TechRadar Verdict
A well-rounded endpoint security solution that covers all the popular desktop and smartphone operating systems. Furthermore, it backs its extensive platform coverage with an impressive interface that includes several administration conveniences, which makes it a good option for all kinds of networks.
Pros
- +
Remote deployment
- +
Useful tools
- +
Easy to manage and administer
- +
Can be deployed on-premise
Cons
- -
Limited control over Linux endpoints
Why you can trust TechRadar
ESET’s endpoint protection software is pitched at small and medium-sized businesses and combines the protection of the company’s popular antivirus solution along with its security product.
ESET Protect Advanced covers Windows, and macOS, and with certain conditions also extends to Linux, Android and iOS endpoints as well.
ESET PROTECT: Features
The antivirus bit of the solution uses heuristics and machine learning to protect against zero-day attacks and malware. It’ll also protect you against fileless malware thanks to the bundled mitigations that’ll detect any hijacked applications.
In fact, ESET monitors and evaluates all executed applications on the endpoints and based on their reputation and behavior will block any processes that act like ransomware. It keeps an eye on typically exploitable applications such as browsers, document readers, email clients, Flash, Java, and such, to look for identifiable exploitation techniques.
One of its interesting protection features is its ability to monitor the integrity and security of the UEFI firmware and the preboot environment. In addition to scanning the computer, ESET also has web access and email client protections to catch and block malicious downloads, harmful webpages, and purge spam from emails.
The security product brings with it a software firewall, the ability to detect malicious communications over the Internet and then block the offending process that initiated it. You also get a Host-based Intrusion Prevention System (HIPS) that uses a predefined set of rules to identify and stop dubious behavior.
The endpoint bundle also includes the File Security product for Windows Servers and Microsoft Azure that can scan and monitor connected cloud storage and VMs.
