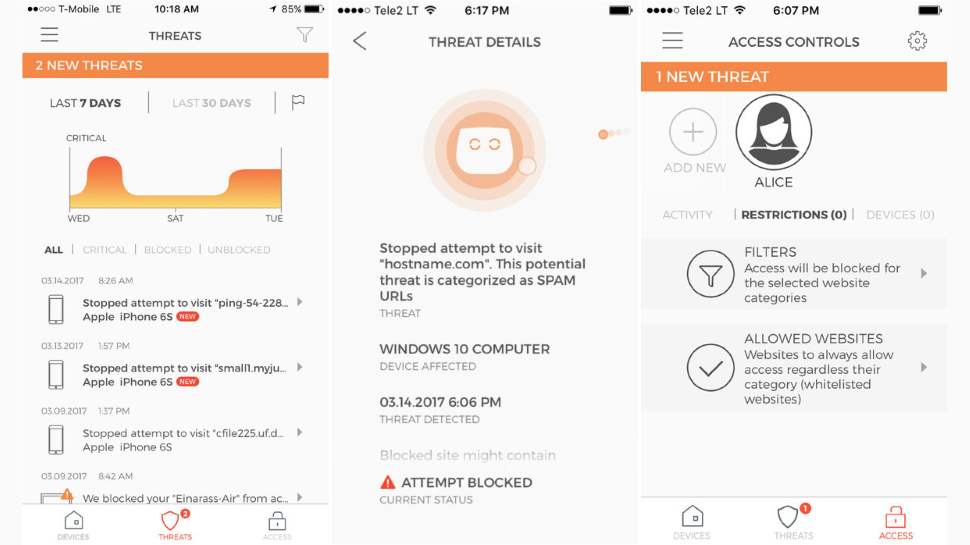
Elsewhere, the CUJO apps provide simple lists of the devices connected to your network. These show details like device type, manufacturer, IP address, MAC address and more. You could use this to spot unusual devices which connect to your network only occasionally, and when they were last seen.
Demanding network users might run into difficulty with more advanced requirements, such as setting up port forwarding. It's possible, but not necessarily straightforward, and we've seen some users complaining of problems.
If your network needs are mostly about local file and device sharing, though, it's a different story, and most users will find their CUJO-protected home works much as it always did.
Final verdict
CUJO seems like a great idea: a neat-looking box you can place in your home, which protects all your smart devices without you having to do anything at all.
Unfortunately, getting to this point might take a while. Setup can be complicated, you may need to reconfigure your network, and advanced tasks like port forwarding could become more difficult.
There's a distinct shortage of technical detail about CUJO's features, too. It protects you from malware by blocking access to command and control servers, for instance, but what other sites are included? Where are these addresses sourced from? How often are they updated, and how large is the database? There's very little information available, which makes it difficult to assess how effective the protection might be.
Overall, CUJO feels like it's caught between two audiences – it’s too complicated for beginners, too underpowered for experts. It could still be useful if you have lots of smart devices to protect, but be sure to check your setup is compatible before you buy.
- Also check out the best VPN

Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided. Mike began his career as a lead software developer in the engineering world, where his creations were used by big-name companies from Rolls Royce to British Nuclear Fuels and British Aerospace. The early PC viruses caught Mike's attention, and he developed an interest in analyzing malware, and learning the low-level technical details of how Windows and network security work under the hood.
