TechRadar Verdict
When it comes to features or price, very few can compete with WBEP. However, inconsistent performance and subpar threat reporting would make us think twice before deciding on this tool.
Pros
- +
Extensive protection features
- +
Resource efficient client
- +
Useful documentation
- +
Cheap
Cons
- -
No support for Linux and mobile devices
- -
Inconsistent performance
- -
Subpar threat reporting
Why you can trust TechRadar
The best business endpoint security protection needs to offer a comprehensive defense against all kinds of malware, while being both affordable and easy to use. Let’s see how Webroot Business Endpoint Protection (WBEP) fares and if we can place it among the best products in its class.
Webroot Business Endpoint Protection: Plans and pricing
WBEP can be purchased through a yearly subscription model. For up to nine endpoints, each one will cost $30. Adding more endpoints gets you a discount, so 10 and more cost $27.6 per endpoint. This makes WBEP one of the cheapest endpoint security solutions around.
Even more impressive, the prices haven’t changed since our original review in 2020.
Customers also have two additional features to add here - Webroot DNS protection, and Security Awareness Training. Both cost the same as endpoint protection, so choosing all three options effectively triples the total cost. That being said, Webroot DNS is a good way to filter out harmful links, and Security Awareness Training is one of those things that every cybersecurity professional roots for these days.
The good news is that there’s a free 30-day trial for all three features.

Webroot Business Endpoint Protection: Setup
Overall, the setup process has been smooth. First you register an account and get a temporary license code and password in the email. You also get a link to set a new password and a secondary ‘security code’. WebRoot will ask for two different characters from this each time you log in, and ask you to set up two factor authentication.
On first login, you can choose between the Business console (which we’re reviewing today) and the Managed Service Provider (MSP) console. After choosing the Business console, we were given a download link for the WebRoot 'SecureAnywhere' software, with the license key preloaded. That made installing it on a Windows 11 machine a breeze.