By default the cloud console enables 'ESET LiveGuard' on new and existing devices. If you choose to enable ESET's recommend 'Optimal' setting then any document types that support macros will automatically sent to a secure ESET server for scanning and access will be limited until they're confirmed as safe. This could cause network slowdown if your organization regularly works with huge amounts of data like this, but luckily there's also a 'basic' option which only scans a limited number of files. ESET notes this is a particularly useful tool when it comes to preventing Ransomware from gaining a foothold on devices.
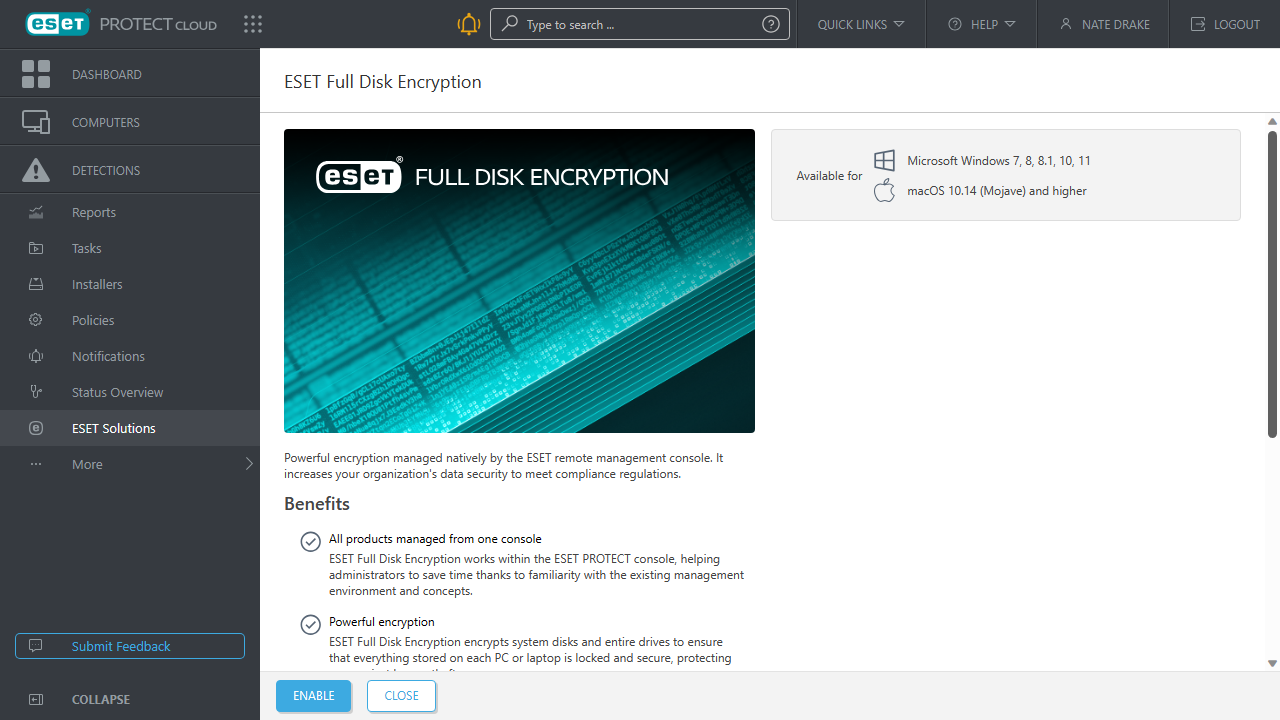
If you choose to create an installer for your device via the cloud management console (see below), you can configure it to support 'Full Disk Encryption', though you'll need to purchase a separate license for each device you want to encrypt.
One advantage of this is that admins can deploy full disk encryption on devices, disks and partitions from Cloud Administrator console. This could be helpful if your organization needs to secure data consistently across multiple devices to be compliant with data protection laws like GDPR.
While the smartphone clients also have the antivirus features that you get with the desktop, their security features differ. On Android and iOS devices you get application control and device security features as well as anti-theft features, such as the ability to remotely lock the device, or wipe it in case it is stolen.
ESET PROTECT: Interface and use
All of these features are accessible and can be tweaked from the endpoint clients or from the smartphone clients installed on the individual devices.
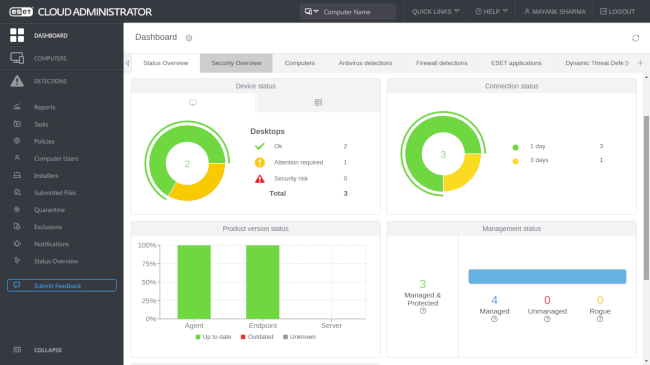
The cloud interface on the other hand, helps you deploy endpoints, rollout specific tasks to them, and get notifications and reports about incidents.
It contains several dashboards that help visualize different aspects of the network. There’s one that gives you an overview of the security incidents, another specifically for virus detections, another for events blocked by the firewall, and more. You can drill down each one of them to oversee the status of computers, along with the threats or quarantined items.
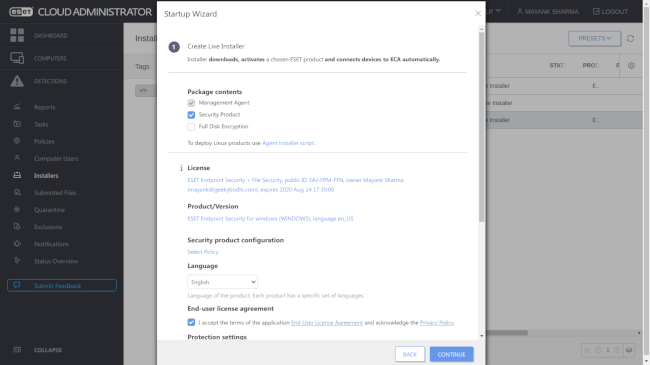
But first you’ll have to deploy the ESET agent to the endpoints. For this, you’ll have to create a small installer. The process for creating the installer allows for some customizations such as the ESET endpoint security product. This enables you to create multiple installers for a different set of machines. For instance, you can create separate installers for Windows and Macs.
