TechRadar Verdict
McAfee's app blocks some real-world threats, but we're unsure how reliable Interceptor's protection might be overall.
Pros
- +
Blocks real-world ransomware
- +
Lightweight
- +
Unlikely to conflict with other antivirus
- +
No-strings attached free
Cons
- -
Not updated since May 2017
- -
Didn't block simulated attacks
- -
Barely any configuration options
- -
Not supported by McAfee
Why you can trust TechRadar
Silent, deadly and constantly evolving, ransomware is never far from the headlines. You might expect McAfee to want to boast about its free McAfee Ransomware Interceptor, then, but instead it's buried deep in the security company's website.
One reason could be that the Interceptor is still listed as a 'pilot', more of an experimental anti-ransomware tool than a full-strength product. There doesn't seem to be much experimenting going on, either, as the last update at the time of writing was May 18, 2017.
The official Interceptor FAQ page points out another problem: Interceptor isn't covered by McAfee's technical support. If you have any issues, you could be on your own.
This doesn't necessarily mean Interceptor has no value. The website explains that it "leverages heuristics and machine learning" to identify threats, rather than using simple signatures, which could allow the program to block even brand new and undiscovered threats.
A second advantage is this kind of behavior monitoring approach doesn't normally conflict with other antivirus tools, allowing you to run Interceptor alongside almost anything to add an extra layer of ransomware protection. Perhaps it's a little out-of-date, and maybe Interceptor only detects a few extra threats, but the program is unlikely to cause any trouble and could make you a little safer overall.
That's the best case scenario, anyway, but does Interceptor really have what it takes to identify ransomware from its behavior alone? We would have to download and install the program to find out more.
Setup
McAfee Ransomware Interceptor is free for anyone to use, with no registration or other hassles required. Visit the website, choose the 32 or 64-bit version, read the license and you can download the program with a click.
The installer is a very compact 3.3MB, which is probably why the setup process appeared very simple, with absolutely no settings or options to consider. We were briefly concerned when a command window appeared and the installation seemed to pause, with nothing at all happening for more than a minute. But then the window disappeared, the installer advised us to reboot our test system, and closed normally.
Despite the tiny setup program, Ransomware Interceptor had taken up a fair chunk of disk space. Most of this was the 310MB occupied by McAfee's core management framework, though; the main program files took barely 17MB.
The package was much lighter in terms of RAM use, with its three background processes taking barely 11MB between them under normal circumstances, and no significant CPU time. This probably isn't going to be a product which slows you down.
Malware will sometimes try to detect and disable security tools by closing processes, deleting files or Registry keys. This can be surprisingly easy – we've seen some antivirus packages which can be killed from a batch file – and so we always check how well security software can protect its own code.
The results didn't impress, at least initially, when we discovered an attacker with Admin privileges could delete most of McAfee's management framework.
Of course, to be fair, if malicious code is running on your system with admin rights, then you're already in big trouble. And although we managed to cause some damage, McAfee's SystemCore support files remained available, and Interceptor continued to run as normal.
There's little sign of Interceptor's activities, as the program has no real interface beyond a single system tray icon, which contains just three management tools. We could toggle protection on and off, whitelist a trusted program to prevent it being blocked in future, or view a detection log to see what Interceptor had done.
You don't get any significant control of how the package works, then, as is the case with some of the competition. Whitelisting programs or turning Interceptor off are your only options.
Despite its extremely basic interface, we also noticed a minor deficiency. Right now, Interceptor displays the same system tray icon whether it's active or not, and the only way you can see its status is to right click the icon and check its menu. We would prefer to see the icon change – to perhaps green for active, red for inactive – allowing you to see Interceptor's status at a glance.
Performance
Testing behavior-based anti-ransomware software is always difficult. Their value is in the claim that they can detect malware which doesn't exist yet, but that's hard to assess unless you have wide access to the very latest threats.
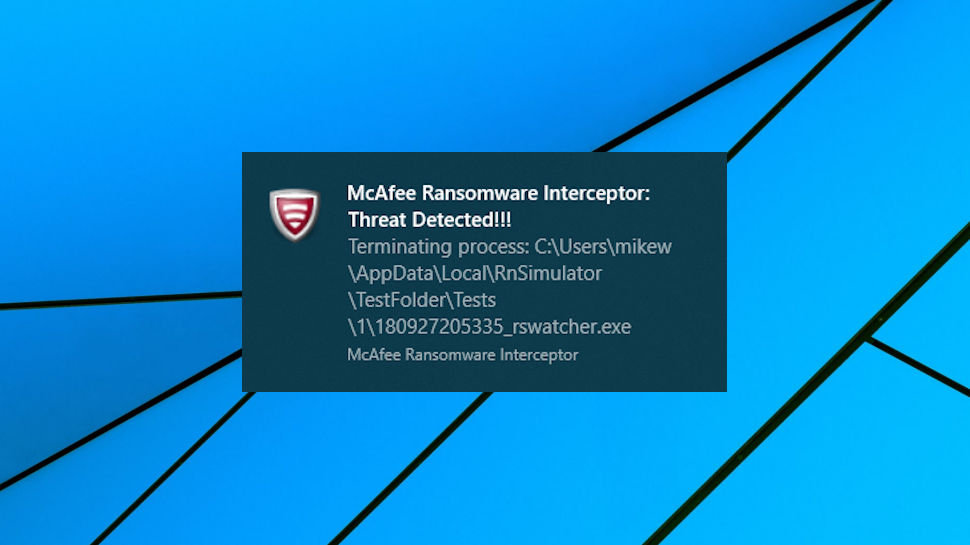
We started with a simpler approach, testing Interceptor against Cerber, a known ransomware strain. The results were excellent, with Interceptor blocking the Cerber process before it could encrypt a single file, and displaying an alert. That's no surprise – we would expect McAfee to have designed Interceptor to look for threats like Cerber – but it does show the program is offering some useful protection.