After installation, we saw Webroot's "Web Threat Shield" option in the Edge browser.
It’s also worth mentioning that the tool doesn’t need to be updated, since malware information is stored in the cloud and thus always up to date.
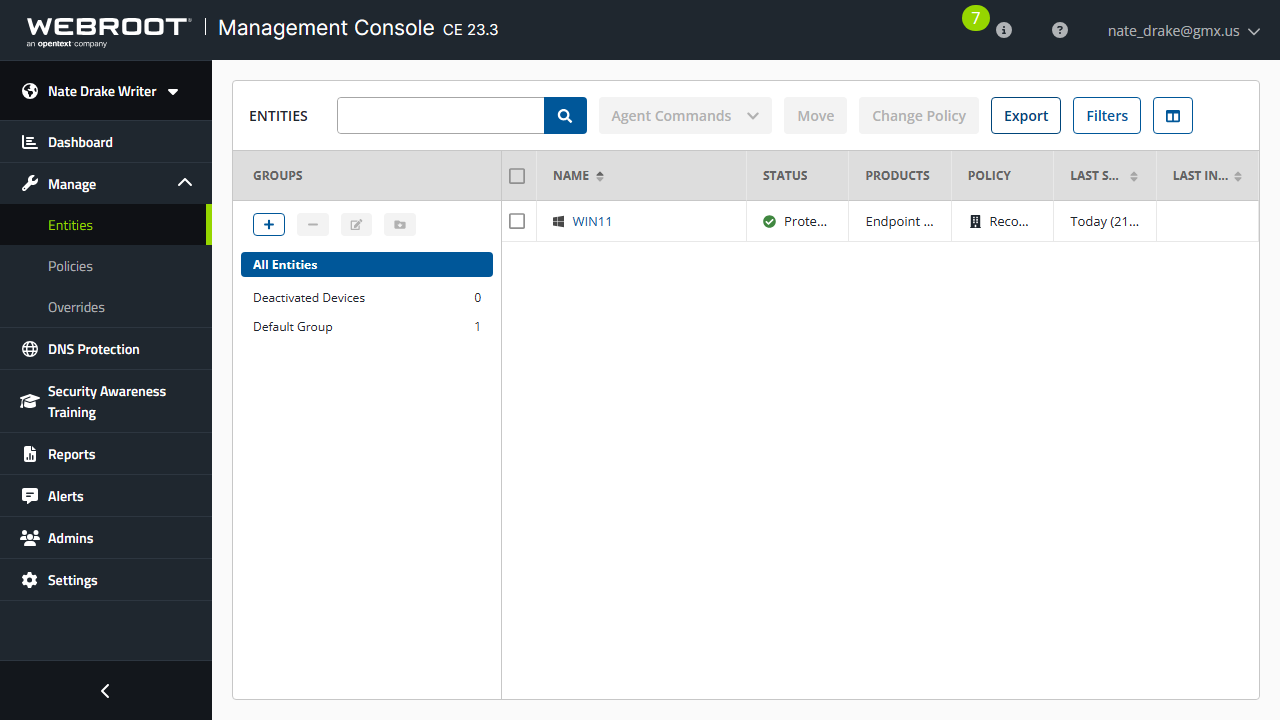
Webroot Business Endpoint Protection: Features
WBEP offers everything you’d need from an endpoint protection platform: defense against viruses, malware, trojans, ransomware, spyware, phishing attacks, browser-based attacks, cryptojacking, and all the other usual threats.
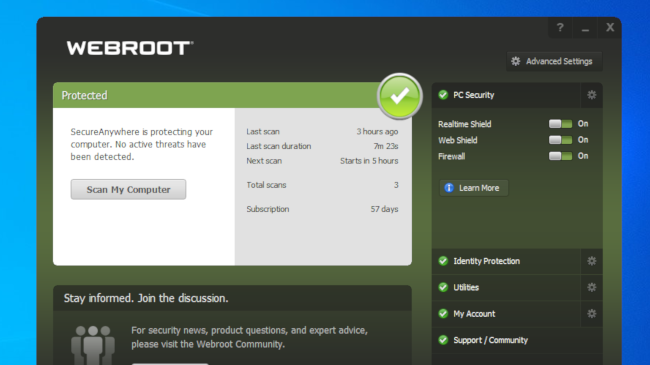
These features are presented as ‘shields’ - so you get a real-time shield, web shield, identity shield, phishing shield and others. Identity shield is quite useful since it helps protect sensitive data that may get exposed online. Another interesting feature is the behavior shield, which monitors individual user behavior and dynamically optimizes malware prevention. It also comes with different heuristics settings that help set the level of threat analysis.
There is also the evasion shield that helps detect and act against evasive script attacks, including malicious PowerShell, JavaScript, VBScript, and other code. One thing to keep in mind is that this one is off by default.
WBEP can also help you determine which applications are allowed to run. There is also a software firewall and a couple of other useful features to help you take charge of your endpoints.
Finally, each session is capped to half an hour, and after 28 minutes the user will be prompted to confirm if they want to keep the session alive. No response results in an automatic log-out.
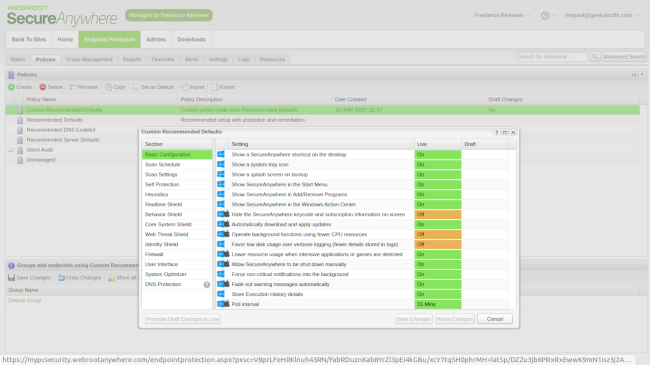
Webroot Business Endpoint Protection: Interface and use
WBEP comes with a number of different interfaces, including the Business interface (which we’re using), and the administration interface. The latter, unfortunately, leaves much to be desired. It isn’t logically arranged, and instead of clearly-labelled starting points, you’ll have to head to the last Downloads tab to install the WBEP agent on your endpoints.