The installer will anchor the selected ESET security product on the endpoint, activate the valid license and automatically connect to the cloud interface. You can either directly download the installer or send a link to it via email.
One advantage of having a cloud interface is that you can log in and remotely manage your endpoints from any device.
If, however, you want to install the endpoint client on devices, you'll need to be using Windows 7 onwards for PC's. ESET cautions that if you're using Windows with an ARM CPU, certain features like the Secure Browser aren't supported.
The client has no such problem with ARM-based Apple Macs, as it's compatible with all versions of macOS from version 10.12 onwards.
The mobile versions of the client will work with any Android Device running version 5 (Lollipop) of the OS or later. Apple mobile devices running iOS 9 onwards are also compatible.
Unlike many endpoint protection platforms ESET does actually offer a client for Linux. The installer supports Ubuntu 18.04 and RHEL Desktop 7 and their derivatives, which covers most modern Linux distributions. There's no support for some more advanced features like Full Disk Encryption but most versions of Linux already offer this option during install.
Best of all, there’s also a remote deployment tool that can remotely deploy the installers to all the endpoints in your network. The remote deployment tool can sync with an active directory server or can scan and map all the endpoints in your network.
The two best administration features of ESET’s cloud-based interface are policies and tasks. Think of policies as predefined configurations that you can push to the endpoints to get them up and running quickly.
For instance there are policies to block access to all devices, another to only allow reads, another to log all warnings and critical events, and so on. You can also create custom policies. A policy can be applied to individual computers or can be rolled out to a group of computers and a computer can have multiple policies as well.
Then there are tasks, which are predefined commands to conduct some of the most common operations. For instance, there’s a task to perform diagnostics on the endpoints, run a scan, update the different ESET modules, isolate a computer from the network, and more. You can also create custom tasks.
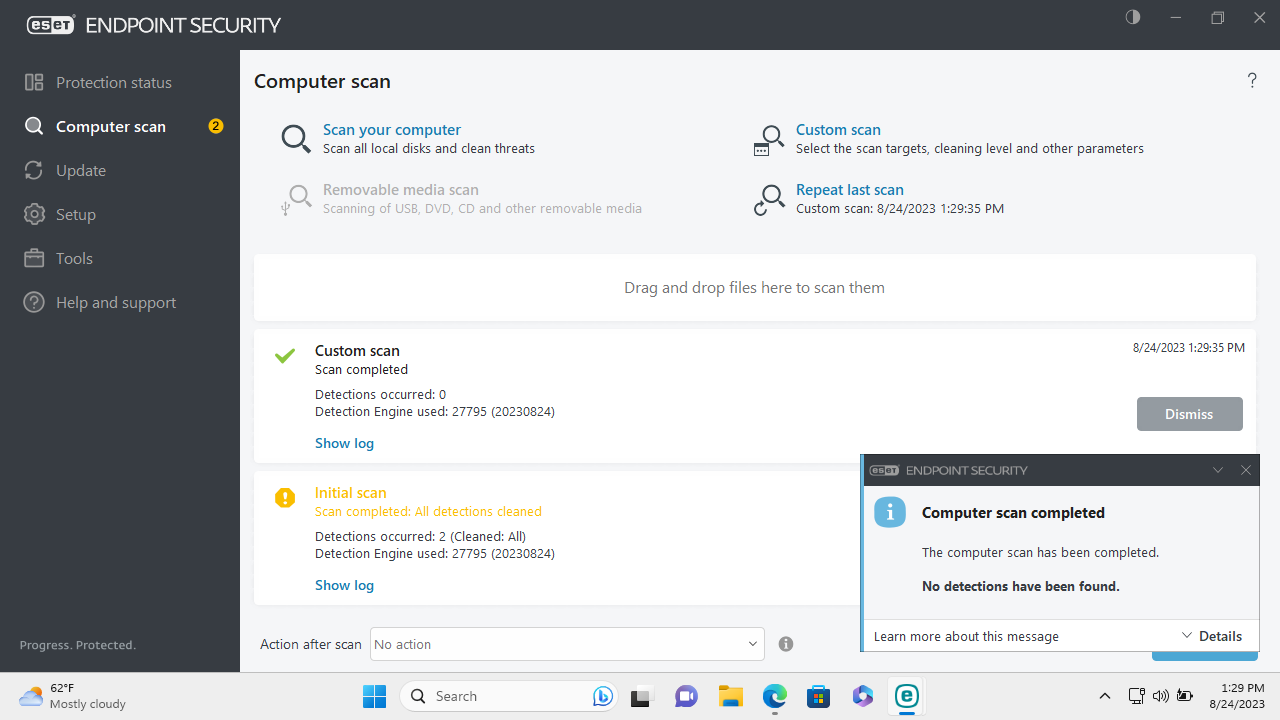
Once a task has been created you can then schedule and execute it as per a defined trigger. The task can be executed as soon as the endpoint receives the task from the cloud interface, or at a selected time.
Finally, like all good enterprise software, ESET Endpoint bundle can also create all kinds of reports to visualize the network status. These reports can be printed or shared in digital form.
ESET PROTECT: Performance
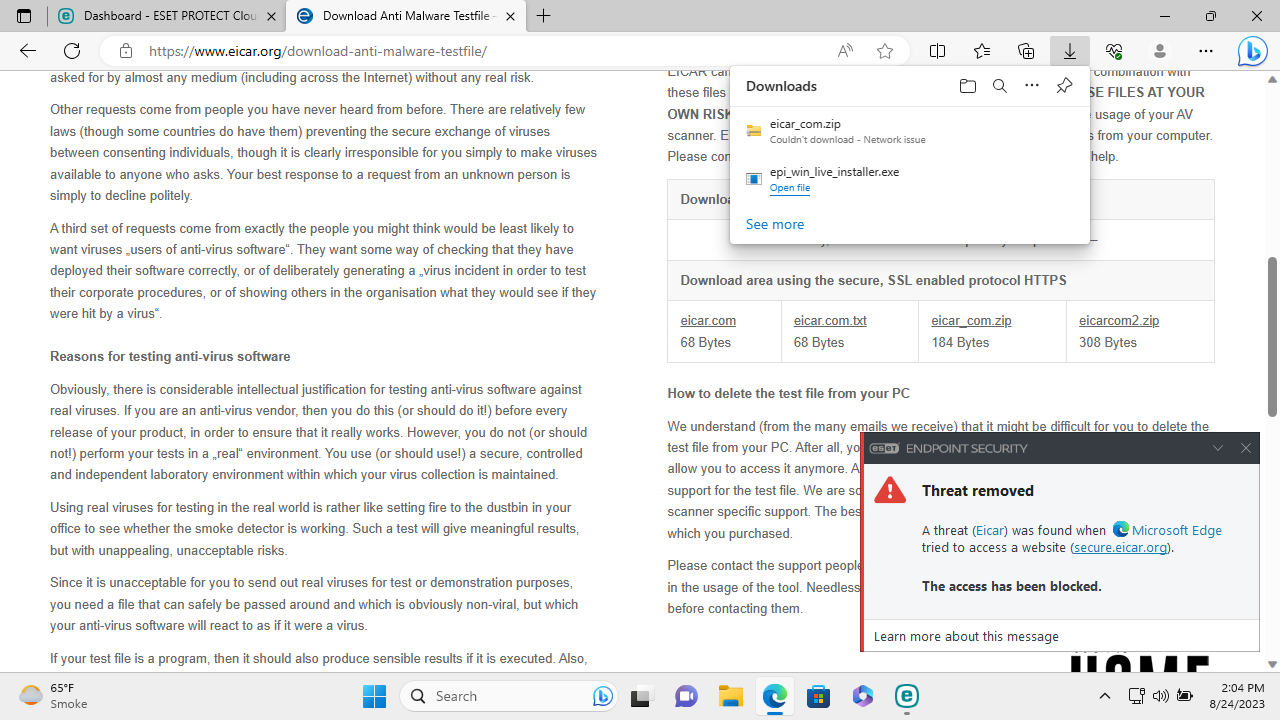
After creating an 'Eset Package Installer' for our Windows 11 virtual machine, we were impressed to see that the endpoint client immediately started updating itself to detect the most recent threats. It then immediately began running an initial scan.