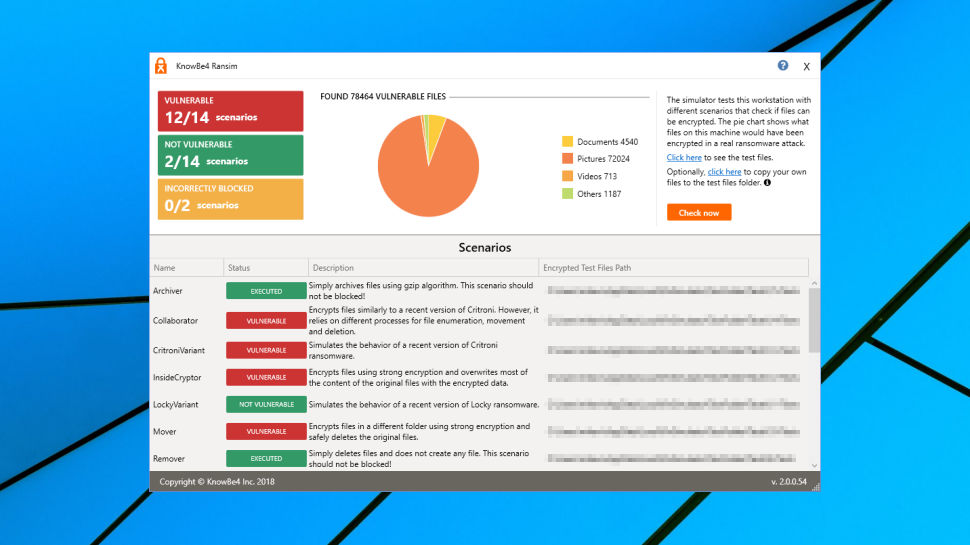
Next, we turned to RanSim, KnowBe4's free ransomware simulator. This runs various tests using different types of ransomware-like behavior, and tells you which have been blocked.
The last time we looked at Interceptor, it failed to detect any of RanSim's 14 attack scenarios. This test showed some improvement, with two attacks being blocked, but we were still vulnerable to the other 12 scenarios. This isn't as alarming as it sounds – all scenarios aren't equal, and it's entirely possible that Interceptor's two detections would be enough to block most real-world ransomware – but we've seen other security tools score higher.
Finally, we turned to a very simple ransomware simulator of our own. It's far more basic than RanSim, with just a single mode of attack, spidering through a test set of folders, detecting and encrypting many common document types. But as it has never been released, we know it's something the McAfee Ransomware Interceptor developers won't have seen before, making it an interesting test of Interceptor's behavior monitoring and heuristics.
Unfortunately, it was a test which Interceptor comprehensively failed. Our simulator was allowed to run to completion, and successfully encrypted every user document and file in our test tree.
We need to interpret these results with care. RanSim may use ransomware-like actions, but it only worked on its own sample files, leaving ours untouched. Interceptor arguably made the right decision by allowing it to run.
We think RanTest is probably the more significant failure, as it was able to encrypt thousands of real files on our test system. It's not real ransomware and only spidered through a single test tree, so it's possible the program didn't meet Interceptor's threshold for detection.
But other antivirus and anti-ransomware tools generally block our simulator right away, with for example Kaspersky Antivirus 2019 not only spotting the threat and killing the process, but also recovering the handful of files it had managed to encrypt before being stopped.
Interceptor still deserves major credit for blocking real-world ransomware, and that is the test which matters most. The program largely failed with our simulated threats, but it may still improve your security, and do so without causing conflicts with other security apps.
Final verdict
Ransomware Interceptor is simple, ultra-lightweight and blocks real-world ransomware without difficulty. It's not as effective with simulated threats as the top antivirus engines, but could still be worth installing as a second layer of security.
- We've also highlighted the best antivirus software in this roundup

Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided. Mike began his career as a lead software developer in the engineering world, where his creations were used by big-name companies from Rolls Royce to British Nuclear Fuels and British Aerospace. The early PC viruses caught Mike's attention, and he developed an interest in analyzing malware, and learning the low-level technical details of how Windows and network security work under the hood.