As for workflow, all endpoints must subscribe to defined policies. While this allows for greater control over the behavior of individual endpoints, it’s not without its challenges. For starters, all WBEP endpoints are subscribed to the Silent Audit policy, which offers limited protection. We’d recommend switching the endpoints to the Recommended Defaults policy for maximum protection instead.
However, this one has a poll interval of 24 hours, meaning any scans or other actions can take up to a day to be communicated to the endpoint. Furthermore, the policy hides the platform’s resource-efficient endpoint agent. We can see this confusing users, especially first-timers, which is why we recommend going through the admin’s guide and best practices guide.
On the bright side, we loved the detailed infographics on endpoints that you can find in the dashboard, where information on infected endpoints and those who haven’t been seen recently can be found. We were especially impressed that the left hand pane can both display each section with sub-options but can also be minimized to a more compact version as users become more familiar with the icons.
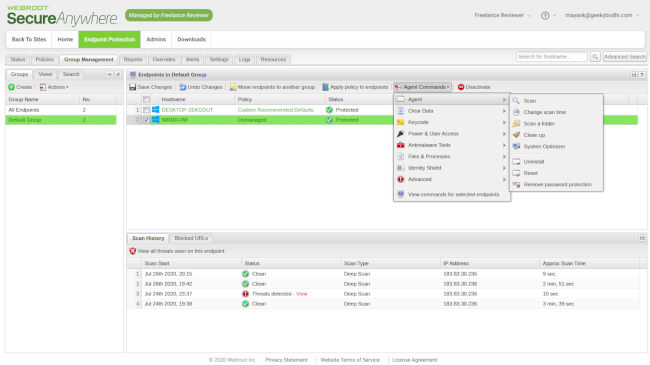
Webroot Business Endpoint Protection: Performance
We test most of our endpoint protection software the same way: we first try to download and run a fake computer virus, provided by EICAR. Then we try to do the same with an actual piece of malware. Finally, we check the logs to see if everything was nicely laid out.
Unfortunately, we were able to easily download the fake virus in a compressed (ZIP) format, and even extract it, without any alerts from the ‘Web Threat Shield’, "RealTime Shield", "Web Shield" or "Firewall". It was only when we opened the 'SecureAnywhere' agent software and manually ran a full system scan that the virus was removed.
While we can’t know for certain, we suspect this has something to do with the ‘Silent Audit’ policy which doesn’t seem to be very proactive about blocking threats.
Running an actual virus yielded better results. This time when we tried to decompress it, WebRoot's Endpoint Protection software automatically quarantined the threat and displayed an alert in the tray.
Finally, we opened the ‘Reports’ tab and found ‘No Threats’.
It's entirely possible that through careful configuration of the device policies and creating a custom installer that we could have created an agent which was more proactive in detecting, blocking and reporting a threat. However, we can't help but feel it would be better if this was available out of the box.
Webroot Business Endpoint Protection: Final verdict
Since our previous review in 2020, some things have changed, and others stayed the same - for better or worse. The interface was revamped, which was definitely a welcome sight. Prices remained the same, which we were also happy to see.
Test results were a mixed bag, however. The platform did not prevent us from downloading and decompressing the virus, but it did detect and quarantine it the second time we ran the test.
We also had to question the use of the 'Web Threat Detection' extension if it doesn't prevent users from downloading a known virus.
But not properly logging the work was most troubling. This would make it difficult for network managers to monitor user activity to see if they're involved in any risky online behaviors. While this may have something to do with the policies we mentioned earlier, we’d love to see proactive detection and reporting right out of the box.
Therefore, despite having a strong set of features, we believe the platform will appeal to a very narrow set of users. We strongly advise you to read through the administration guide before making any moves.
With almost two decades of writing and reporting on Linux, Mayank Sharma would like everyone to think he’s TechRadar Pro’s expert on the topic. Of course, he’s just as interested in other computing topics, particularly cybersecurity, cloud, containers, and coding.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.