The scan failed to detect any threats, even though we'd placed a zipped test virus file (provided by the good people of EICAR), directly on the desktop. We had more joy when we tried to decompress the test virus however, as the client immediately detected the threat and quarantined it before it could be run.
When we tried to redownload the ZIP file with the virus using Microsoft Edge, the client also blocked the download automatically.
We noted that by default, both the Secure Browser and 'Web Control' (which blocks access to potentially unsafe websites) are disabled. After enabling Web Control, we tried to visit file sharing site 'The Pirate Bay' and search for (legal) downloads of Ubuntu Linux. We found that while we could search for torrent files, Edge was blocked from displaying details on files.
We were curious to see what happened when deploying the secure browser, so enabled this too. After a mandatory restart of the PC, we opened the Secure Browser to find what seemed to be Microsoft Edge.
On further examination of ESET's Support Pages, we discovered the following statement:
"When you open ESET Secure Browser directly from the Tools tab in the product menu, ESET Secure Browser is opened in the web browser that you set as default. Otherwise, when you open your preferred web browser , the ESET internal list will be redirected to the same type of web browser secured by ESET."
It's not clear exactly what additional protection this would provide if a user clicked on a harmful link, nor does a 'browser within a browser' seem necessary if you already have 'Web Control' enabled. We ran our tests with the Pirate Bay within the 'Secure Browser' with the same results as before.
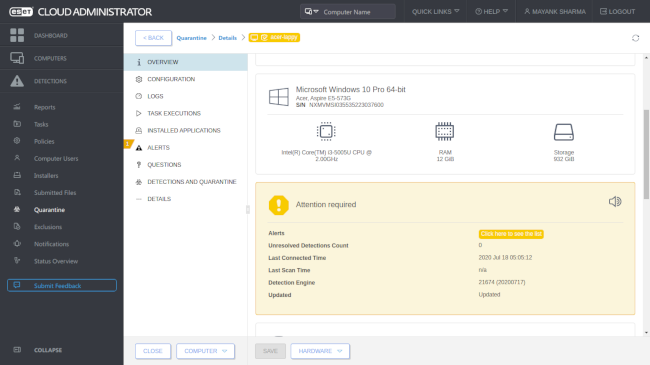
The only curiosity was when we logged into the ESET cloud console after running these tests, the Dashboard reported no security risks. Admittedly this was true given that the client had detected and blocked threats before they occurred but we think this should have been flagged.
A quick visit to the 'Detections' section however displayed all 3 security alerts triggered by the test virus, providing helpful information about the circumstances in which they occurred.
ESET PROTECT: Plans and Pricing
At the time of our last review in 2020, ESET's pricing model was a little convoluted. as Endpoint bundles could be managed with either the cloud-based interface or an on-premise one for different prices.
There are now four main tiers, all of which can be managed via a console either based in the cloud or on premises. The choice is now down to users.
ESET Protect Entry is the most basic tier. It includes the aforementioned cloud/on premises console, as well as 'Modern' Endpoint Protection and real time protection for data passing through your organization's servers.
If you want to find more about what these (or indeed any other) features entail, the ESET Business Products page contains a list of helpful hyperlinks for each, providing a detailed overview of what's included. Prices start at $211 for up to five devices for one year.
ESET Protect Advanced (which is the subject of this review), includes all of the above features in the 'Entry' tier, as well as 'Advanced Threat Defense', which can use cloud-based sandboxing and machine learning to detect and test for potential threats. This tier also offers Full Disk Encryption, though ESET's pricing page seems to suggest you also have to pay for extra licenses to set this up on each device. Prices start from $220 for up to five devices for one year.
ESET 'Protect Complete' is the company's most recommended plan and there's currently a special offer saving customers 20%. Prices start at $270.80 for up to five devices per year. This tier includes more advanced protection for Microsoft 365 apps, along with a dedicated consoles. Subscribers also benefit from tools to scan mail servers to prevent threats from reaching users' inboxes, as well as active tracking and patching of vulnerable endpoints.
The ESET 'Protect Elite' plan is for 26 devices and upwards, with prices only available on request. It includes the same features as all the above tiers, as well as detection and response and multi-factor authentication, which are only available as a purchaseable extra for the other pricing plans.
ESET also offer a number of extras you can purchase on behalf or your organization such as CyberSecurity Awareness Training, email protection and advanced protection for Microsoft Office 365 and Sharepoint.
Further discounts are available for all plans if you're willing to pay in advanced for longer subscriptions for 2 or 3 years. You can also trial all products for free for 30 days without providing credit card information, provided you register an online account with ESET.
ESET PROTECT: The competition
Perhaps the biggest advantage the ESET endpoint bundle offers over its peers is that it offers both cloud-based and on-premise management consoles.
As a security product though, like most of its peers, besides hunting for malicious files on the computers, it also protects your web browsing and monitors connected devices as well.
Admittedly it doesn't come with its own VPN as with similar products such as Avira Prime for Business. It also doesn't have a standalone 'secure browser' but this has dubious security value in any case as it's difficult to persuade workers in your organizations to switch from their usual browser. This is where ESET's "Web Control" shines, as it can provide protection for the endpoint's default browser.
Also, its user-interface offers the same kind of dexterity that you get with Bitdefender GravityZone Advanced Business Security (GZABS) without any of the complexity. Although it doesn’t ship with an administrator’s guide, the contextual help and the tooltips make easy work of navigating the interface.
When we first logged into the cloud console, we were introduced to its main features through the 'ESET Protect Tour', which explained the ins and outs of the Dashboard, as well as the sections for Computers, Detections, Tasks, Policies, Notifications and Updates.
ESET PROTECT: Final verdict
ESET PROTECT offers an impressive set of security features that are nicely complimented by its deployment and remote management functionalities.
Despite the fact that most of its remote administration features cover only Windows and macOS, it still doesn’t leave your Linux endpoints completely in the lurch, which is a definite plus. Its coverage of both Android and iOS devices makes it one of the most complete endpoint security platforms.
We are not knocking off points for the lack of a secure 'standalone browser', as the 'Web Control' feature more than makes up for this without users on your endpoint devices having to change their default web browser.
The ability to manage Full Disk Encryption of devices, as well as remote wipe of mobile devices will also be welcome news to organizations who handle sensitive data.
We were especially impressed by ESET's Protect Advanced's ability to immediately quarantine malware as soon as it was detected, whether this was from unpacking a compressed virus or when trying to download a harmful file directly within the browser.
We feature the best business laptops.
With almost two decades of writing and reporting on Linux, Mayank Sharma would like everyone to think he’s TechRadar Pro’s expert on the topic. Of course, he’s just as interested in other computing topics, particularly cybersecurity, cloud, containers, and coding.